This story began on May 4, 2022, with an email from a reader named Erman ATEŞ. In his email, Mr. Erman, a conscious and sensitive father, stated that smart kids’ watches are increasingly being preferred by many parents for valid reasons, but due to their lack of conformity to standards in terms of software, security, and privacy, and also due to a message he saw on Instagram, he began to worry on behalf of all parents and asked me to focus on this issue. As a security researcher who always listens to readers, as in my blog posts Instagram Scammers, Backdoor Hunting, Hacker Hunt with a Deception System, I decided to address this issue for the benefit of society and awareness of information security.
Upon looking at the following photo, are kids’ smartwatches really a tremendous technological boon for parents to keep their children under surveillance?
Or, upon looking at the following other photo, are parents unwittingly putting their own and their children’s privacy and secrecy of their private lives at risk with a watch-like potential spy device that allows for audio surveillance?
To find answers to these questions, I decided to purchase a children’s smartwatch that was affordable in terms of price for my security research. For this, I began to examine the Kid’s Smartwatches categories on shopping sites such as Hepsiburada and Trendyol. After looking at the most popular watches with the most reviews and ratings, I decided on a brand and model with over 1000 ratings and purchased it.
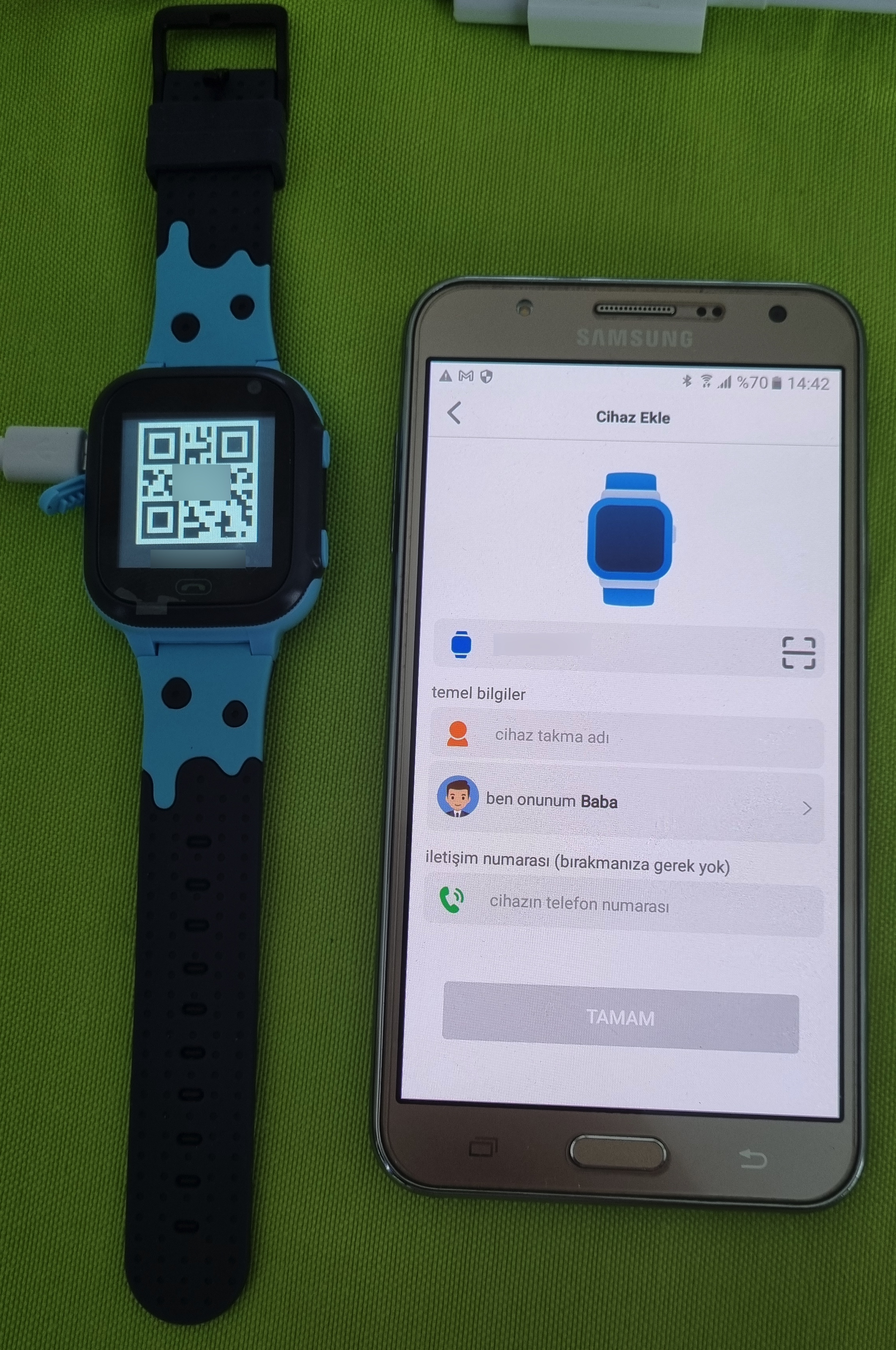
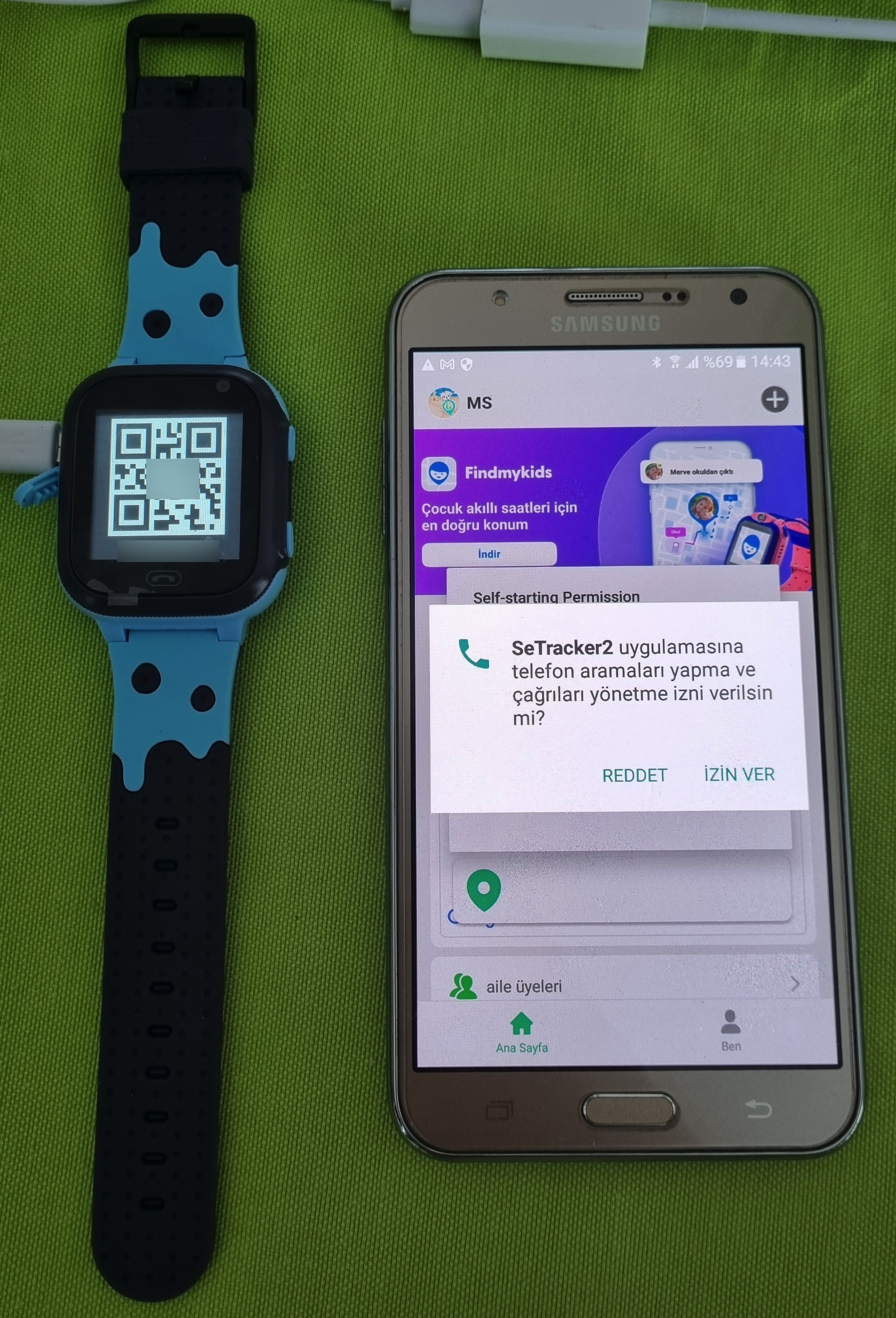
When I took the watch out of the box and looked at the installation guide, it stated that an Android or iOS mobile application developed by a Chinese company called 3G Electronics was required to remotely manage the watch.
