Escape from Imprisonment
As someone who has used the ADSL modem of internet service providers for years and conducted security research on them (such as “How Secure are ISP Modems?” and “The Importance of Firmware Analysis“), I cannot say that I have a positive attitude towards using gift modems on an individual level. Some of the main reasons for this are: the embedded user accounts used by internet service providers can be easily discovered by anyone, and if the end user leaves the management page of the modem/router open to internet access, it can be misused by others; the firmware is a special version, which means that it cannot be updated to the latest and most secure version; and the firewall cannot be set up for each port, and the management pages are limited.
About two years ago, when the fiber internet infrastructure came to my house, the ADSL modem was replaced by a router. The Tilgin brand router, model HG1332, which is not even mentioned by name on its own website, that my internet service provider forced me to use, replaced the enjoyable days I had on the internet with imprisonment. The WiFi signal strength beyond average, the absence of OpenVPN support, which has become commonplace in routers, the lack of support for modern security world’s encrypted DNS communication (DoH), and the limited support for dynamic DNS (DDNS) are just a few of the many negative reasons that I can mention.
After a short unhappy relationship with this router, I contacted my internet service provider to change the router, but unfortunately, I received a negative response. When I researched on the internet to get rid of this router, I could not find any tangible sources other than complaints, and as I did not have much time to do so, I had to resign myself to my fate over time.
As the time I spent with Tilgin HG1332 became increasingly unhappy, I learned that after a year of searching on the internet, my internet service provider allows you to use your own router by using the HG1332 in bridge mode. As time went by, I began to search for ways to completely get rid of the HG1332 that I hated so much. When I called for help through my social network accounts, many people volunteered to help. After Aykut ALPER told me that he had done this with a Mikrotik router on a different internet service provider, and another helper told me that I could get rid of the HG1332 by using the VLAN ID, PPOE username and password, I started working on the list of needs.
