I have been hearing this question more and more frequently from many people around me, both those I know and those I don’t know, in recent years: “My data has been encrypted, they’re asking for money, what can I do? Who can I get help from?” I see this as similar to the question, “I lost my arm, what can I do?” from someone who didn’t put on their seatbelt and then smashed into a wall at high speed. Unfortunately, some mistakes are not easily or even possible to fix. In the cyber world where encryption malware is running rampant, if you don’t regularly back up your data, use strong passwords on your systems/devices (such as using a combination of upper and lowercase letters and special characters), and harden the security of your systems, it won’t be long before you inevitably become the target of someone’s malicious intent, directly or indirectly. If you look at the security research I’ve done from the past to the present, you’ll be able to understand what I mean better.
In my blog post “Virtual Siege” that I wrote in 2010, I set up a simple honeypot at my home, and the point I was trying to make with the following sentence was that the problems faced by end users today in the virtual world were almost like echoes of what I had highlighted in the post.
“If I were to briefly summarize the information I obtained from the honeypot records, I would say that the first connection was made to one of the 11 ports on the honeypot within 12 minutes of being connected to the internet, and in the next 5 hours, a total of 14 different IP addresses from 8 different countries had established communication with the honeypot.”
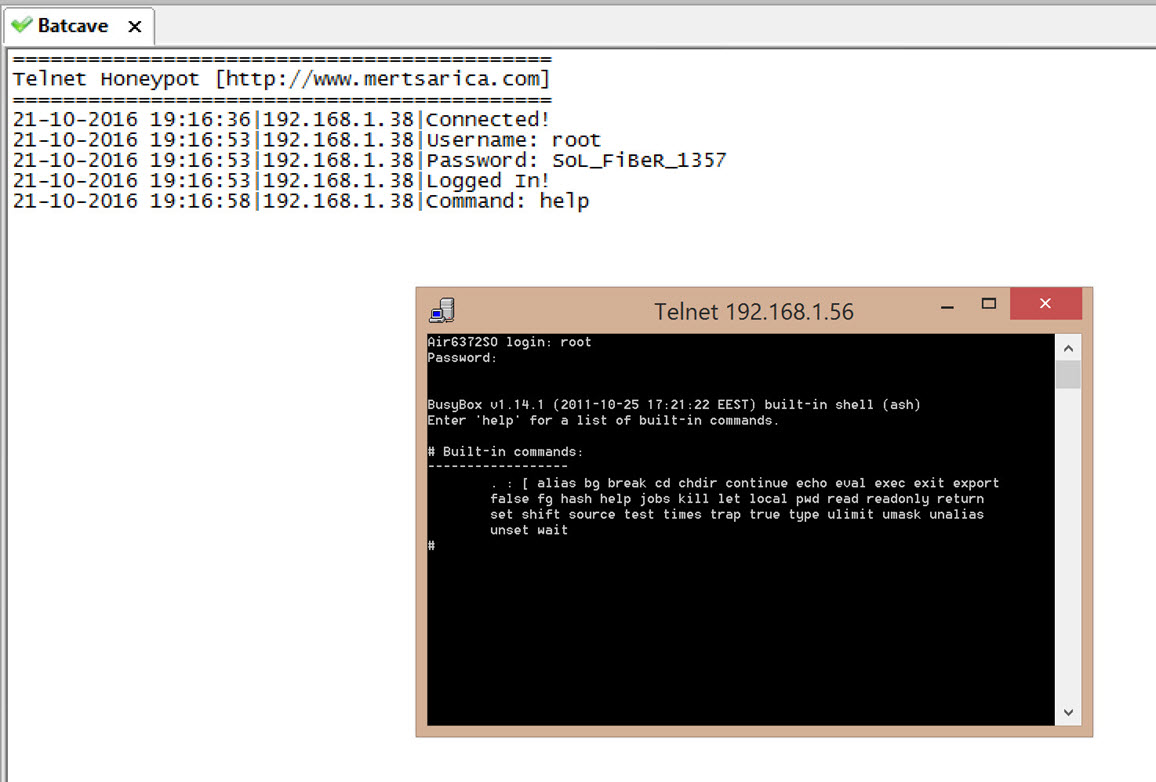
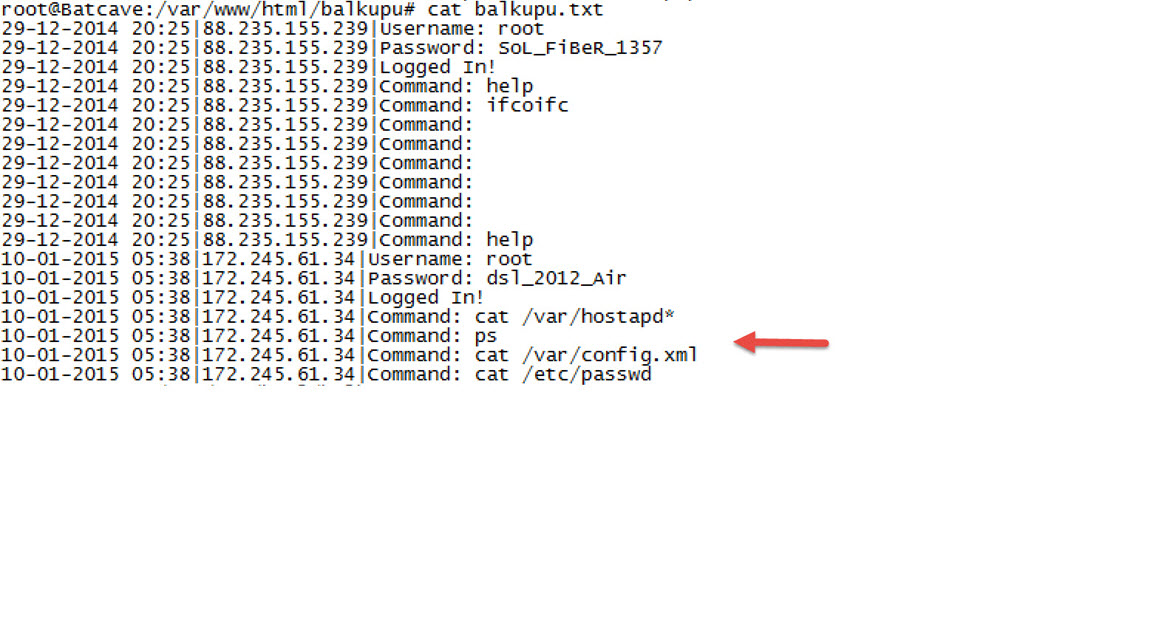
In another blog post of mine titled “Air6372SO Default Account Verification” in 2014, I tried to draw attention to how user names and passwords embedded in hardware and software can endanger our security as end-users. In the post, I also quietly put into action a fake Telnet Honeypot tool that I had designed to accept incoming connections, which would impersonate itself as the console interface of an Airties modem. The tool would record anyone trying to connect using the embedded passwords that were the subject of the post. After the post was published, a short time later I found that it was receiving connections from both inside and outside of the country. One of those connections came from an IP address in England (172.245.61.34) that had successfully intercepted the name and password of a WiFi access point and was trying to crack the password. When I thought about the reason behind this, it was likely that malicious individuals could be building dictionaries of passwords or could use this information to commit cyber crimes through your WiFi modem.