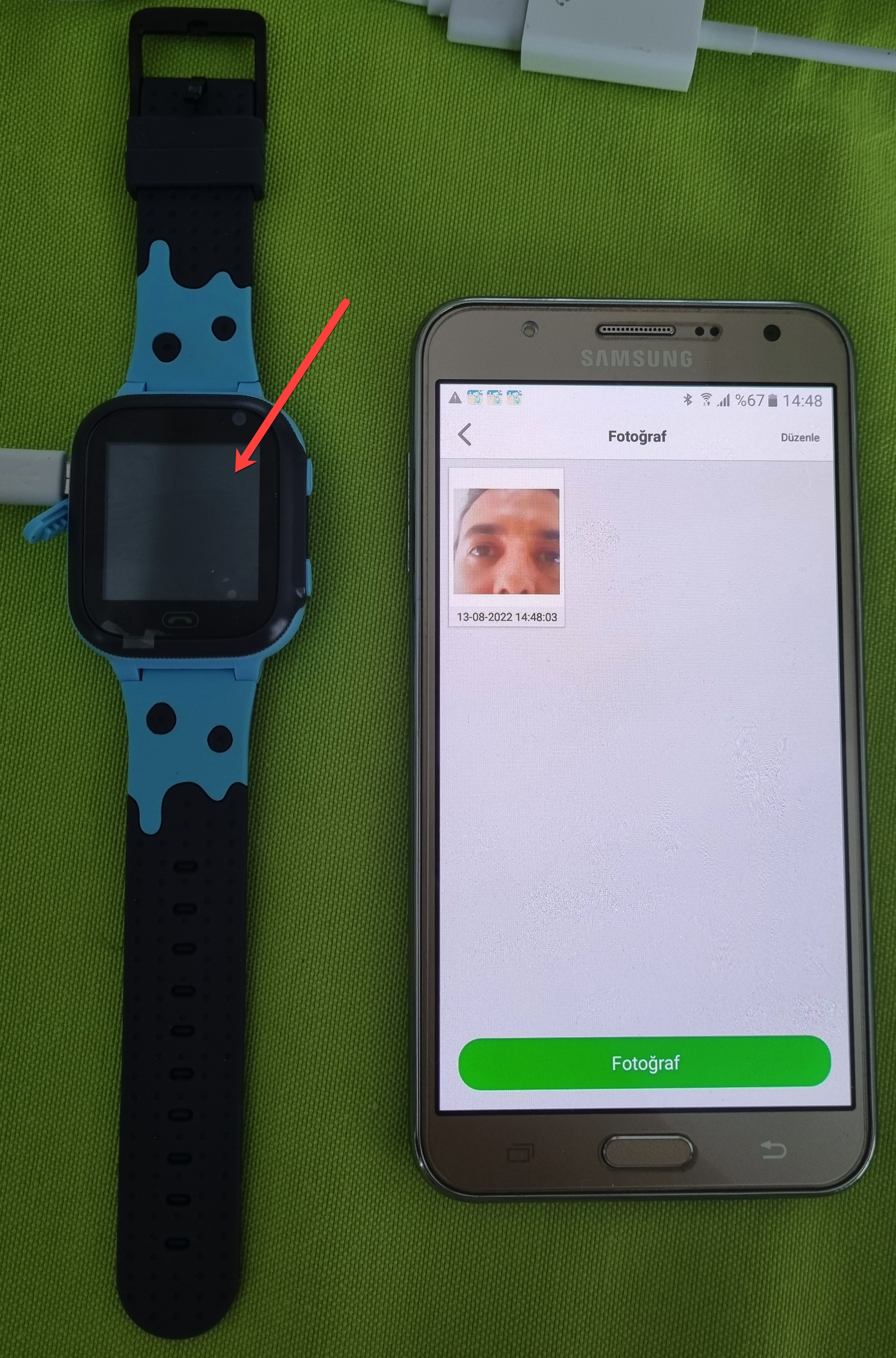
Upon examining the information collected by the SeTracker2 app, I saw that it collected personal, sensitive, and potentially private information ranging from location, audio, and video recordings, to the contact list, name, phone number, and email address.