Some of the questions that came to my mind when I was preparing the list were:
Since I know that for years, DD-WRT, Tomato, Asuswrt-Merlin, and other custom firmware can be easily installed on Asus routers and modems, I prefer Asus brand. And because the hardware software Asuswrt-Merlin has security features that I liked, I choose it. Since the models supported by Asuswrt-Merlin are generally expensive, I bought the RT-AC1900U model, which was the most suitable for me in terms of price and performance.


When I connected to the interface of Tilgin HG1332 as an admin user, unfortunately, most of the management pages where I could see my VLAN ID were hidden. When I researched HG1332 on the internet, I came across a successful work by İlteriş EROĞLU, who had managed to obtain the username and passwords defined on HG1332. In my article “The Importance of Firmware Analysis” from 2015, I also drew attention to the TR-069 communication that takes place over an insecure channel, and it surprised me to see that it was still in use in İlteriş’s work years later. In the article, I was able to easily learn my VLAN ID by connecting to the interface of HG1332 with the root user.
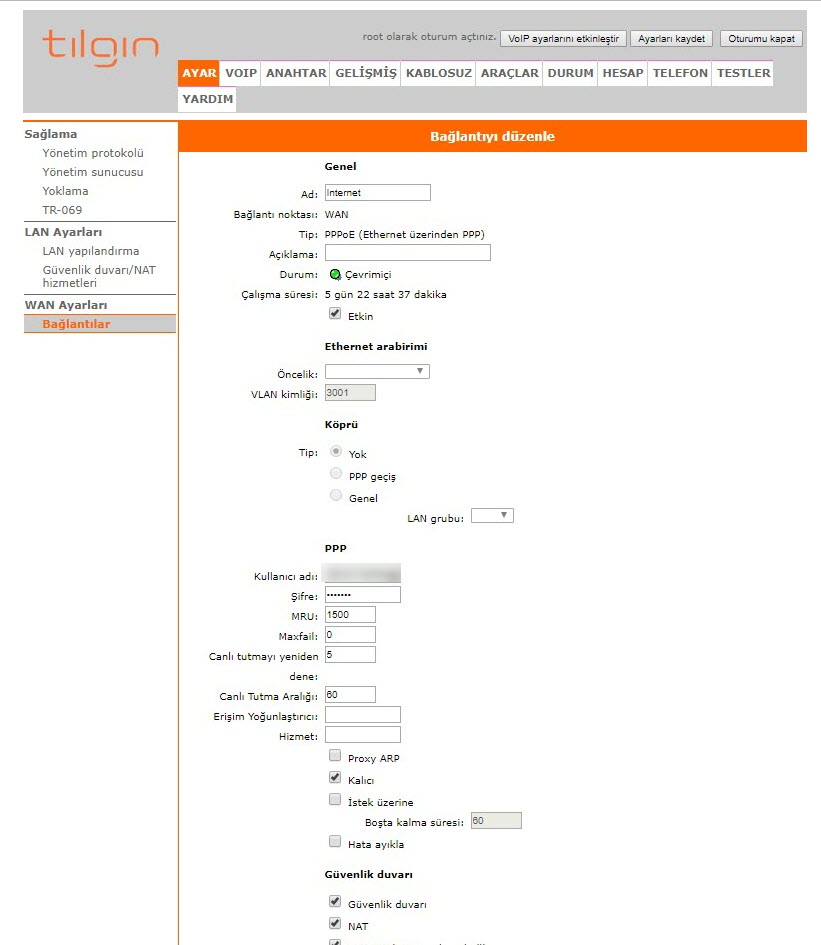
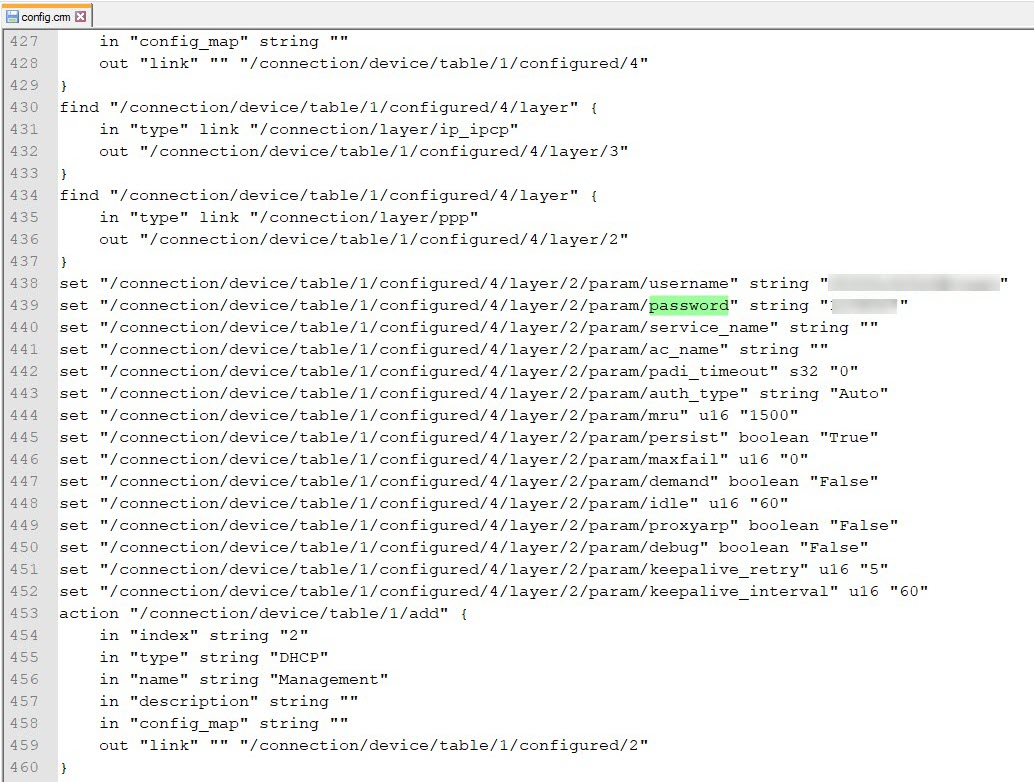
After entering the interface with the root user, I was able to obtain the PPPoE password by downloading the current configuration from the router and extracting it from there, as the PPPoE user’s password was masked.
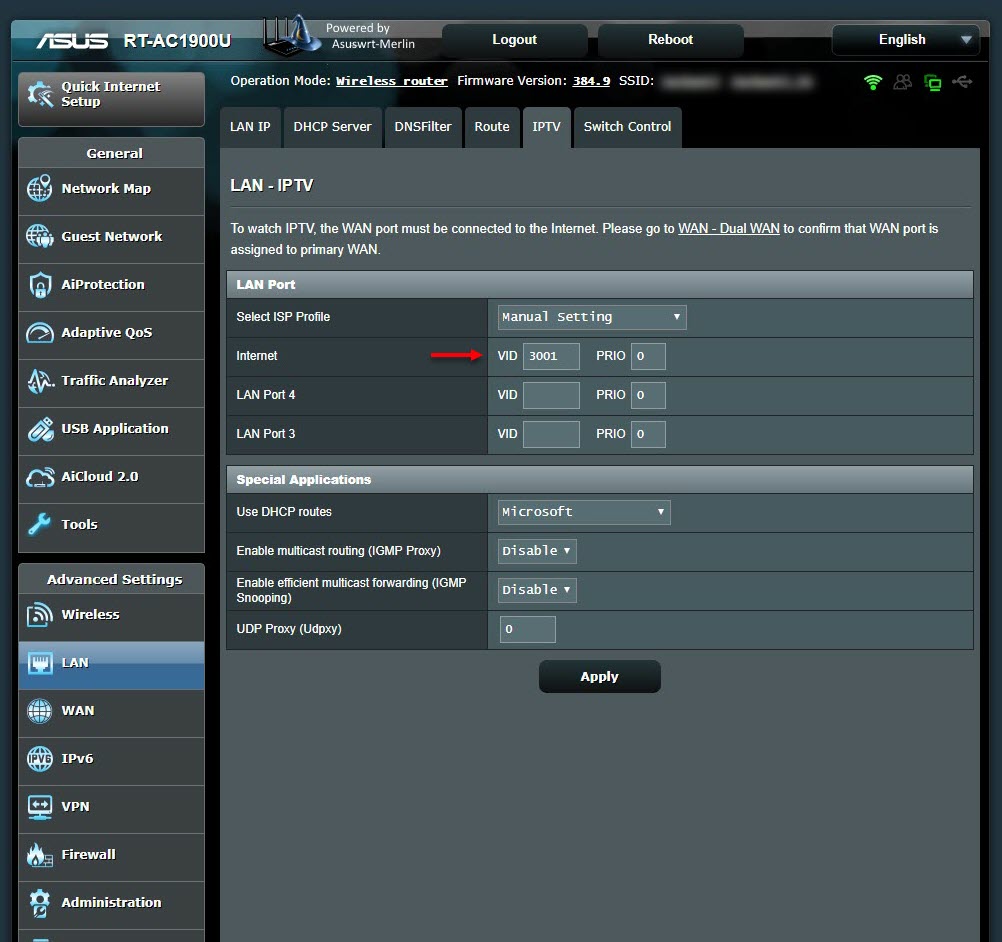
I downloaded the relevant firmware version (RT-AC68U firmware should be used for RT-AC1900U) from the Asuswrt-Merlin website for the RT-AC1900U, and successfully installed it through the web interface. Then I also made the PPPoE and VLAN ID definitions, and saw that the router was able to connect to the internet successfully.