Towards the end of 2016, I decided to shed light on the methods used by ransomeware attackers who were using the encryption method I mentioned in the beginning of the post. According to rumors, malicious individuals were scanning Turkish IP blocks with tools such as Nmap, targeting open Remote Desktop services and performing dictionary attacks using tools such as Ncrack. I began collecting the necessary hardware for this research without breaking my budget (in 6 installments).
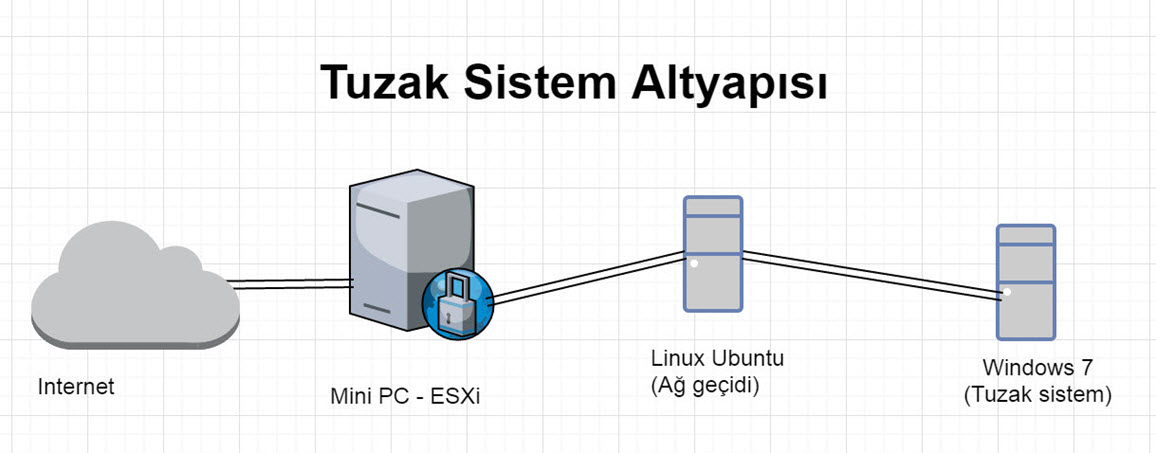
After collecting the hardware, I ended up with a deception system that had a 2GHz processor, 8GB of RAM, and a 120GB SSD disk. So first, I installed the free ESXi virtualization system, and on top of that, I installed a Windows 7 (Honeypot) with a fake accounting application to catch malicious individuals who hack the trap system, and to monitor the network traffic and limit internet connection. I also installed an Ubuntu operating system (Batcave) to make sure that the system can’t be used for other crimes. I isolated Windows 7 on the local network and used Ubuntu as a proxy server (with ssl inspection) to connect to the internet.
To make the deception system more attractive to malicious individuals, I began searching for an accounting software to install on the Windows 7-based system. To decide which accounting software to use, I used information I had gathered from victims of data encryption and chose Akınsoft’s OctoPlus software.
