Microsoft Office Macro Analysis
Some of you, who are the same age as me or older might remember the Melissa malware that spread through Microsoft Office Word macro in 1999 and affected millions of systems worldwide. Melissa malware was spreading by sending the first 50 people on Microsoft Outlook in the system it was
infected with the help of macro support that came with Microsoft Office.
If you are asking “What is a macro ?”, Microsoft company will answer you as stated below;
A macro is a series of commands and instructions that you group together as a single command to accomplish a task automatically.You can record a sequence of actions, or you can write a macro from scratch by entering Visual Basic for Applications code in the Visual Basic Editor. However, malware can also use this functionality to download threats onto your PC. Macro malware usually hides in Microsoft Word or Microsoft Excel documents.
Throughout the years because of the misuse of macros (the abuse), Microsoft company did some security improvements on Office software. One of these improvements was new file extensions that were released with Office 2007 version. For example, if a file that was created with Office 2007 has the letter m in the file extension, this means the office file includes a macro. With this improvement, we were able to be cautious towards the files that have the letter m in their extensions and block them based on their extensions.
You could be saying why are you telling us all these since it’s been 20 years after Melissa virus and Microsoft did what they could about the situation. Recently we can see malicious online banking software’s and malwares like RAT trying to be spread across by using office files that include macros. Because malignant users know that the file extensions with letter m get attention, they create the macro files by using Office 2003 hence, they are able to get past the systems and informed users that do extension checks.
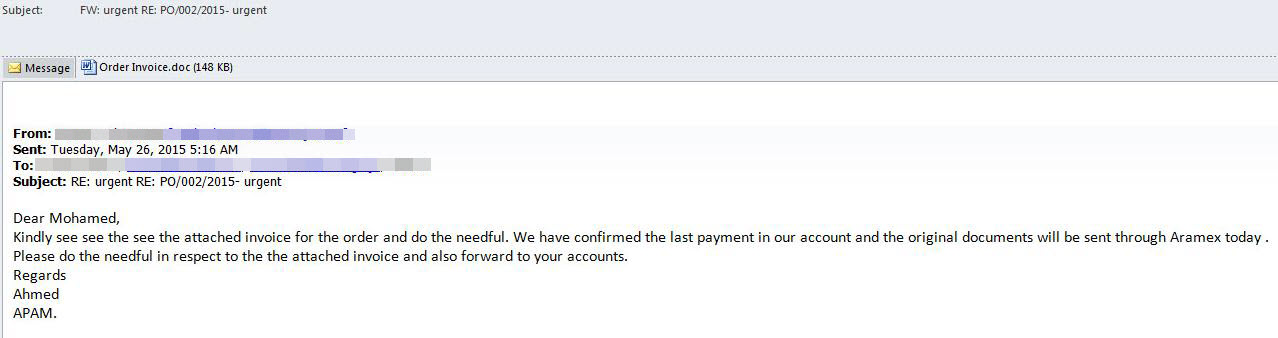
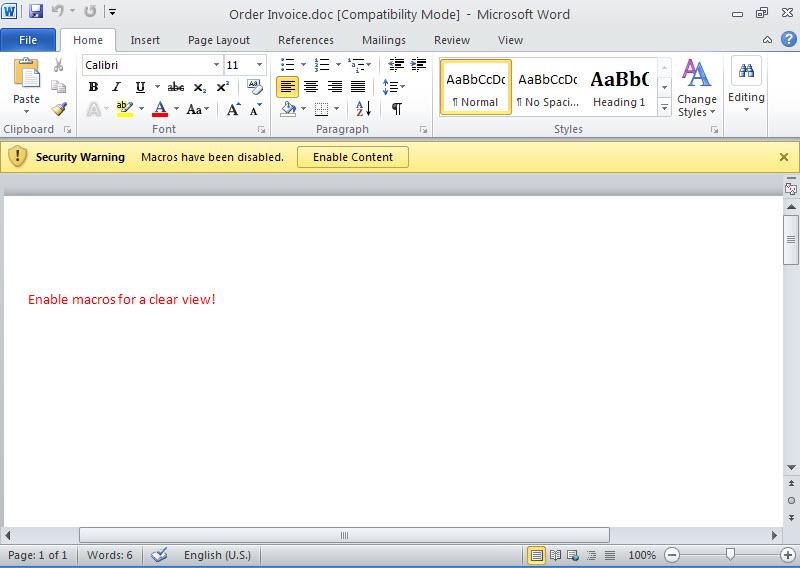
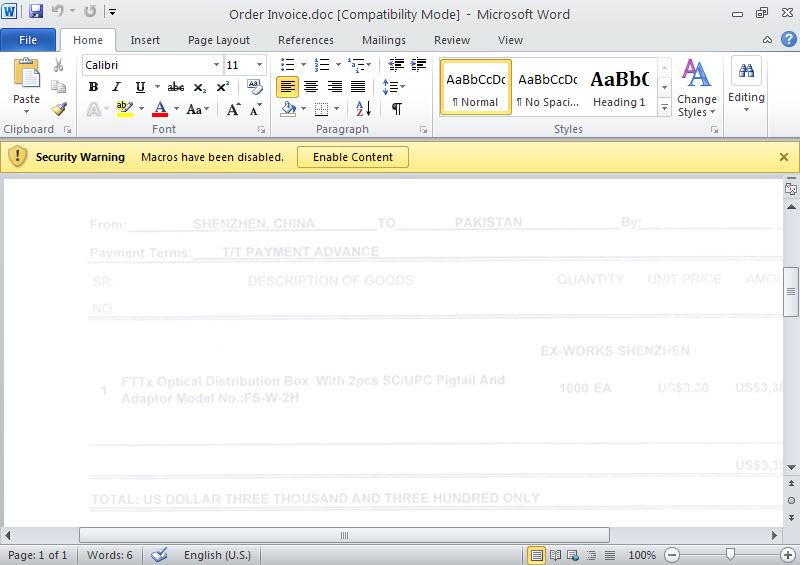
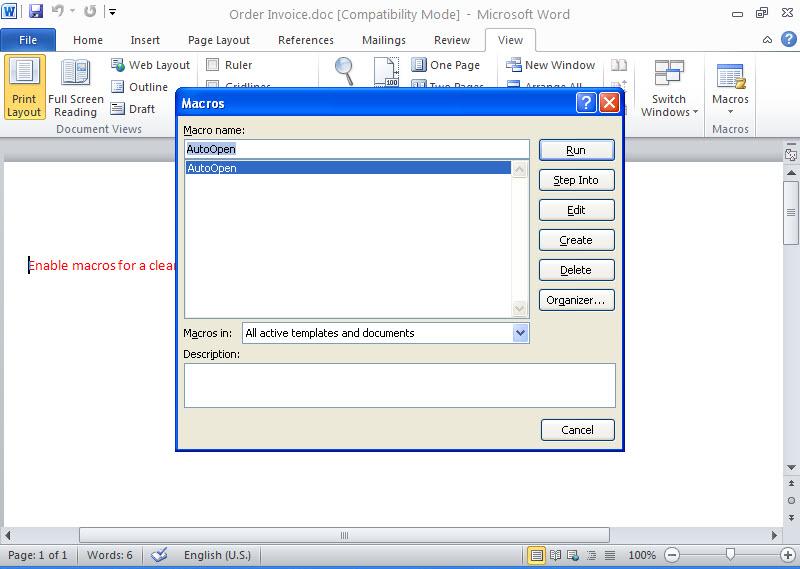
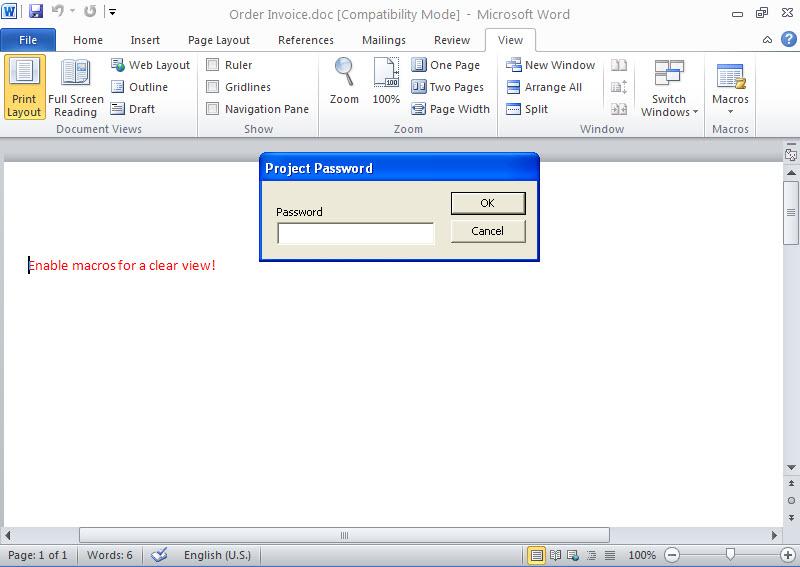
