Exposing Pig Butchering Scam
Over the years, as I have been targeted sometimes directly (LinkedIn Scammers, Sponsored Scamming) and sometimes indirectly (Who Viewed My Profile?) by scammers, I have made it my duty to write about these attempts in blog posts and warn those around me about them. At times, I have even received messages about scams from my spouse, friends, and close ones and have tried to write about them (Instagram Scammers) whenever I get the chance. And now, I am here again with a new scam attempt to expose.
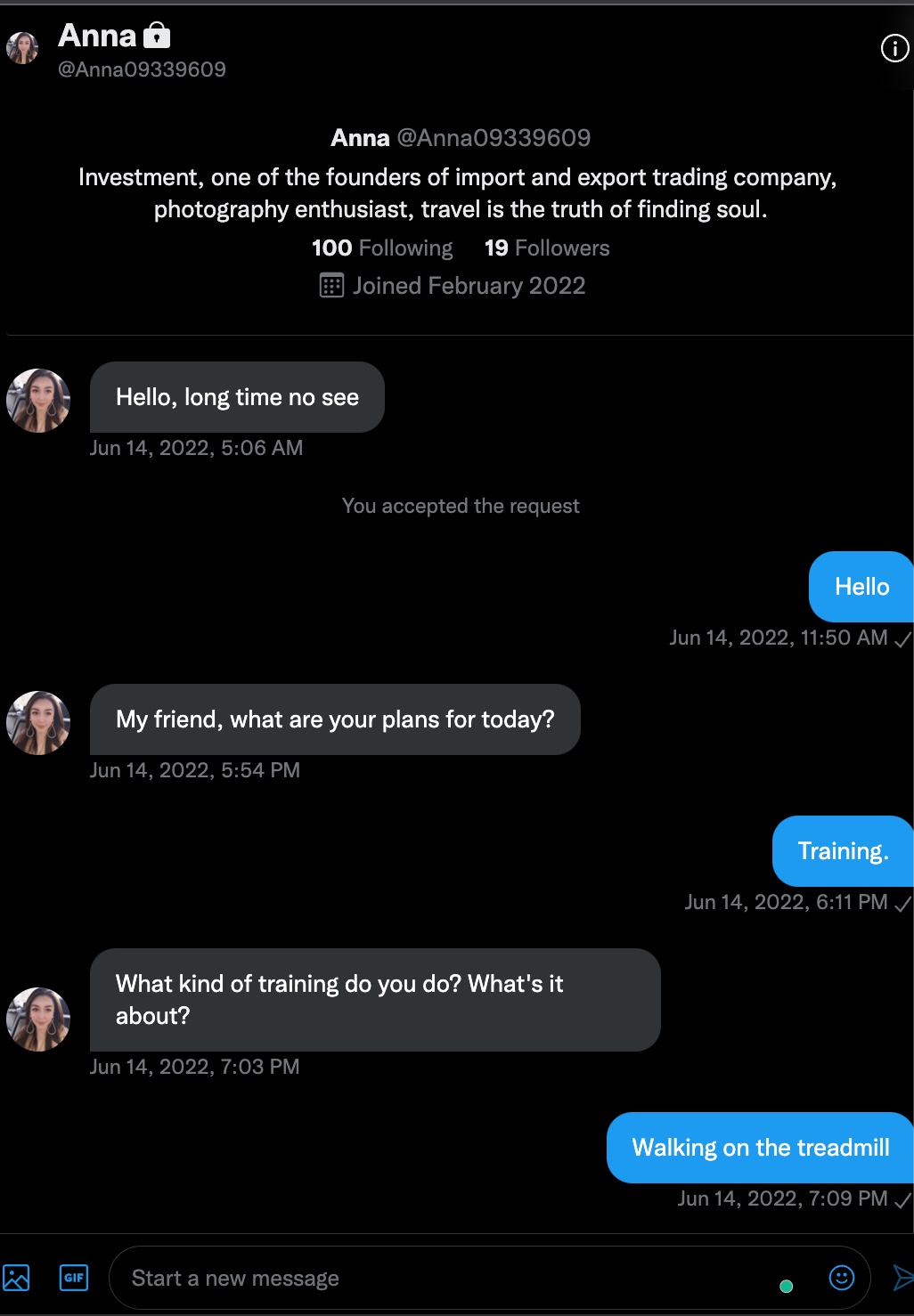
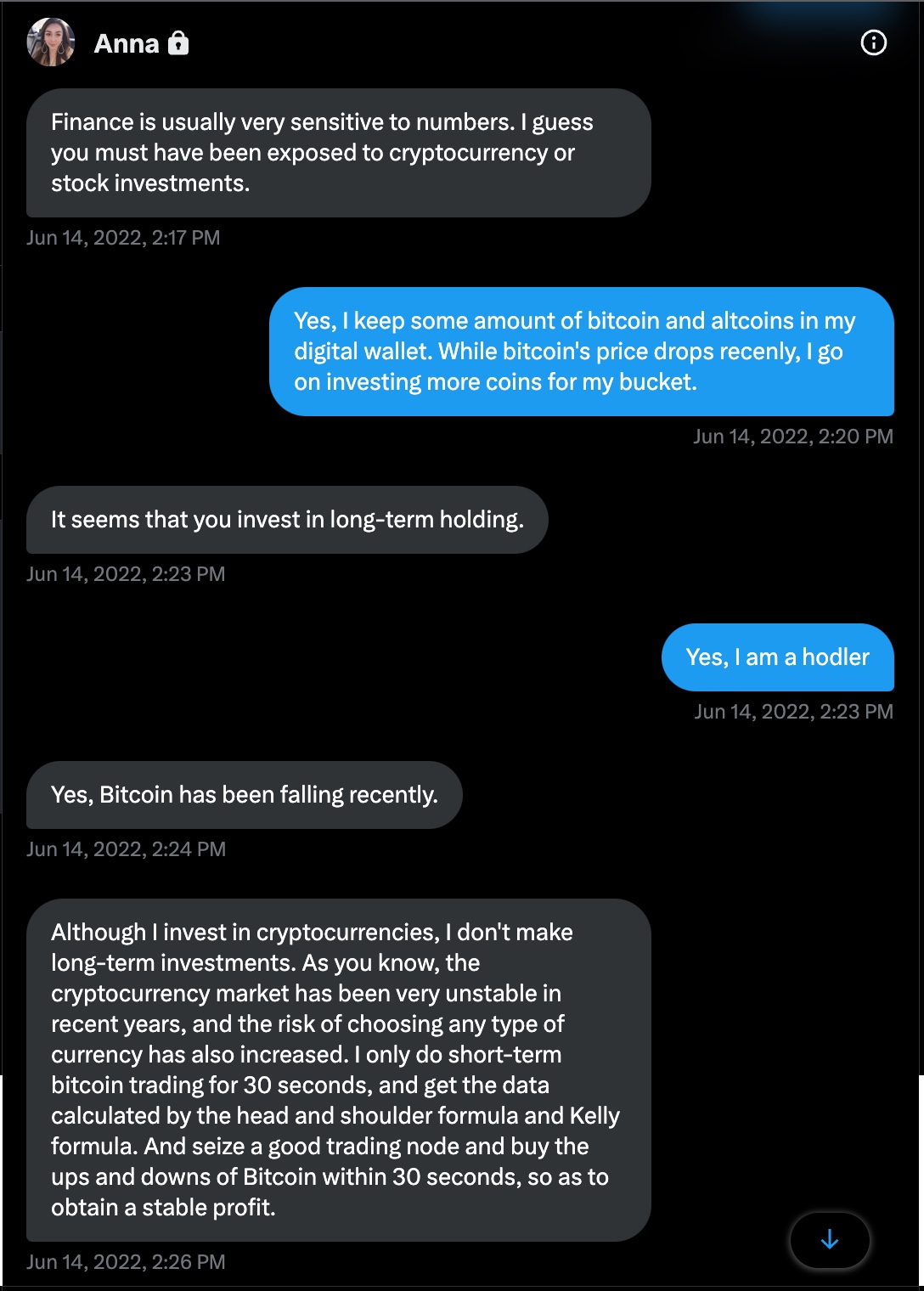
As I announced through my Twitter account in June 2022, this attempt started with a message from a protected Twitter account named Anna on June 14, 2022. In this message, Anna started the conversation by talking about how she hasn’t seen me in a long time. After learning my name (Mark *fake*), where I live (a Belgian living in Turkey *fake*), and what I do (CFO of a FinTech company *fake*), the topic shifted to where I invest my money and the loss of value of Bitcoin cryptocurrency at that time.
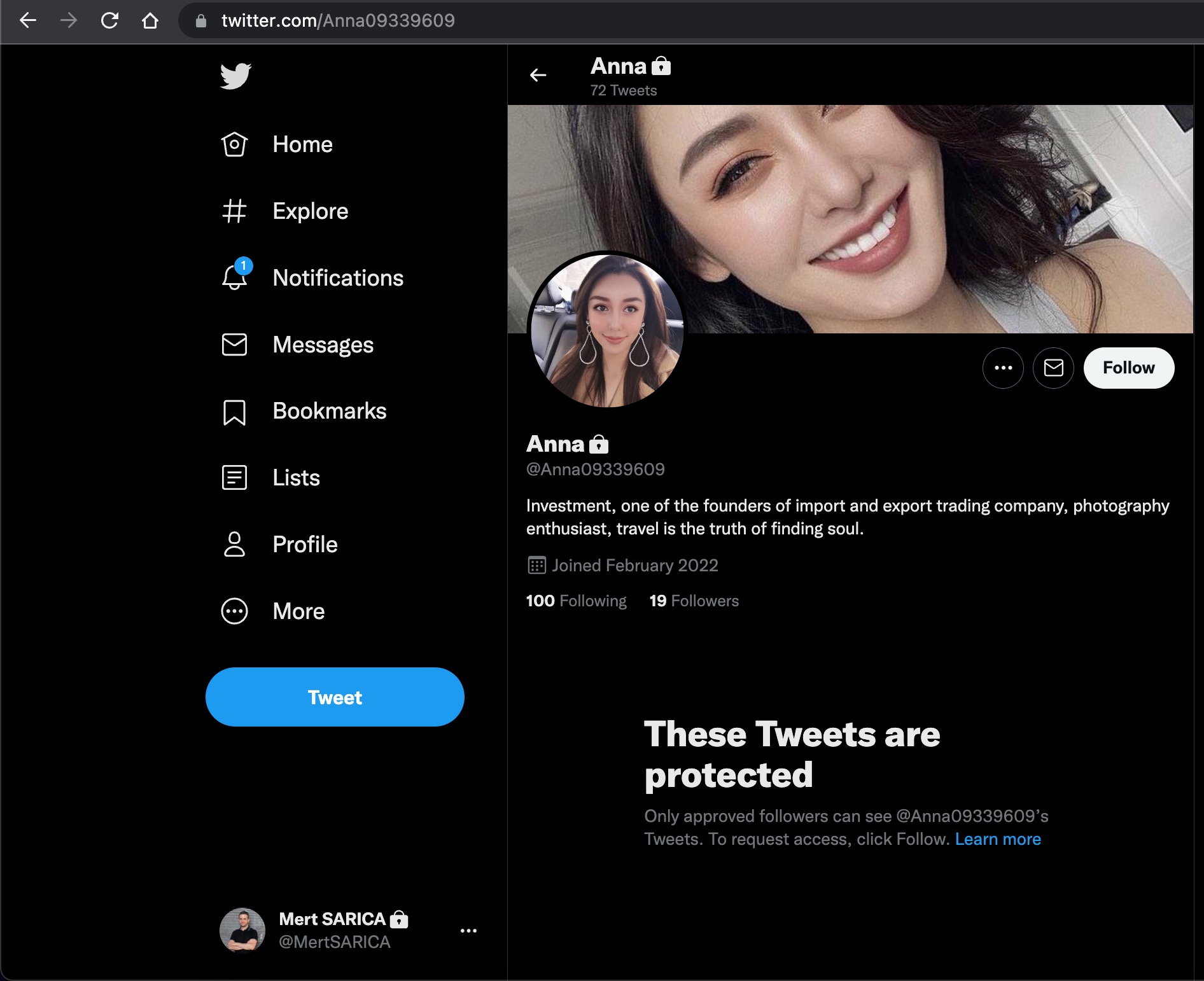
I took a break from the conversation and decided to find out who the photo on Anna’s profile really belonged to, as I suspected it was fake. To do this, I used the Visual Search feature of the Yandex search engine and discovered that the profile photo belonged to a Chinese person named Shasha Zhao. When I looked at the photos shared on Shasha’s profile, I found the exact photo on Anna’s profile.
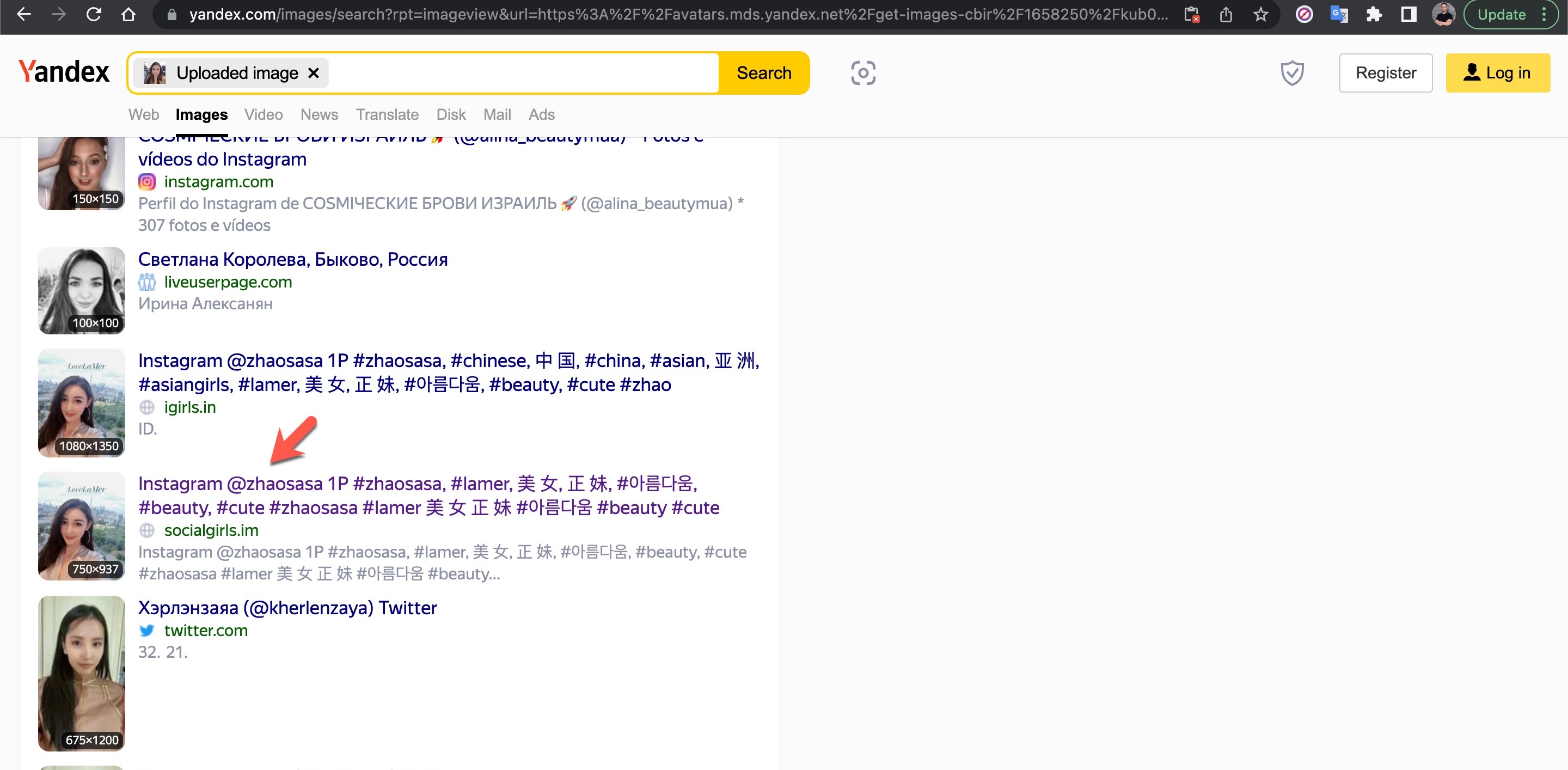
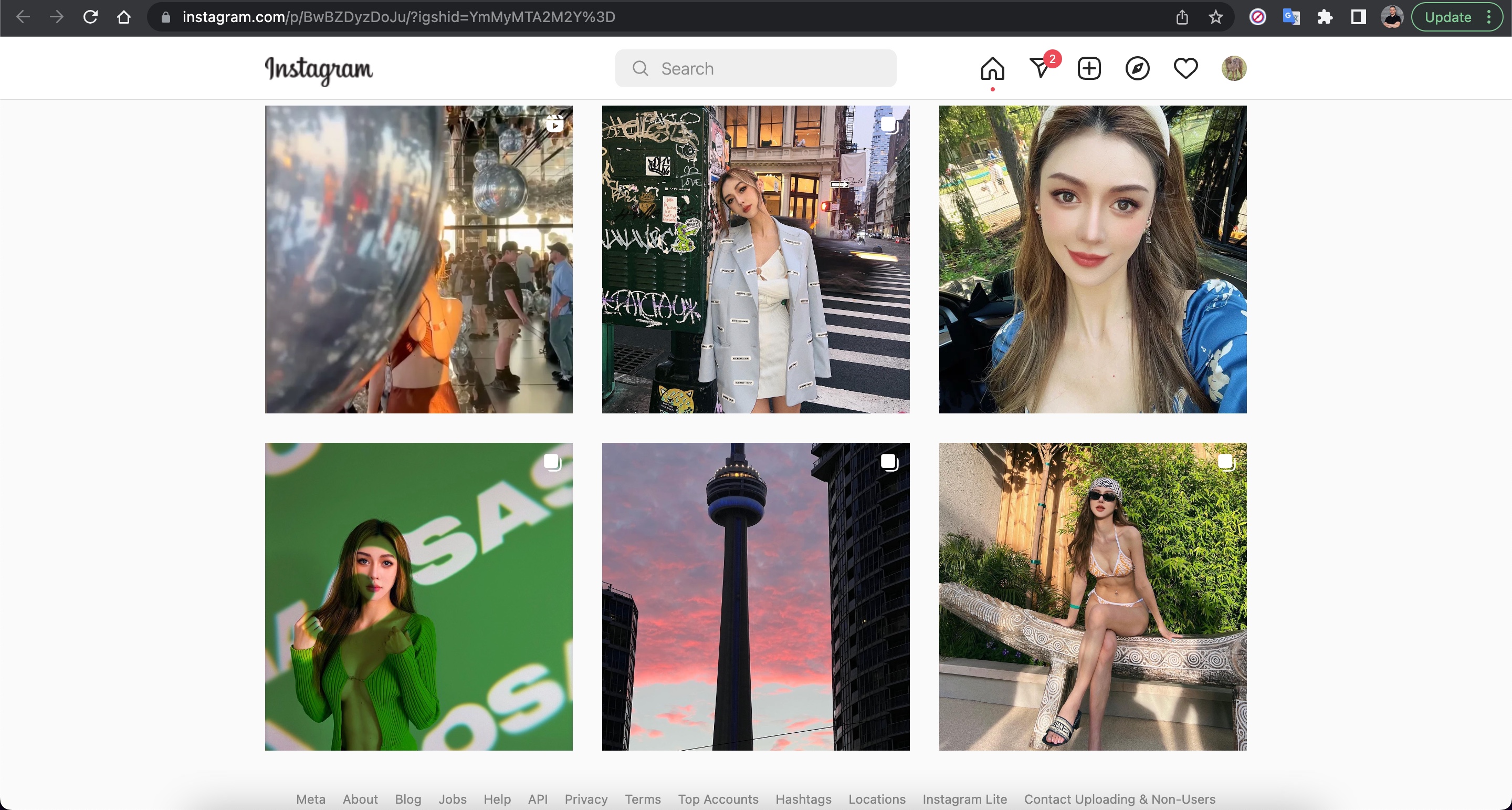
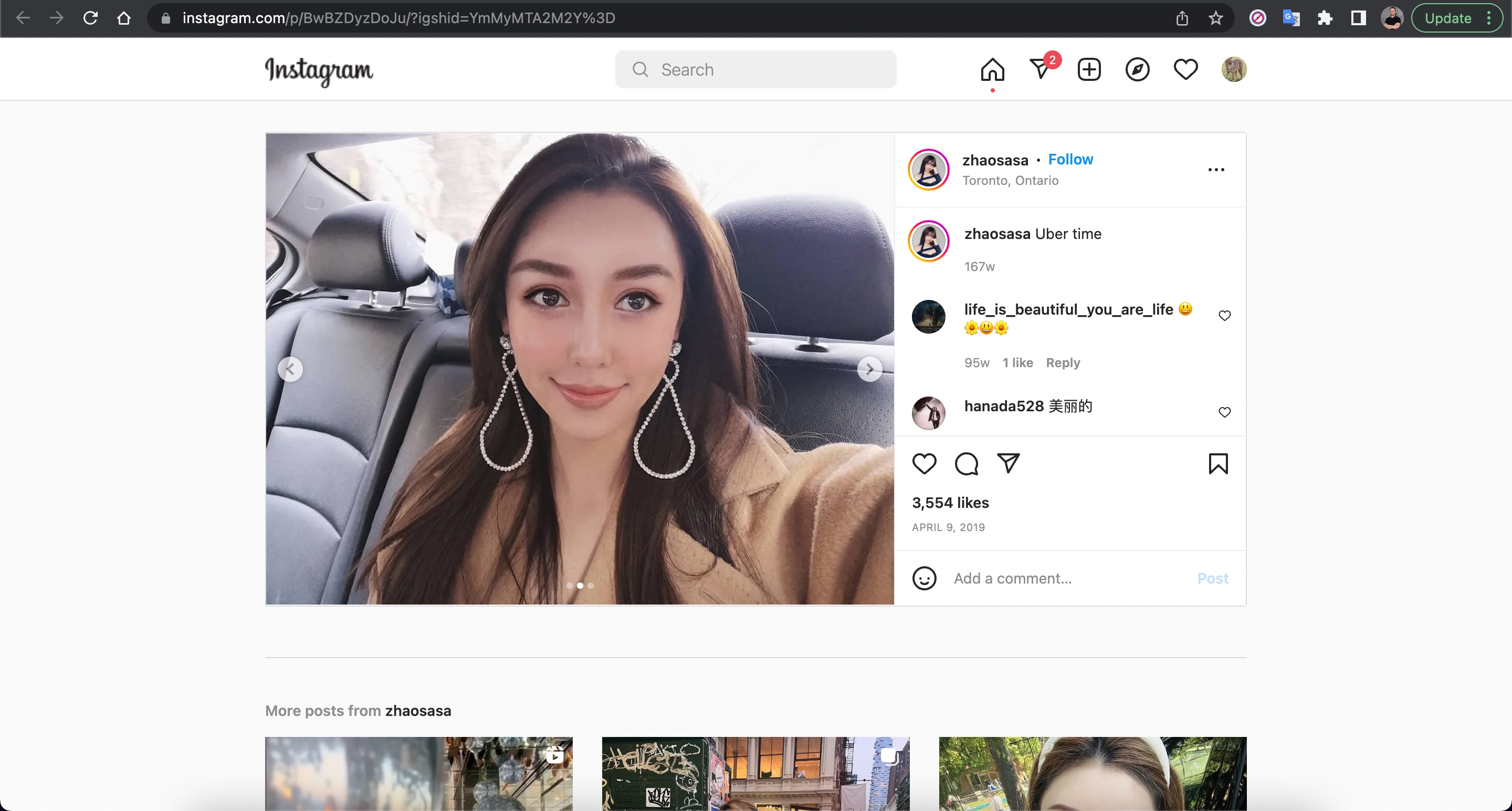