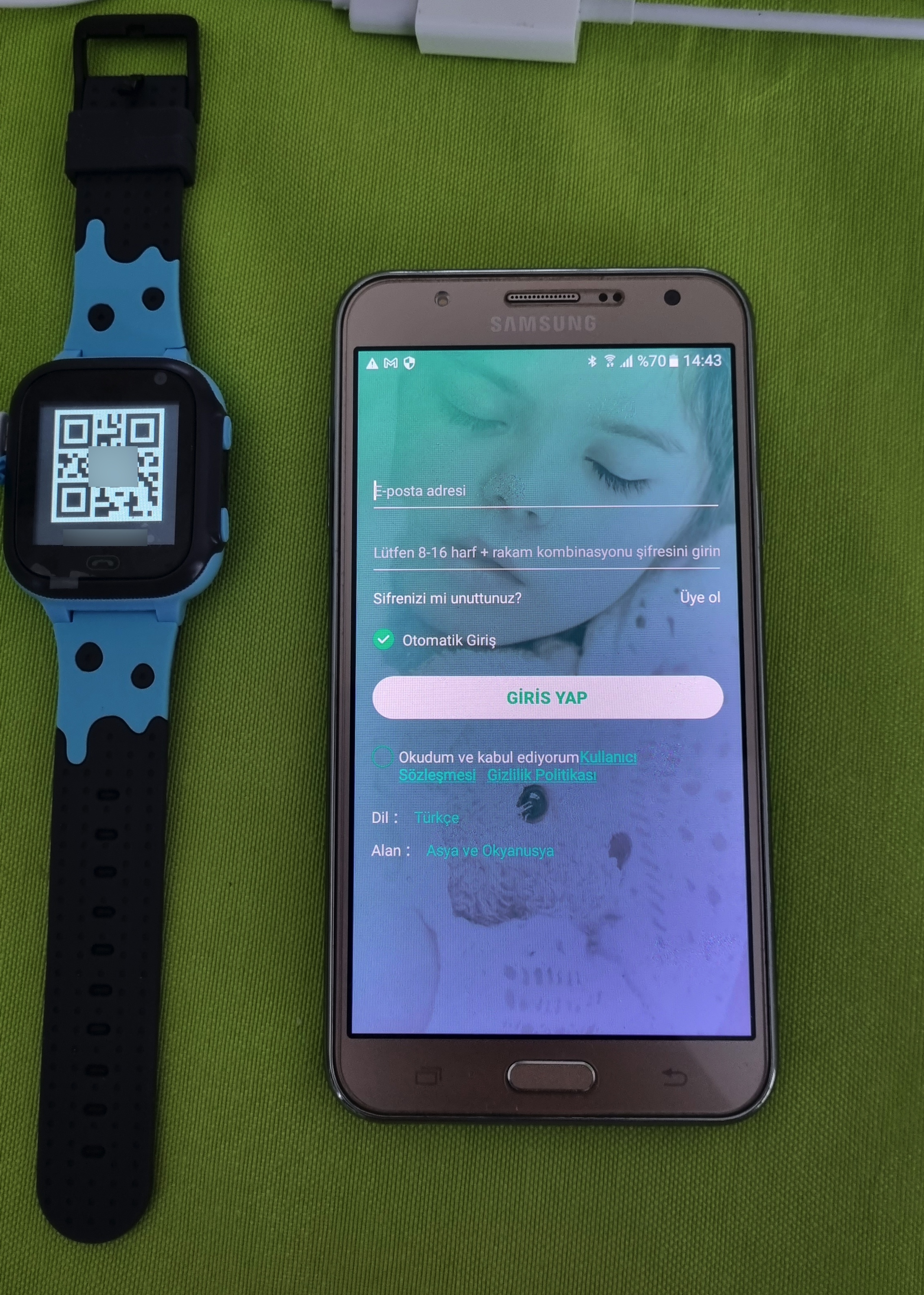
After inserting a SIM card into the watch and turning it on, I opened the SeTracker2 app and registered. Then, after pairing the app with the watch, I began to examine the app and the menu steps.
