Dear Diary,
In 1996, when I was around 13-14 years old, I heard a news about cyber attacks that were being carried out by computer hackers in the news. I was very interested in who they were? How were they able to penetrate systems? I decided to search for answers to these questions. I wanted to be like them, but I had no idea how. Over the years, by reading many technical books and articles and by practicing, I was able to find answers to all the questions that troubled my mind and I was able to turn my curiosity and hobby into a profession in the field of cyber security.
As someone who had kept what they had learned for years, 10-11 years ago, Hüzeyfe ÖNAL, who shared his knowledge about cyber security and wrote many technical articles, caught my attention. After communicating with him on LinkedIn and having a critical conversation, he asked me “Since you think you have knowledge in these topics, why don’t you write technical articles?
Putting exceptions aside, we think that we have a innate knowledge accumulation on most issues in the geography we live in. Sometimes we defend our opinions as true without our knowledge and when asked, we think that there is no one better than us in that specific area. We love to use sharp language in our criticism and we don’t shy away from being sarcastic, dismissive or destructive, but when the topic comes to “Why don’t you do better?” we start listing excuses. However, in the technical areas of cyber security, excuses can’t be hidden because if you think you know better, if you believe in your ability, you can show your knowledge by writing a technical article and/or giving a presentation.
If you are lucky, when you face the question “Why don’t you do better?” as a response to your criticism, you will make a decision like me and put your hand under the stone to do better. If you are unlucky, you will learn to empathize with the other side as seen in the video below before criticizing them eventually.
Huzeyfe’s question was one of the important turning points in my life. Thanks to that question, I decided to challenge myself and become a security researcher and blogger, dedicated to sharing what I know and what I’ve learned. I want to thank Huzeyfe ONAL specially for the 10th anniversary for giving me the opportunity to share my knowledge with cyber security enthusiasts through my blog and presentations.
Since November 2009, as I’ve been writing my blog, I’ve witnessed firsthand that knowledge is power, and it grows when shared over the years.
Over the past 10 years, through my blog;
Over the past 10 years, with my blog;
To achieve the things I’ve described above, I have worked hard for many years in a disciplined manner. I may have spent a month or three months researching for a blog post that you read in 15 minutes, and then I would spend about 6-9 hours of my personal time collecting and compiling the results and putting each one into a blog post.
Years may have been harsh and merciless to me in terms of time, but I have never regretted the time I spent on my beloved security research and blog posts. However, as the years passed, the time I could dedicate to security research has gradually become more and more challenging to write a blog post every month.
After 10 years, I have decided to slow down a bit, to spread my blog posts over a wider time frame and to share this situation sincerely with you.
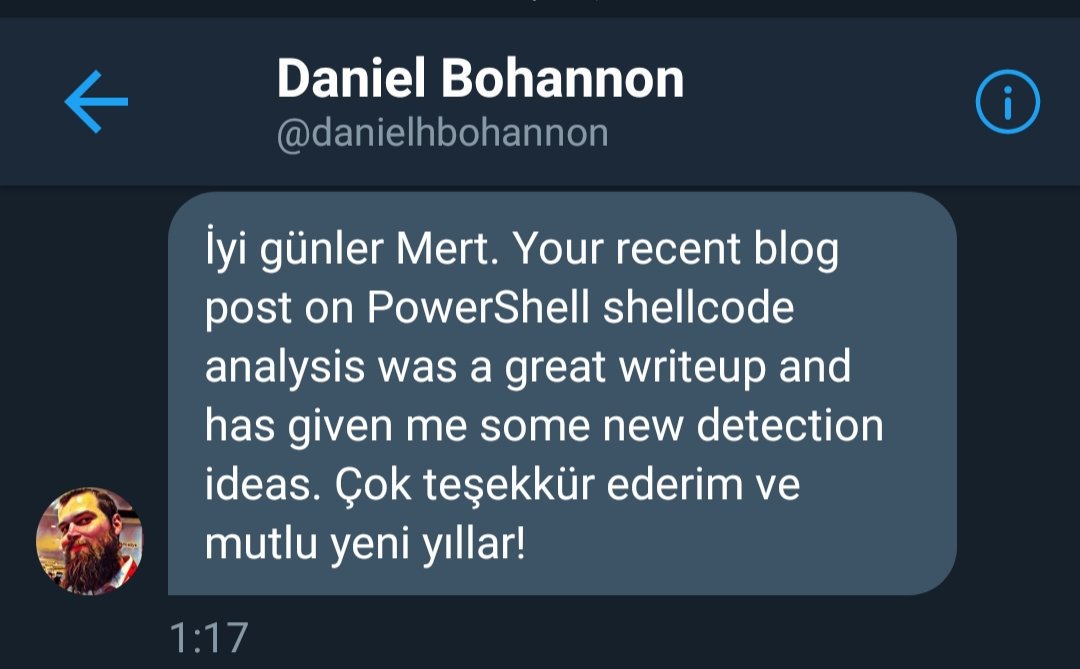
Over the years, your positive feedback and constructive criticism have always kept my motivation high and encouraged me to continue to do security research, write a blog, and give presentations.
I am grateful to my valued readers who always supported me.
I look forward to seeing you in new writings.