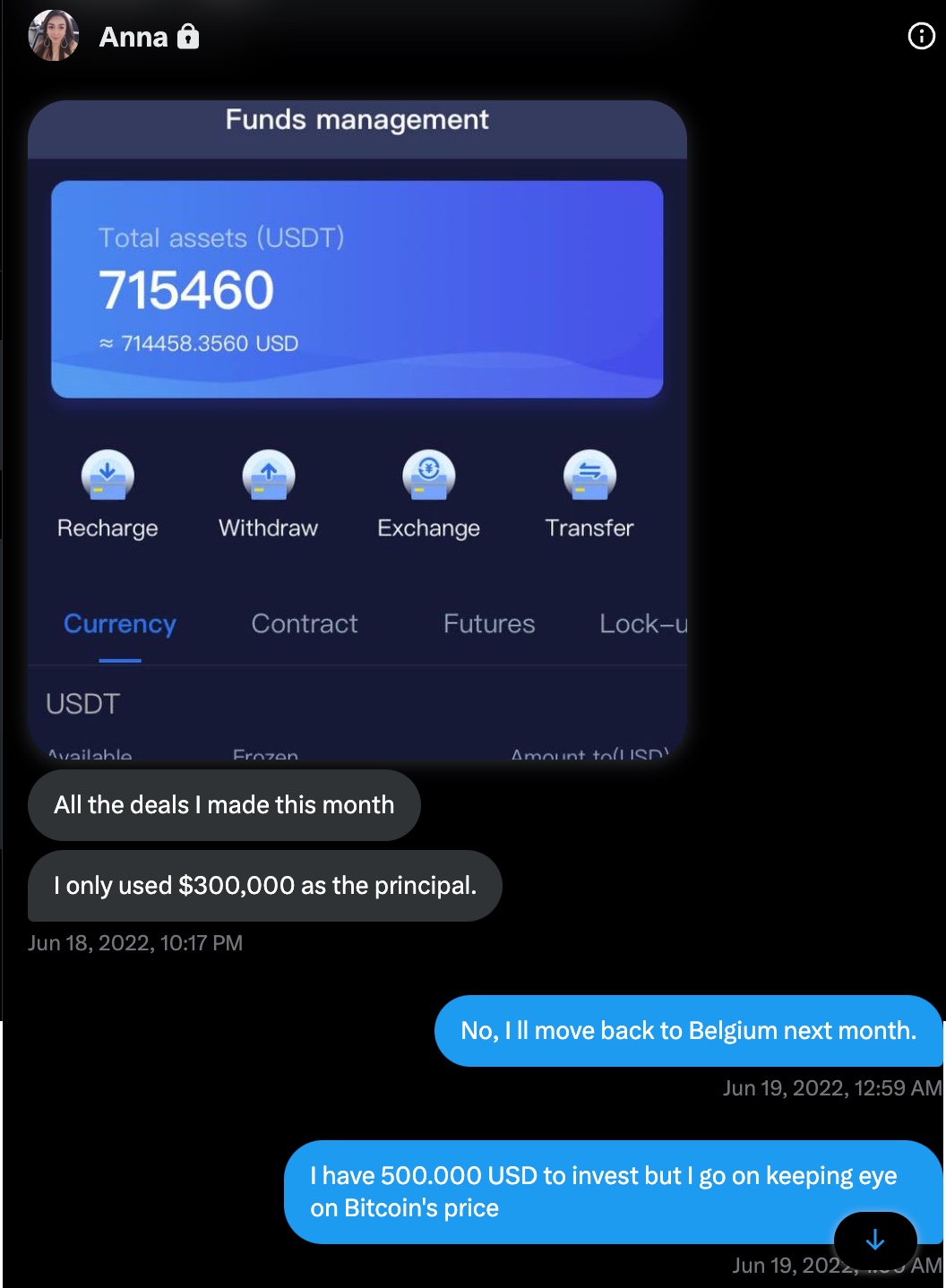
Anna, who initially claimed to live in Singapore and founder of a garment import and export trading company, asked to continue the conversation on WhatsApp and shared a US phone number (+19295654212) with me. When I questioned her about using a US phone number, she changed her story, saying she lived in the US for business reasons. To pique my interest, she then claimed to have made a profit of around $715,000 from a crypto investment of $300,000. I informed her that I was considering investing $500,000 to see her tactics for quickly making a profit.
After sharing that I consider her to be a very good investor and want to invest with her, she told me that I need to enter the MonexCrypto platform for short-term investments. She also shared that I need to visit the https://app[.]monexcrypto[.]net address, download the mobile application, and register.
I went to the website to download the mobile application and when I looked at the source code of the webpage, I found out that there was both an Android (update.apk) and an iOS version of the app. After uploading the Android app to VirusTotal and Pithus, a mobile threat intelligence platform, and quickly checking the somewhat suspicious results, I decided to thoroughly examine the version developed for the iOS operating system.
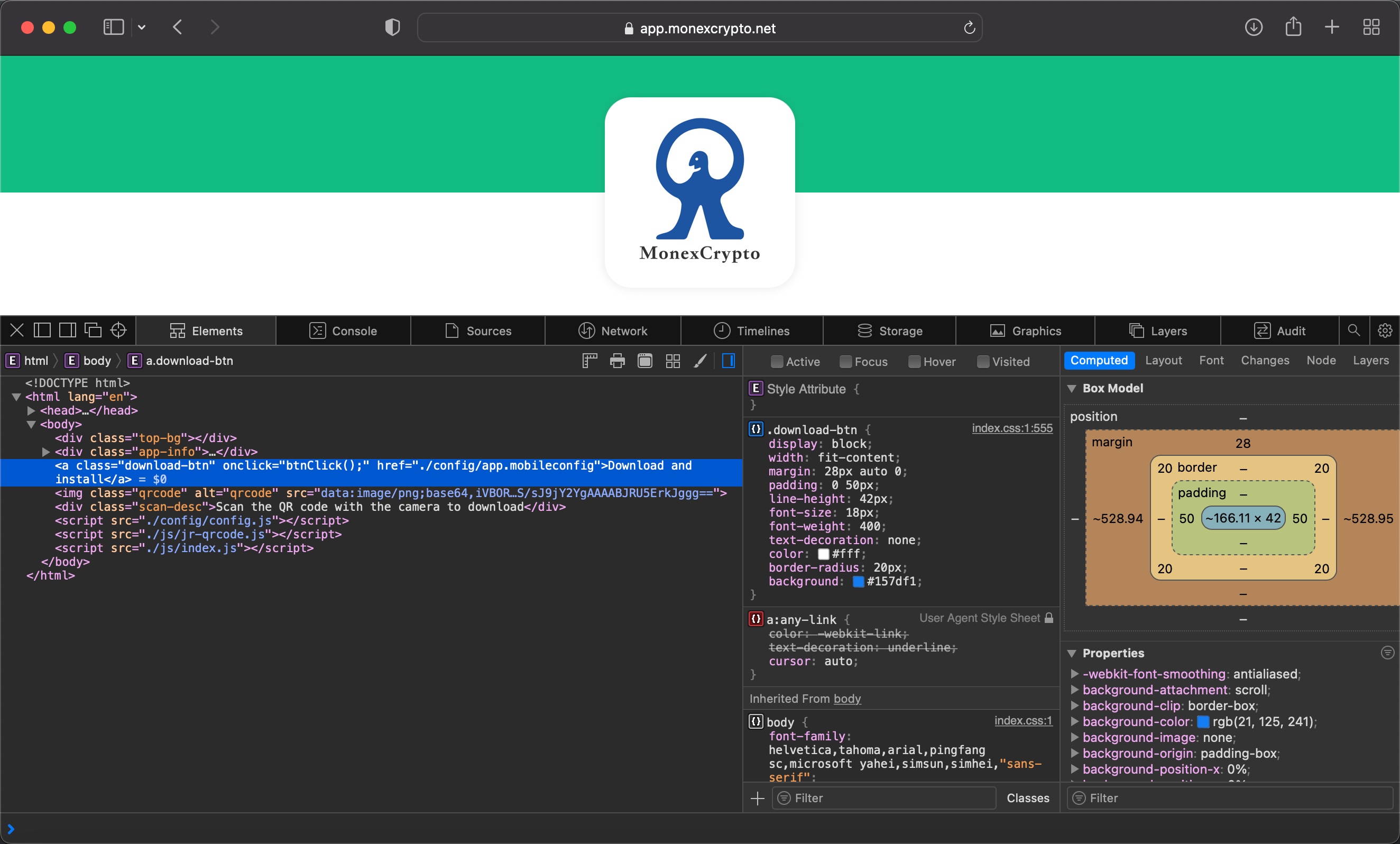
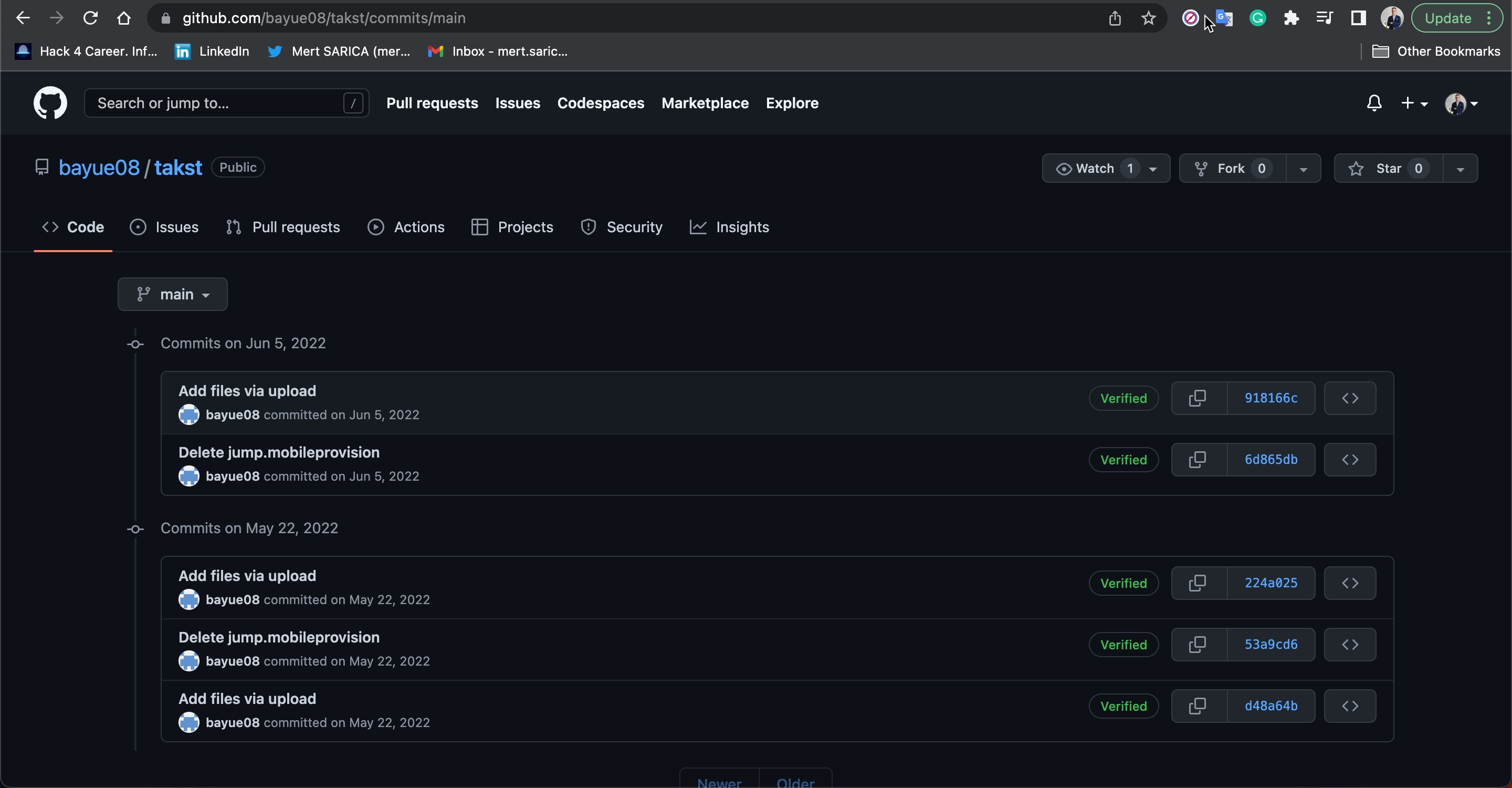
After seeing that the mobileprovision file, which enables third-party applications to run on the iOS operating system, is stored on GitHub, I viewed the information about the developer/company (QuanLi Network Technology Co., Ltd. (SRD7J8LLBV)) registered in the Apple Developer Program.