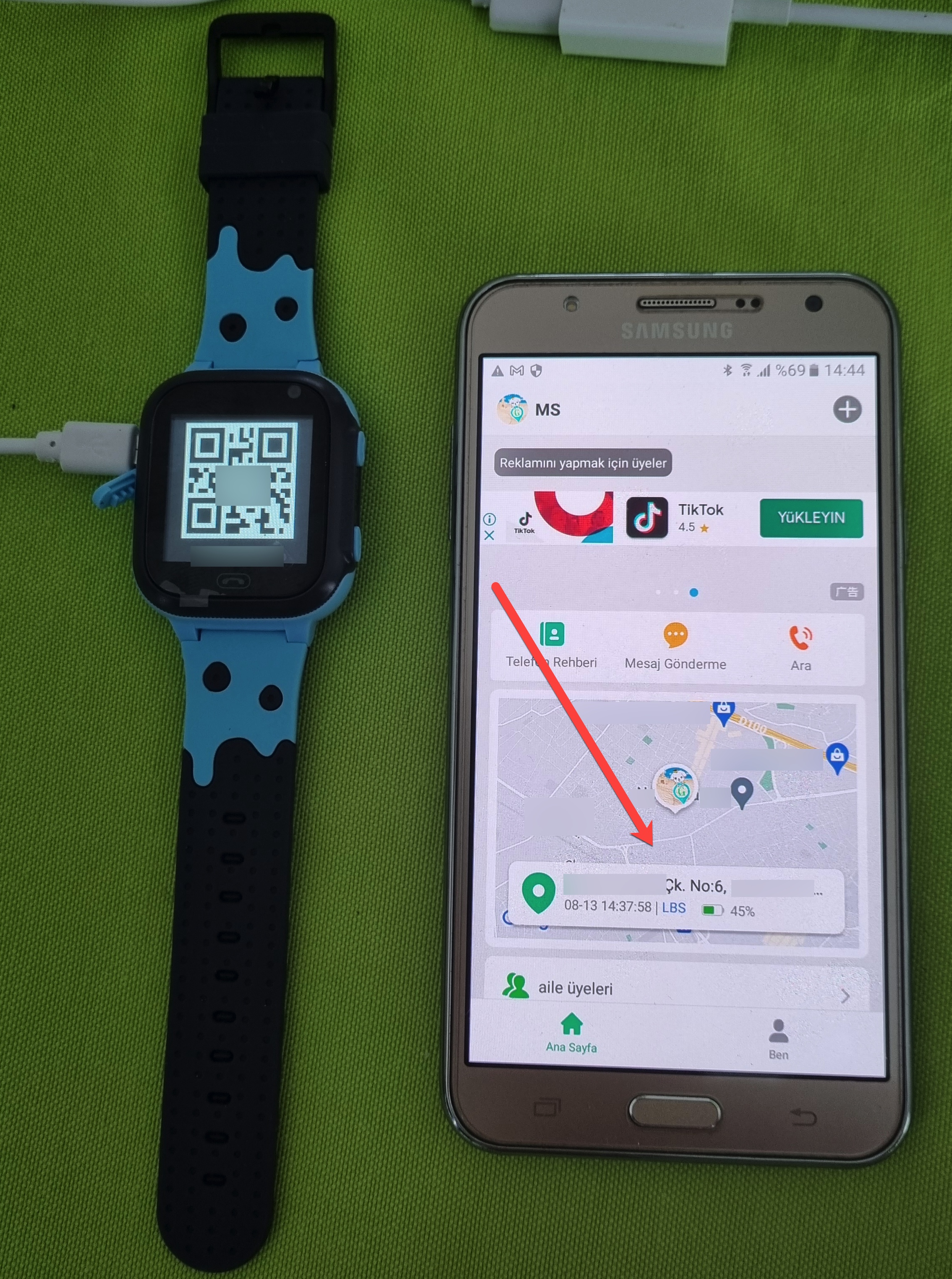
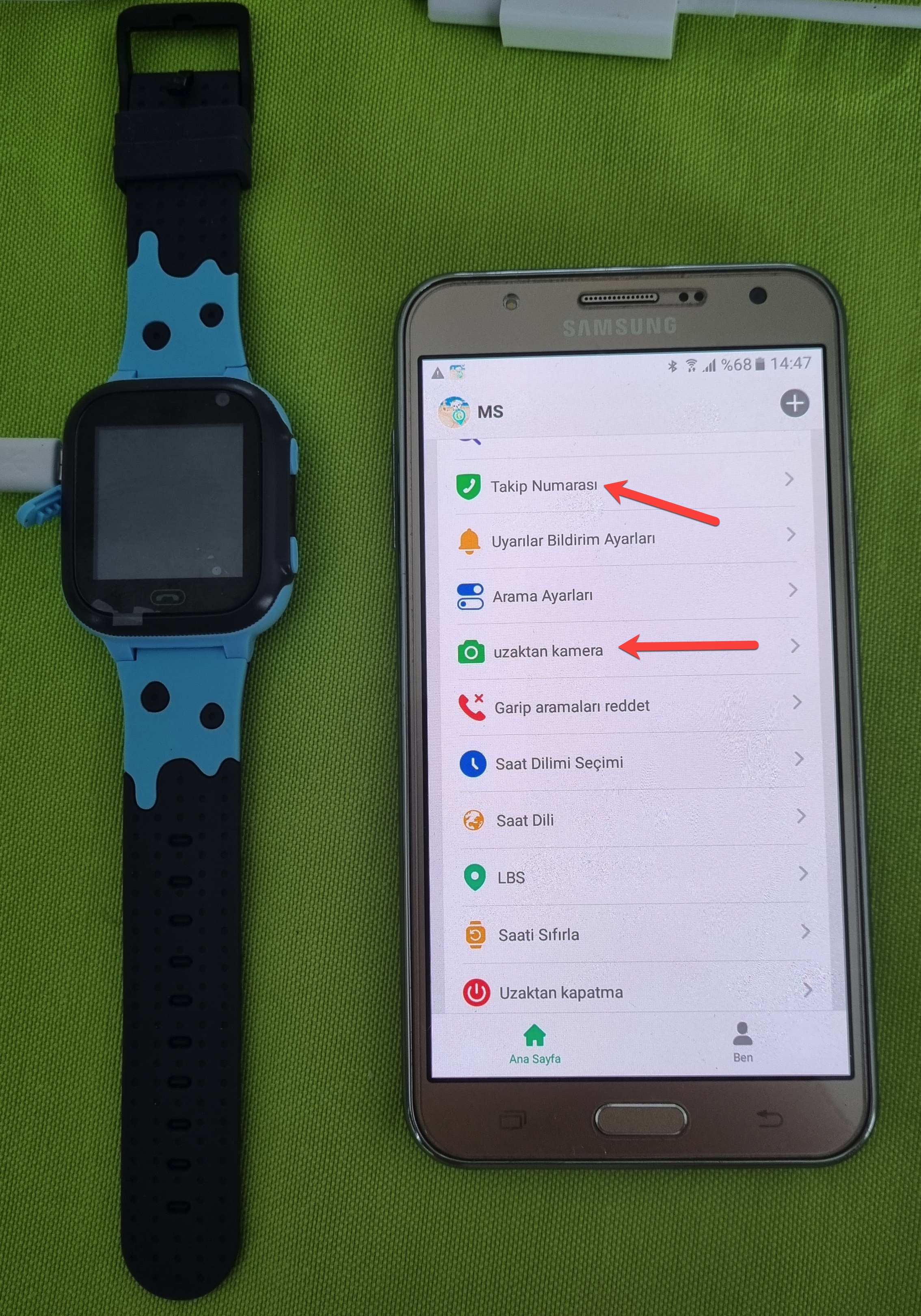
The first thing that caught my attention in the app was the ability to track the watch on a map in real-time, followed by the Tracking Number and Remote Camera menu steps. The Remote Camera menu allows you to take photos with the watch’s camera at any time. The watch does not produce any visual or auditory alerts at this time. The Tracking Number menu allows you to make the watch call the entered phone number, and audio surveillance can also be performed using the watch’s microphone. Again, as in the Remote Camera step, the phone does not provide any alert that surveillance is being performed.
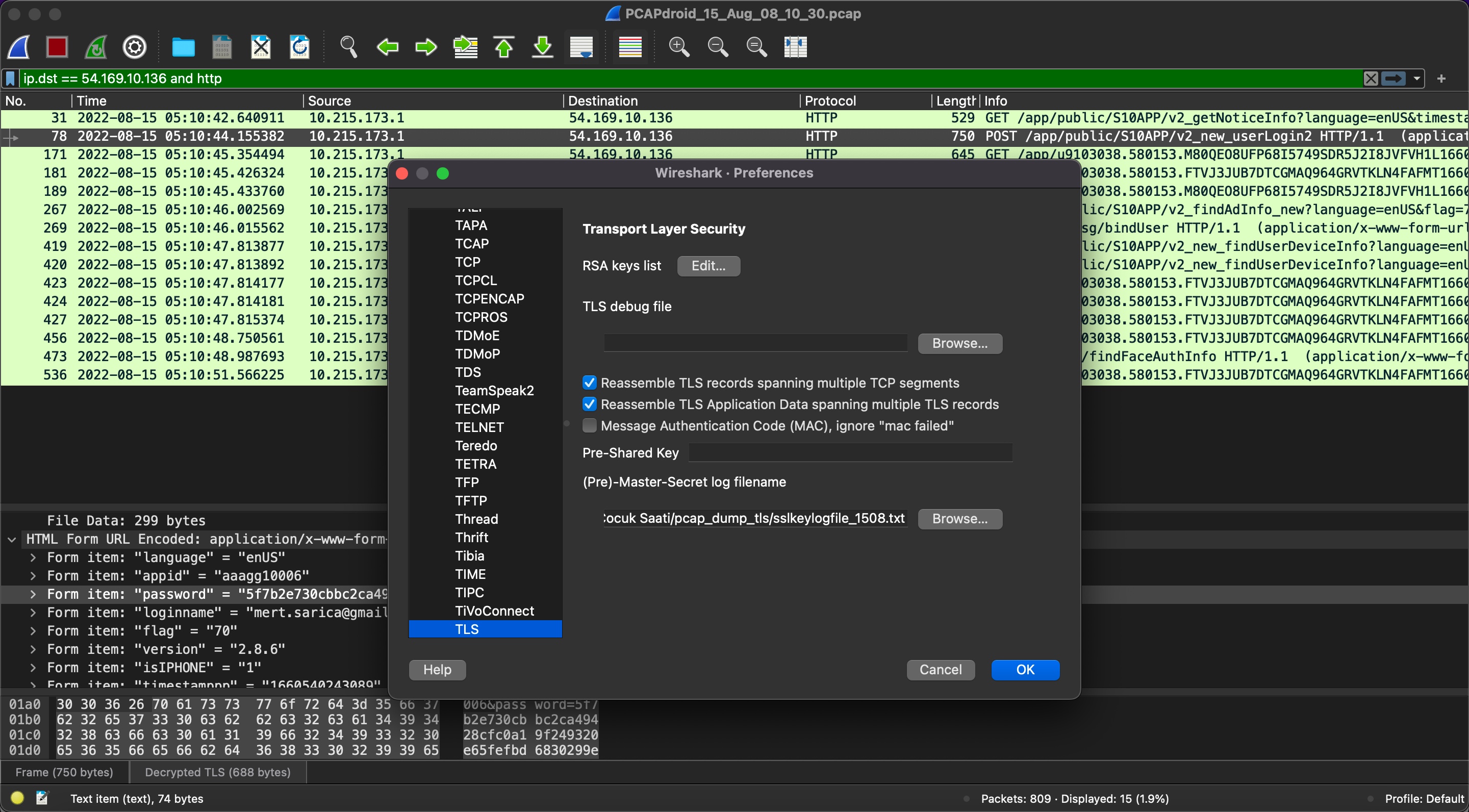
“Oh, how wonderful, we can track and listen to our child in real-time,” you might think. But let’s suppose that the email address you used to log in to the SeTracker2 app, and the password you could not strengthen by using special characters, was stolen or guessed by malicious people for a moment. A malicious person could violate your privacy and secrecy of your private life by accessing the app through the watch on your child’s