As a cybersecurity researcher who has been actively using social media and the network for many years, you may have noticed that I share cybersecurity articles and news that I read and liked on LinkedIn and Twitter among my connections, especially during the week. Because my Twitter account is protected, my LinkedIn shares reach many more people than my Twitter shares, which can bring me to the radar of fraudsters, and scammers and result in receiving suspicious messages.
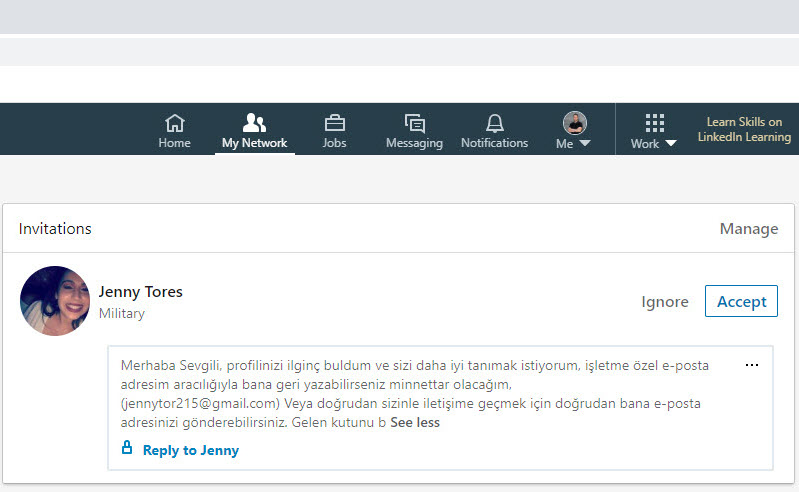
One day, I received a private message from Jenny Tores on LinkedIn. In the message, which was prepared with Google Translate and consisted of a text that was barely intelligible, she mentioned that she found my profile very interesting and wanted to contact me. I decided to take this opportunity, which came to me in the guise of a journalist searching for news, and communicates with this person.
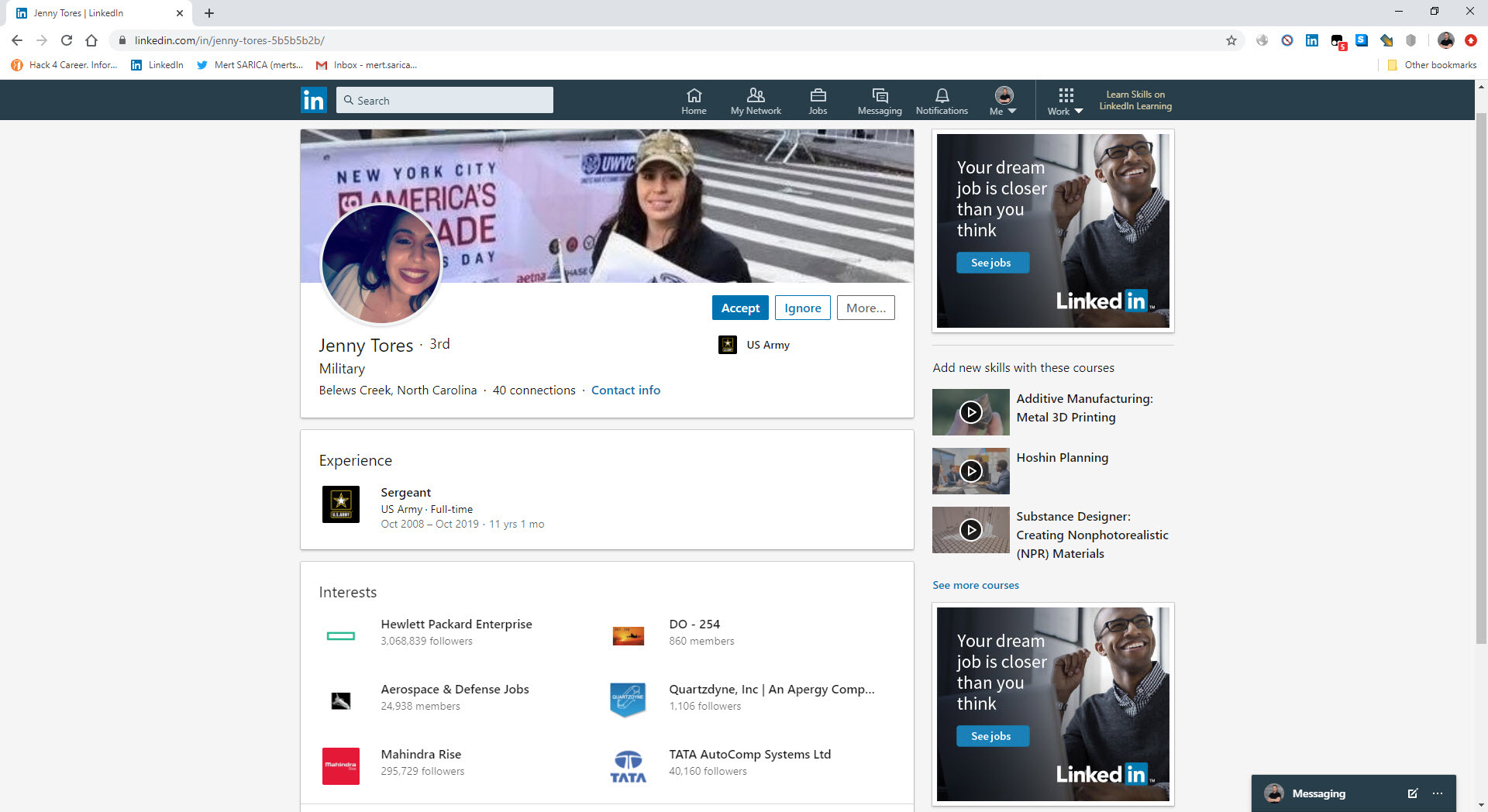