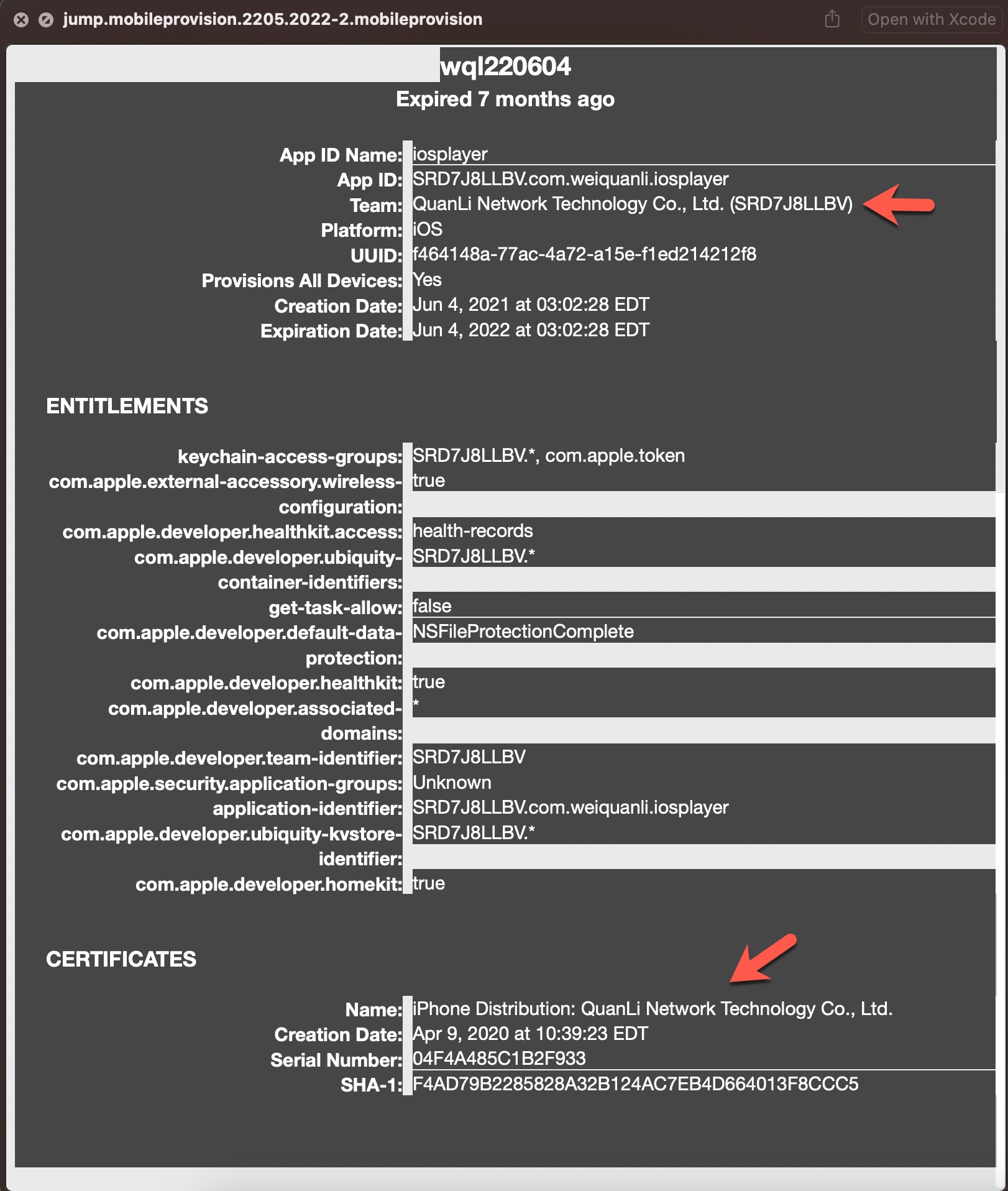
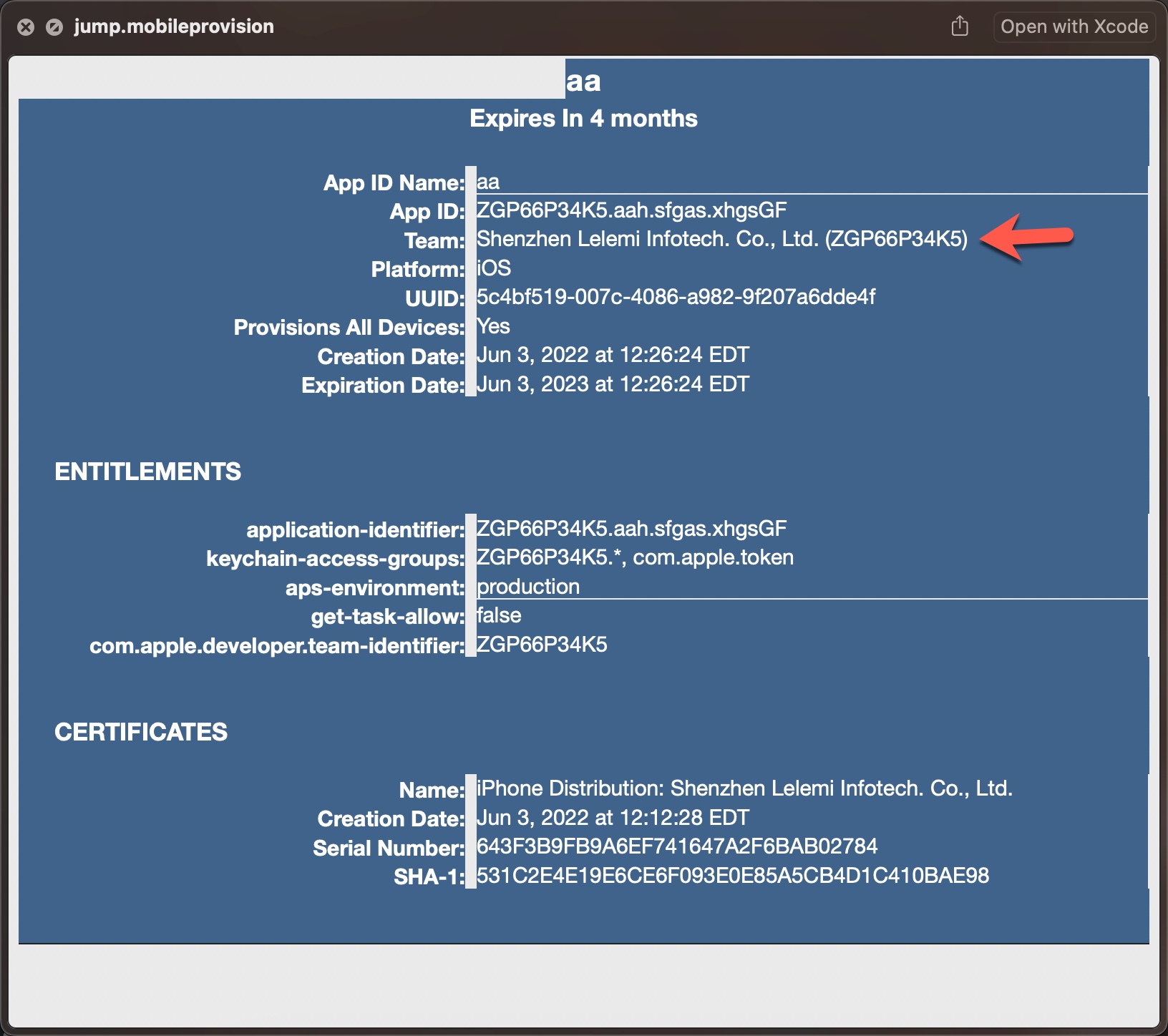
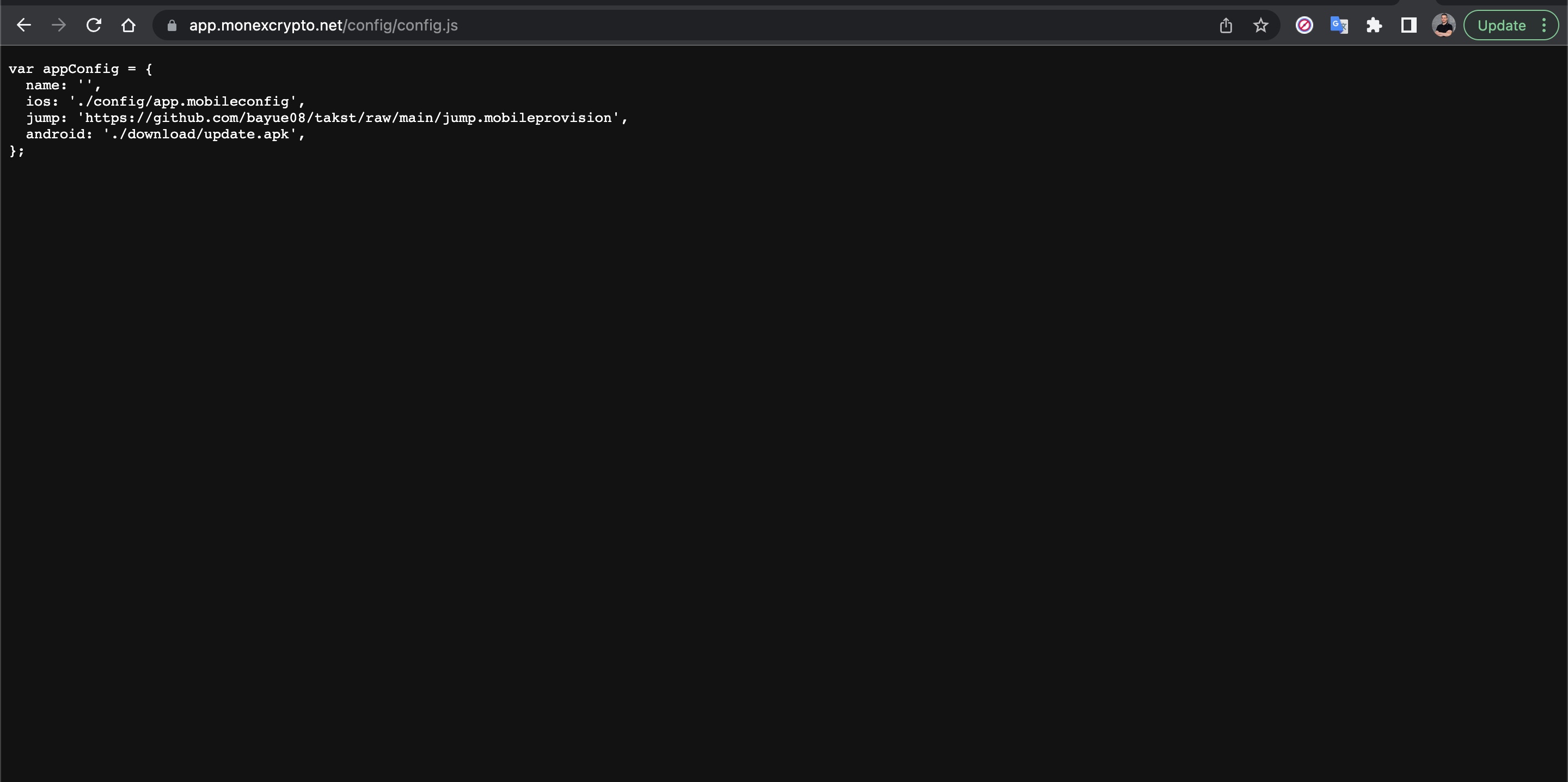
I examined the app.mobileconfig XML file, consisting of payloads that load settings and authorization information onto Apple devices. When I ran the file in the Simulator application located in Xcode, I learned that it is a Web Clip (WebClip) that opens the https://www.monexcrypto.net web page and is signed by a developer named Gang Dai.
Web clips: A web clip is an icon on the device Home screen that links to a website or URL. Web clips can optionally launch full-screen web apps and can run offline using HTML5 local storage. Configuration profiles can include web clips that use a custom title and icon, and can optionally be nonremovable. Web clips can point students to specific websites for educational purposes. For more information about configuring web clips on a device, see WebClip profile page in Apple Developer documentation.