arm and tracking their location in real-time, taking their photo, sending messages, deleting the sent message without leaving a trace, and making the watch call the phone number specified to perform ambient listening. In addition, let me emphasize that there is no chance of accessing the log of all these operations performed by a malicious person through the SeTracker2 app!
“I am very careful and cautious and don’t easily fall into the hands of scammers,” you might say. But if you use the same password for multiple websites during login, one of those websites may have already been hacked, and your username/email and password may have been obtained. If you do not use Multi-factor Authentication (MFA) (the SeTracker2 app does not support MFA!), remember that malicious people can easily log into websites and mobile applications (such as the SeTracker2 app) where your account is with the information obtained!
Multi-factor authentication (MFA; encompassing two-factor authentication, or 2FA, along with similar terms) is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism: knowledge (something only the user knows), possession (something only the user has), and inherence (something only the user is). MFA protects user data—which may include personal identification or financial assets—from being accessed by an unauthorized third party that may have been able to discover, for example, a single password.
Another important issue is that you may inadvertently commit a crime through your child using watches with audio surveillance feature.
I hope that those familiar with my security research, especially my blog post titled Run Mert Run expect to see in this article how the vulnerabilities I identified through reverse engineering, static and dynamic code analysis of the SeTracker2 application can be exploited, or how a hardware vulnerability I discovered can turn the watch into a spy device. After all this, I believe that I can clearly convey that these watches, through the SeTracker2 application, invite malicious individuals to use them for nefarious purposes and pose a significant danger to parents and children. :) Still, anybody who wants to learn more about the application’s technical aspects can take a look here and here for studies that were conducted in previous years.