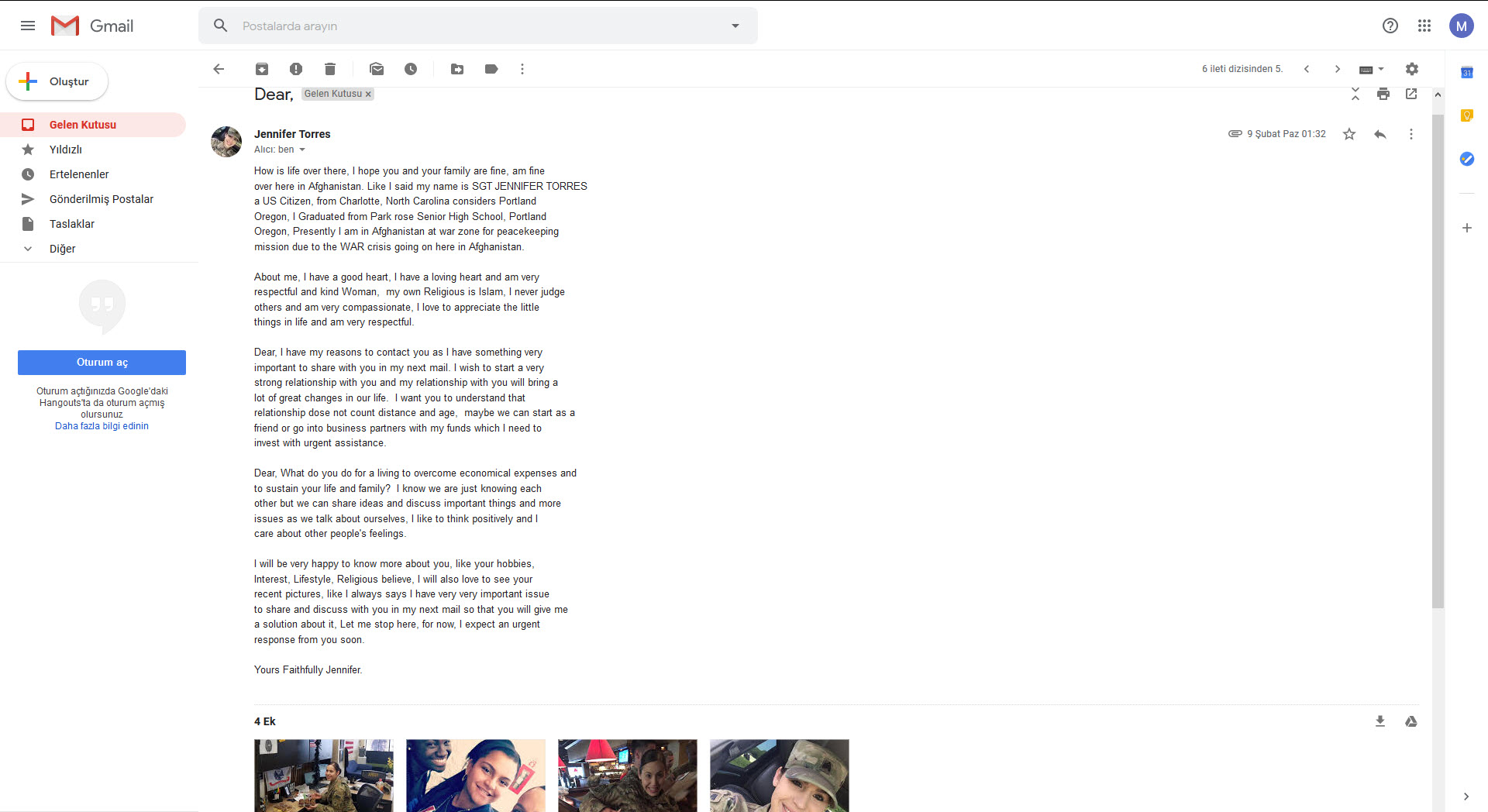
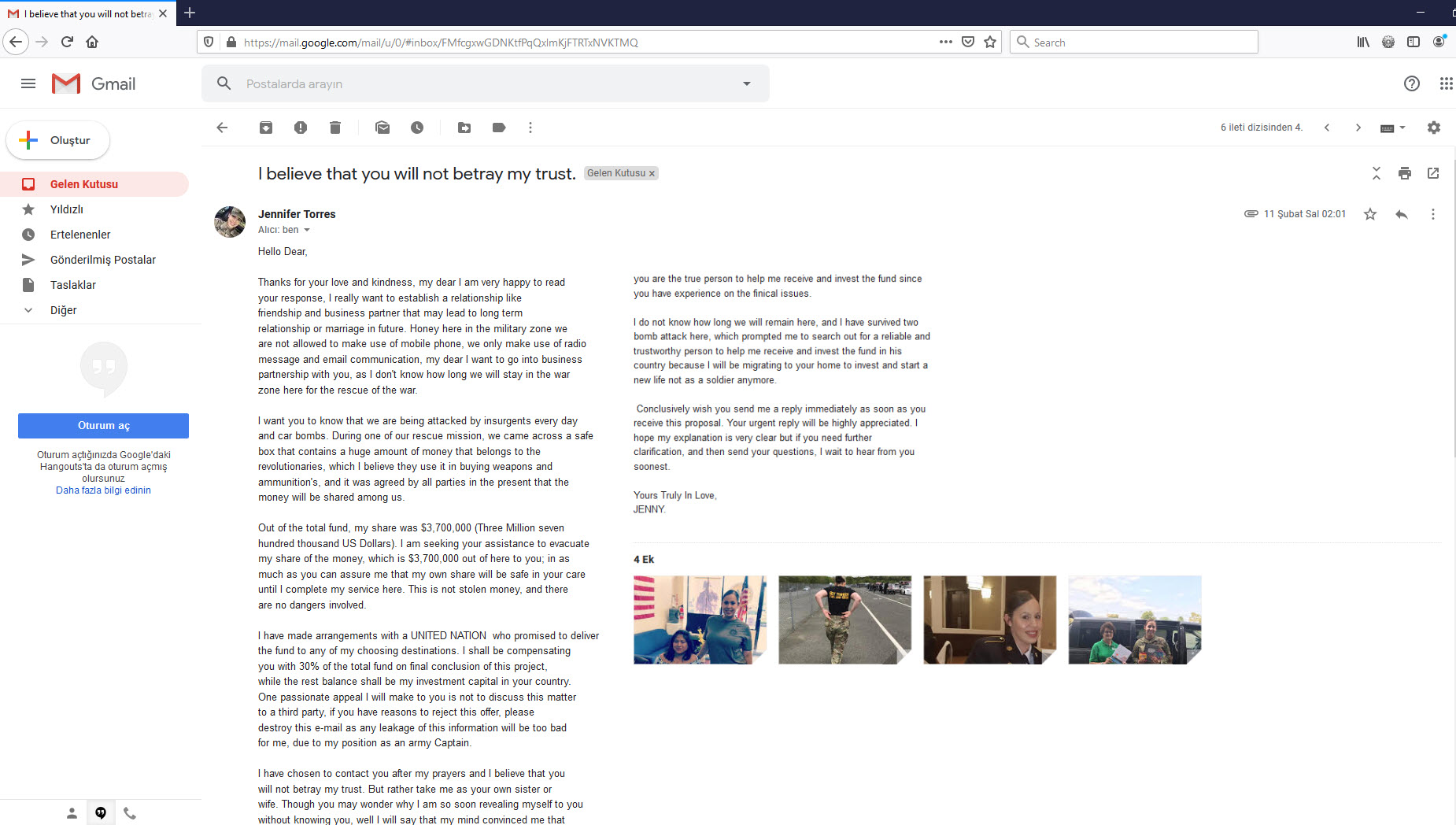
After sending her an email, in her reply, she mentioned that she is an American soldier in Afghanistan and that she wants to start a new relationship, that age and distance are not necessary, and that she will mention the important topic she wants to talk about in her following email. To make the social engineering attempt seem more realistic, she didn’t forget to send me 4 photos of herself. The writing style in her email was surprisingly good compared to the broken-sentence LinkedIn message.
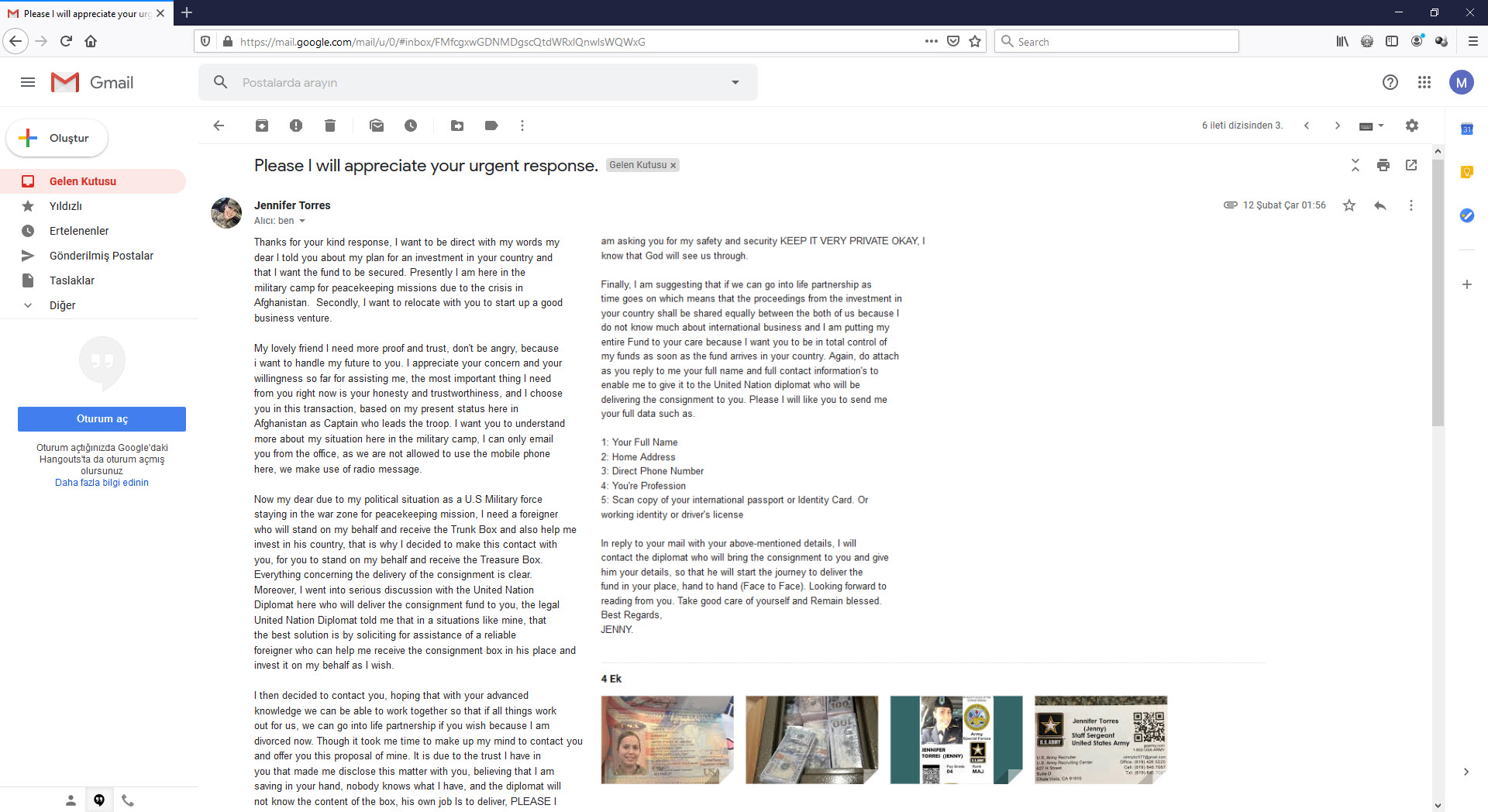
In her second email, she mentioned that she found a box containing a large amount of money during a rescue operation she carried out, that her share is precisely $3.7 million, and that she wants to take this money to another country until she completes her mission, of course, with my help. :) She also didn’t forget to send new pictures in this email.