Well then, how can we analyze a file that we thing has a macro? We can open the office file with Microsoft Office software in a virtual machine then we can display the contents from the Macro menu (view -> macros -> view macros). However, malicious users that know this way usually put password protection to the macro. To be able to solve this password you can use Reset VBA Password tool.
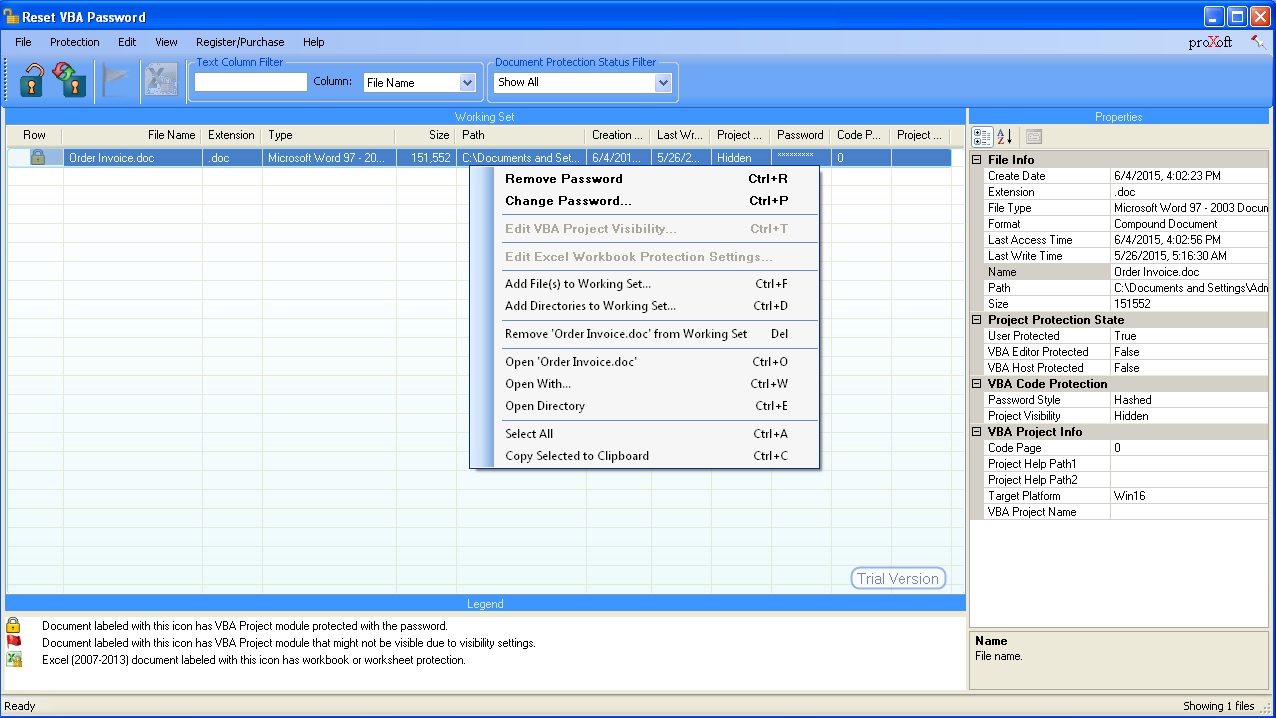
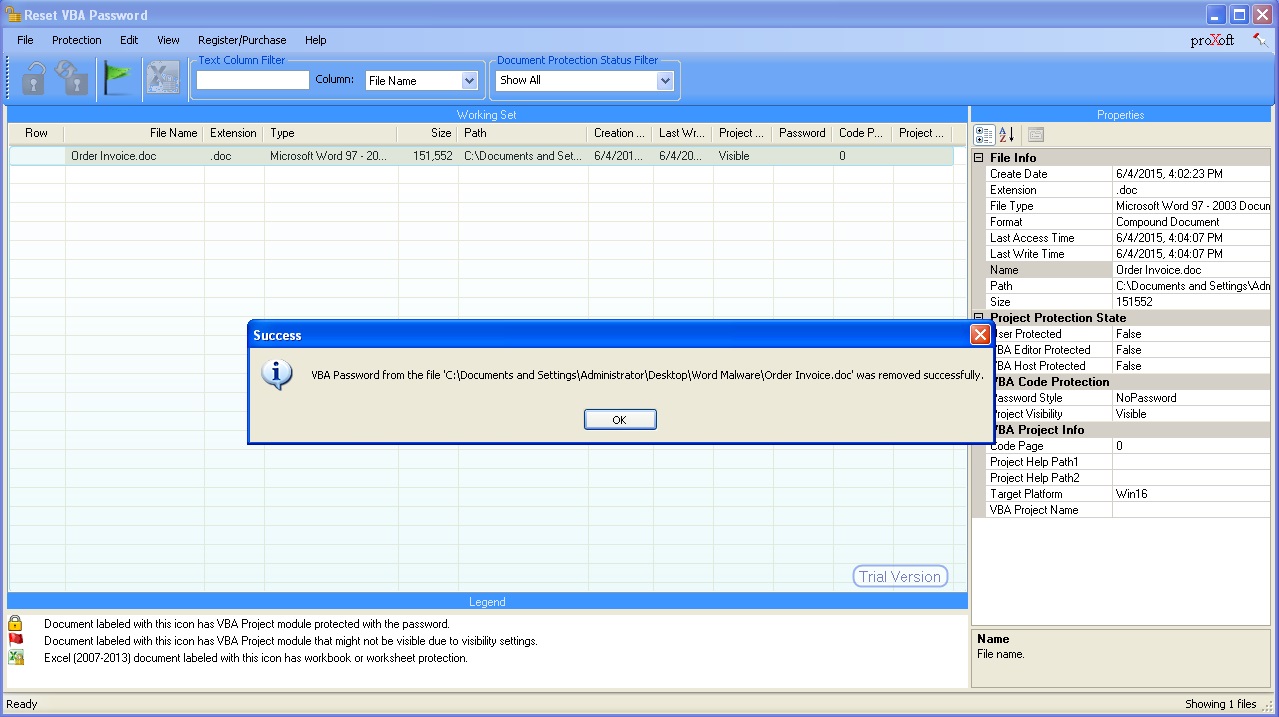
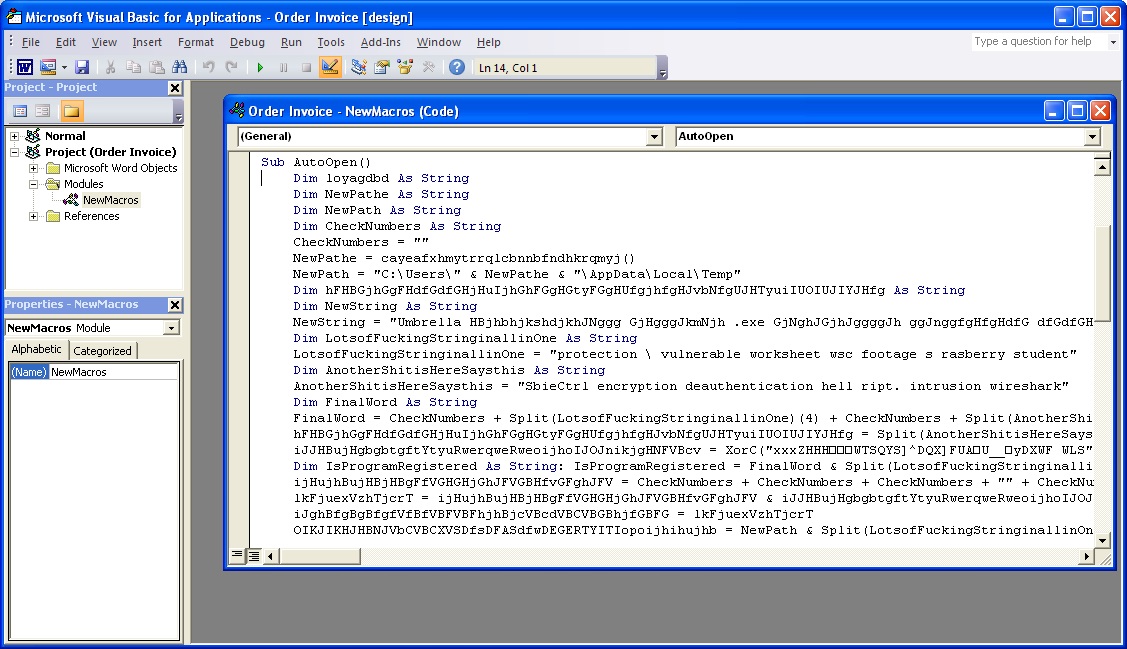
It is also possible to analyze an office file that you think has a macro without Microsoft Office and this is possible with OfficeMalScanner tool. OfficeMalScanner is a very beneficial tool that helps us analyze suspicious (shellcode, PE detection) office files and also help us extract the macro code it found inside the office file for us to analyze.
For example, if we have a suspicious file that we think was created using Microsoft Office 2003 like I mentioned above, you can give this tool info command as a parameter and let the tool analyze the file and extract the macro code for us. If the file in hand is created with Microsoft Office 2007 or later, we can use the inflate command (actually no different than changing the office file extension to .zip then opening it with winzip/winrar) to make the tool open the file and extract the macro code inside the file with once again info command.