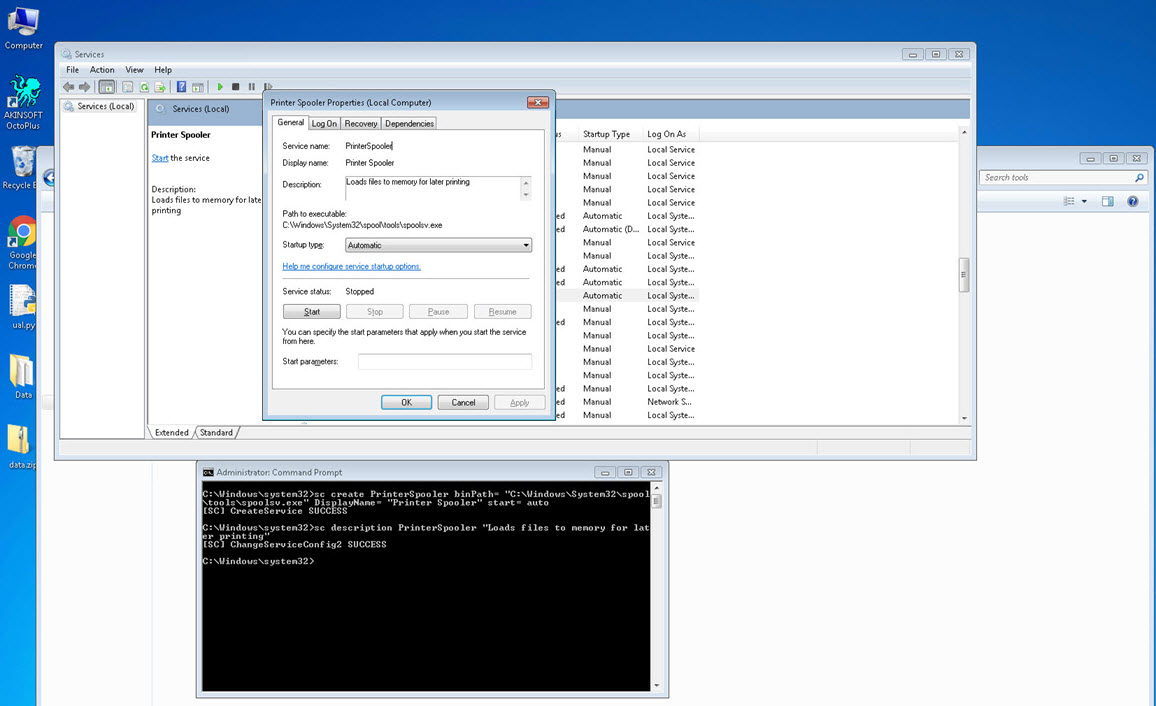
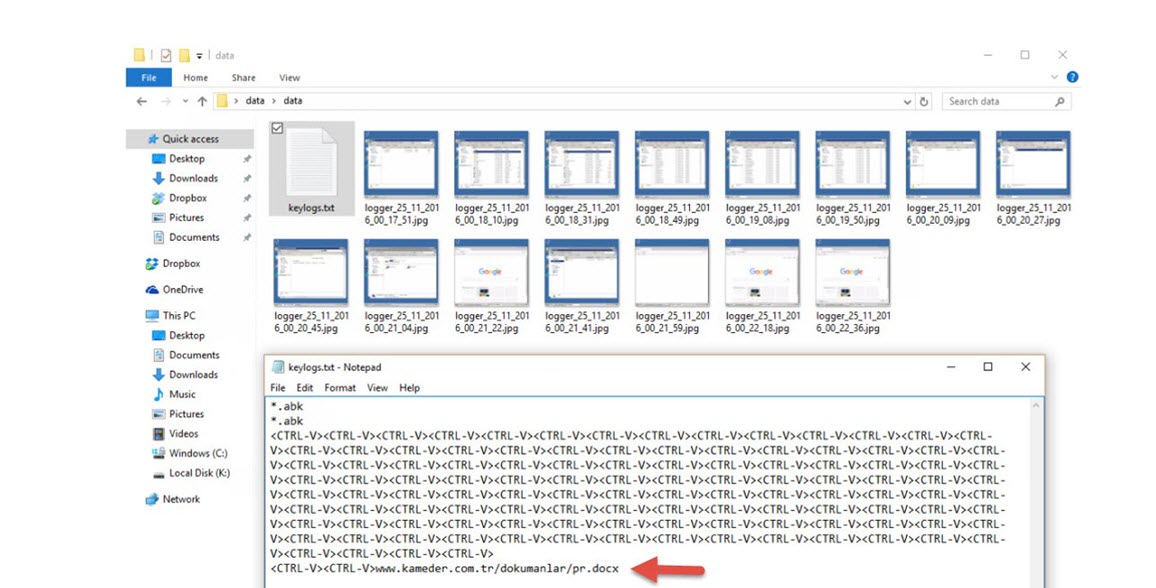
When it came time to design the tool that would make the deception system a trap, I created a tool called UAL (User Activity Logger) using Python. It would record all of the user’s actions on Windows (keystroke logging, video recording, screen capture, clipboard copying) and sends all information except the video file every 5 minutes by email. However I decided not to share the source code for this tool for the safe use of it. To avoid raising the suspicions of the malicious individuals who connect to the trap system, I hid various folders, including the Python27 folder, on the operating system. Then, I changed the name of the compiled UAL.py tool to spoolsv.exe, and registered it as a Windows service so that it would run again with each session.
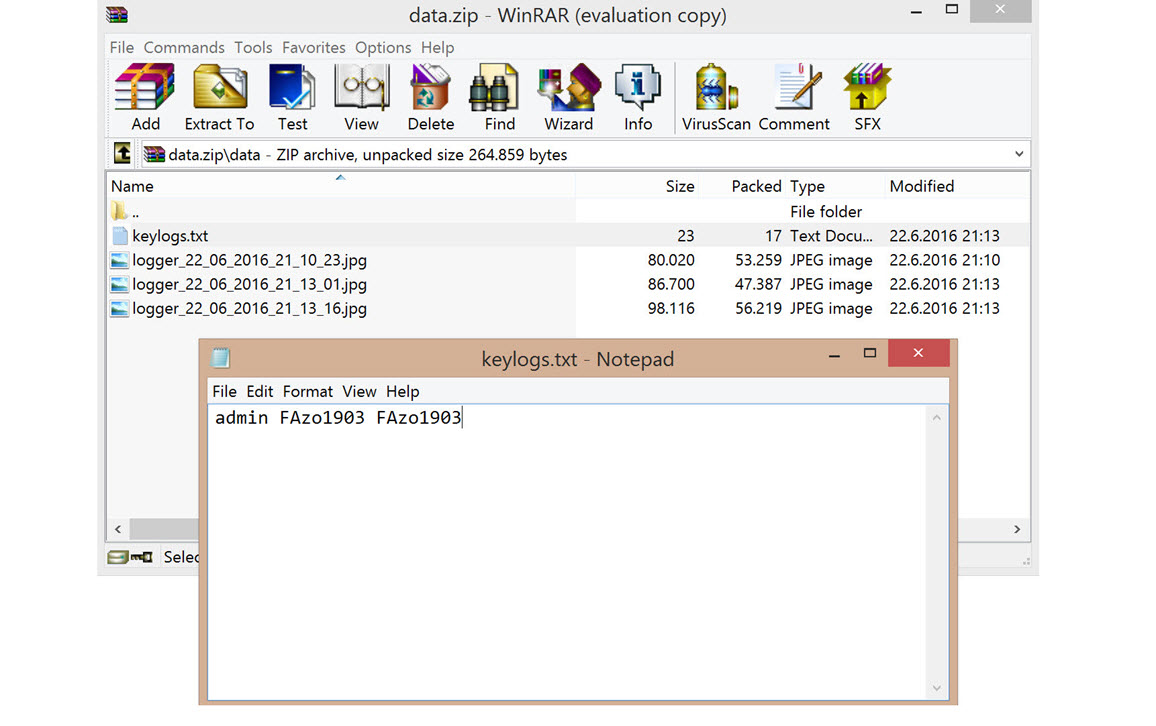
After setting up the deception system, with an admin password called accounting, and allowing access to the internet through the modem, I began monitoring the system for 6 months. During this time, I made many improvements to the system thanks to the information obtained from those who fell into the trap. For example, many malicious individuals checked the modification date of files before encrypting them to see if the accounting program was actively being used. Although some were able to crack the administrator password of the trap system using dictionary attacks, it took nearly 6 months for one of the ransomeware attackers, who targeted individuals and made the news, encrypting data and leaving a note, to fall into the deception system.