I hope that, like the example set by the decision taken by Germany in 2017, our authorities will also take a similar decision and ban the sale of these potential spy devices that look like watches on shopping websites, thus bringing an essential step towards protecting parents and children from such dangers.
In light of this information, I strongly recommend that those who use smart children’s watches that can record their surroundings use them with awareness of the risks. Please share this article with other parents, friends, and loved ones to create awareness.
Hope to see you in the following articles.
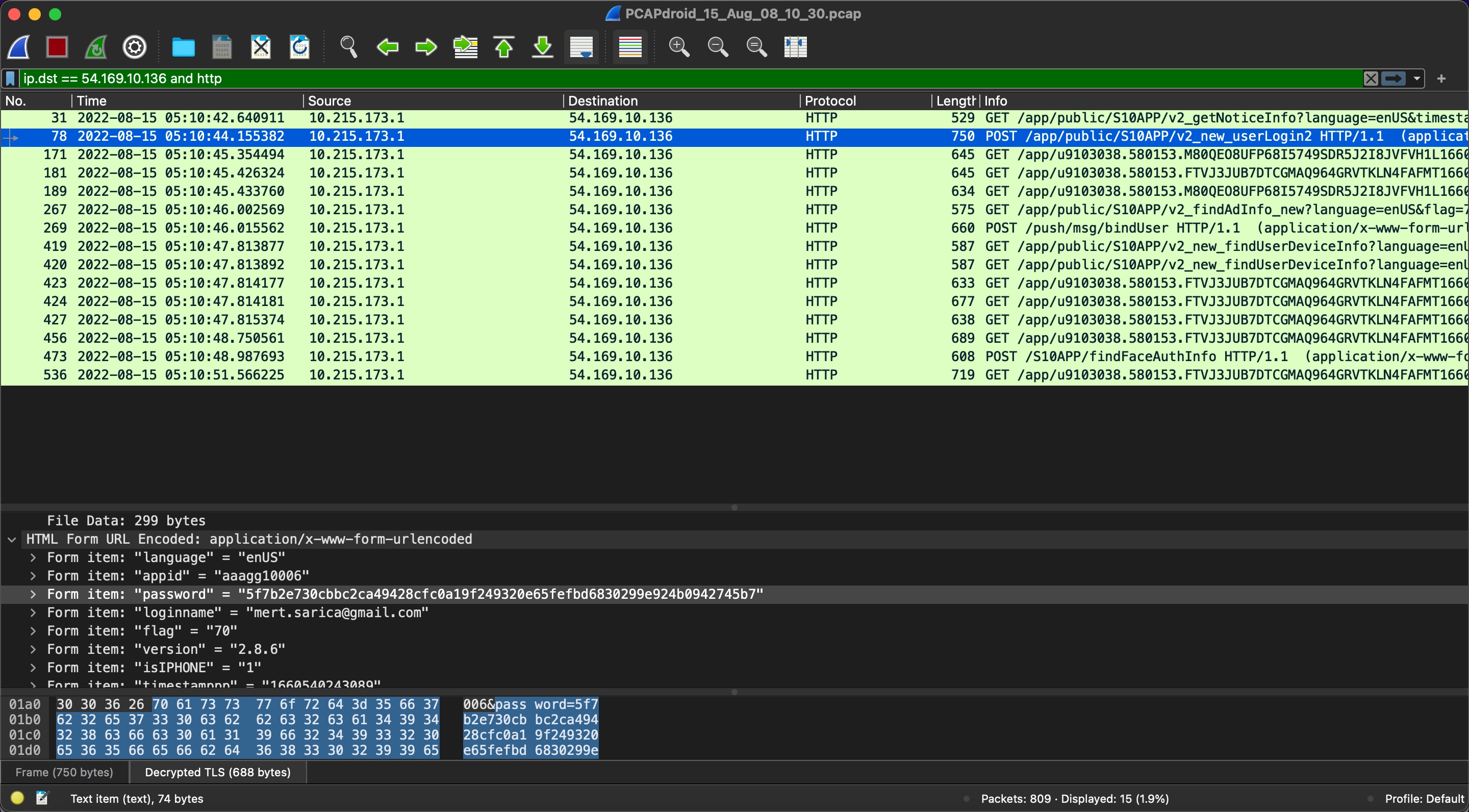
Note: For my technical readers, I would like to share that the SSL Pinning method is used in the SeTracker2 application, and through the use of a simple Android application called PCAPdroid, it is possible to record and analyze HTTPS traffic. This can be done quickly by recording the traffic and then analyzing it using the Wireshark tool.