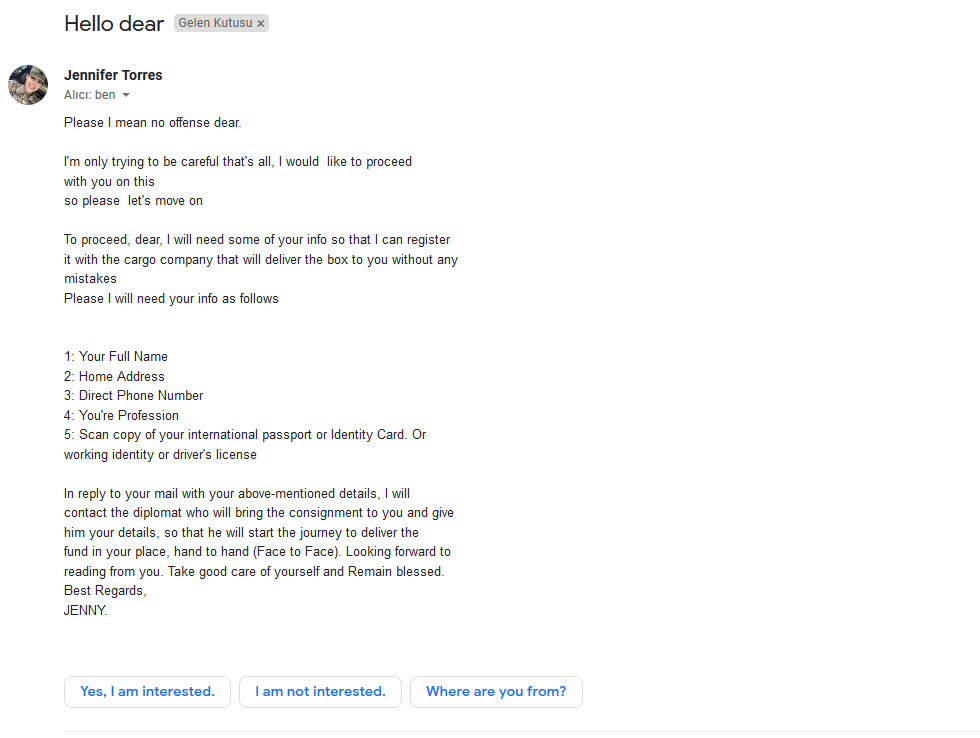
In her third email, to win my trust and to be able to carry out the shipment, she wanted me to send her my personal information, phone number, scanned passport or, if not, my driver’s license, and even my residence address, which I prepared from e-government. After examining the new photos she sent, including the 100-dollar bills in the box and her passport, I was convinced (kidding :)) to send her all the information she wanted from me.
After saying, “Oh dear, how can you not trust me” to her, in her final email, she said, “Let’s turn a blind eye to the past, but let me collect your information,” and ended