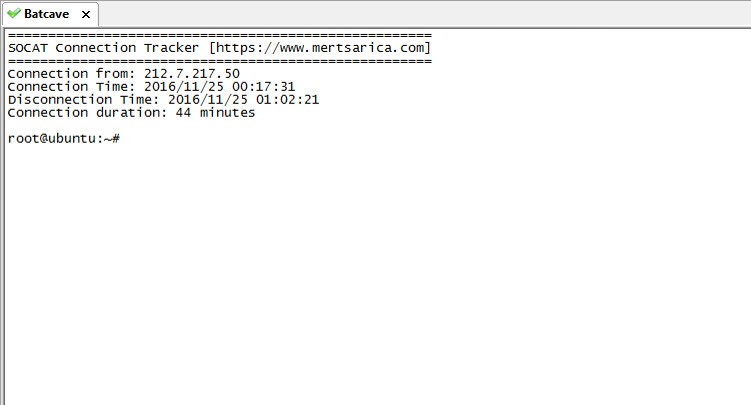
To be able to know the IP addresses of those who connect to the trap system and how long they stayed connected, I decided to redirect connections through Ubuntu (Batcave) instead of allowing internet access to the Remote Desktop service. To do this, I used the socat tool on Ubuntu to redirect all requests to port 3389 to the trap system’s port 3389. Since the detailed logging feature of socat was not practical to read, I also created an additional tool in Python called Socat Connection Tracker to help in monitoring connections.
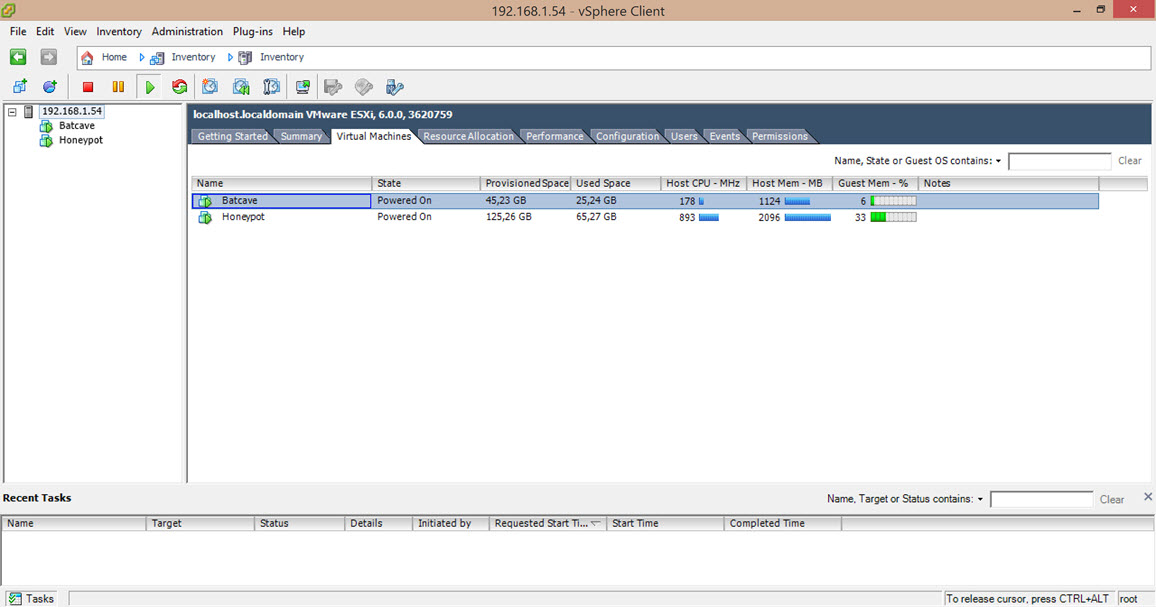
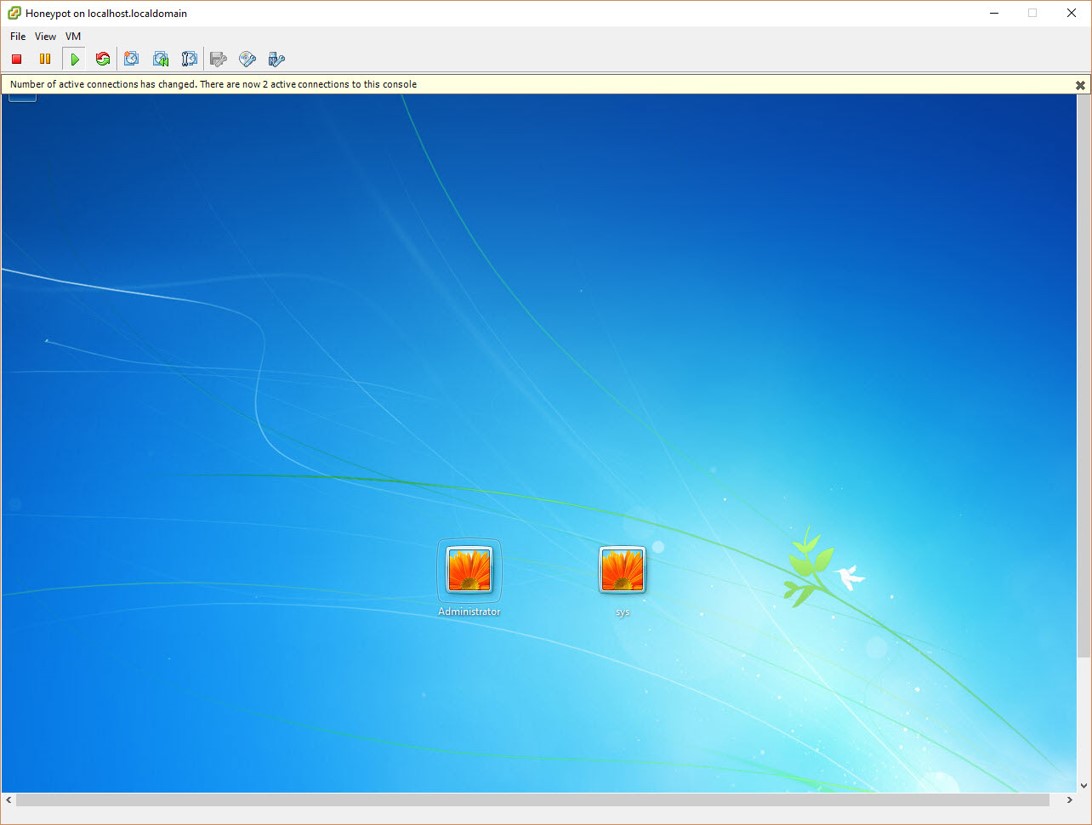
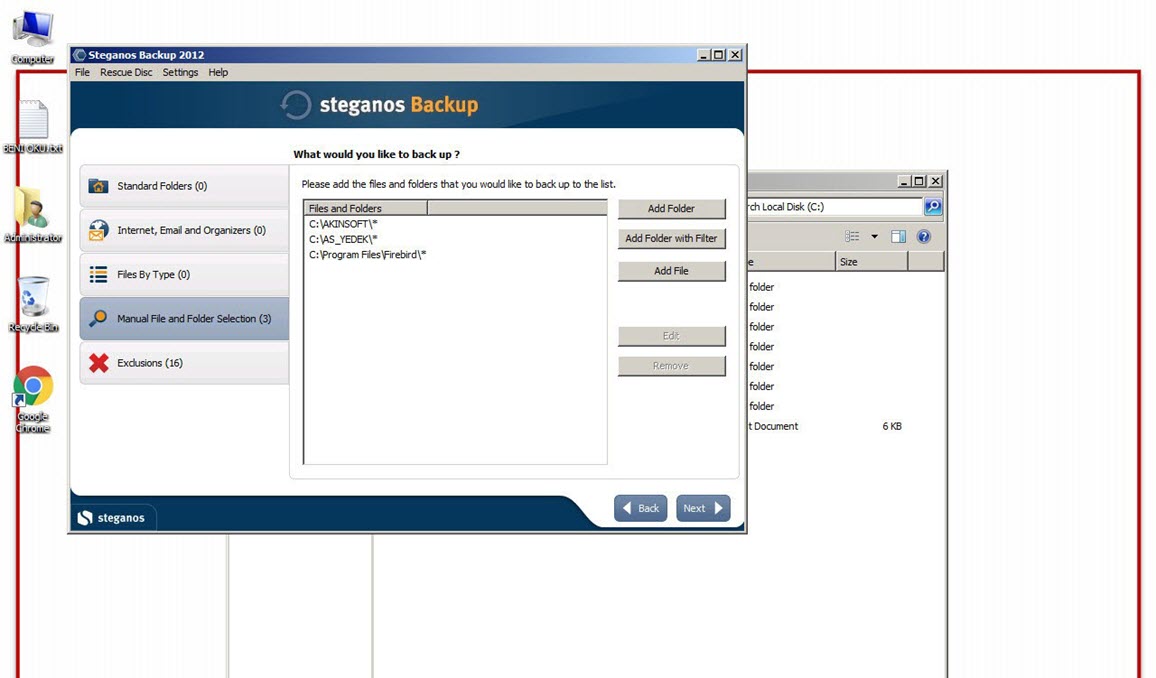