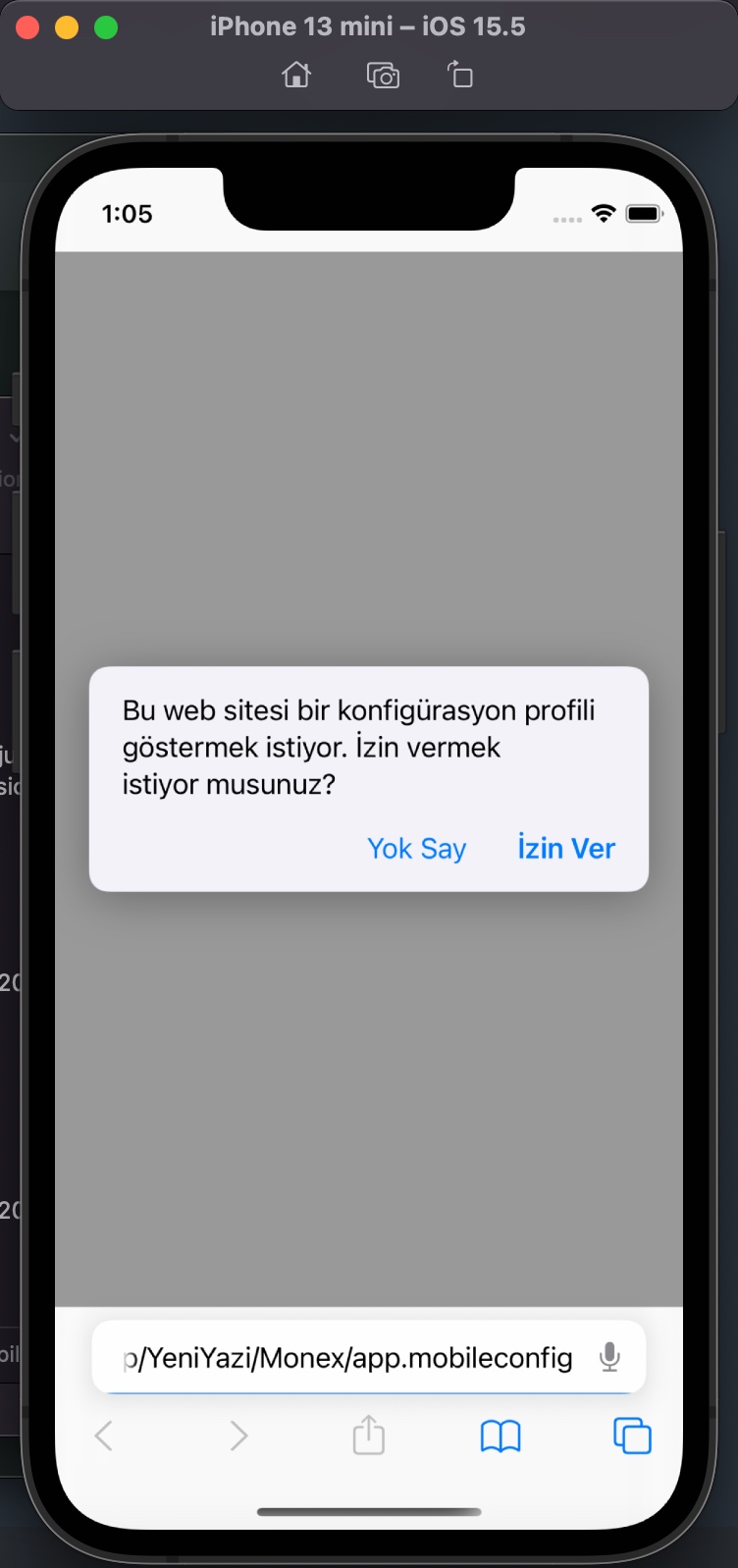
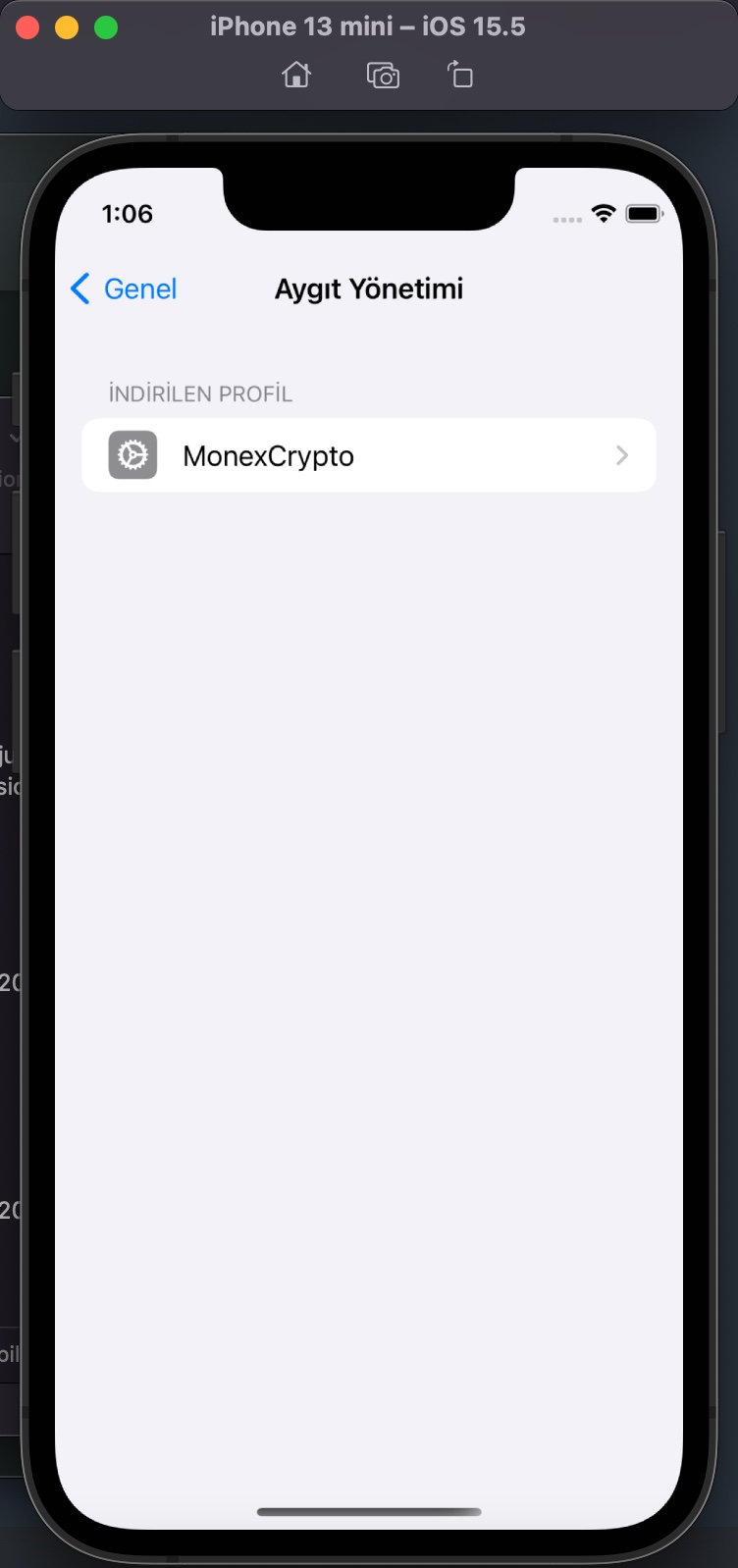
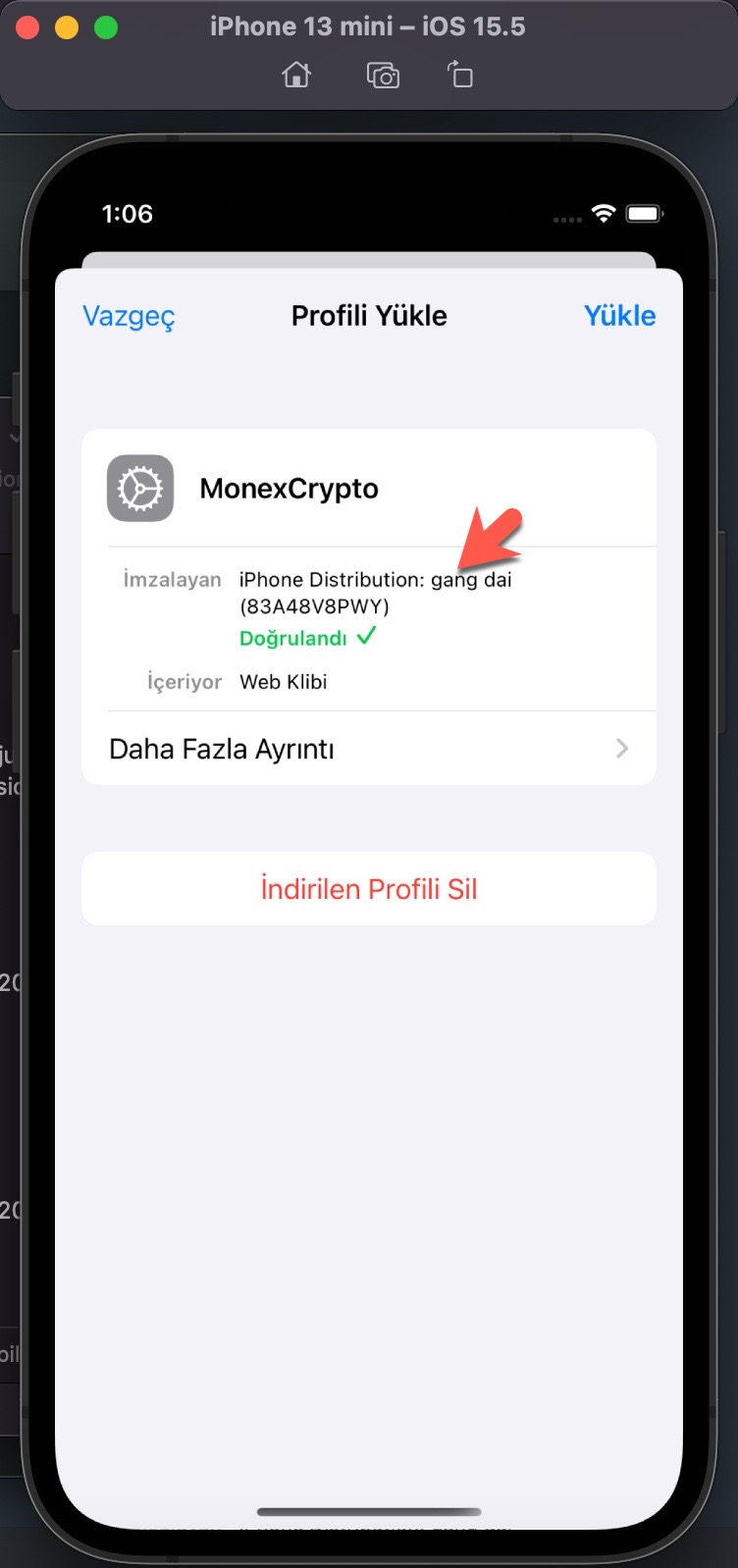
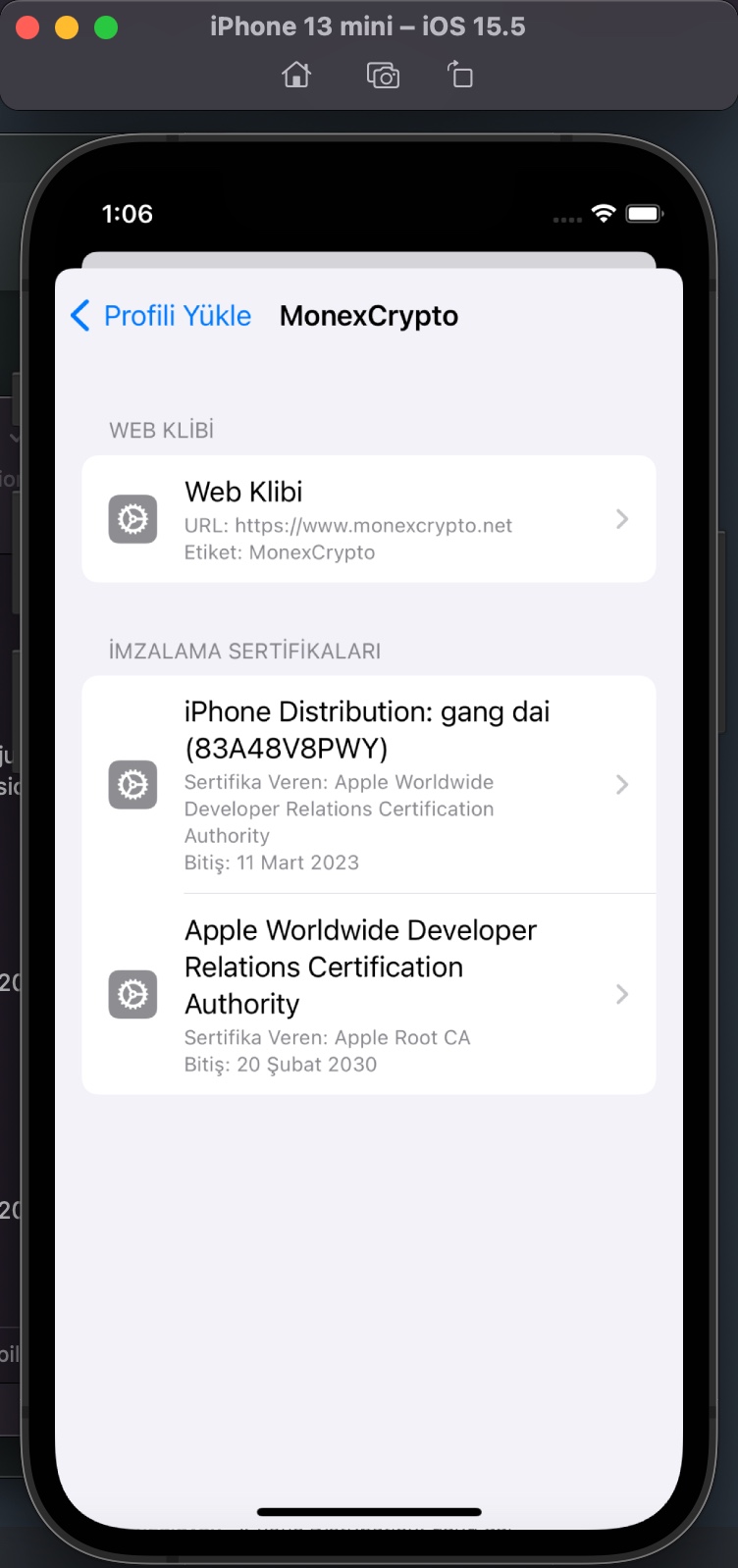
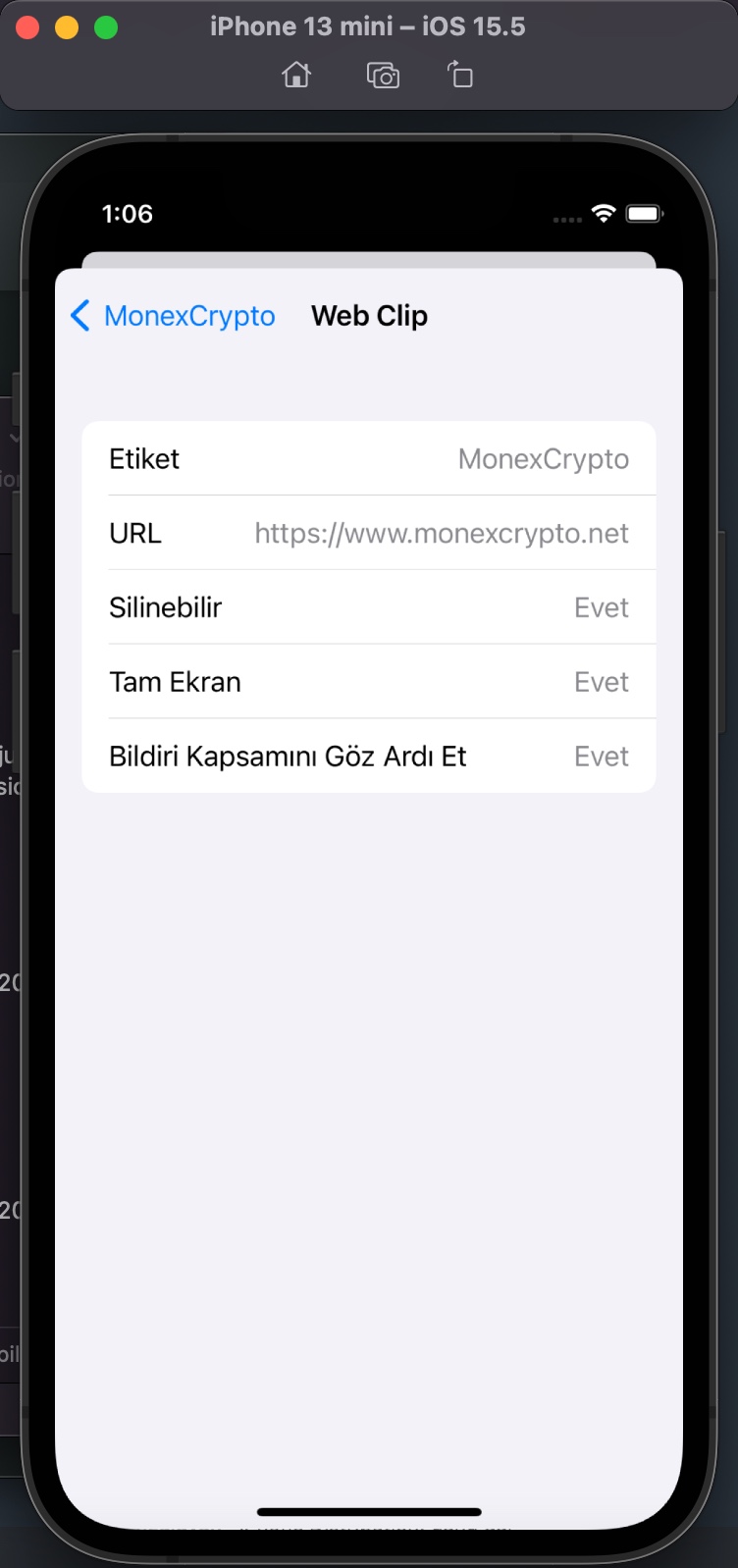
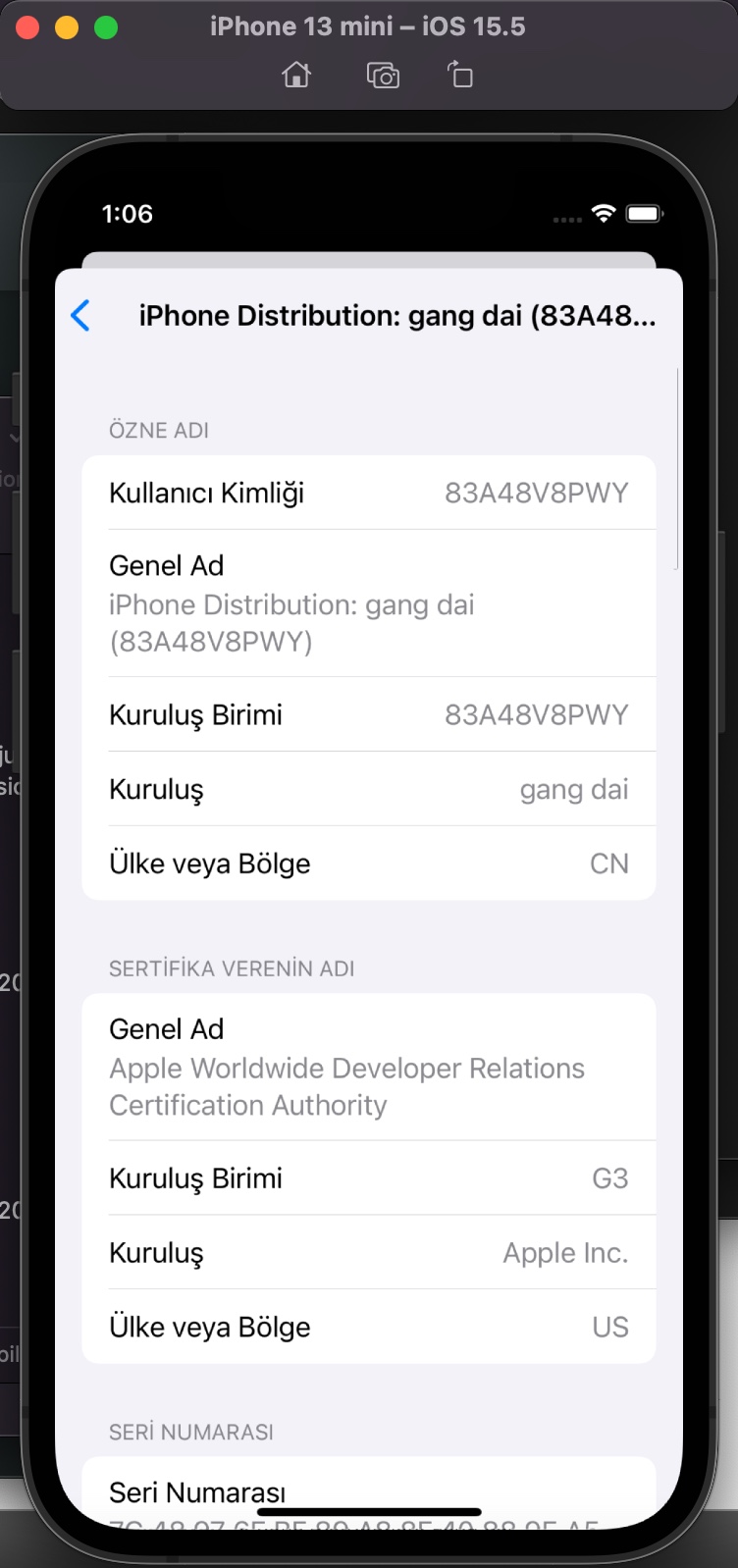
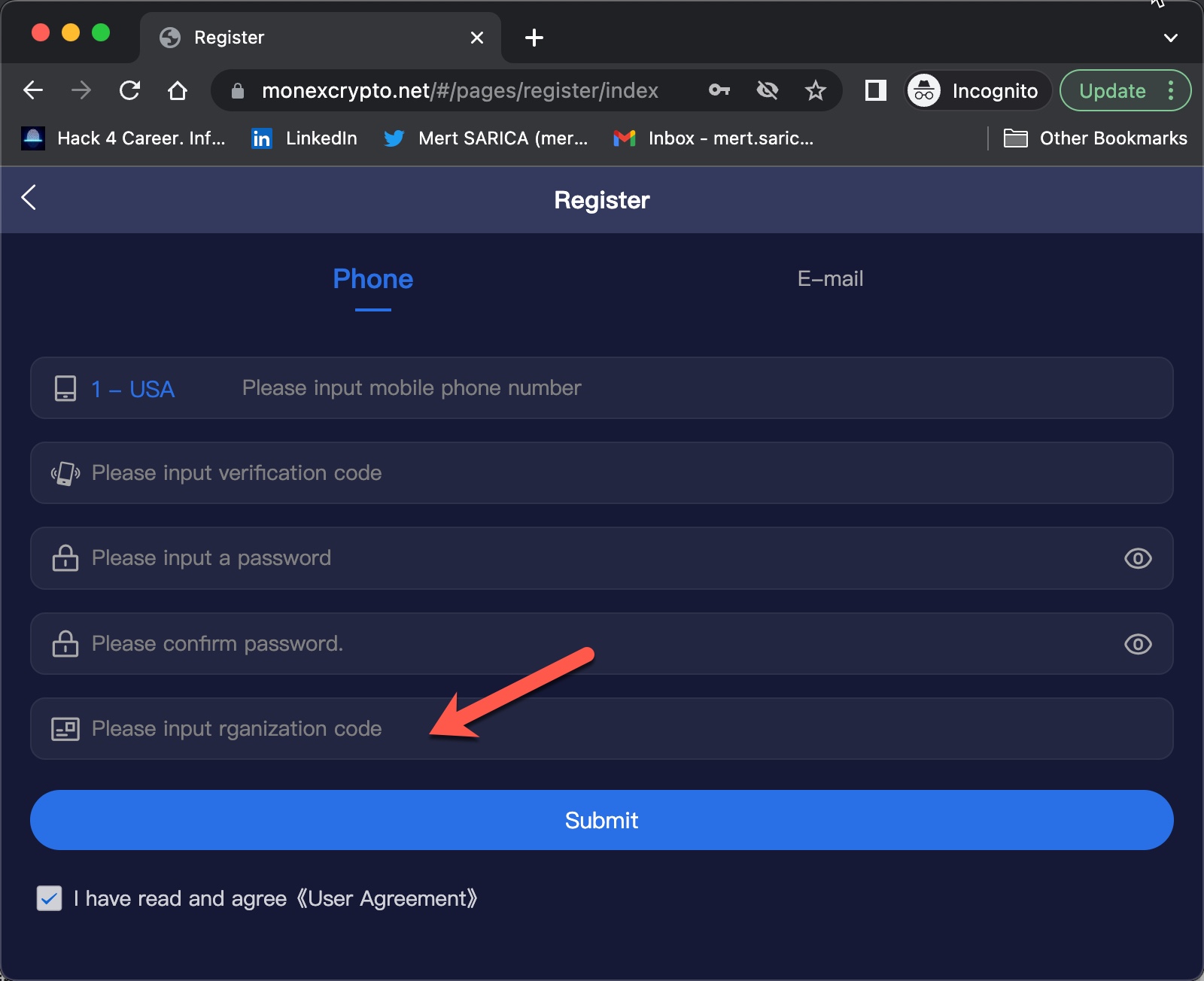
When I tried to register on the website, I was expected to enter an Organization Code in the registration form. The purpose of placing such a code in the form by scammers was probably to prevent cyber security researchers and/or cyber security vendors from detecting this page and collecting information, and they had been successful until now. Whenever I told Anna that I was having issues in the app installation, she kindly did everything she could to help me with screenshots. So I decided to ask Anna for help one more time in finding out the organization code. :)