the conversation. As a cyber security researcher, I decided to investigate the information in the emails and drop the scammer’s mask.
After reading a helpful article on the current state of image search engines a few months ago, I decided to take a closer look at the emails sent by our lady.
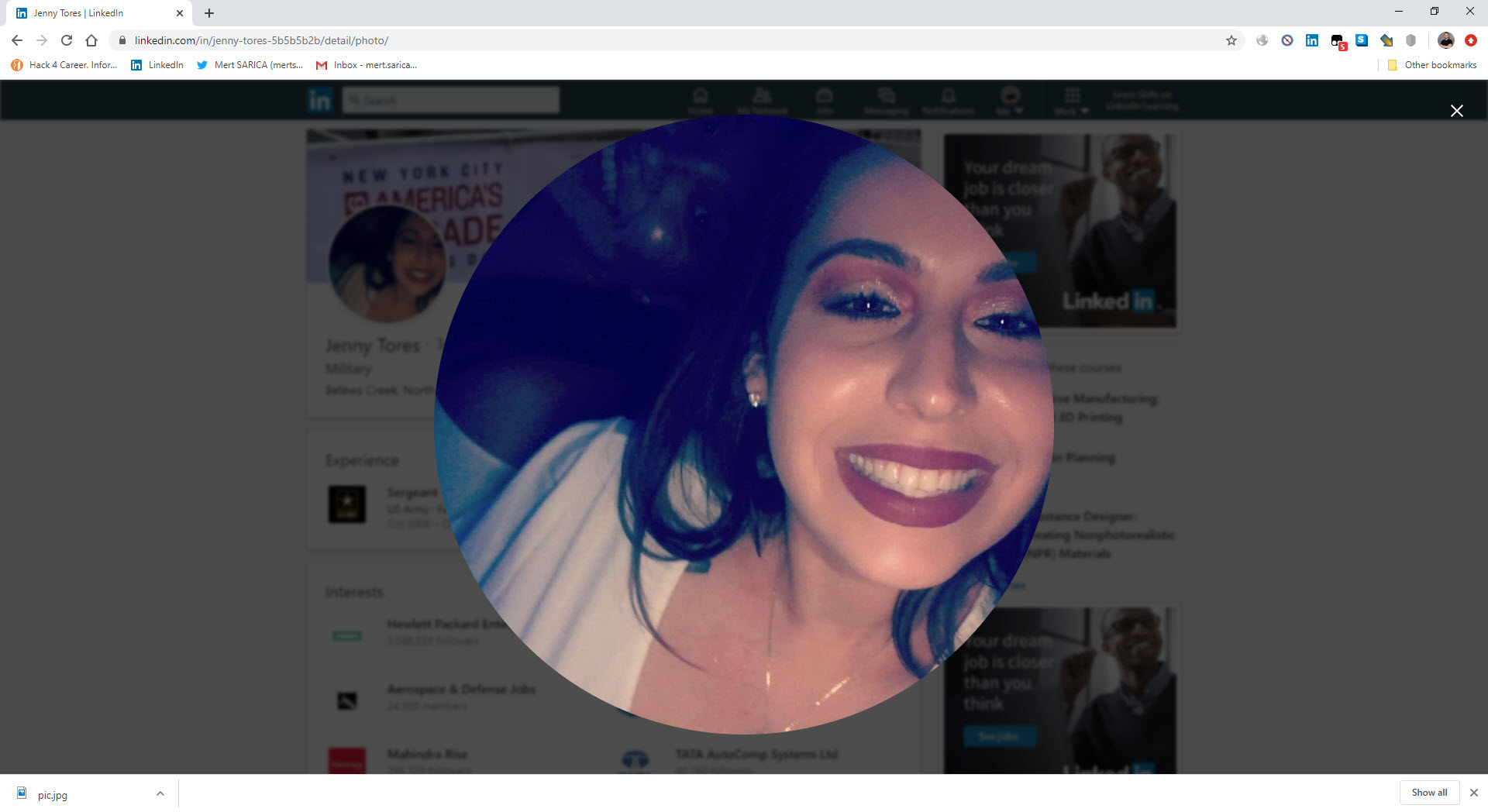
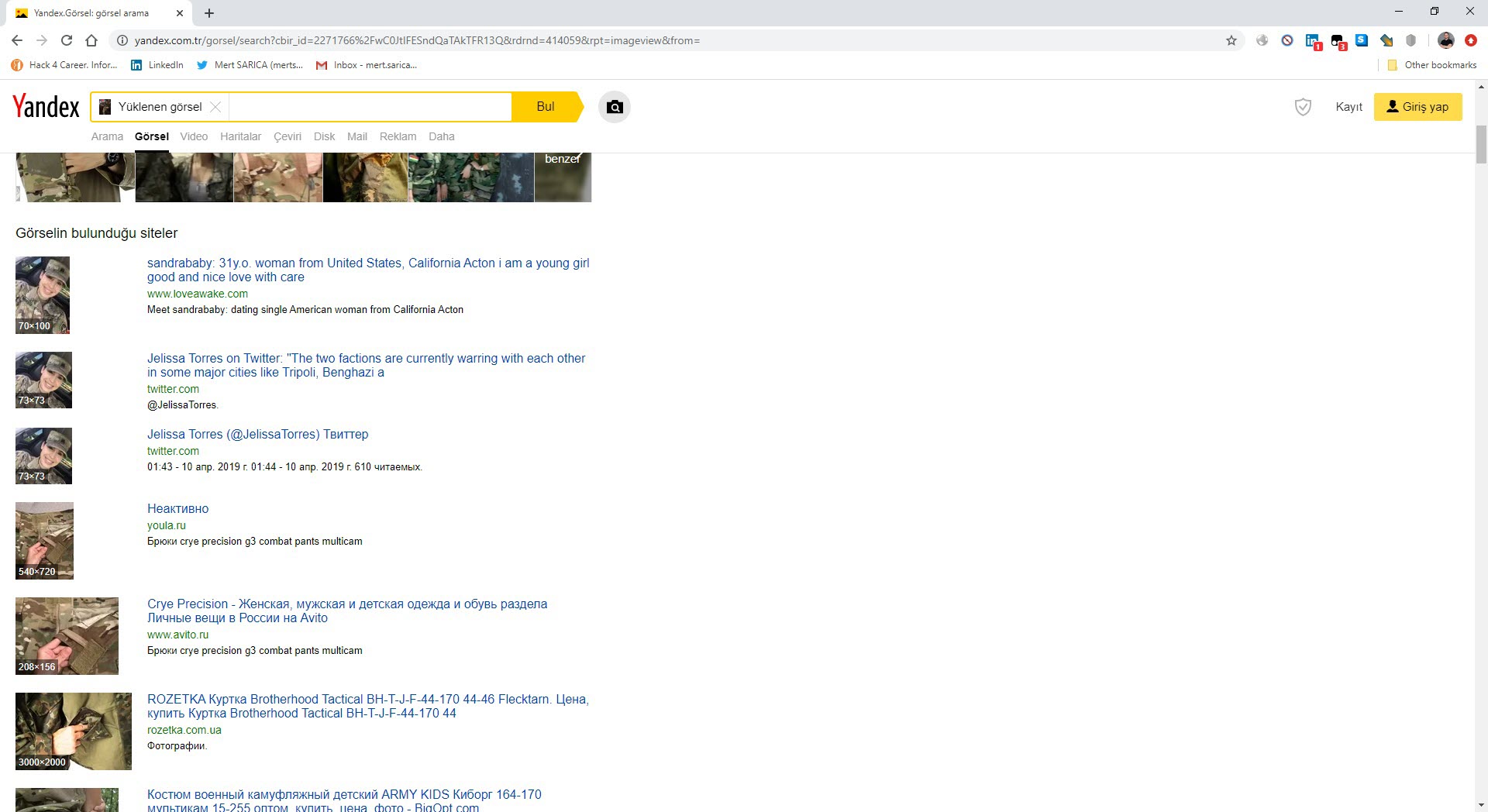
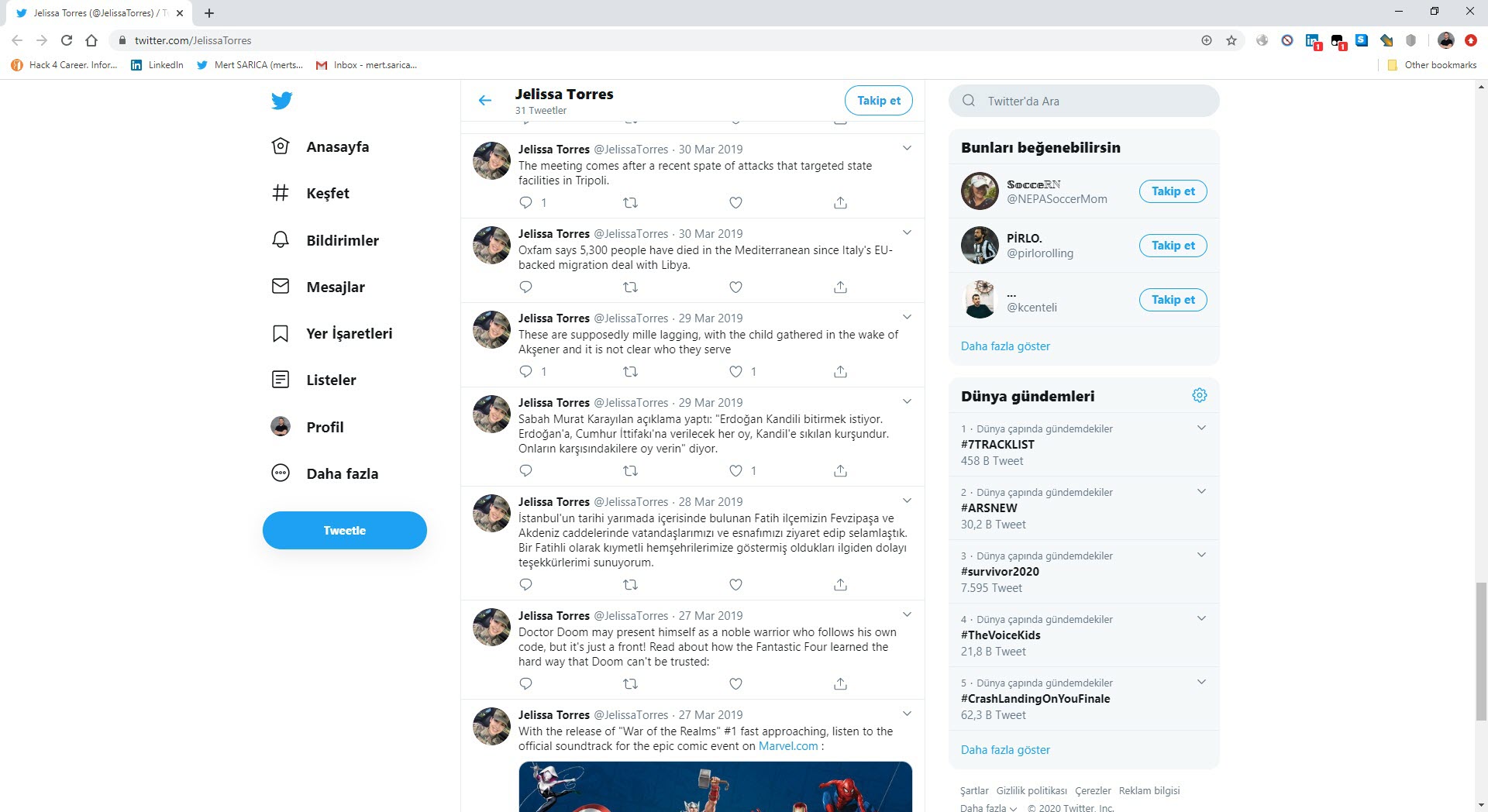
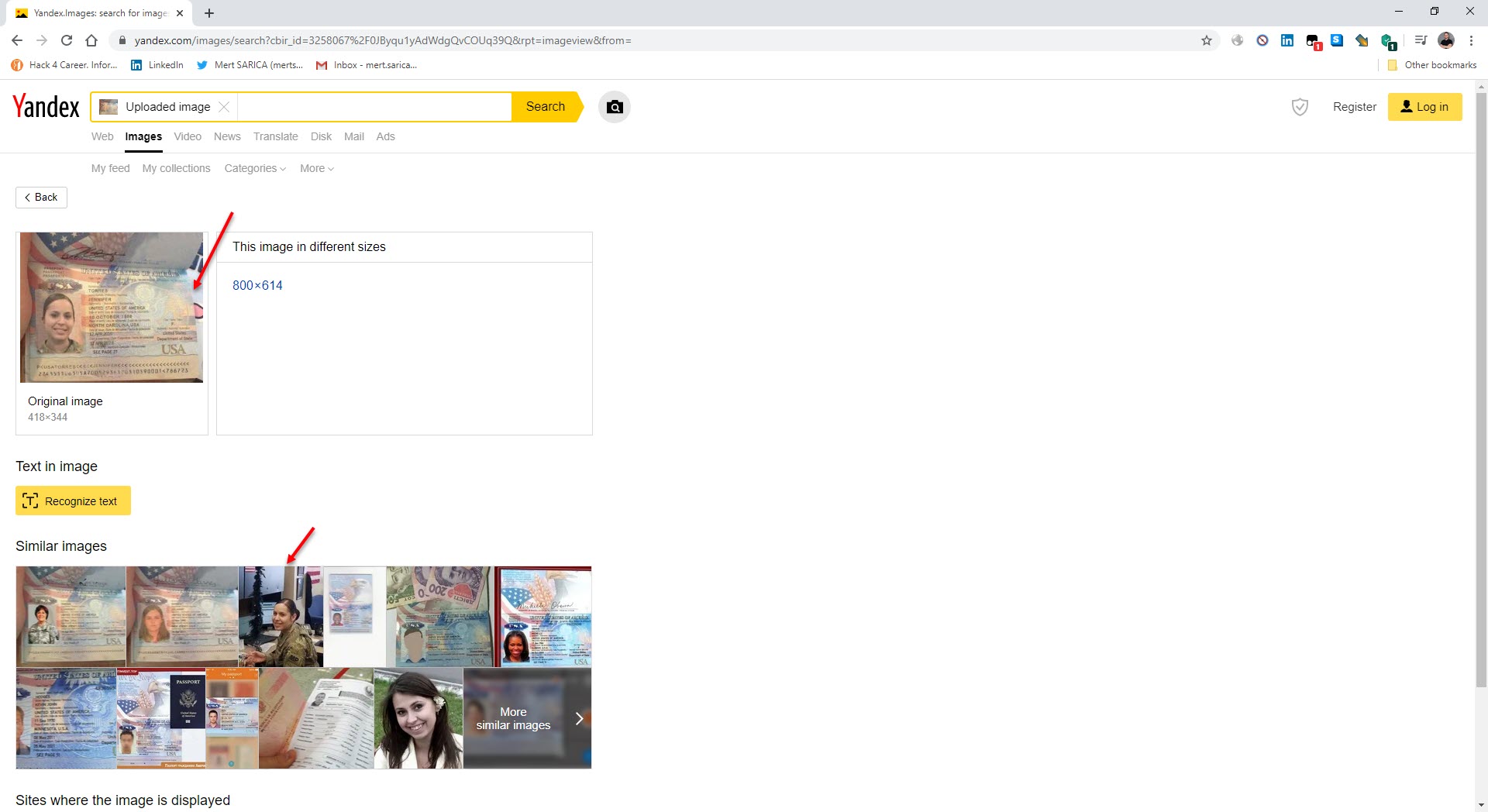
When I searched one of the photos in uniform on Yandex.Images, I learned that other websites were using this photo and that there was a social media account under a different name (Jelissa Torres).