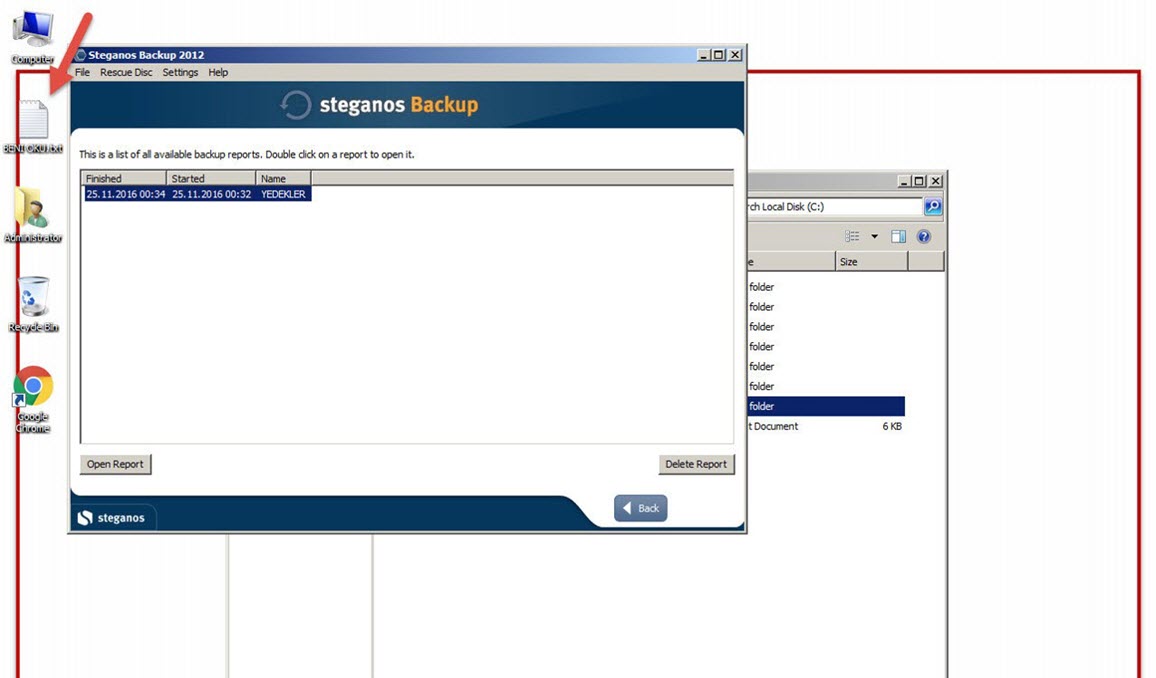
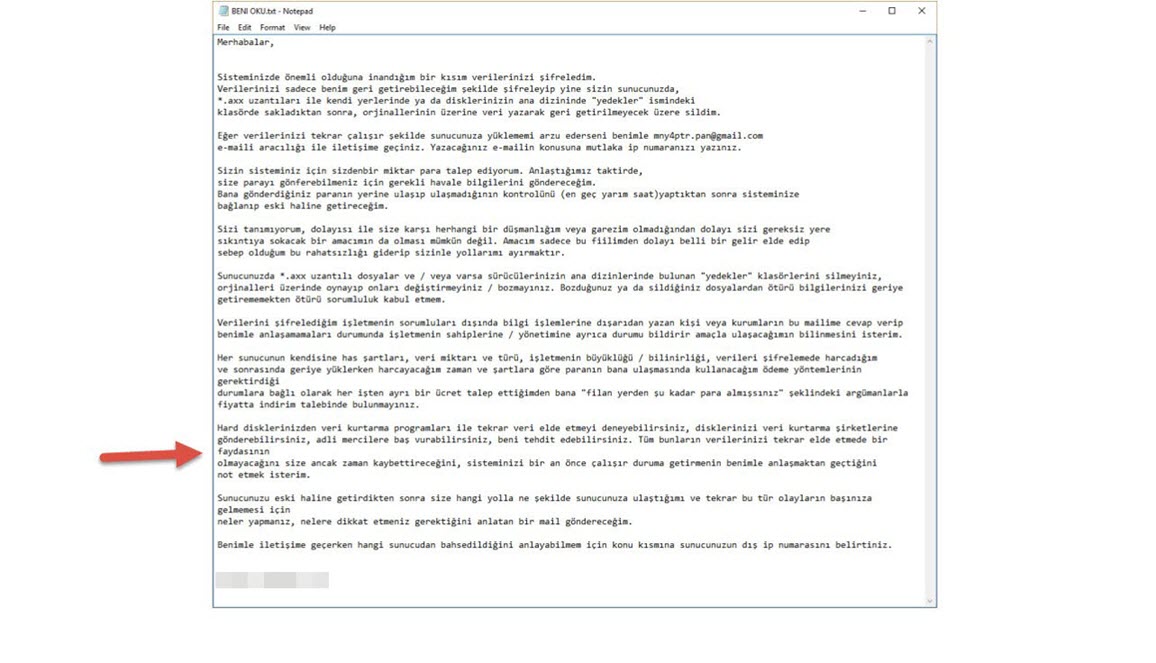
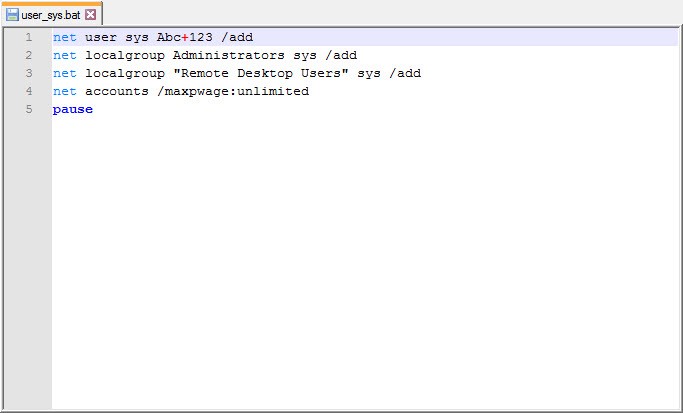
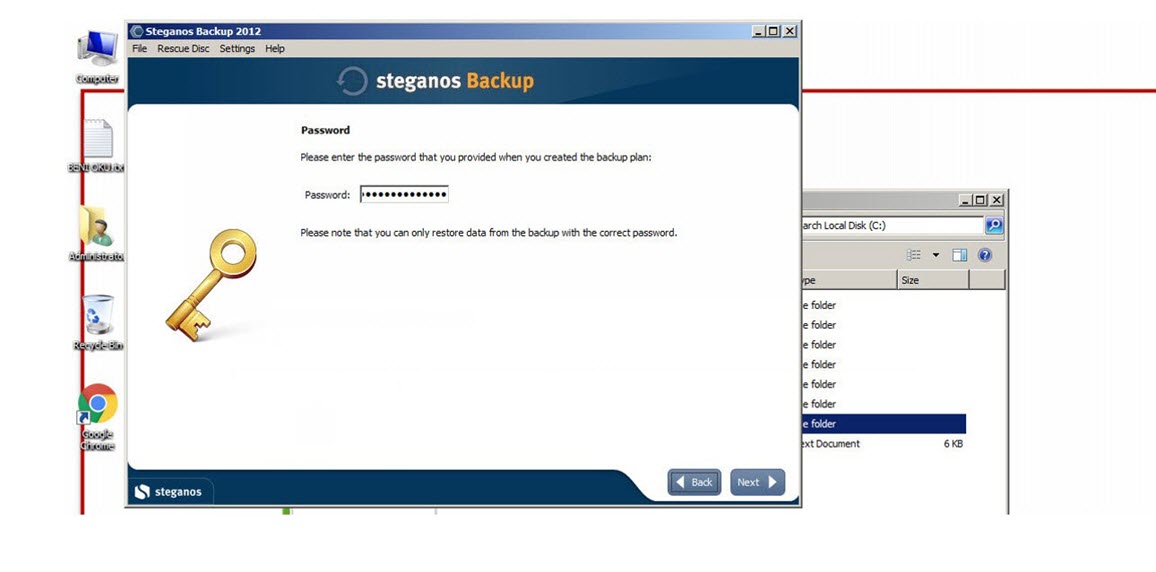
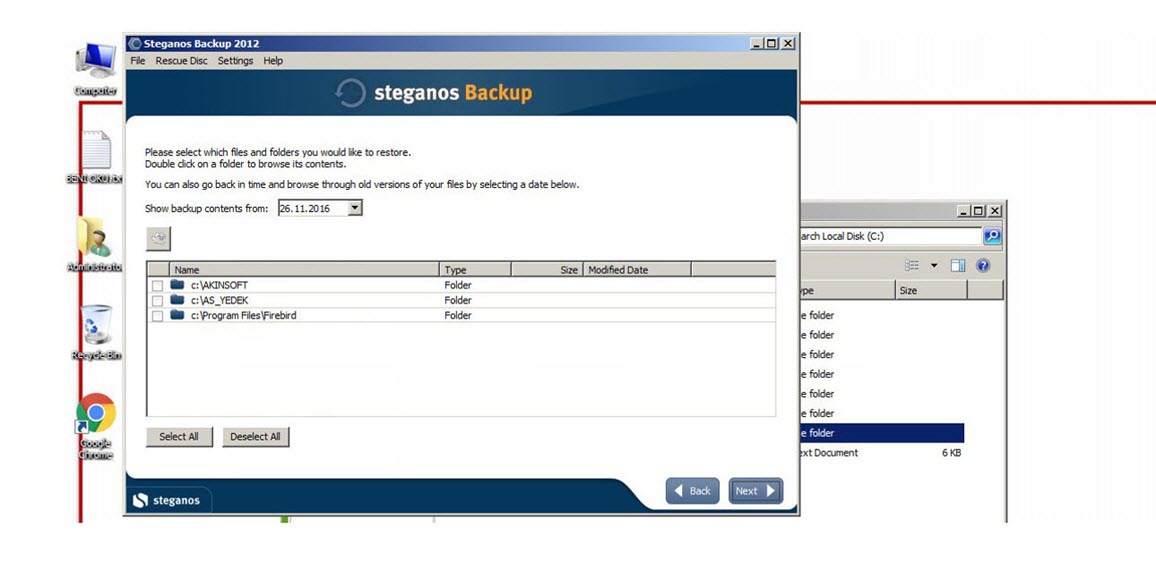
One morning, I woke up and found that my email inbox had received many emails sent by the deception system, indicating that someone had hacked the system while I was asleep. When I connected to the trap system’s console through the ESXi interface, the first thing that caught my attention was that a new user named ‘Sys‘ had been created. When I logged in, I saw that the accounting program’s folders were encrypted and backed up with Steganos Backup 2012 software and there was a note on the desktop. It became clear that the day