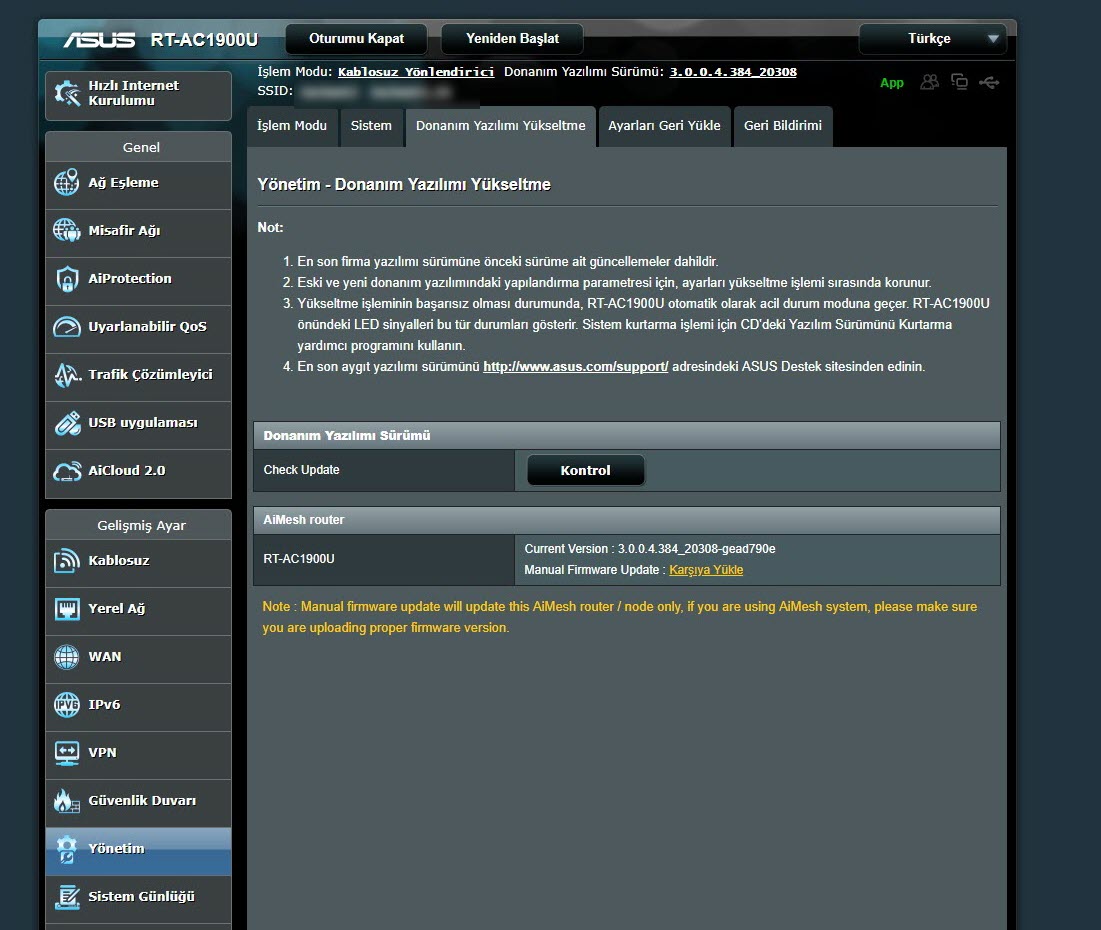
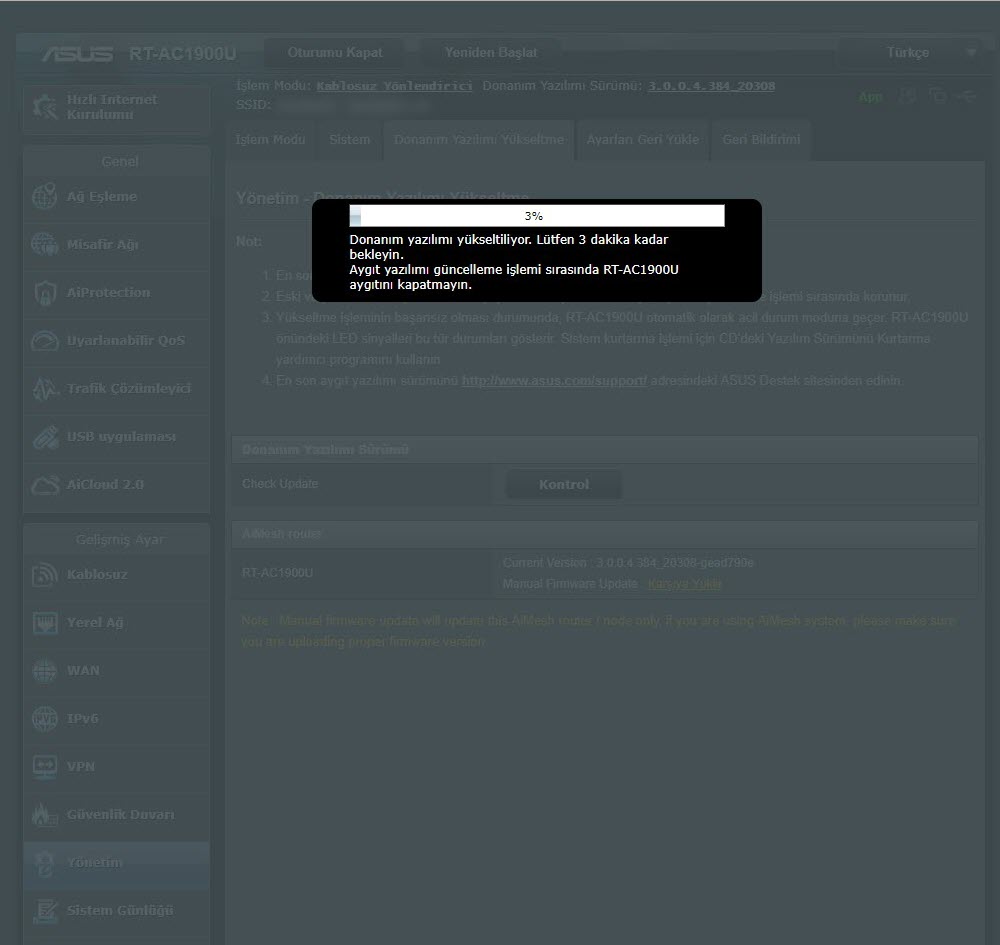
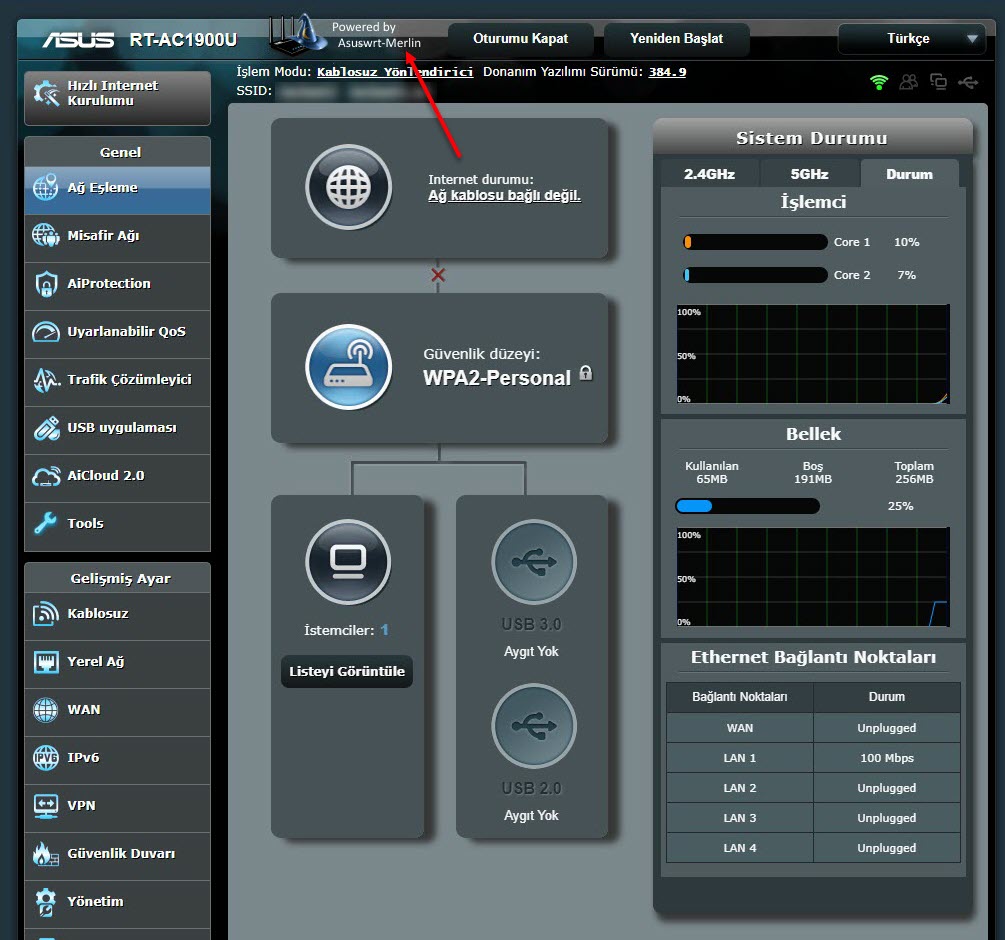
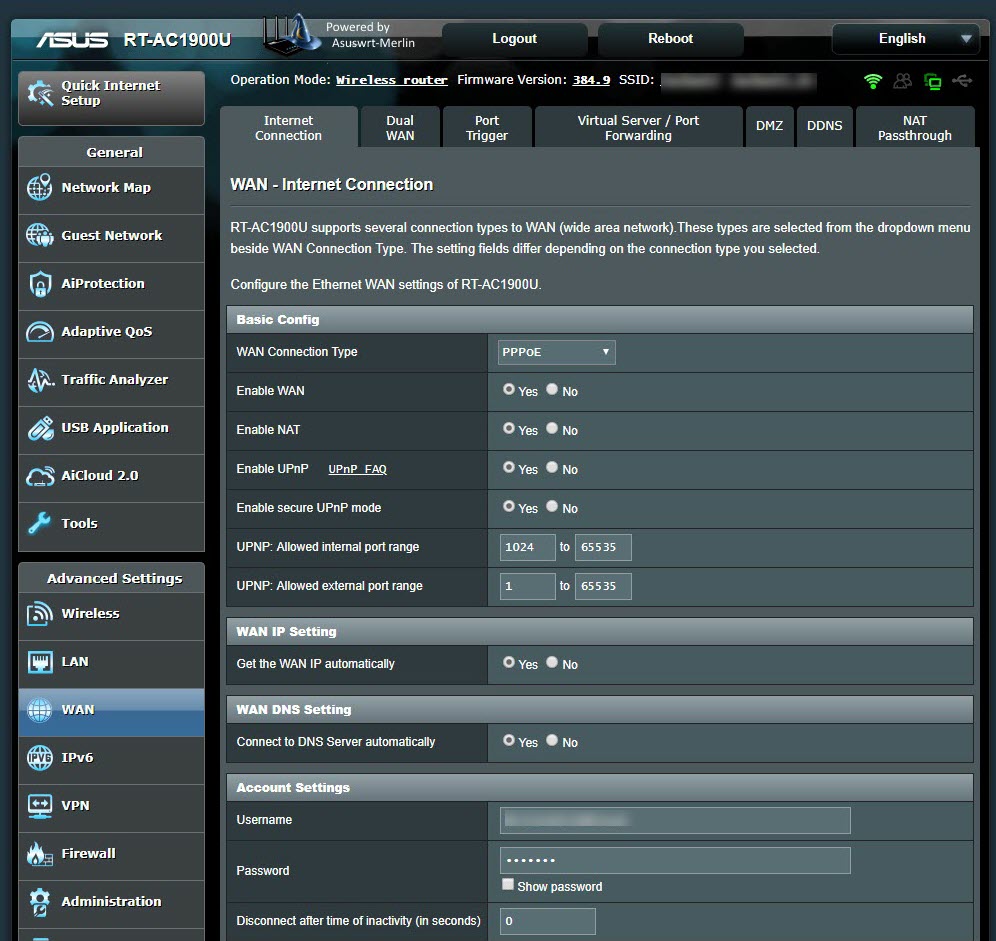
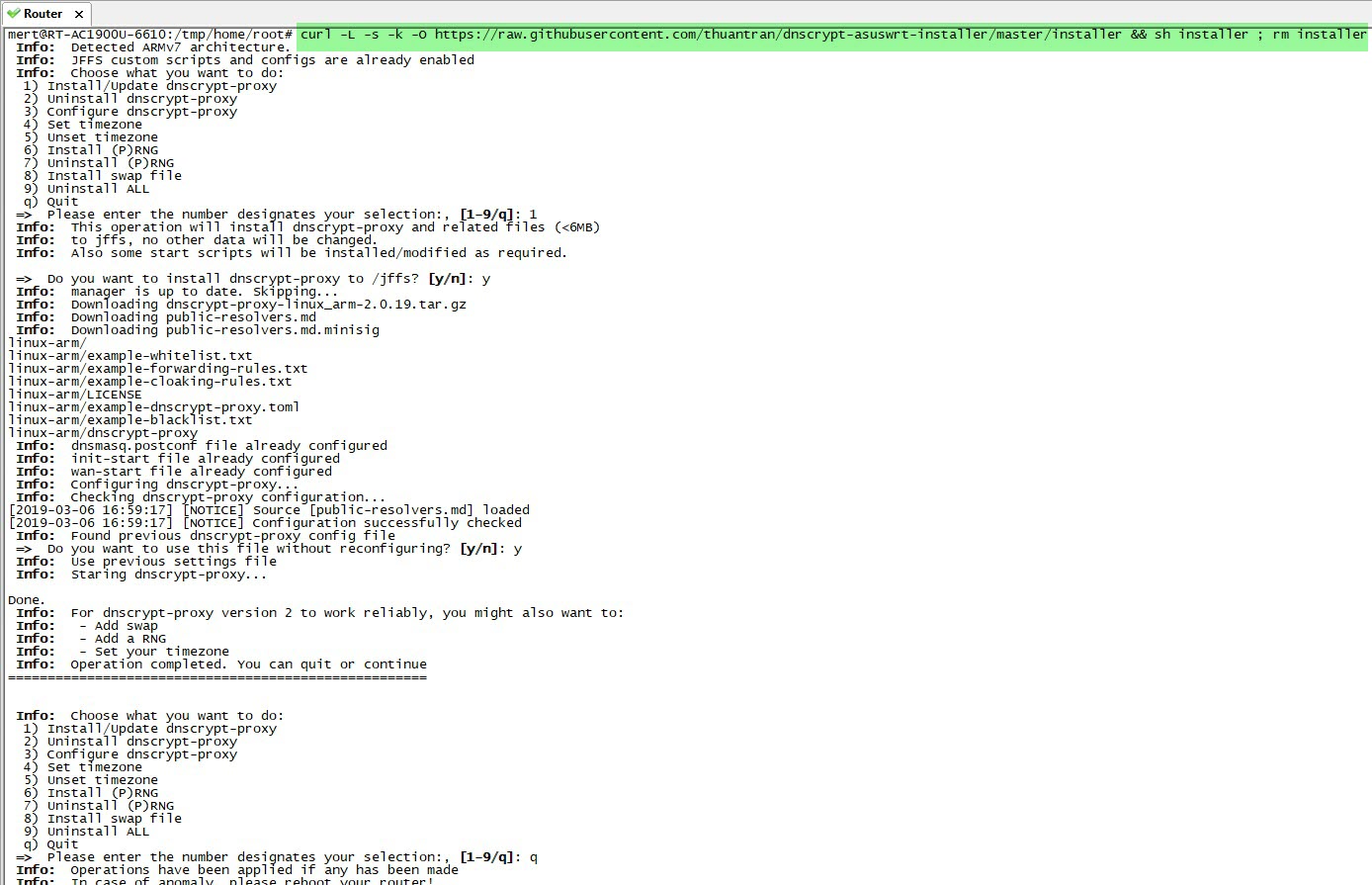
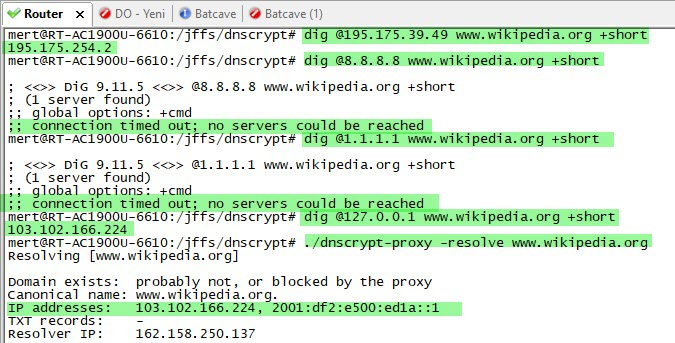
Next, it was time to make all the DNS traffic performed by the router encrypted (Dns over HTTPS – DoH). My first task was to connect a USB disk where I could install and run the packages on the router. Then, I completed the installation quickly by running the command entware-setup.sh in the command line. To install the dnscrypt-proxy tool, which supports DoH, I ran the command curl -L -s -k -O https://raw.githubusercontent.com/thuantran/dnscrypt-asuswrt-installer/master/installer && sh installer ; rm installer and completed the installation. To confirm that the dnscrypt-proxy tool was working properly, I attempted to resolve the IP address of the wikipedia.org address, which is still banned in my country, and I saw that the tool was working successfully.
To take advantage of the router’s capabilities, I decided to test its connection with VPN services (Netflix users will understand the reason well. :)) I decided to subscribe to NordVPN, a VPN service provider that I saw many advertisements for while traveling in the US. I was able to successfully connect to one of NordVPN’s servers by following the steps on their help page specifically created for Asuswrt-Merlin users.
After connecting to NordVPN, I noticed that my internet connection had slowed down to the point where I couldn’t access any web sites. I was thinking “There must be a problem with this VPN server” and “Is this VPN server slow too?” when I realized that I couldn’t connect to any of the 10 servers I connected to. Just as I was about to question NordVPN’s service quality, I remembered reading some messages on social media about claims that VPN services were being slowed down.
