I released the first version of the program on March 25 and notified several information security related sites and Darknet was one of them. At that time Darknet did not make any news but suddenly in last week, they changed their decision and made a news about a 6 months old software. It was old and got broken (online check was broken due to changes in Virustotal’s site) in 6 months and I did not have chance to fix bugs in a time. Recently massive download attempts forced me to fix bugs and release a new version.
Today I have released v1.2 which includes bug fixes. I highly recommend you to download and run the latest version.
Download Malware Check Tool v1.2
———————————————————————————————-
ABOUT
—–
This program intends to detect a malicious file in two ways; online and offline.
It calculates the md5 hash of a specified file and searches it in its current hash set (offline) or on virustotal site (online) and show the result.
It has http proxy support and update (for hash set) feature.
Coded for fun so enjoy it :)
CHANGELOG
———
v1.2 – New Virustotal changes implemented.
v1.1 – Wrong implementation of md5 calculation fixed. (Credit goes to roynal [.] smith [@] gmail [.] com)
USAGE
—–
python malware_check.py update
- This command updates its current hash set (hashset.txt) by crawling threat information from http://www.avira.ro
- Hashset.txt includes virus name, virus type, md5 hash of the virus, severity and discovered date.
- If there is no hashset.txt file, it will visit http://www.avira.ro and start gathering virus name,vvirus type, virus md5, severity and discovered date
- If there is a hashset.txt it just up to date its current hash set to the latest.
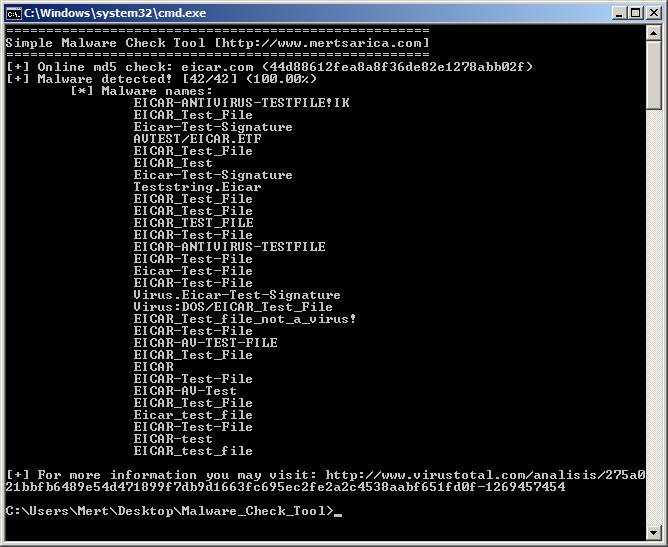
python malware_check.py online malware.exe
- This command calculates the md5 hash of a specified file (ex: malware.exe), submits it to http://www.virustotal.com and then shows the result.
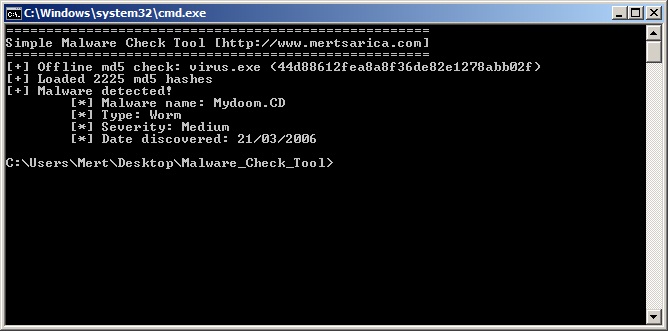
python malware_check.py offline malware.exe
- This command takes the md5 hash of the specified file (ex: malware.exe) and searches it in its current hash set (hashset.txt) and then shows the result.
Note: For http proxy support you have to edit malware_check.py and modify the required fields as shown below.
proxy_info = {
‘user’ : ‘username’, # proxy username
‘pass’ : ‘password’, # proxy password
‘host’ : “proxy host”, # proxy host
‘port’ : 8080 # proxy port
}
CONTACT
——-
Author: Mert SARICA
Email: mert [ . ] sarica [ @ ] gmail [ . ] com
URL: http://www.mertsarica.com








15 comments
VirusTotal has updated it website, this tool is not work now. Hoping you can make a update for it, thanks!
i tested it is great tool. my question:
is it possible to scan all the file for example c:\ drive calculate md5 value and submit to virustotal?
Virustotal will restrict the batch of md5 value?
Hello,
It is not possible with the current version but I’ll think about adding that feature for the next version (will take 3+ months due to military duty).
Regards,
thank for tool
—————–
[email protected]
Your welcome :)
Thanks M.S!
I think I have missed one point, that is a “rescan” option to force to scan again to get the latest result.
I would like to ask, is it possible to have “upload-to-scan” function? I mean when a file has not uploaded for scanning yet, then upload the file to scan and then get the result.
I dont have time for coding that at the moment but have added it to my todo list.
Still have problem in some files. I have replied an email to you.
Please test it if it is again regular expression problem?
Fixed.
I tested v1.3, but I found some problems on showing the correct names or results. I have sent a email to you with an attachment of the scan results.
I assume that it is fixed now…
Waiting for a version with corresponding AV names!
I’ll try to prioritize it roynal, nowadays I have been working on writing a new article for my visitors, thanks for your patience :)
Here is the newest version (v1.3), please test it and then share your experience :)