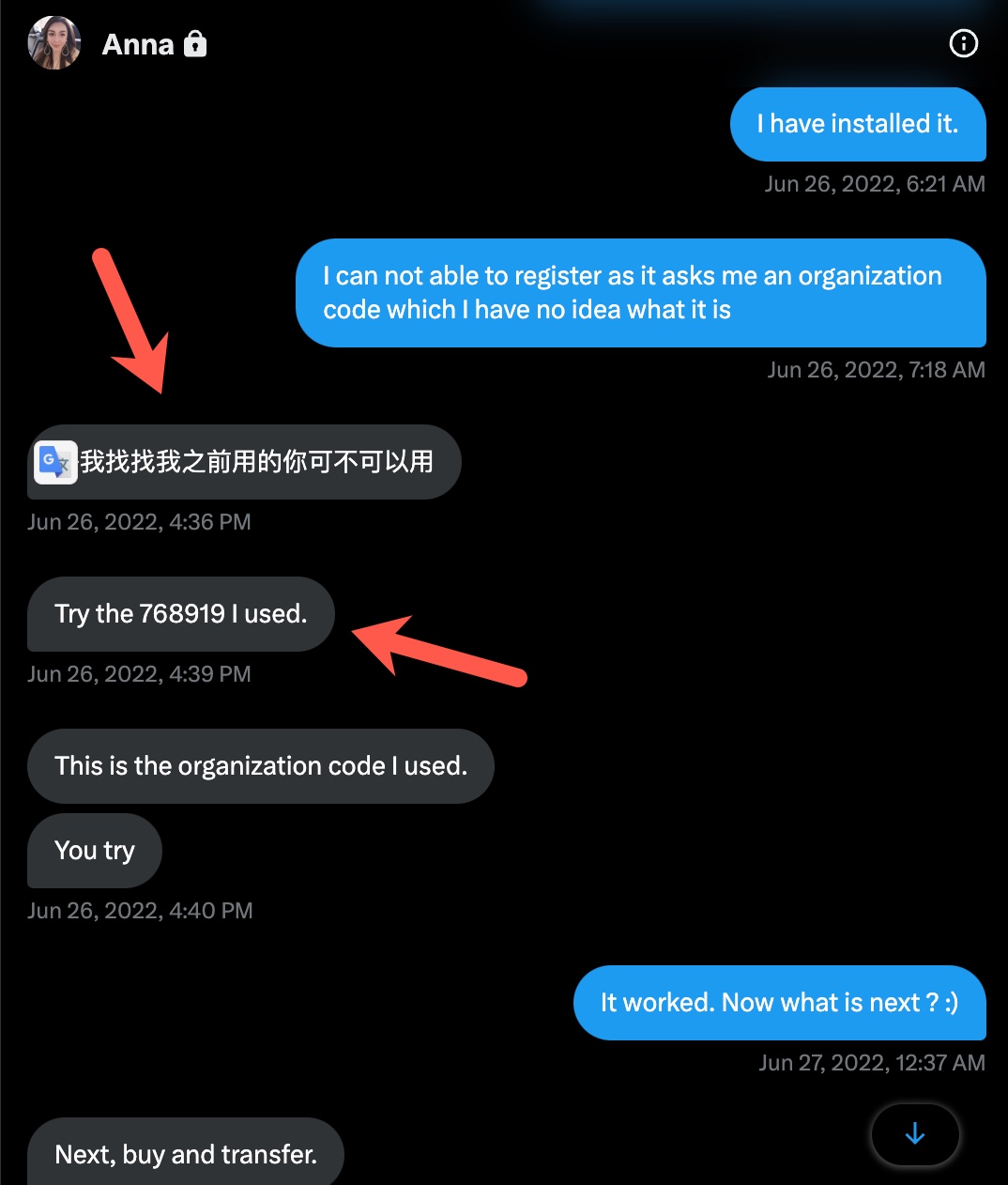
When I asked her the organization code, she first wrote Chinese words (probably she was communicating with me using a Chinese-English translation service), then she shared with me the code (768919) that I needed to enter into the form.
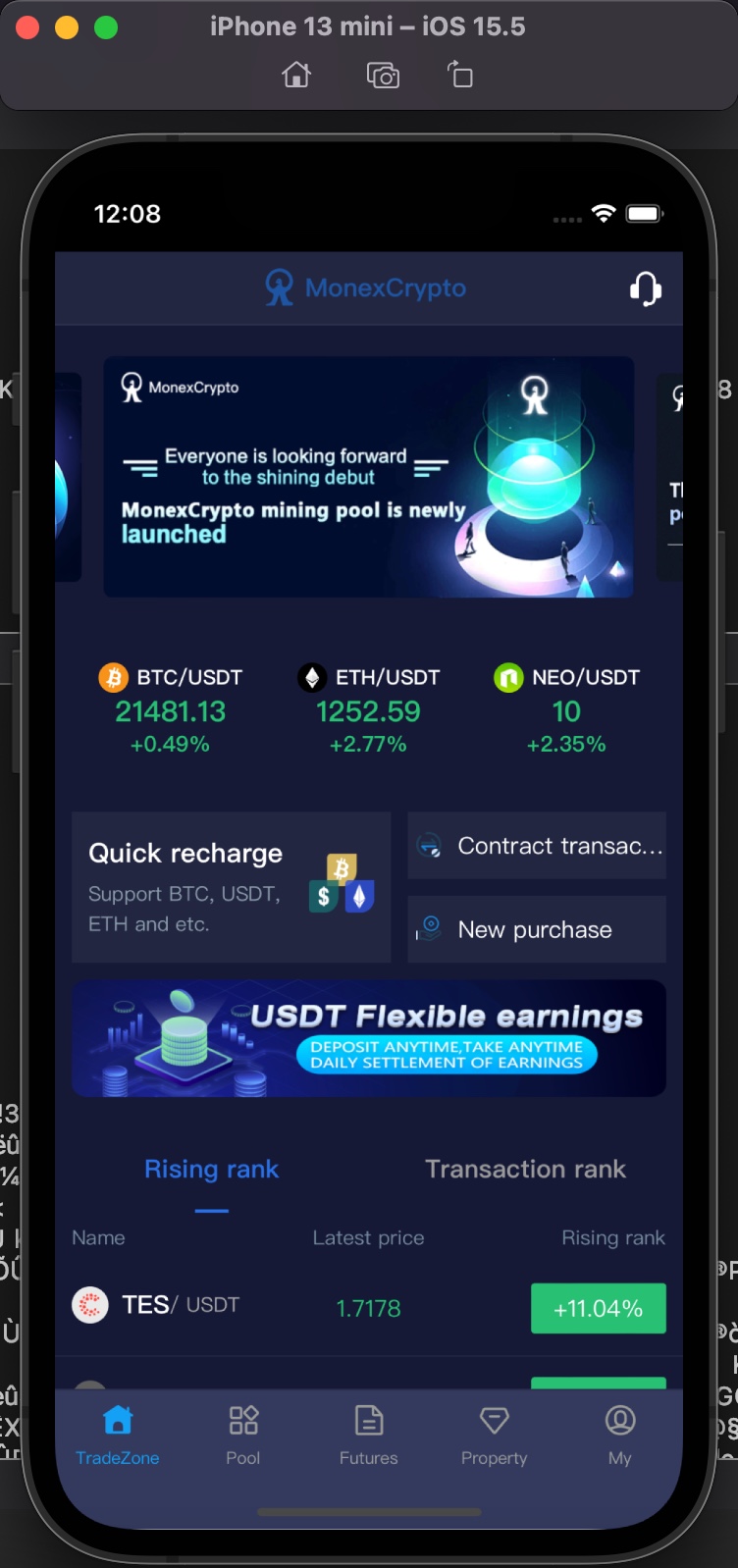
When I successfully registered and started browsing the website with Web Clip, I saw pages and menus about real-time market tracking, depositing money into the wallet, withdrawal, etc.
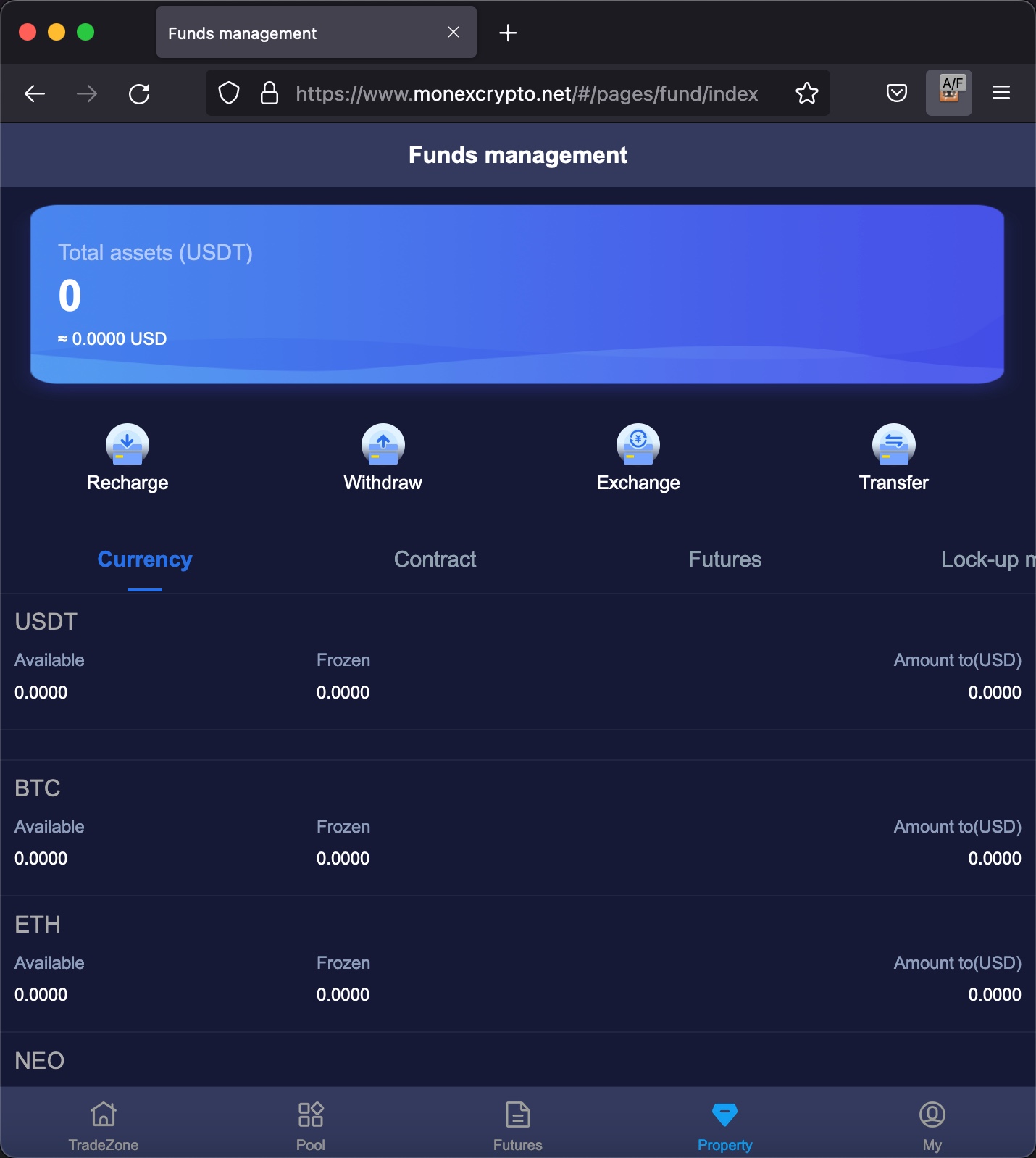
Later, I visited the Recharge page, which I thought could be the ideal place for scammers to trap their victims, as the page for depositing and withdrawing cryptocurrency. Like other exchanges and platforms, when I visited, I was presented with the addresses of my cryptocurrency wallets.