I had been waiting for had finally come and the connection was made by someone stayed connected for 44 minutes which can be seen from the screenshot provided.
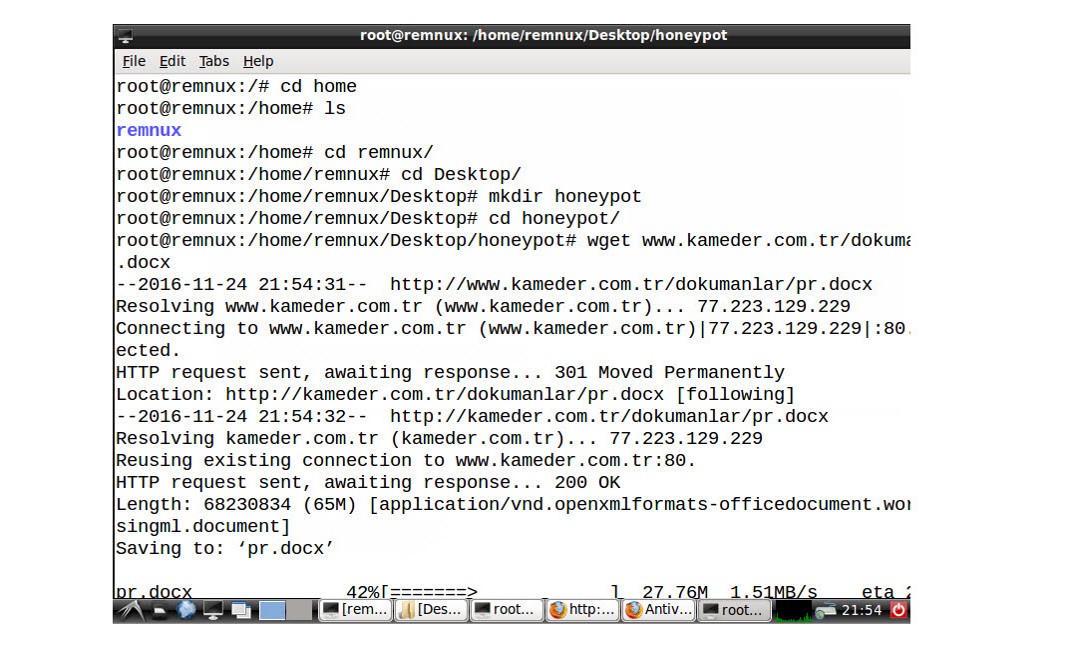
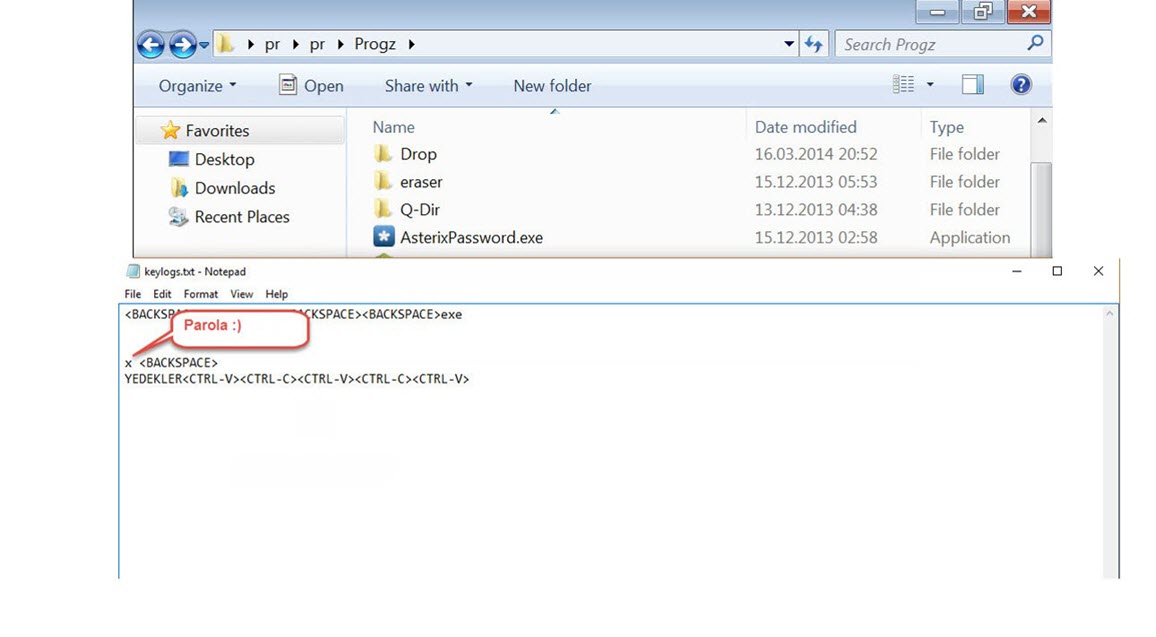
Upon reviewing the records of the malicious person, I found that he had downloaded a file named “pr.docx” from a website (likely a hacked one) called kameder.com.tr. Because the file was a 65 MB document, it seemed suspicious and I was able to find out that it was a ZIP file. When I tried to open the ZIP file, it asked for a password. Quickly checking the records, I found that the password was x. Upon opening the ZIP file, I found all the tools that the malicious person