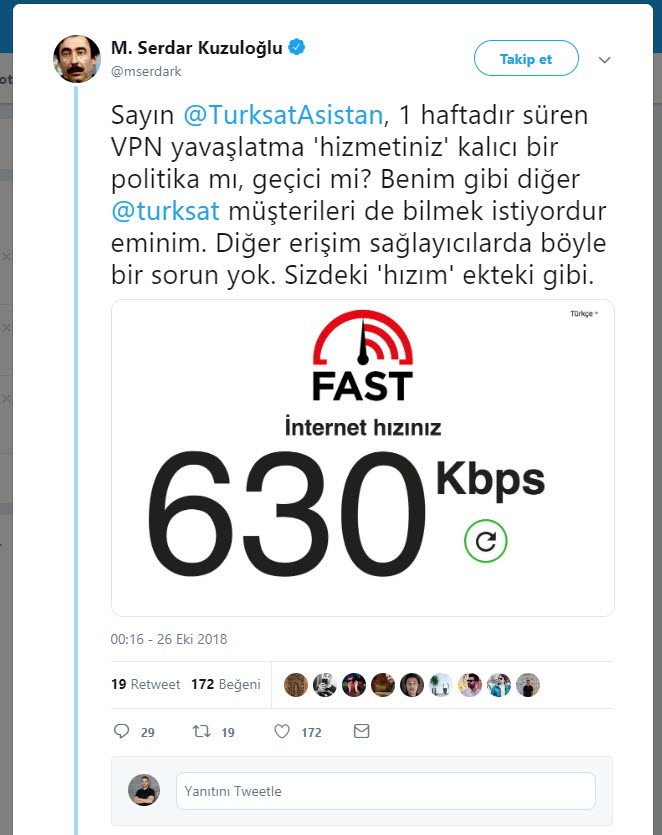
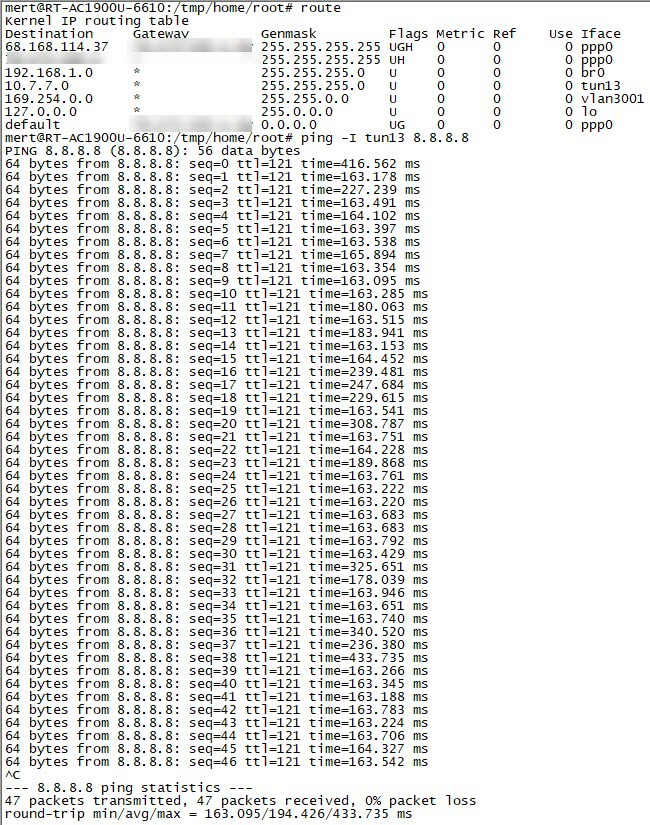
I noticed that when I pinged the IP address 8.8.8.8, which is Google’s DNS server, from the NordVPN servers I connected to, the response times were increasing exponentially.
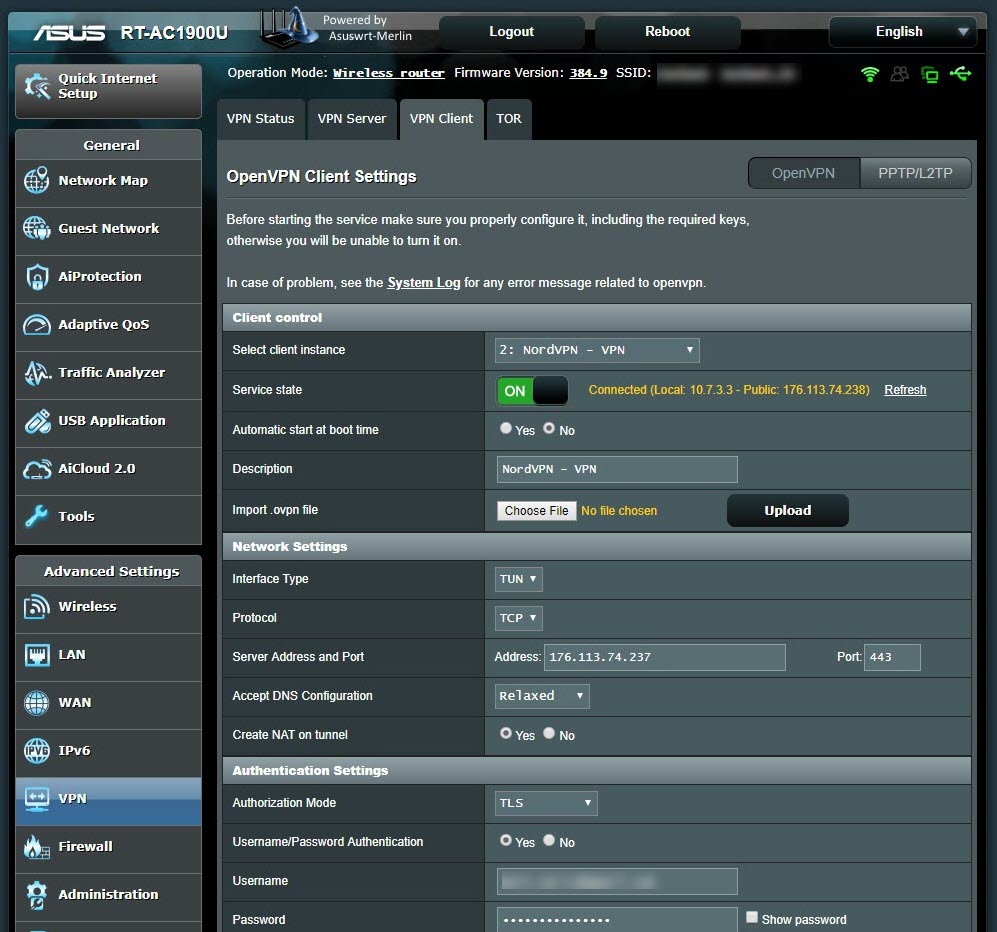
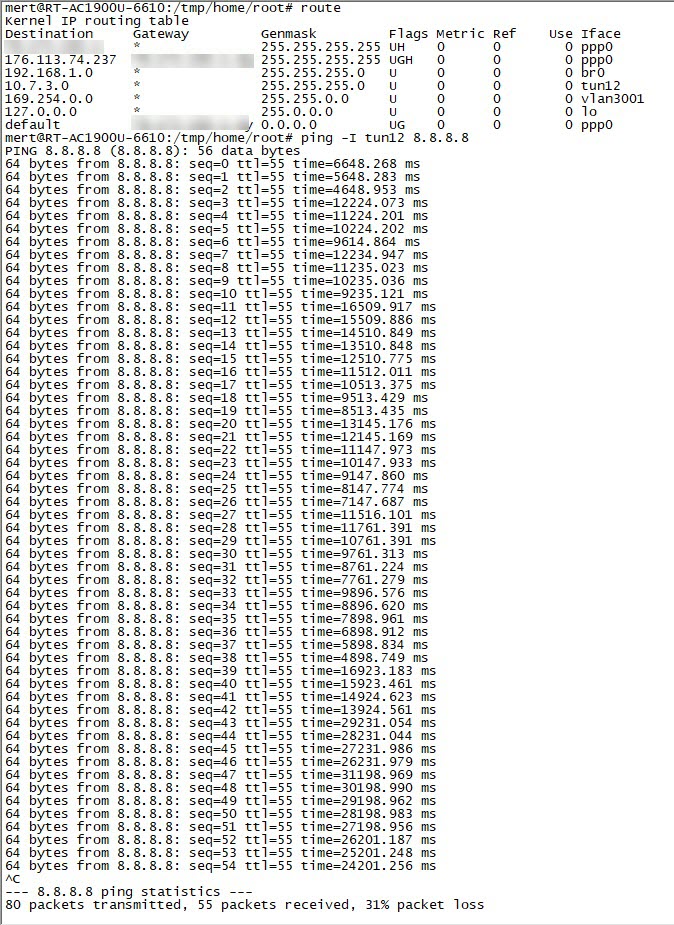
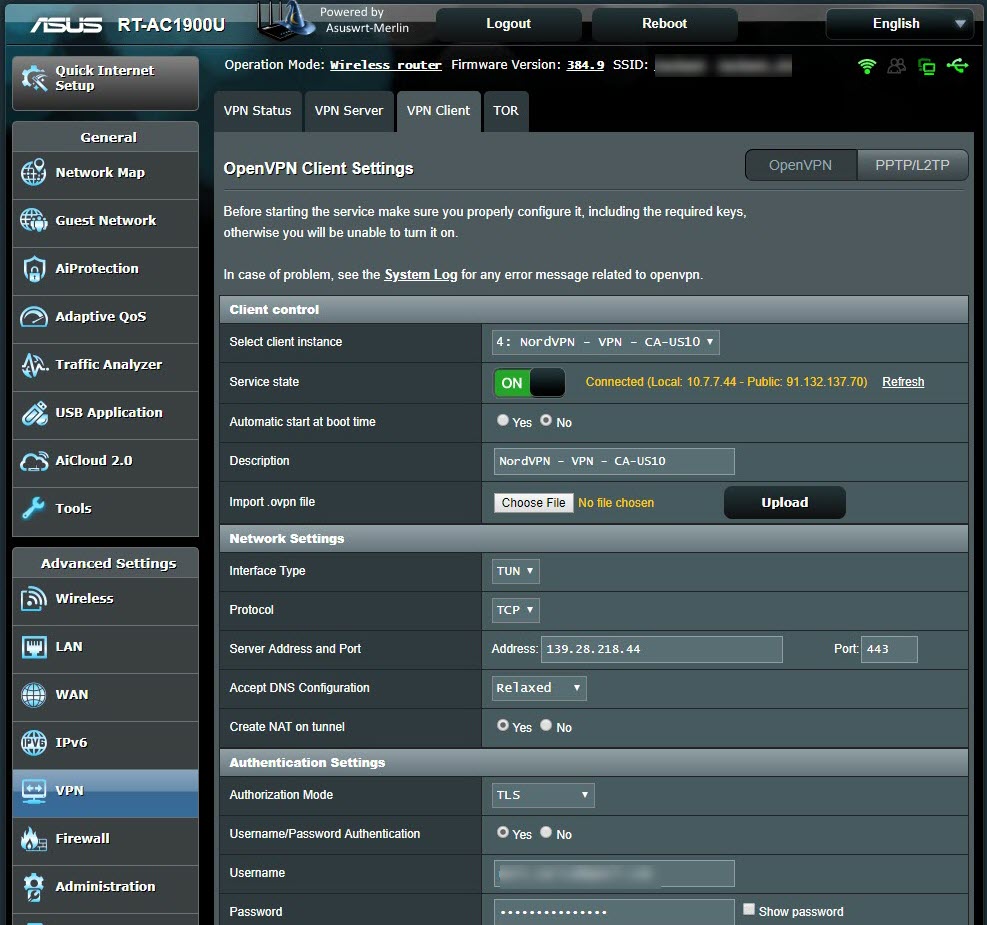
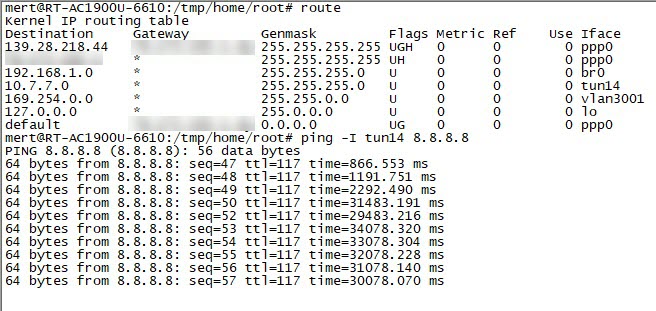
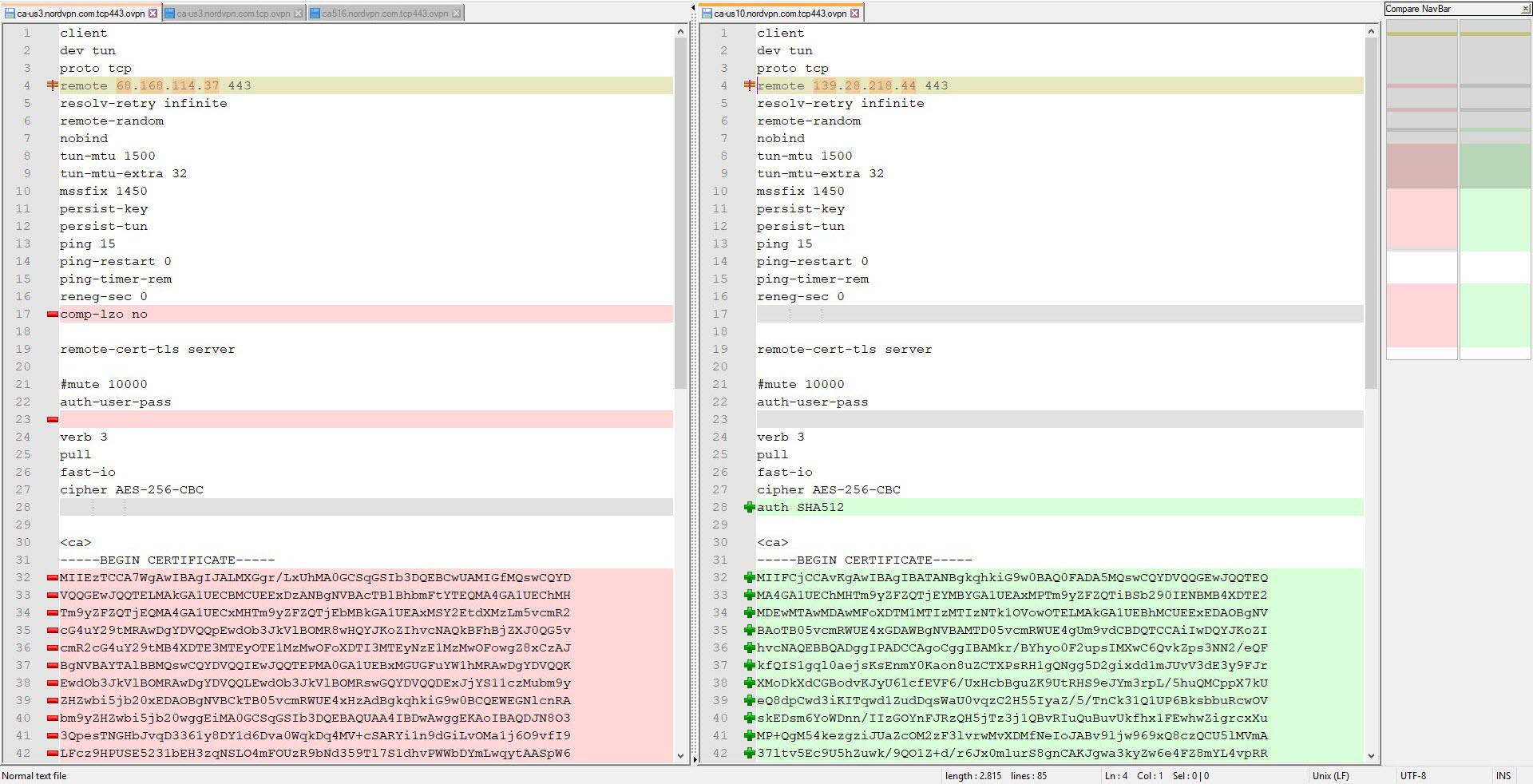
When I connected to one of NordVPN’s servers with the Double VPN feature, I saw that the ping time was much more reasonable and I could access websites. When I connected to another Double VPN server, I again noticed that my connection was incredibly slow. When I compared the OpenVPN connection settings of the two VPN servers, I found that the AUTH parameter (HMAC digest algorithm) used in message verification was different (SHA512 instead of SHA1). When I tried to connect to all NordVPN servers that use the AUTH parameter of SHA1, I found that the connection did not slow down and therefore I believe that the slowdown could be related to the SHA512 algorithm.
When I asked on LinkedIn what could cause the delay in PING times, the general responses were that the line could be saturated, the router in between could be malfunctioning, there could be a problem with the ethernet card, there could be a grounding problem in the local network, the firewall connection list could be full, the system could be under attack. Based on the screenshots I shared and the comments from LinkedIn, I decided to leave it to you, dear readers, to find out what caused this delay as an exercise.
In conclusion, after years of using the Tilgin HG1332 router without choice and complaining, I was finally able to escape and get a new router that I could secure myself, full of security features. Especially with the support of OpenVPN, when I want to take advantage of free public WiFi services in public places like shopping centers, hotels, cafes, airports, etc., which are free but pose a risk to users in terms of information security, I can connect to my router at home securely via VPN from my computer or mobile phone, and minimize that risk, which made me very happy.
Hope to see you in the following articles.