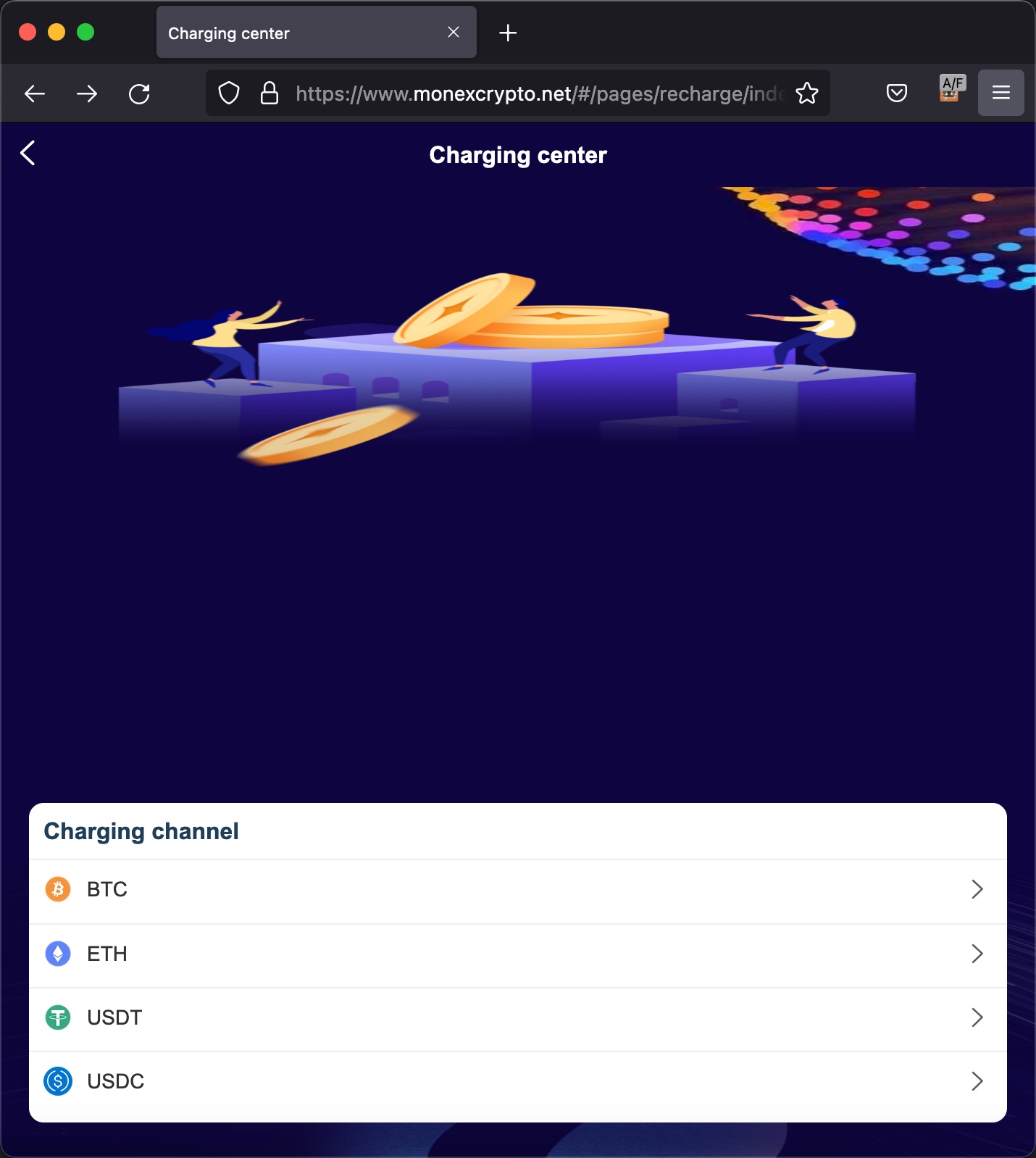
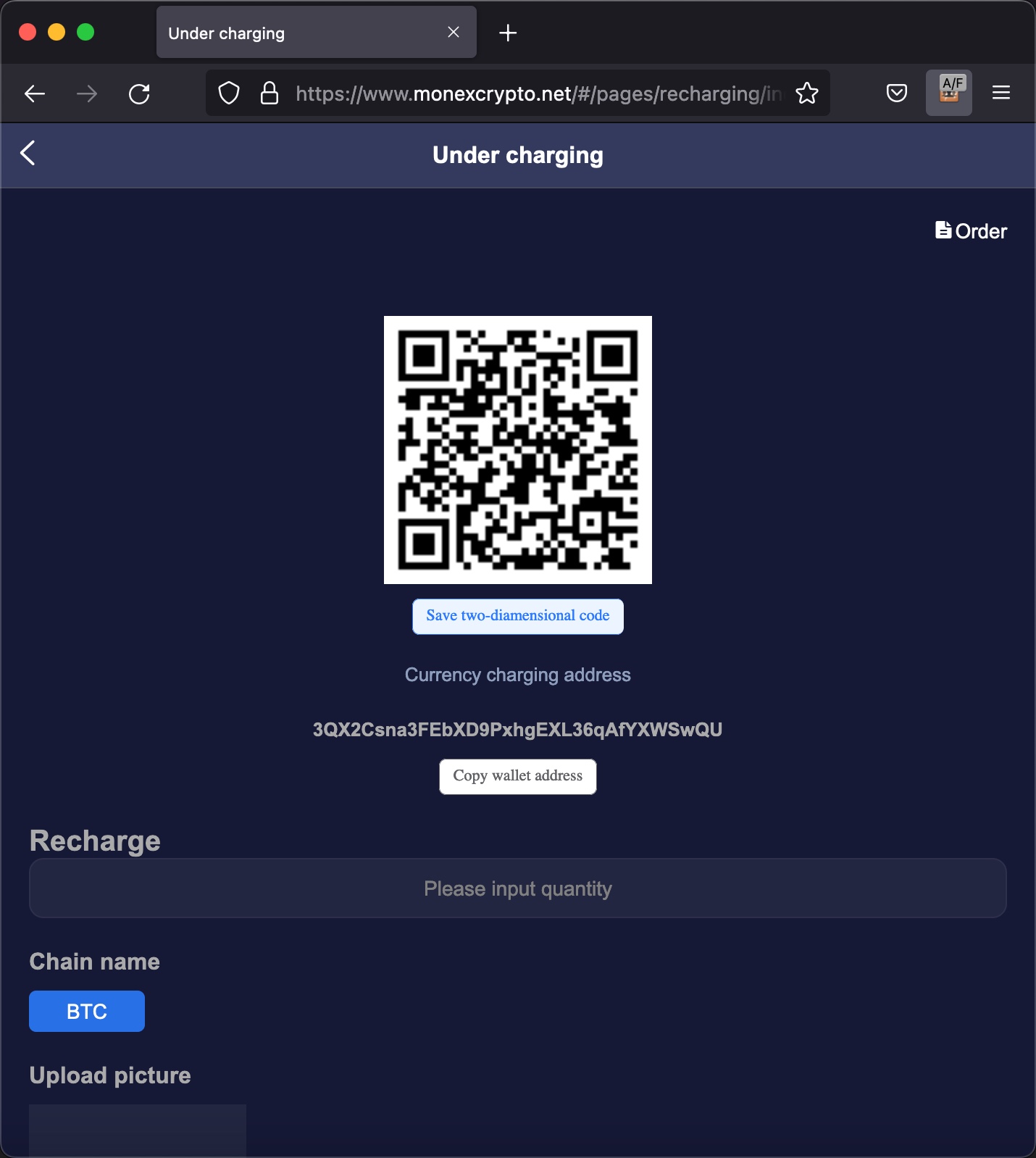
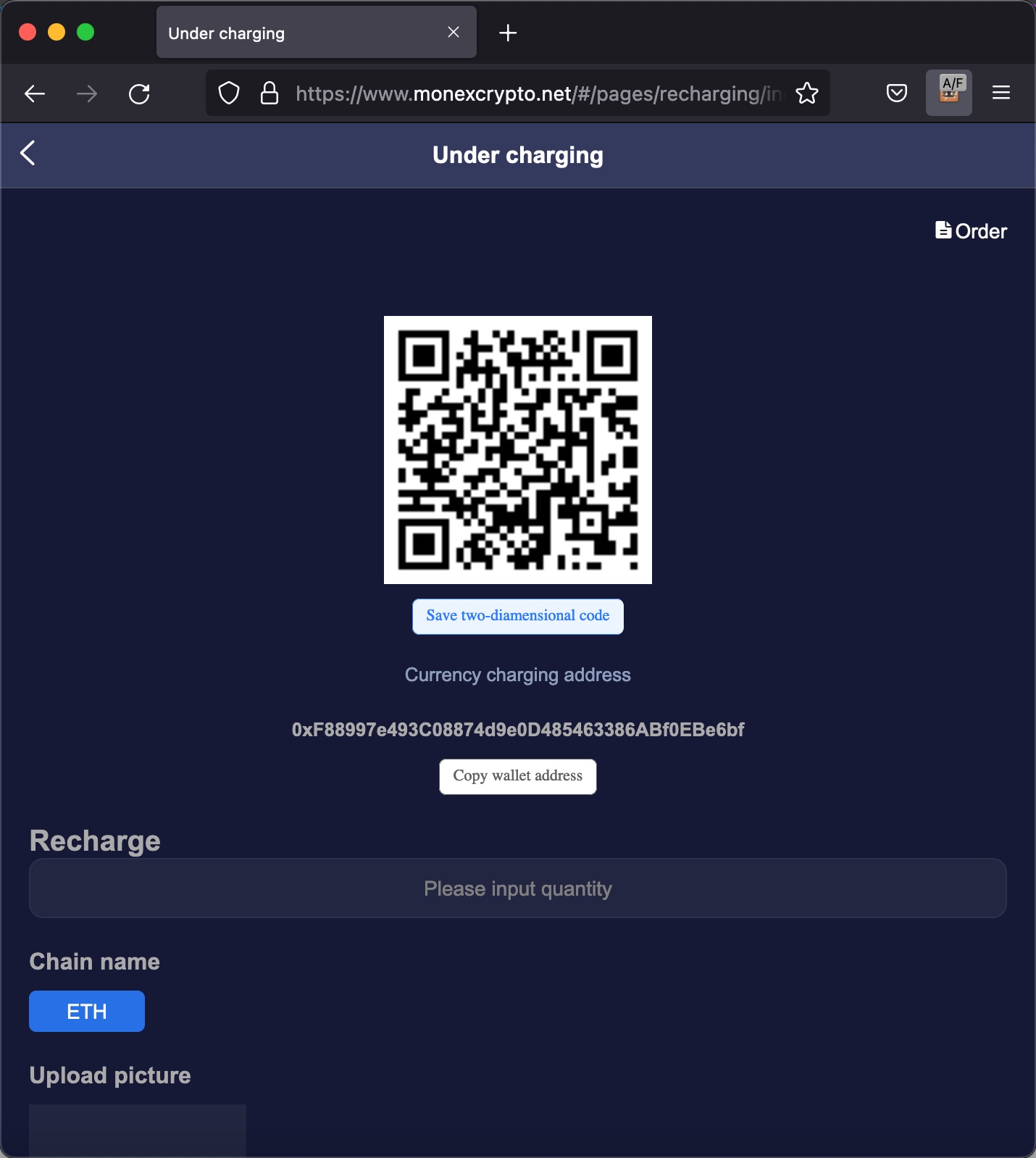
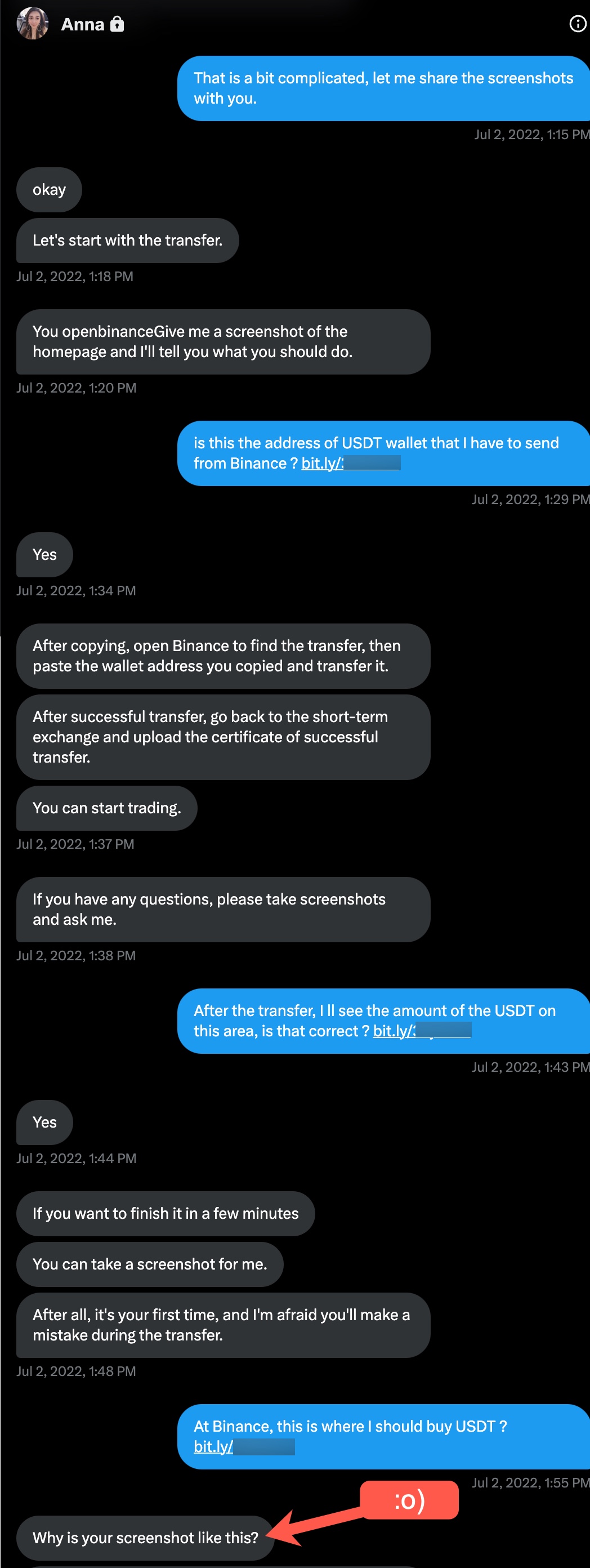
On June 28, 2022, Anna realized she was very close to scamming me, began directing me on how to send cryptocurrency (USDT) via a cryptocurrency exchange named Binance to my wallet.
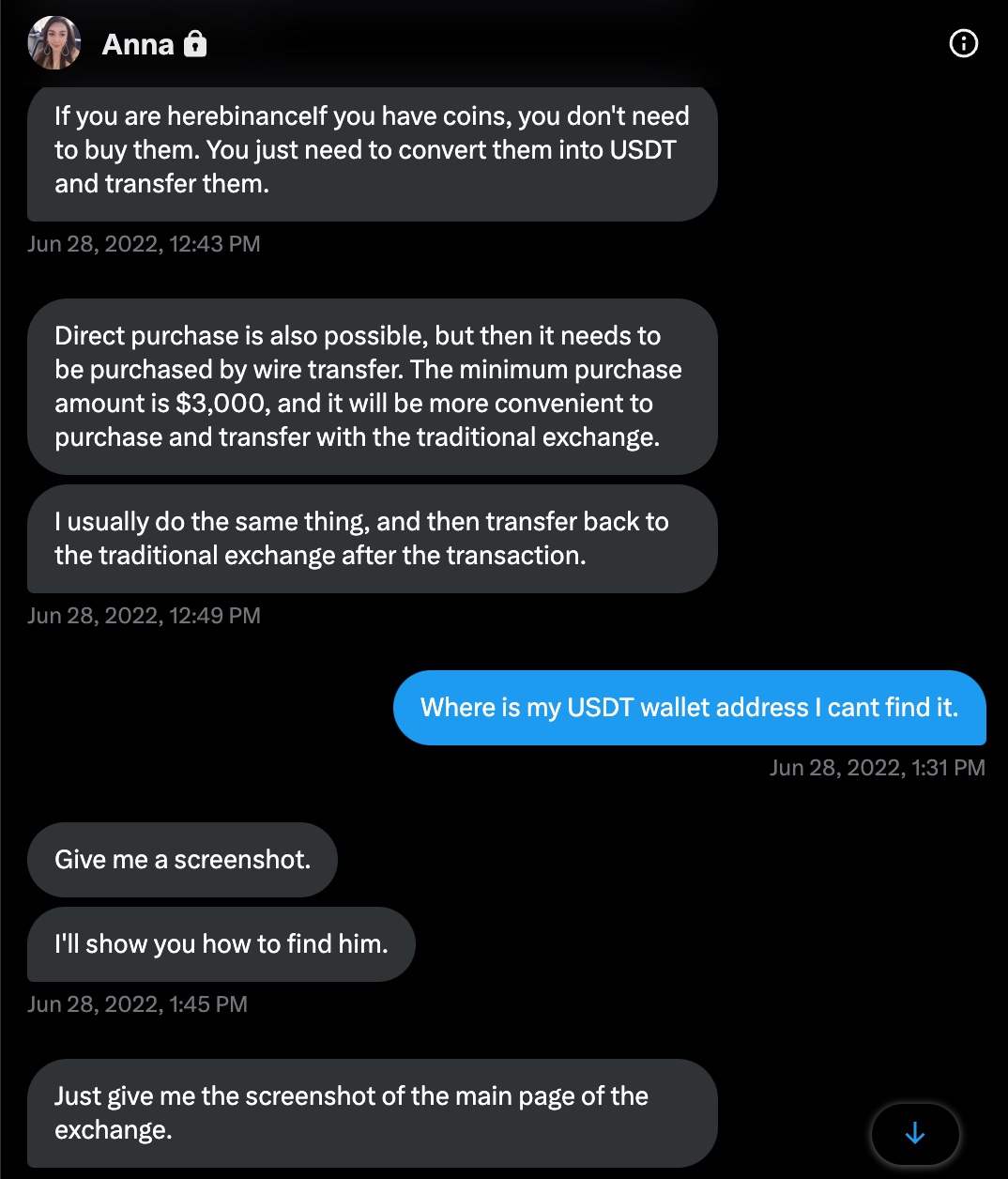
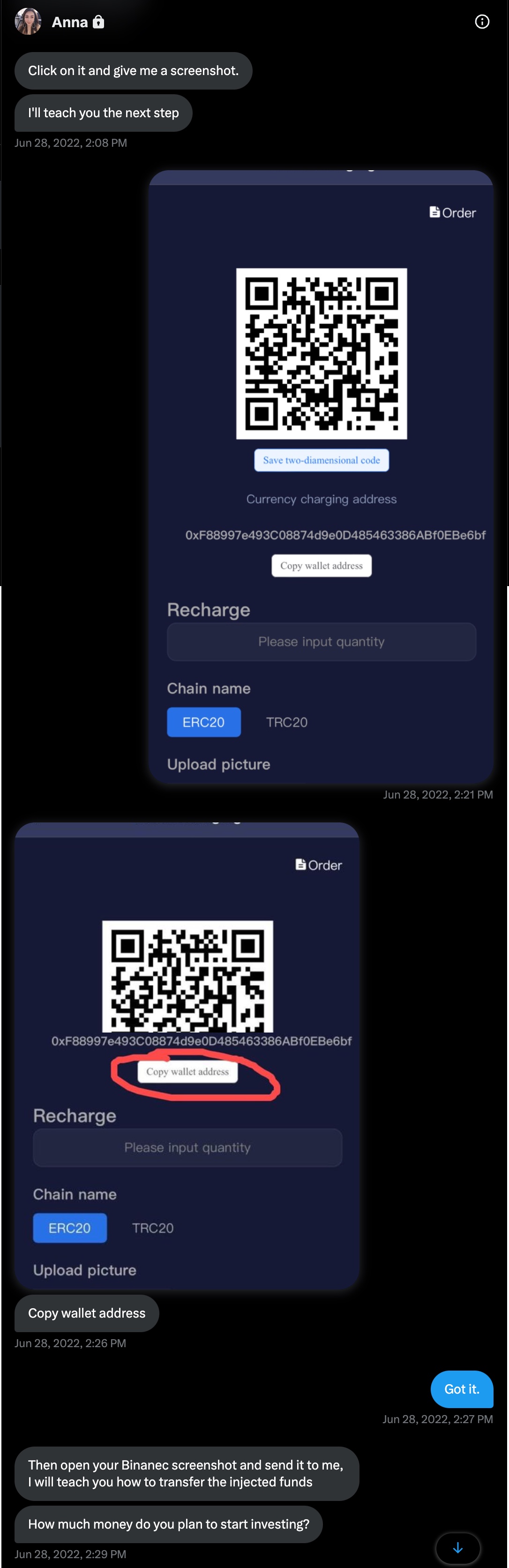
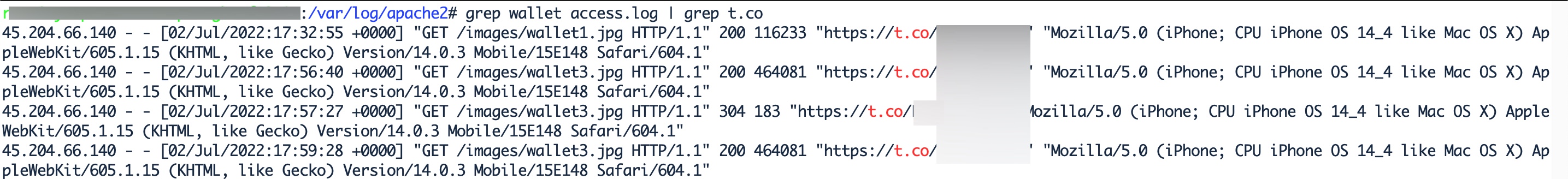
As I began to wonder which country Anna was really communicating with me from, I started to think about what I could do to find out Anna’s IP address. I guessed that Anna, who had never suspected me despite the éCyber Security Researcher” background image on my Twitter profile, continued to carry on her plan to trap me for 15 days, had no concern about Operations Security (OPSEC). For this reason, I decided to share the web addresses of the screenshots I hosted on my website with Anna by using the Bitly URL shortening service in order to obtain her IP address.