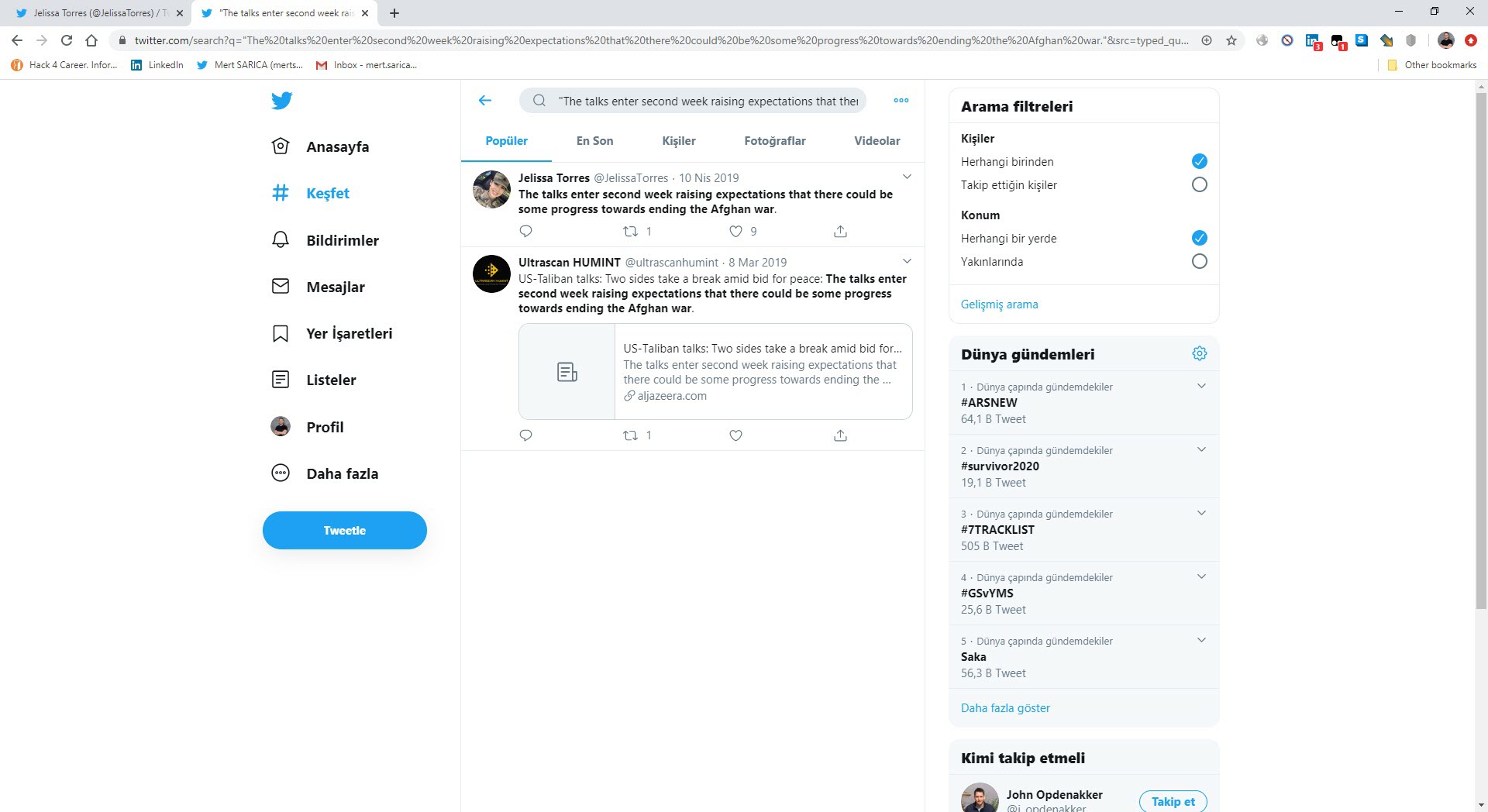
When I looked at the @JelissaTorres Twitter account, I noticed that there were Turkish messages among the tweets she sent until May 2019. When I searched these messages on Twitter, I learned that they were copied and pasted messages from other accounts.
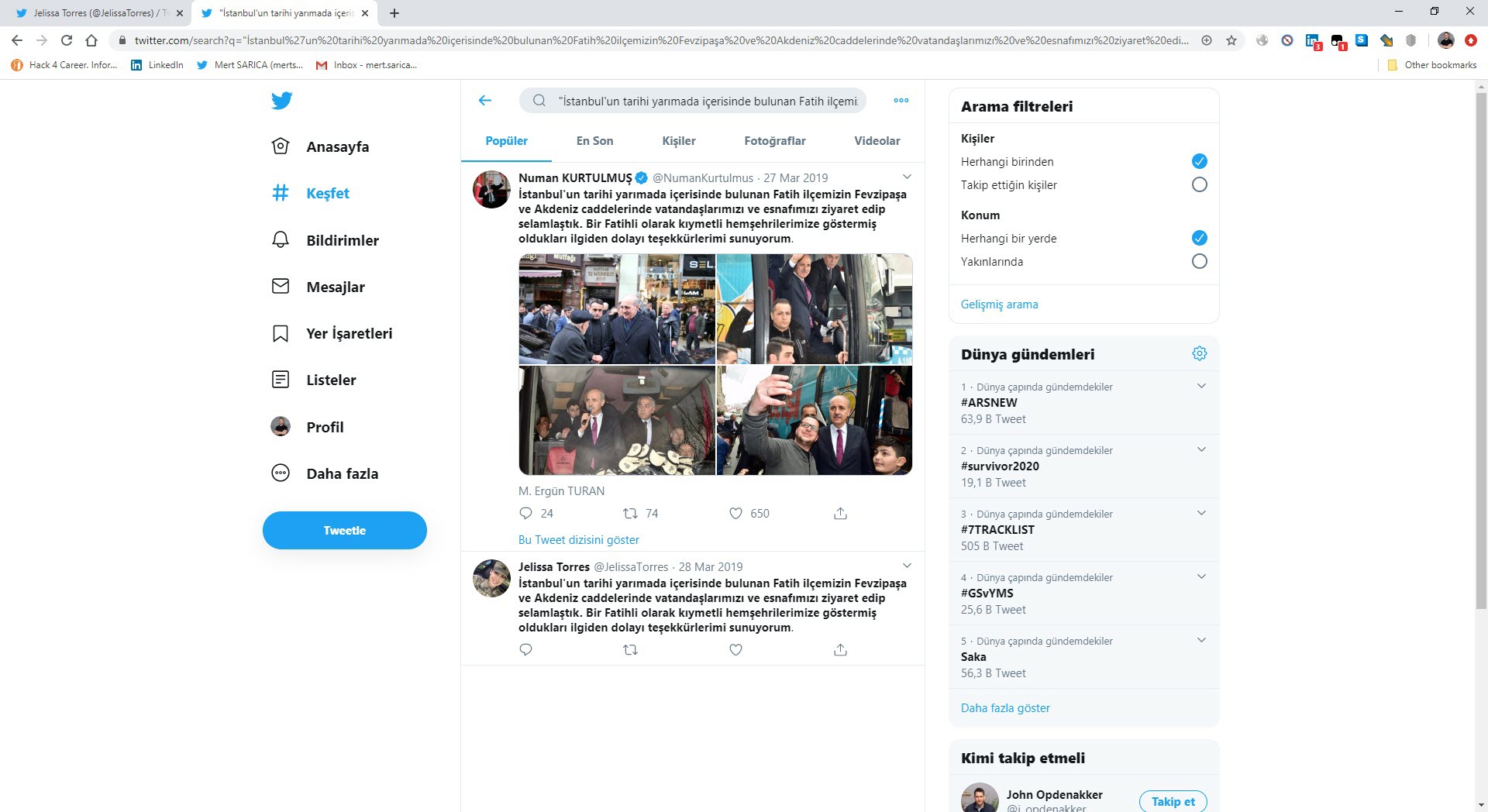
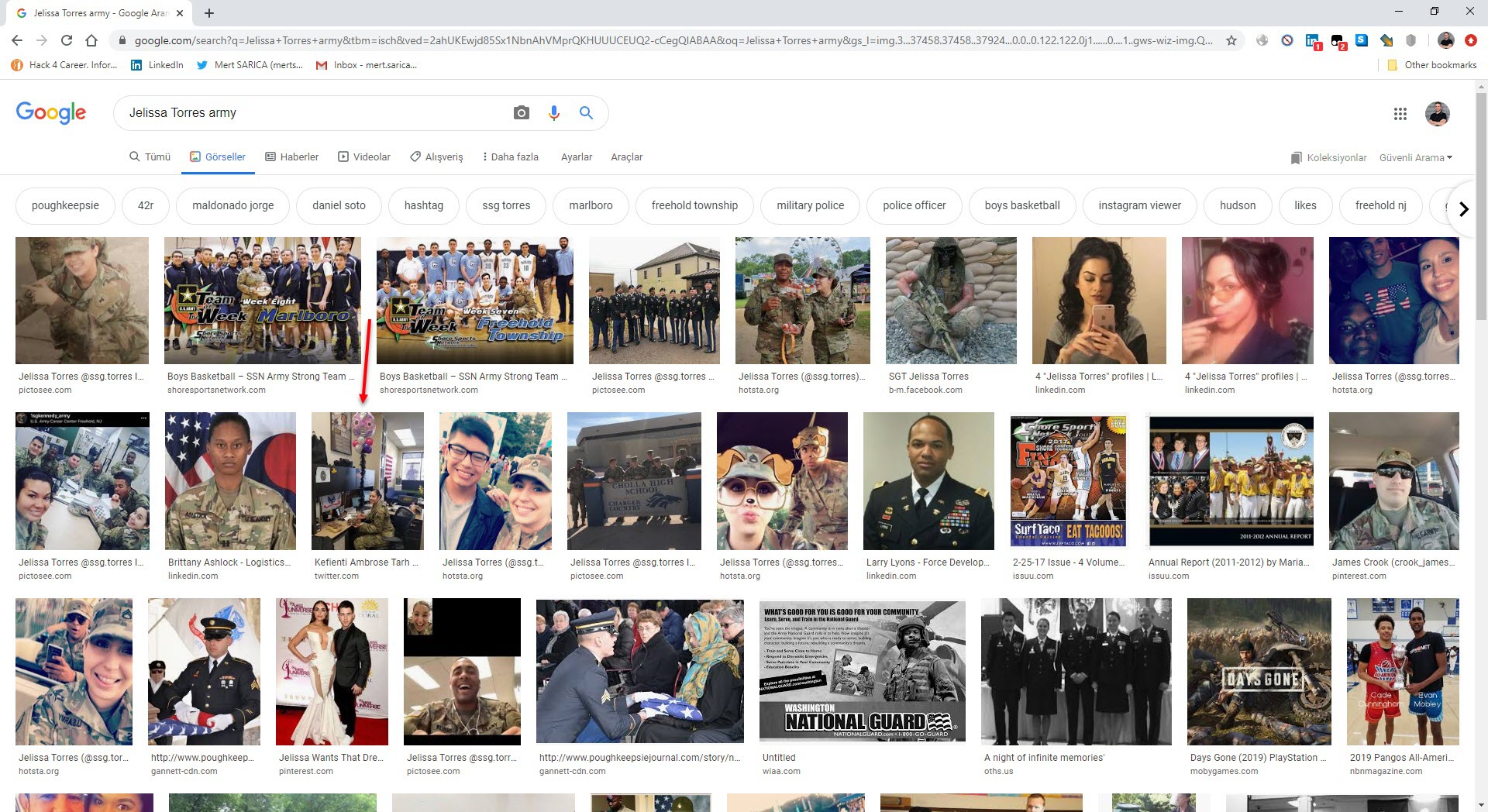
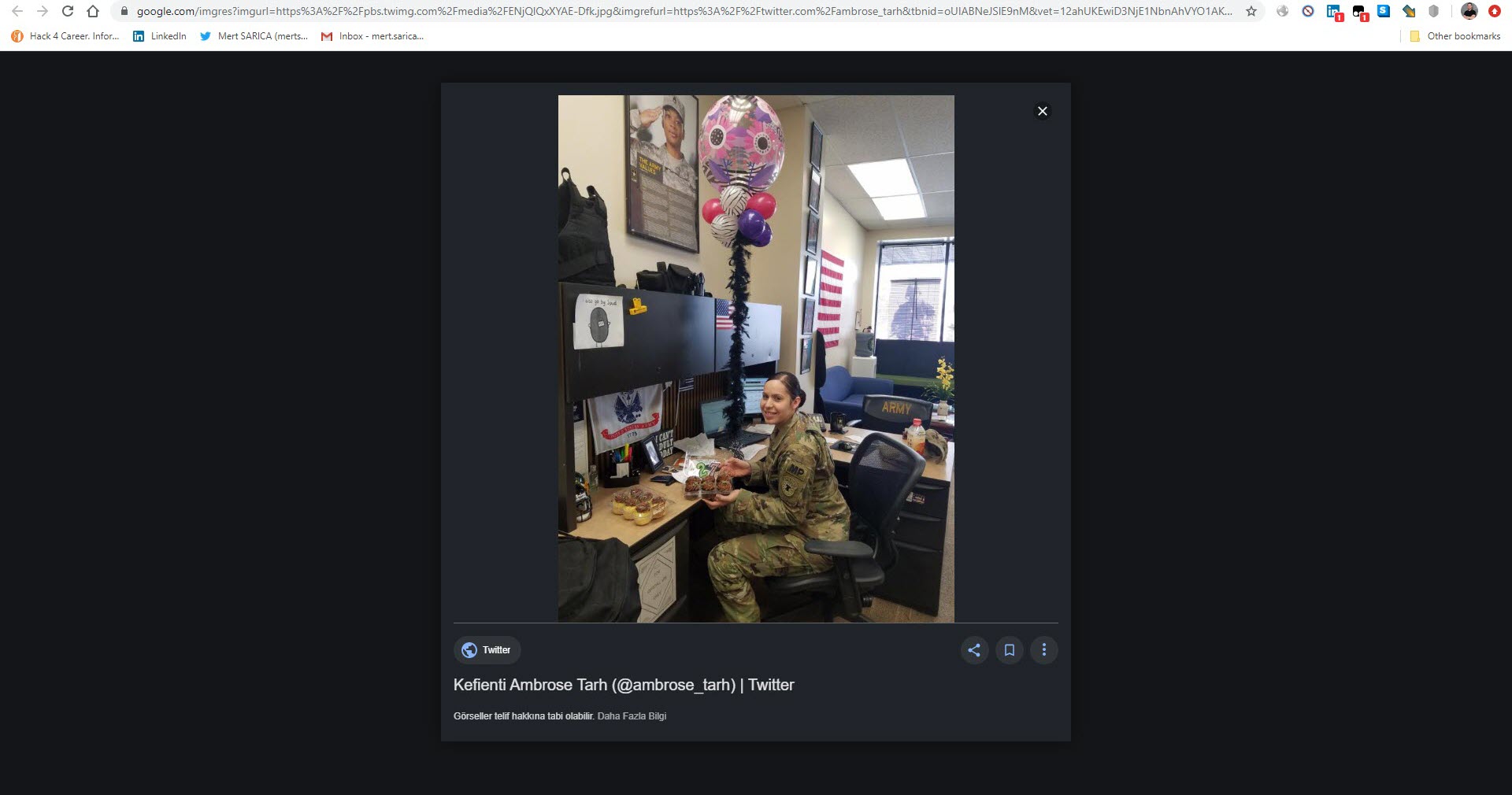
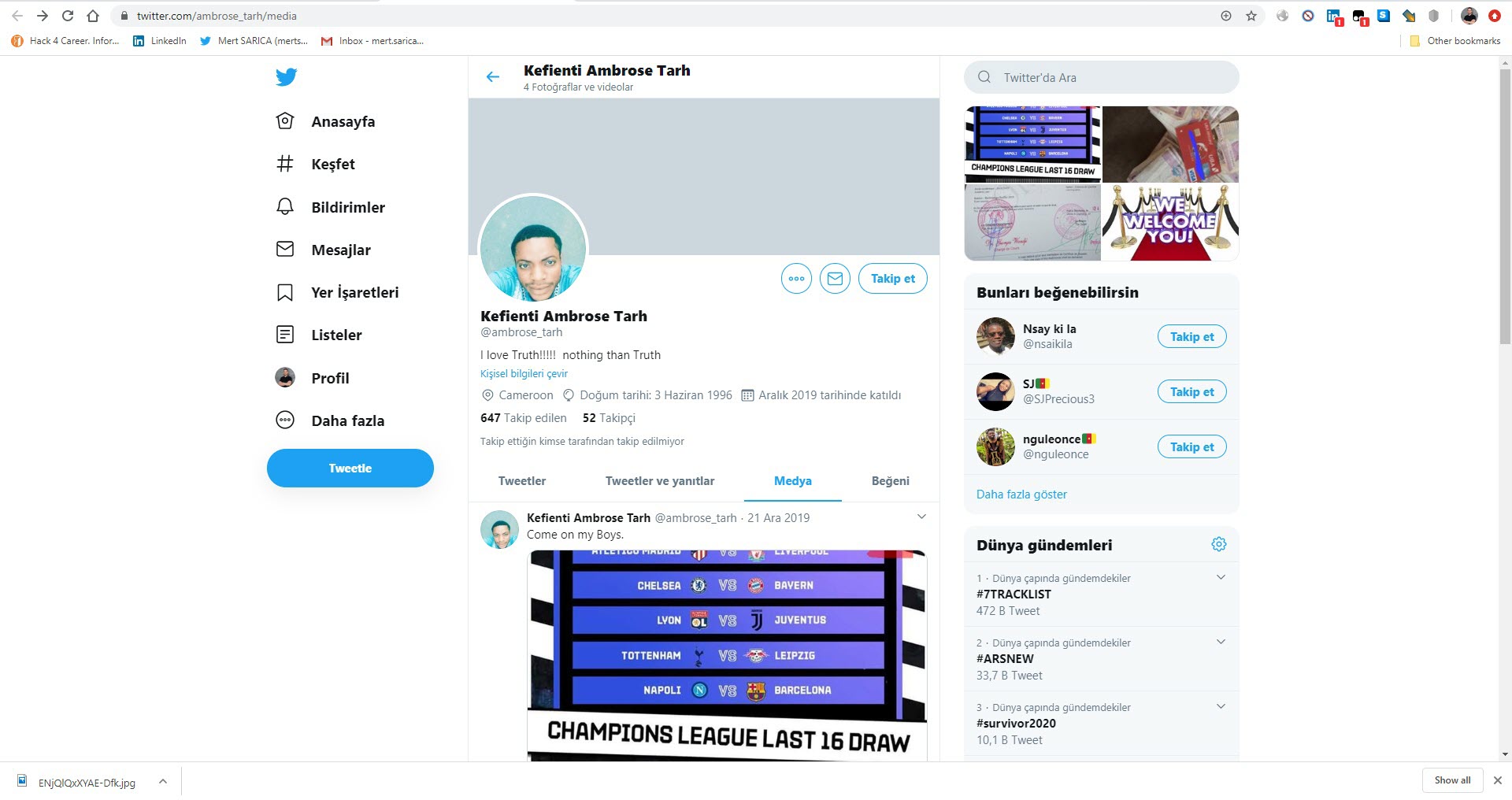
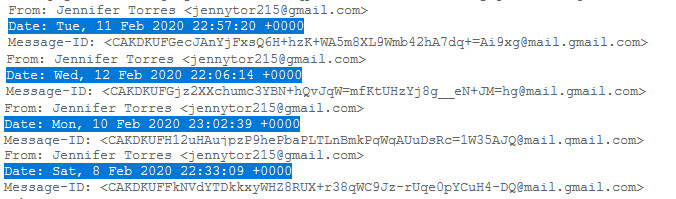
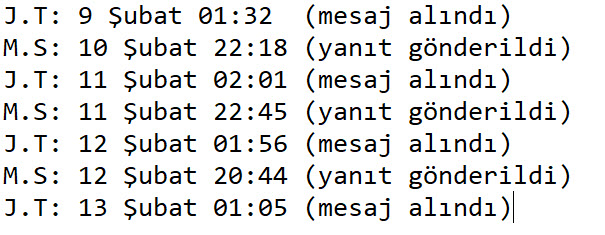
When I searched “Jelissa Torres army” on the Google search engine, I noticed that the @ambrose_tarh Twitter account shared one of the photos sent to me and then deleted it. (OPSEC fail?) When I checked the subject information of the emails sent by Jelissa, I saw a time difference of -3 hours between the sent emails and Turkish time. Considering that there is a 3-hour time difference between Turkey and Senegal, Ghana and Guinea, which are neighbors of Cameroon, I began to think that it is highly likely that these emails were sent by this person from Cameroon or by other people related to them from one of these countries.