had used to upload and run on the hacked system. After finding the password for the “Sys” user in a bat file, I continued to search for similar files in case it contained the password for my encrypted files, but found no such file.
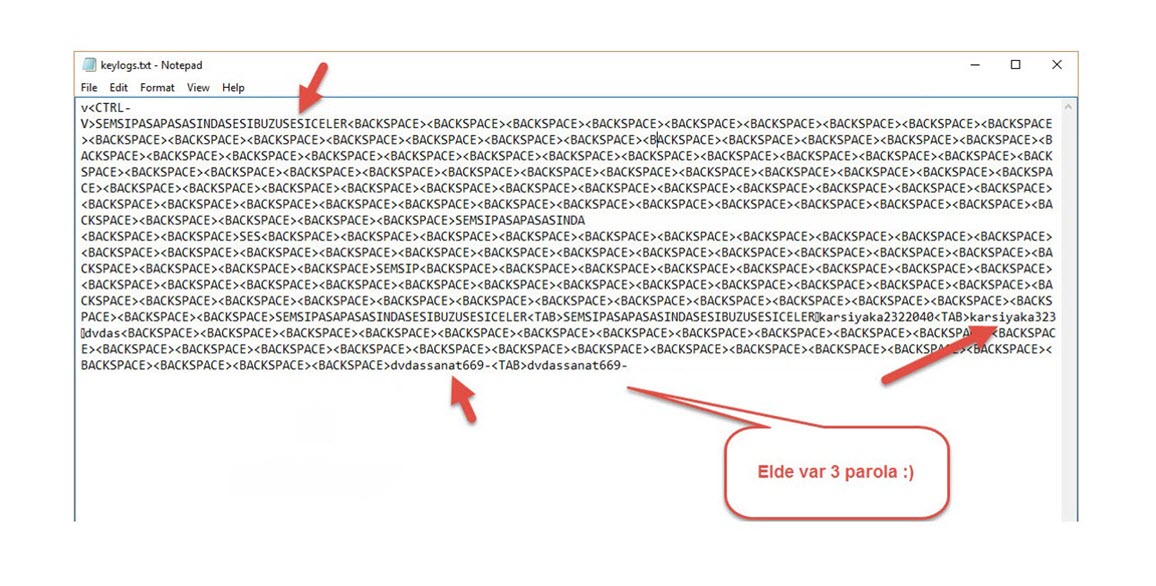
I noticed that the malicious person had a hard time typing in the password they had chosen to encrypt the accounting program’s folders due to the trap system copy-pasting and blocking file sharing. :) After struggling to type in the long password starting with SEMSIPASA, they had tried a password starting with KARSIYAKA and failed to type it in, and had finally decided on the password of DVDASSANAT669-. Without knowing they were being monitored, the malicious person had planned to encrypt the data and send it via email, but thanks to the deception system, I was able to decrypt the password with DVDASSANAT669- and clarify the situation for myself.
In conclusion, in order to combat ransomware, it is important to periodically backup your systems, store your backups in a secure location, check and disable unnecessary internet connections, and use strong passwords on your systems. This will make it more difficult for ransomware to achieve its nefarious goals in the short term.
Additionally, you can watch the video that the trap system recorded of the malicious person encrypting the data in the link below.
Hope to see you in the following articles.