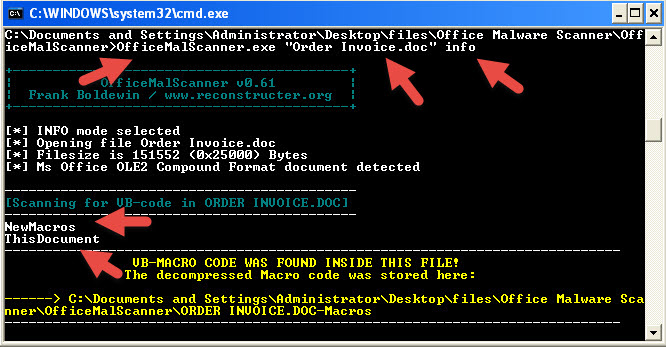
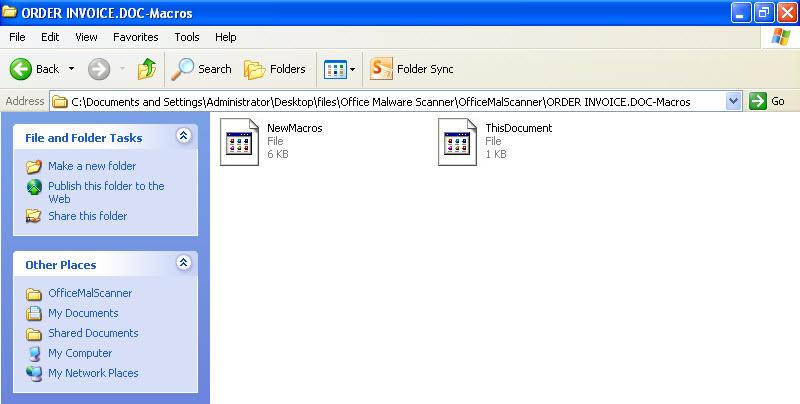
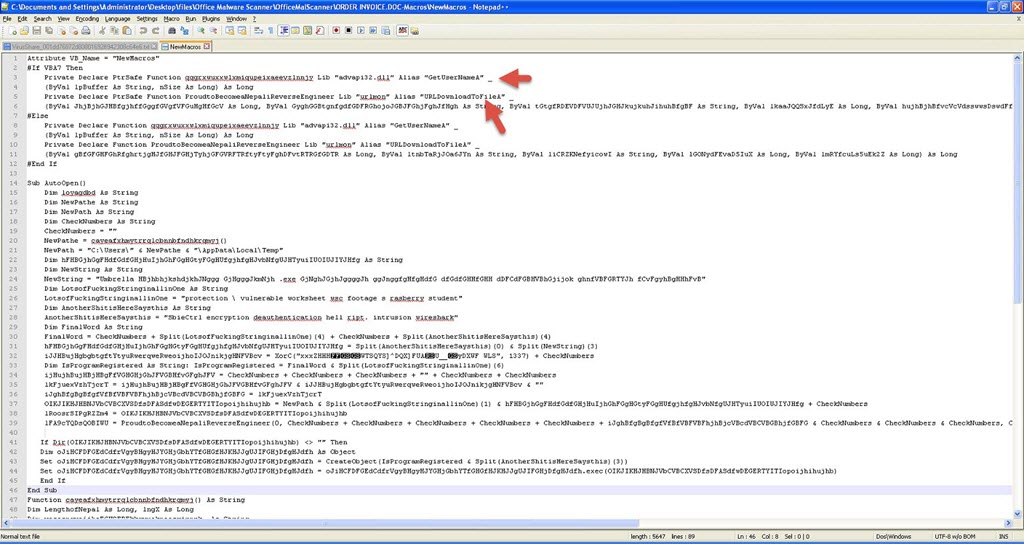
When we analyze the macro code that came up, we can see that it is a downloader that downloads RAT type malware by inspecting the used API’s.
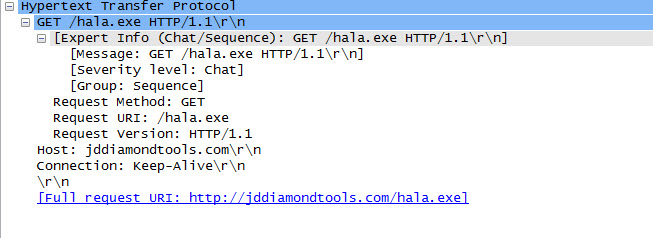
Hope that this post will be helpful for you to analyze suspicious office files. See you on the next post and have a secure day.
Original Article: Microsoft Office Makro Analizi
Translated to English by: Hüseyin Fatih Akar | Twitter: @thehakar)