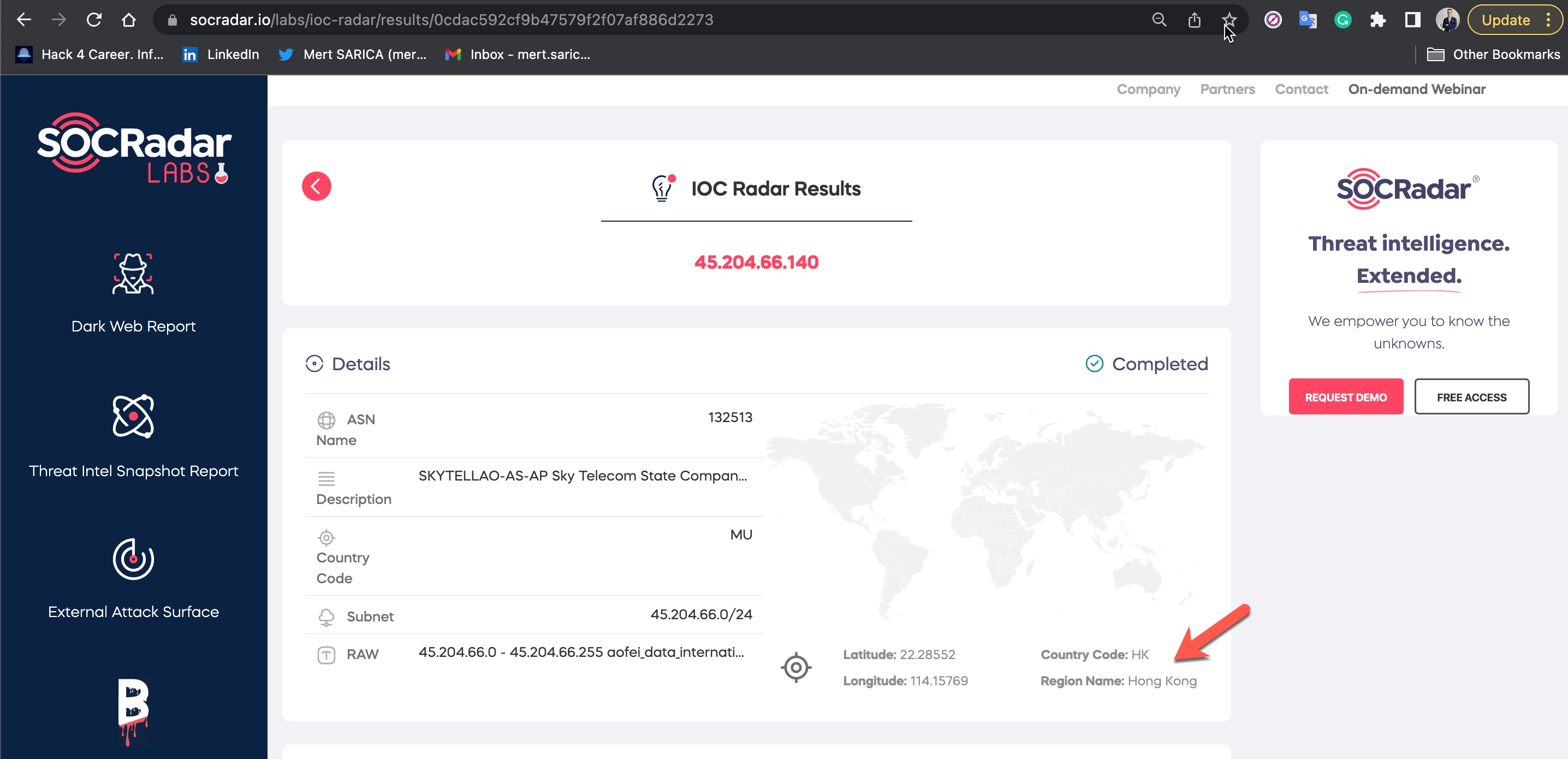
Because Anna did not hesitate to click on the three bit.ly addresses I shared, with the help of the SOCRadar’s IOC Radar I learned that she was communicating with me from the 45.204.66.140 IP address located in Hong Kong.
As I continued to browse the MonexCrypto website, I decided to check if the Bitcoin and Ethereum cryptocurrency wallet addresses were unique to me or same for everyone who joined the platform. If these wallet addresses belong to scammers and they show their own addresses as wallet addresses to each person who joins the platform (victim), they can easily steal the cryptocurrency from their victims with ease. Based on the research I conducted on this matter, I discovered that;
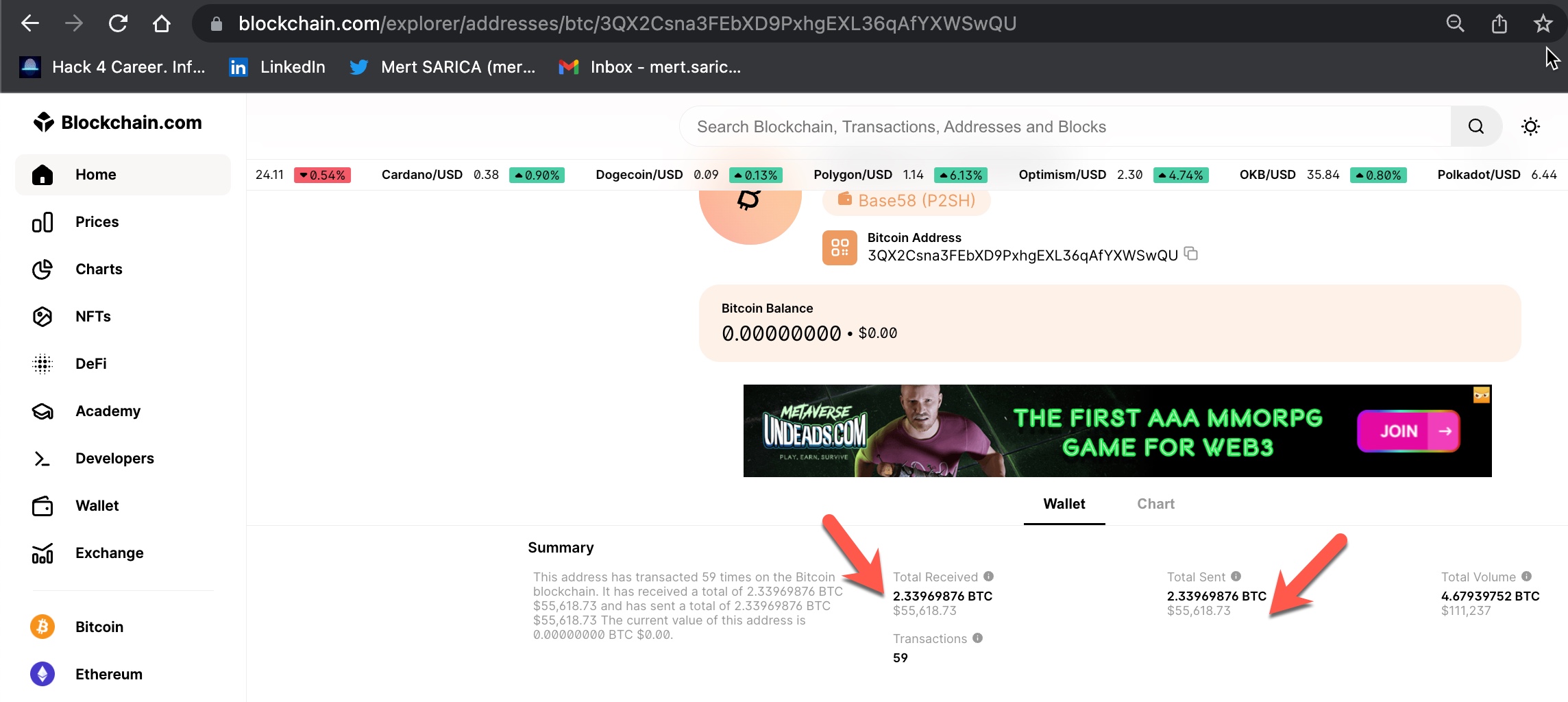
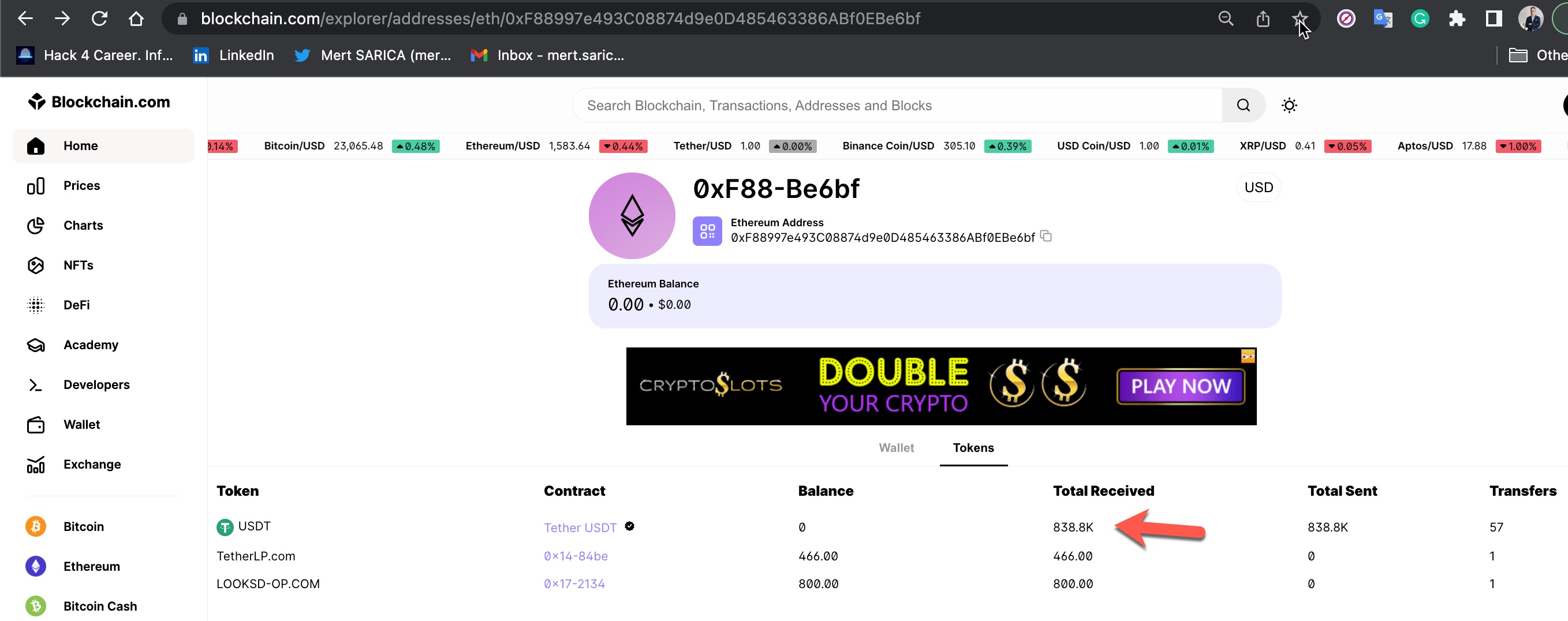
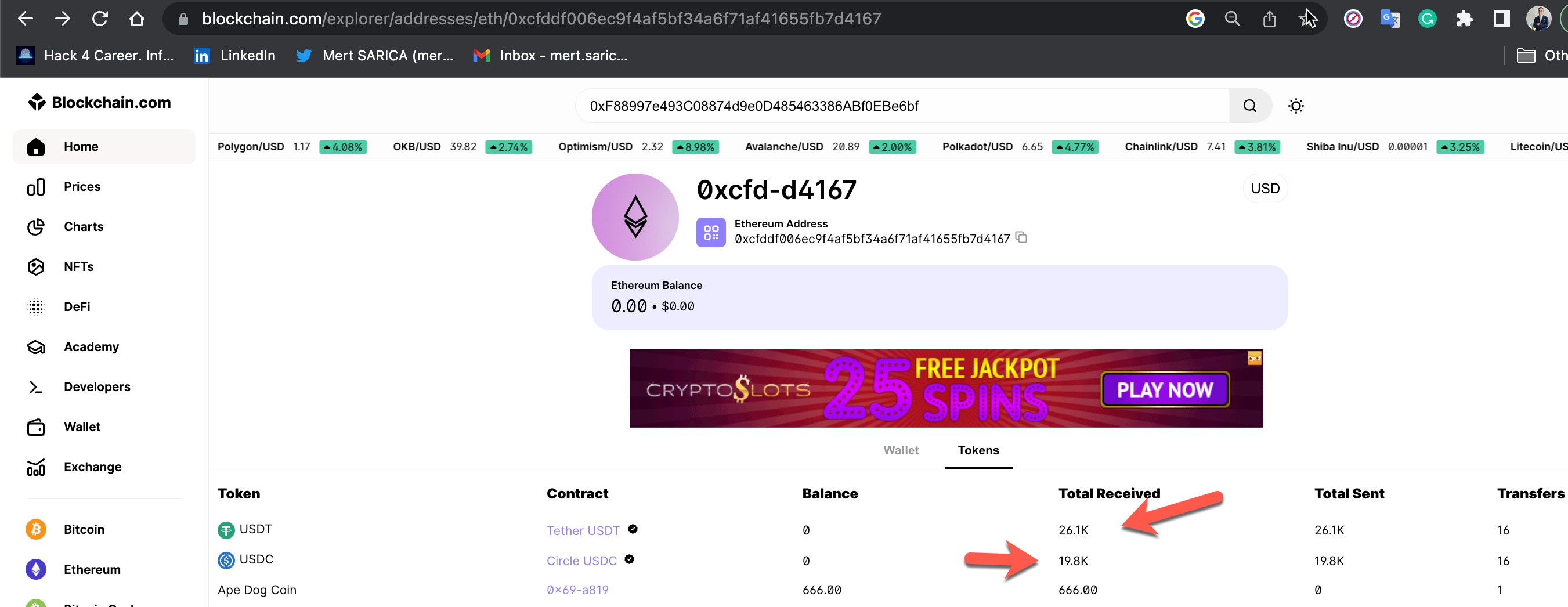
Disclaimer: I would like to remind that I am not an IRS agent or a Blockchain expert capable of tracing end-to-end cryptocurrency transfers as described in the book Tracers in the Dark: The Global Hunt for the Crime Lords of Cryptocurrency in case of any errors. :)
From the date I registered on the MonexCrypto website, June 26, 2022, to January 29, 2023, I roughly checked my wallet addresses 5 times by logging into the MonexCrypto website, and I noticed that they changed every time. Based on this information, the wallet addresses were not individually produced, but were the scammers’ own wallet addresses, and they changed these addresses at certain intervals. When I listed and gathered the wallet addresses and the money transfers made to these wallets, I realized that the scammers had stolen approximately 3 million dollars worth of cryptocurrency, to the best of my estimation.