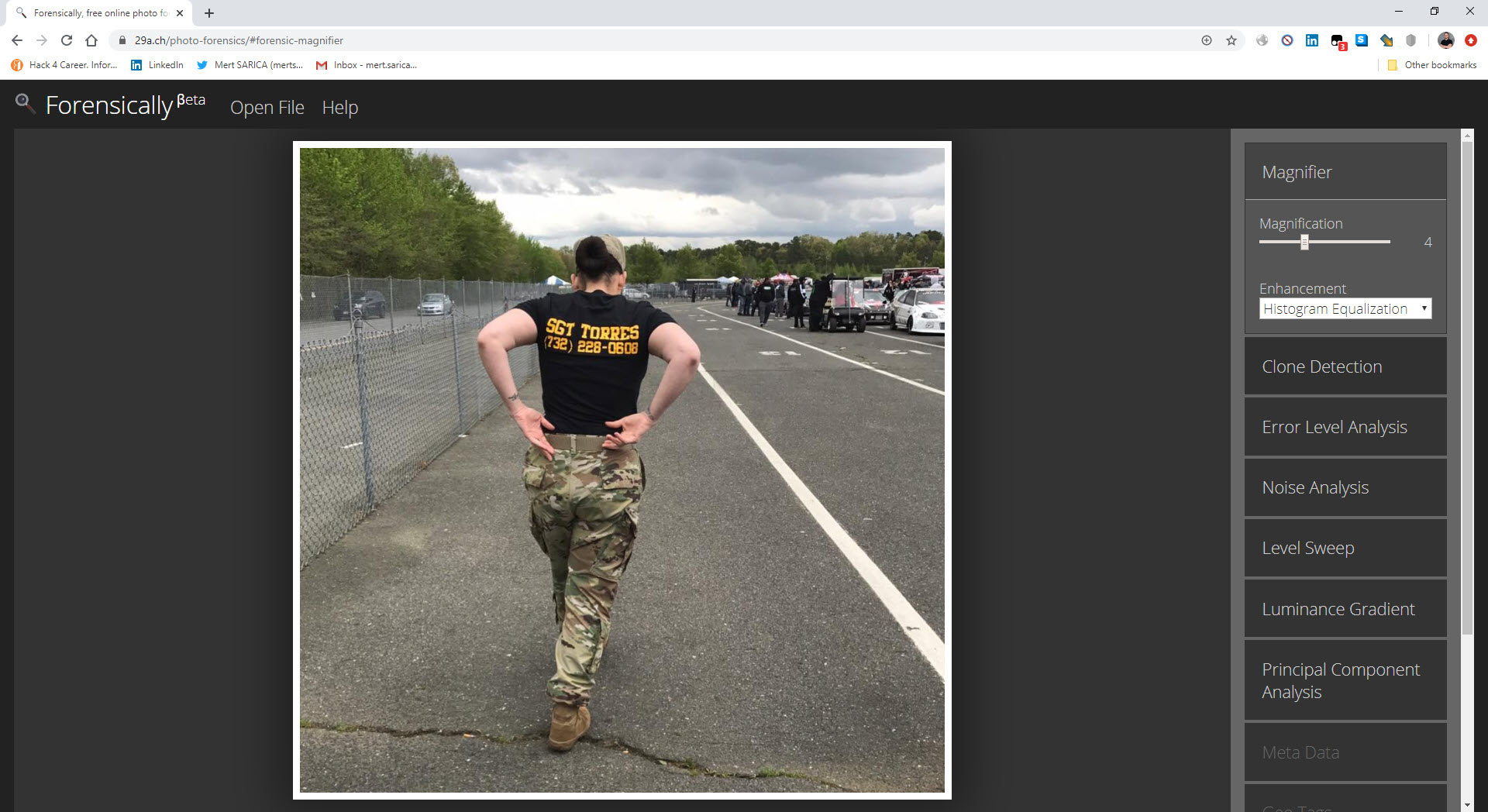
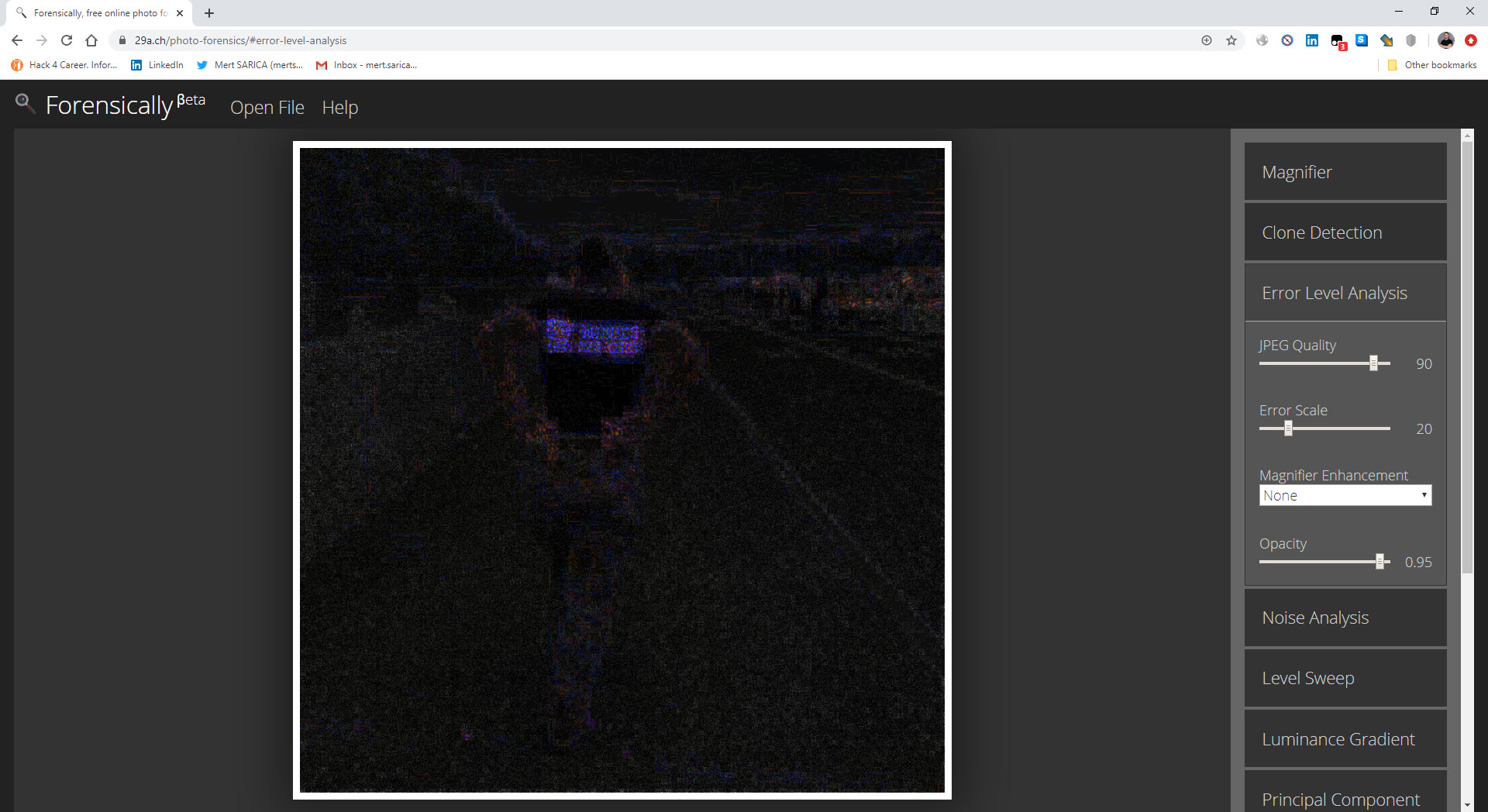
The amateurish photomontages caught my attention as I quickly glanced at the photos. As I mentioned in the Manipulated Photo Analysis blog article I wrote 7 years ago, I started analyzing the images using the ELA technique and the copy detection technique in the Forensically web application.
Thinking that no one would print their name and phone number on the back of their shirt like a sealed donkey, I analyzed this photo with the ELA technique, and, as I expected, I found the name and phone number on the back were added to this photo later.
