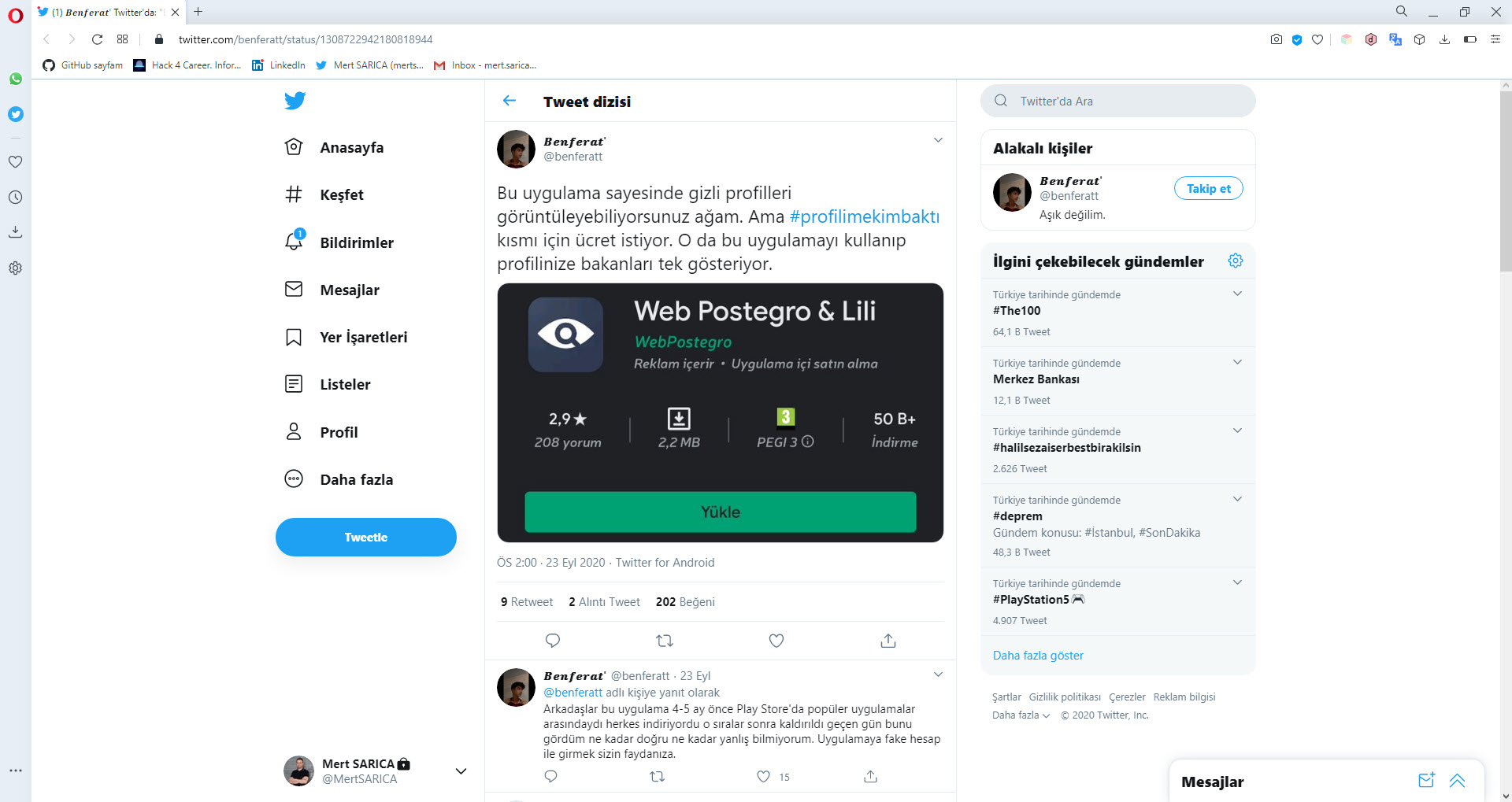