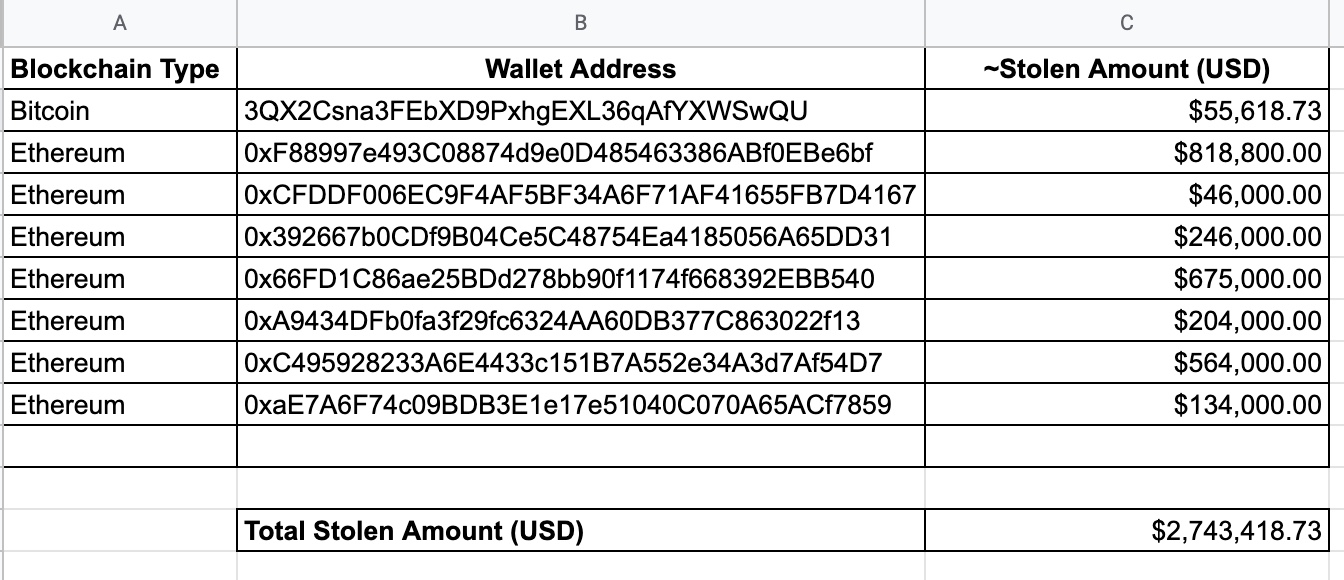
Of course, while I was trying to unmask Anna on July 18th, 2022, the FBI issued a warning against fraudulent attempts made through fake crypto exchanges/investment applications like MonexCrypto. According to this warning, approximately 42.7 million dollars worth of crypto had been stolen from 244 people worldwide. I had already learned how 3 million dollars were stolen. :)
In 2021, the FBI’s Internet Crime Complaint Center received more than 4,300 submissions related to pig butchering scams, totaling more than $429 million in losses. And at the end of November, the US Department of Justice announced that it had seized seven domain names used in pig butchering scams in 2022. (Source: Wired)
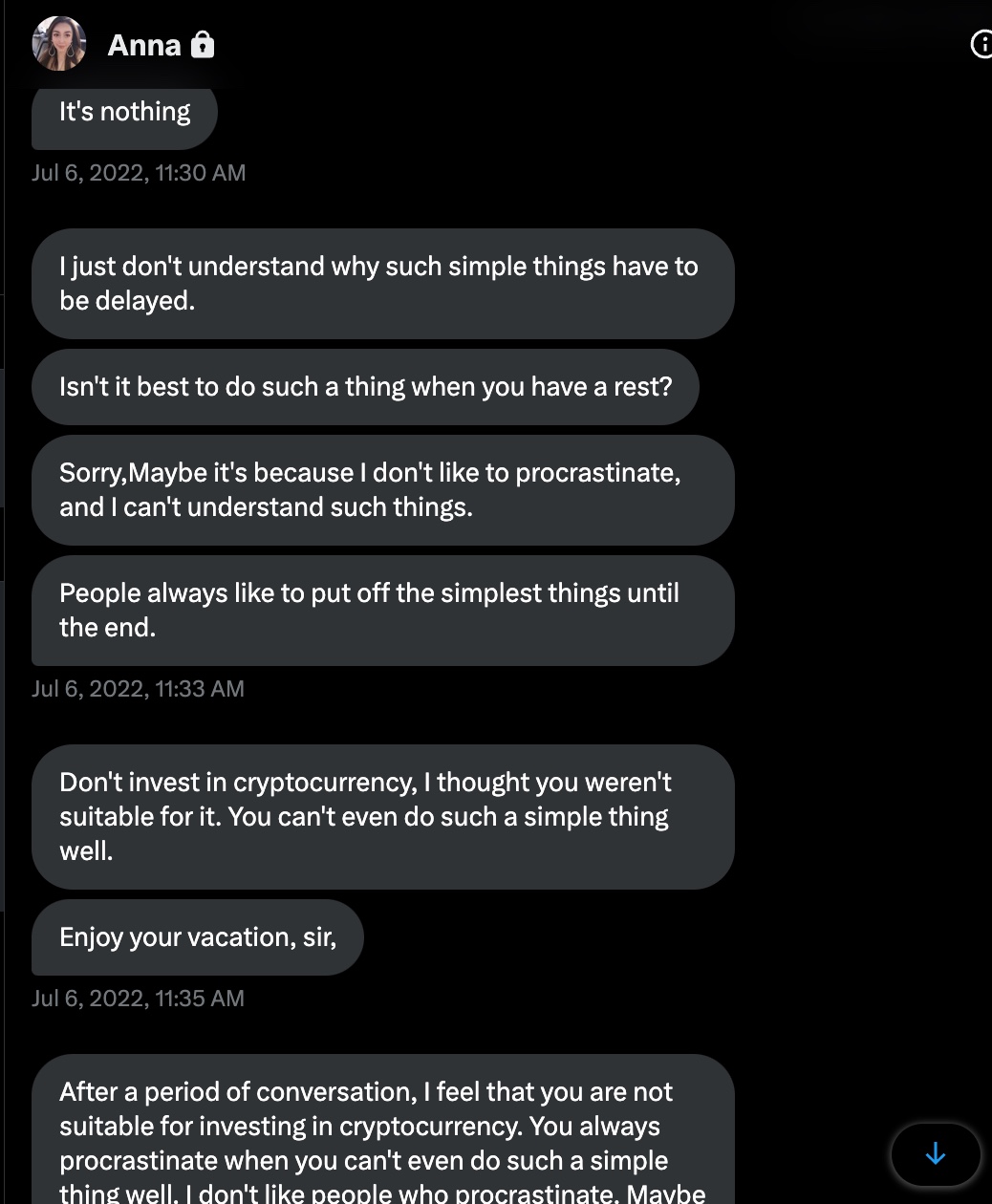
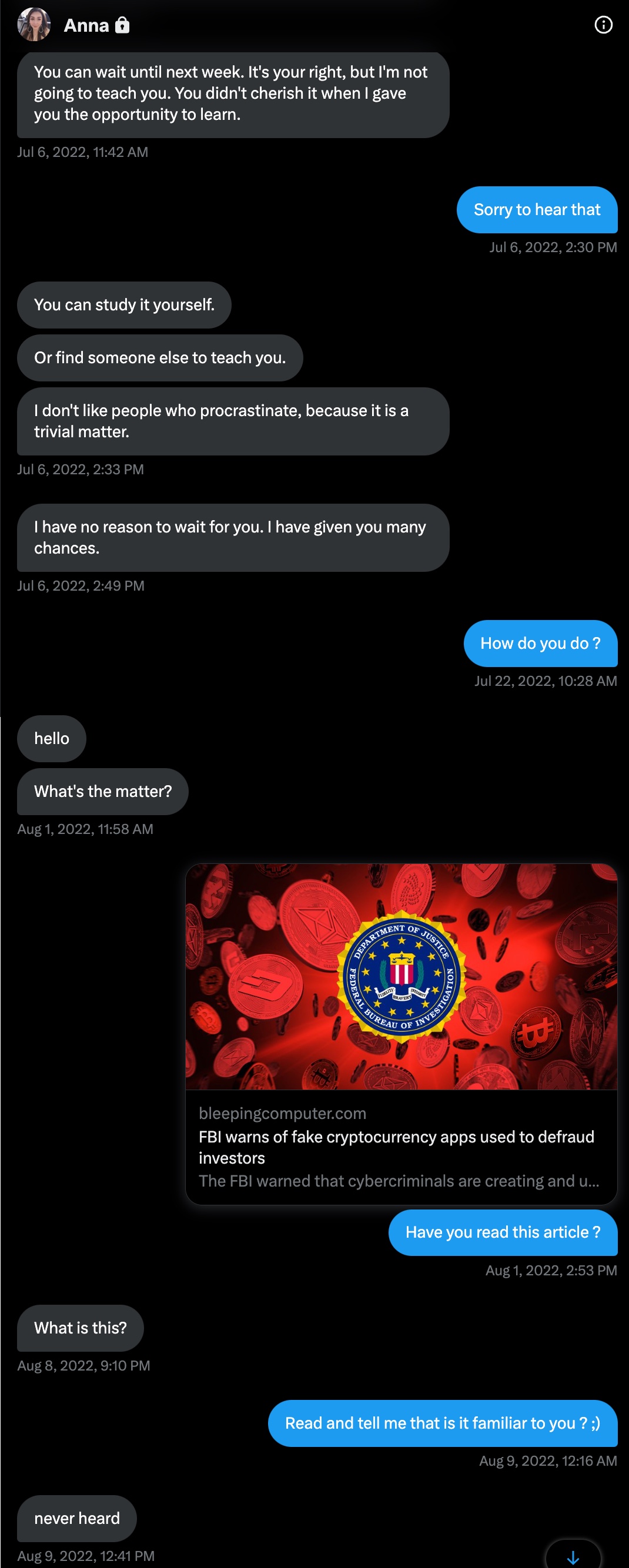
Anna, who exhausted all means of persuasion to deceive me from June 14th to July 6th, 2022, she started sending messages full of complaints on July 6th. I put an end to our conversation with the bad guy smile by informing Anna of the FBI’s warning on August 1st, 2022. :)
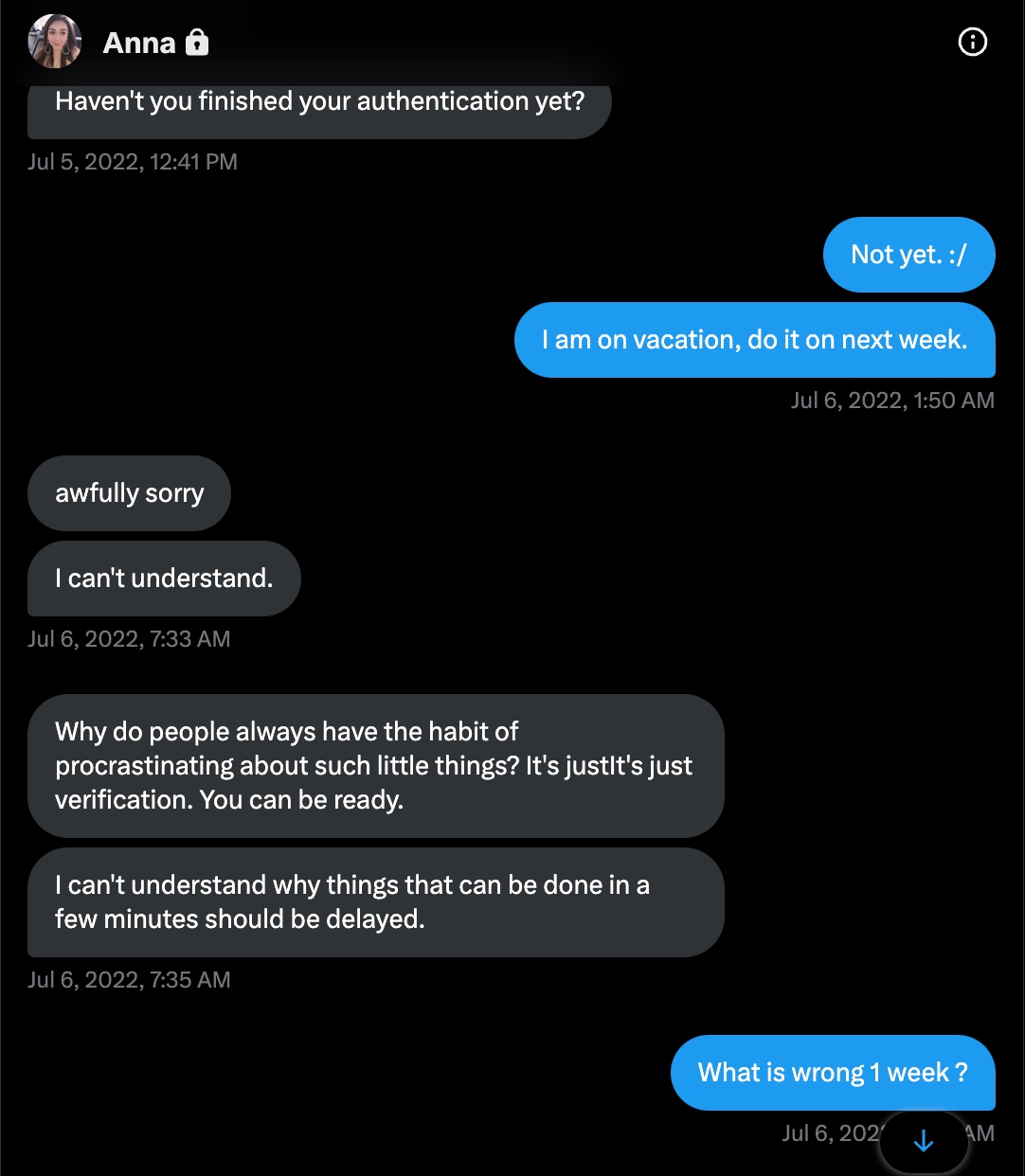
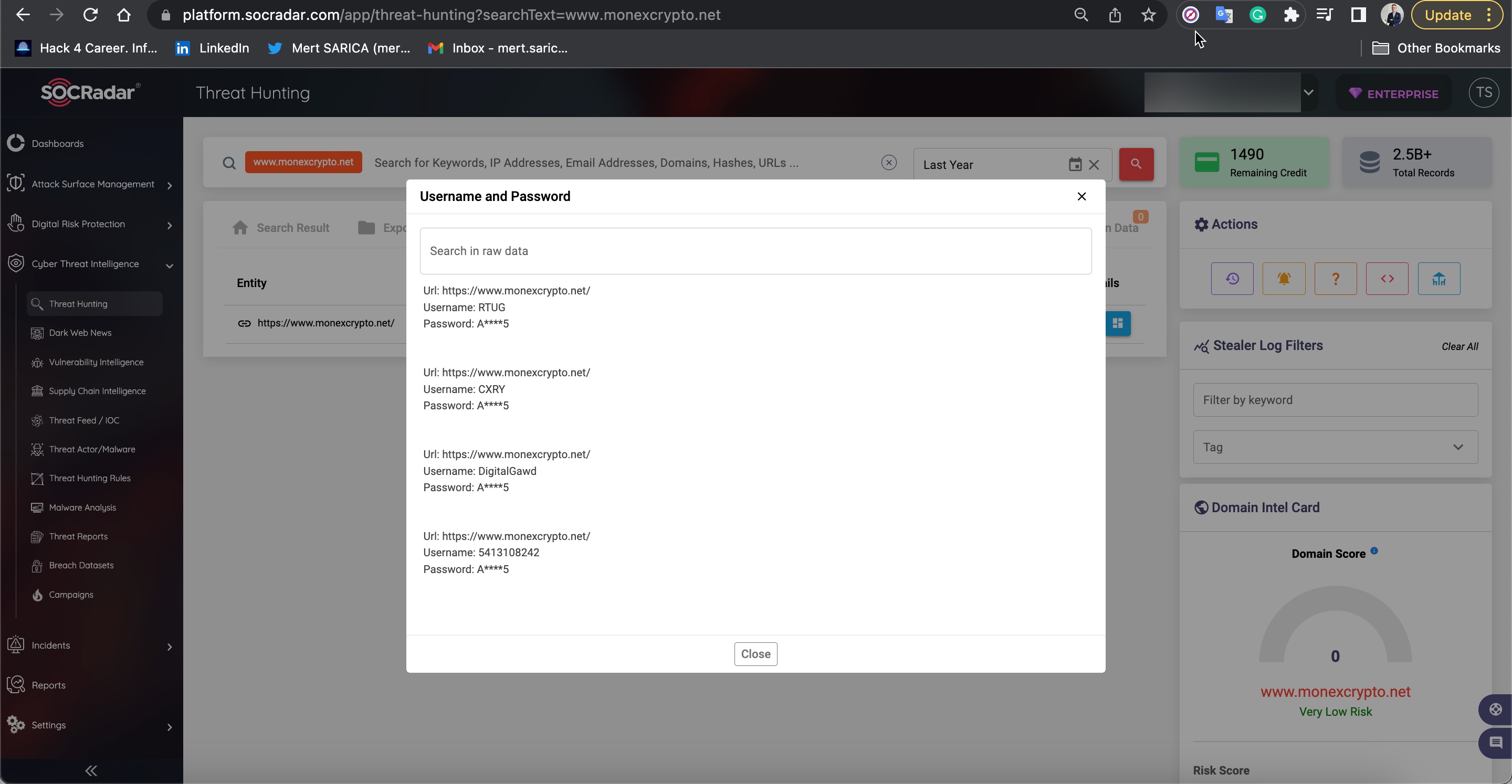
It seems that Anna continued to catch new victims in her web without slowing down in the following months and was successful, as some user passwords were also stolen when they entered the monexcrypto.net site on September 5th, 2022, according to information detected as stolen by a malicious software (Stealer) on the SOCRadar Cyber Threat Intelligence platform.
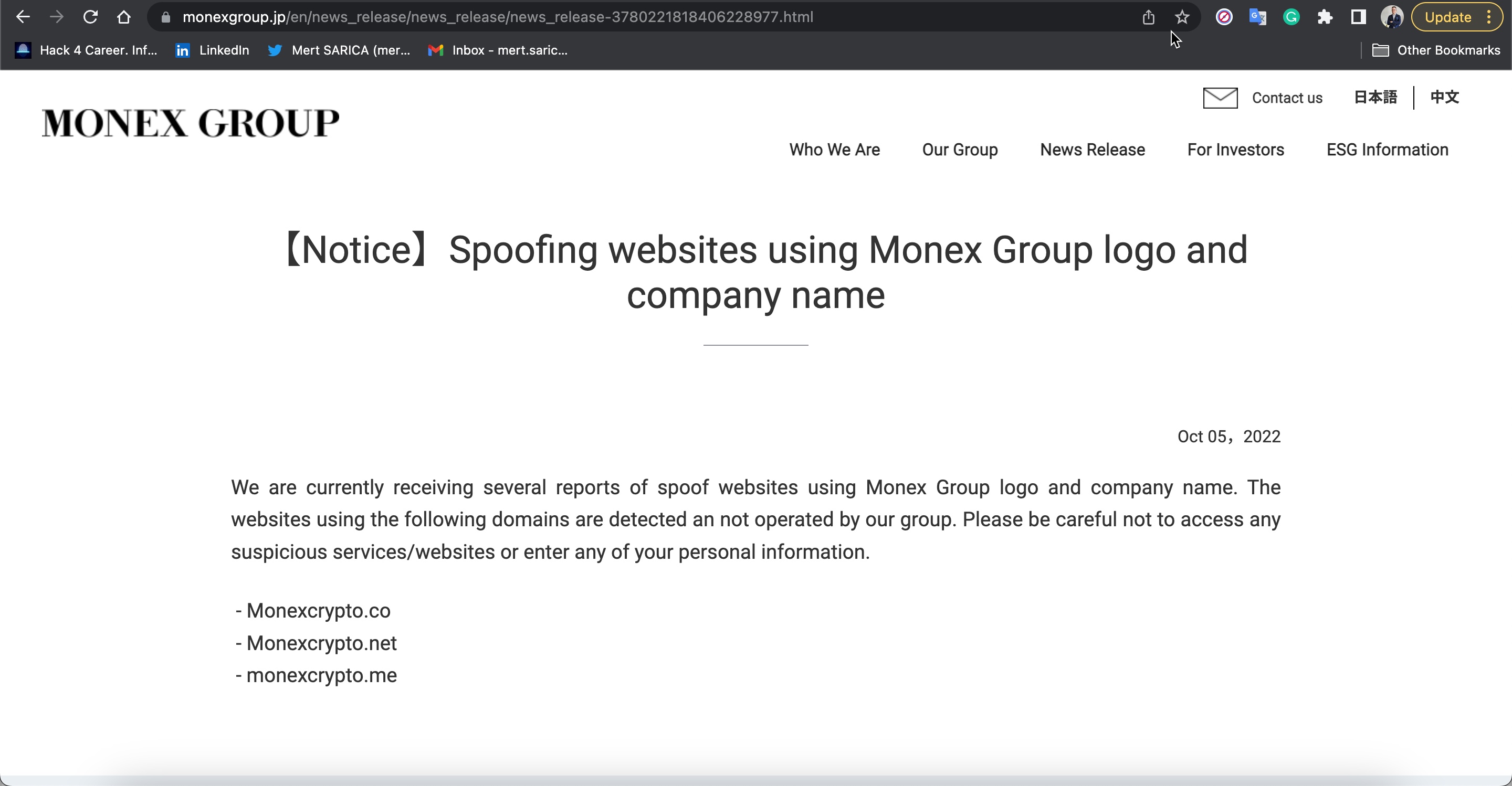
By October, the Monex Group issued a warning that two more websites, starting with the monexcrypto.net website, were using the group logos without permission.
As a result, we have learned in detail how Anna and her scammer friends carried out the Pig Butchering Scam, a well-designed fraudulent scheme, and how they made millions of dollars in loot, from the applications downloaded not only from 3rd party websites but also from the Apple App Store and Google Play Store.
Pig Butchering scam is named after the practice of fattening a pig for slaughter. In this case, scammers build a relationship with a victim online before convincing them to send money or invest in high yield crypto-currency accounts.
I strongly request you to share this article with your friends, loved ones to raise security awareness. Hope to see you in the following articles.