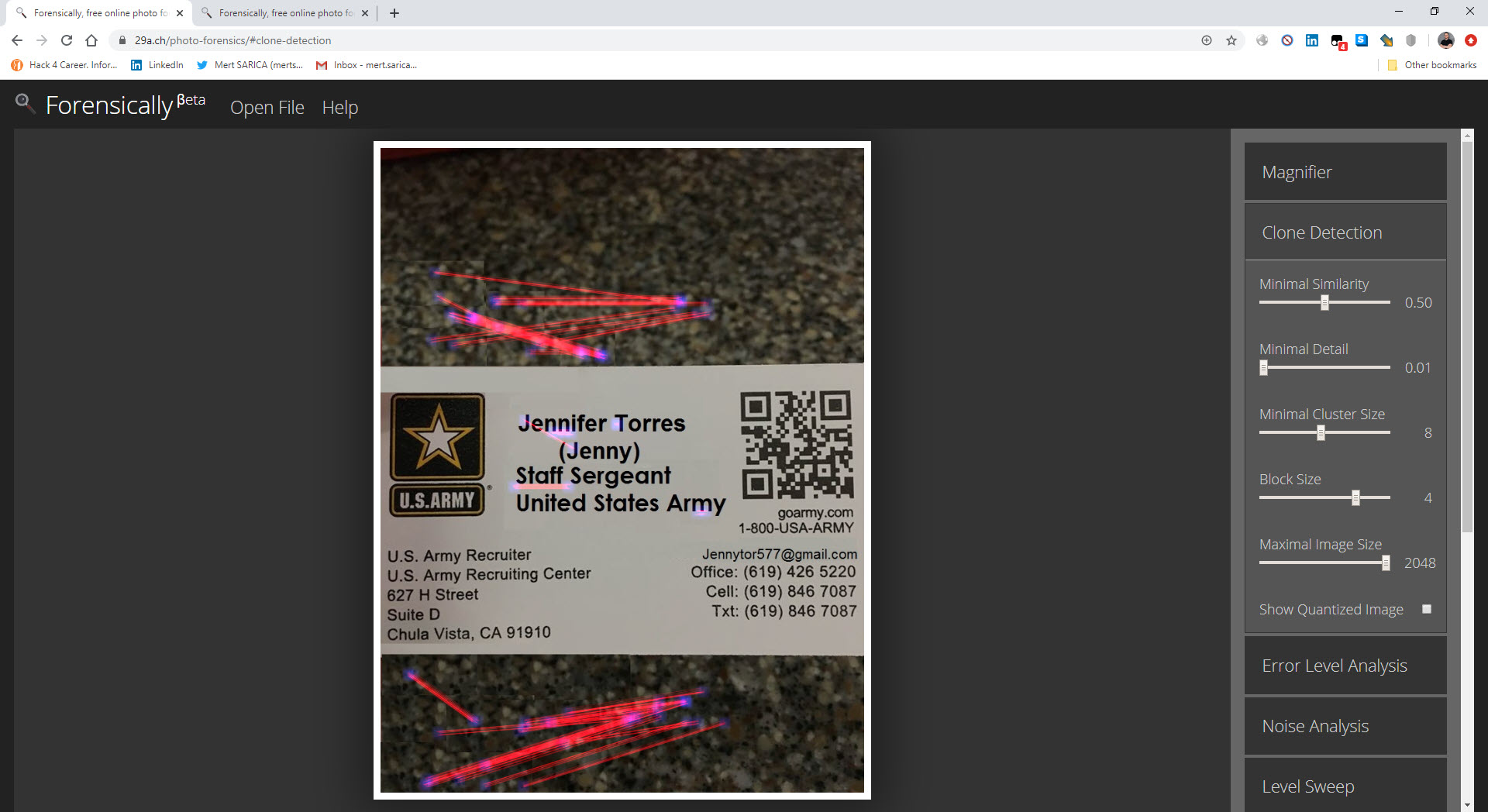
Although it was clearly visible that the photo with the business card was a photomontage, I used the Clone Detection page to confirm that many copies were made on this photo.
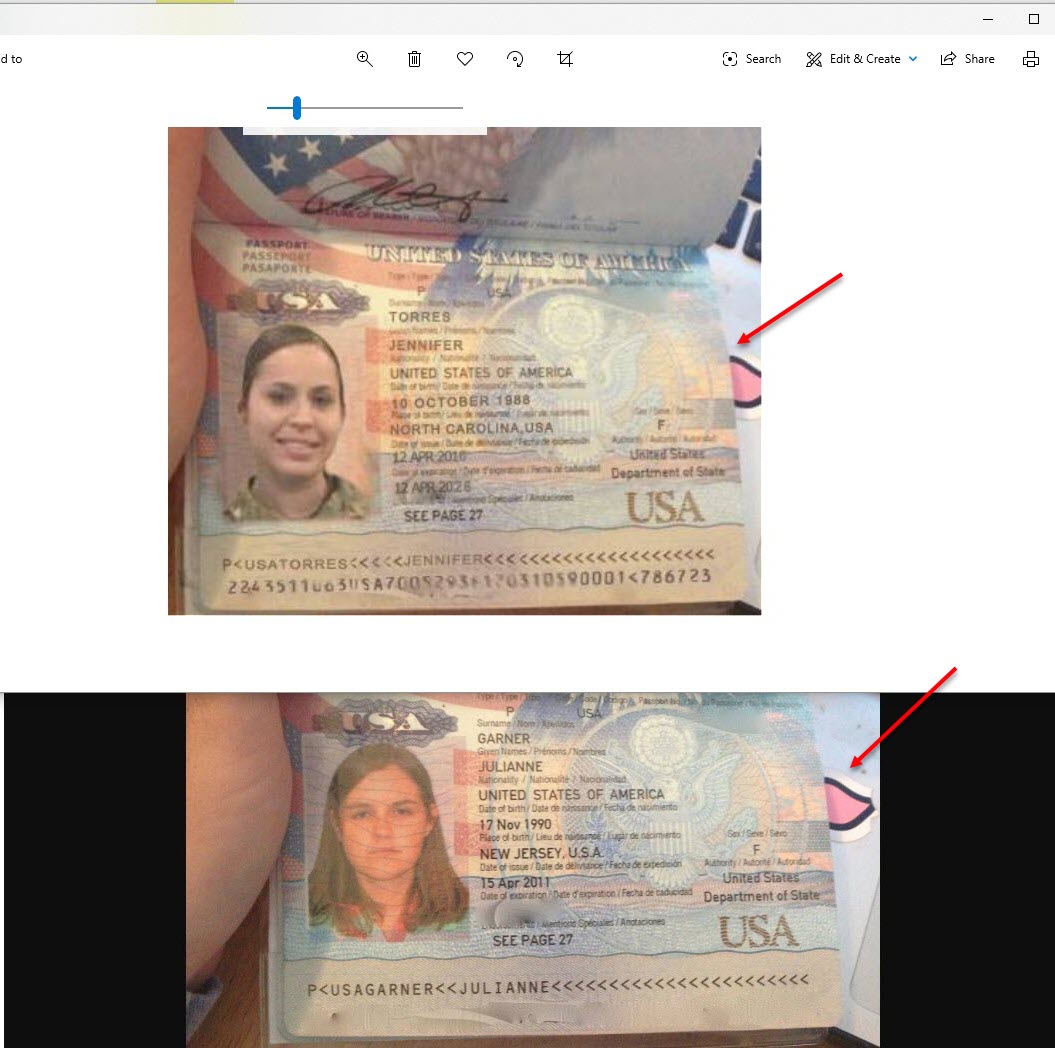
Finally, when I searched for the passport photo on Yandex.Images, I found similar fake passport photos with the same pink sign in the background, confirming that the passport was also fake.
In addition to this, the name and surname of the lady in question (Jennifer Torres) and the name and surname in the uniformed photos sent with the email were also obviously different.
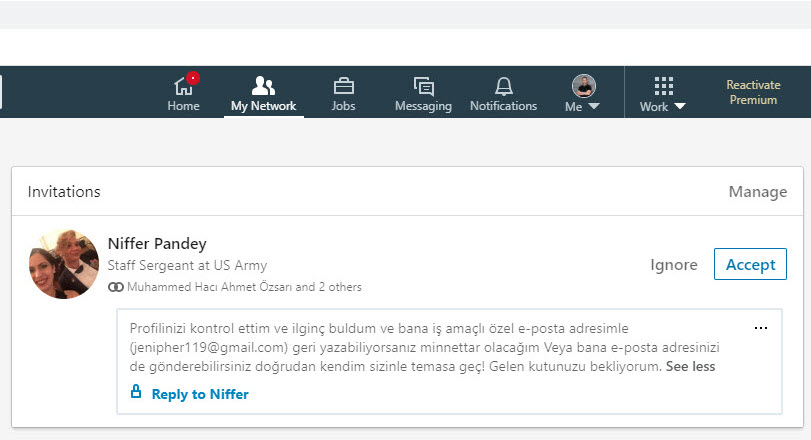
After cutting off communication with Jennifer, the greedy scammers did not let go and continued to flood my LinkedIn inbox with new messages for a while.
It seems that the once very popular Nigerian Prince scammers have decided to continue their activities on LinkedIn, so it would be helpful to be careful and warn those around you.
I hope to see you again with a new post in healthy days when we leave the COVID-19 pandemic behind. I wish everyone healthy and safe days.