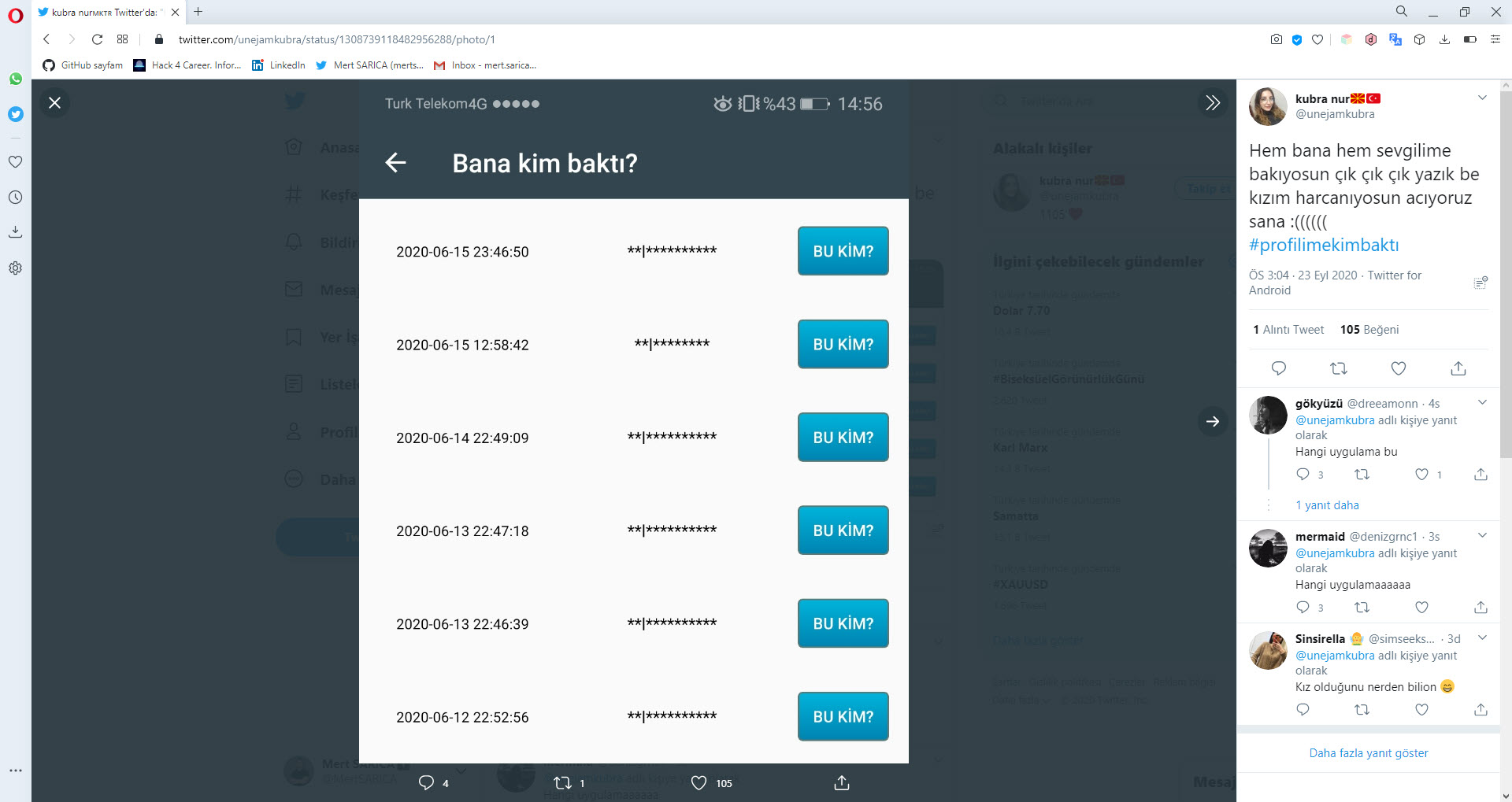
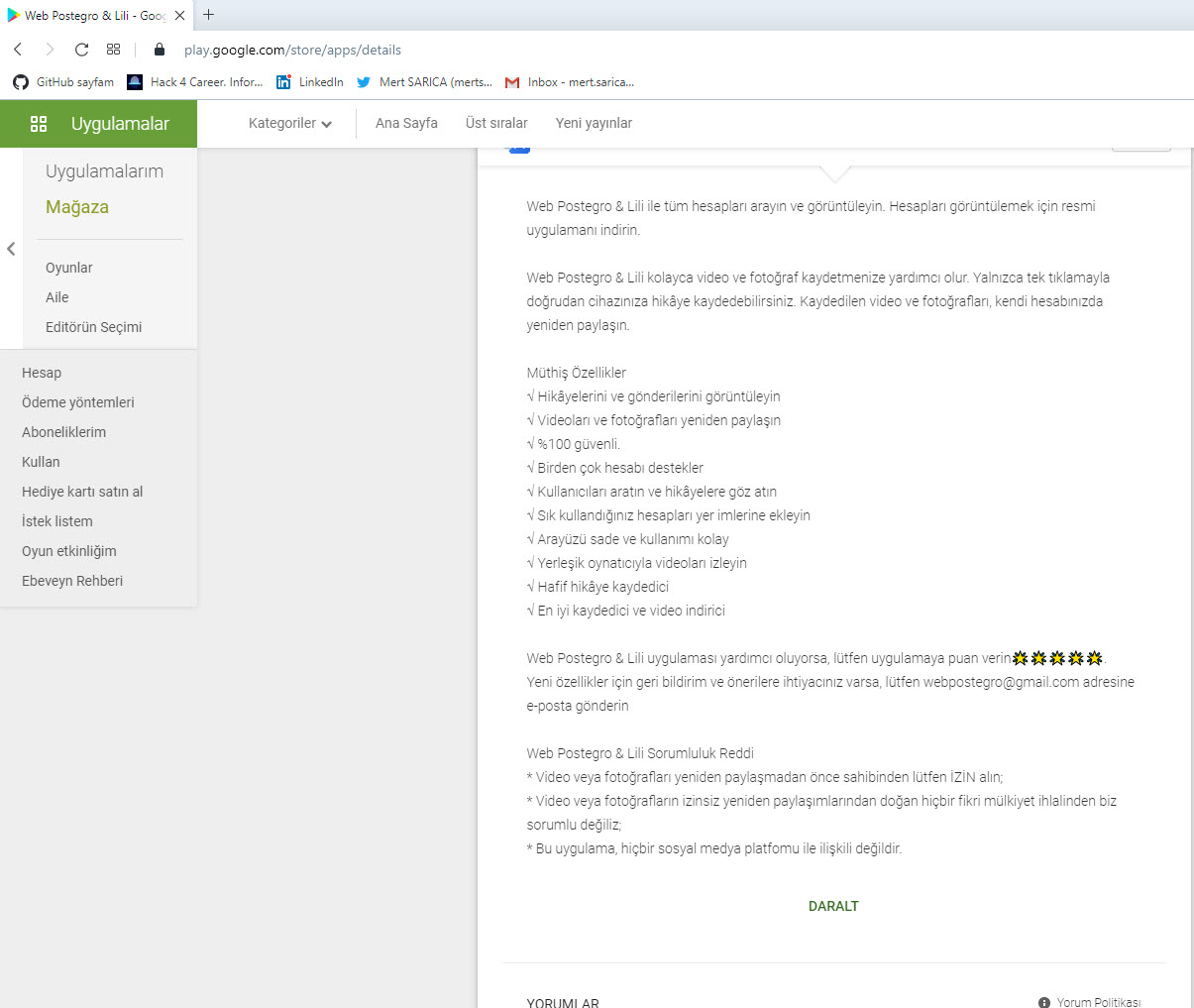
On September 23, 2020, while browsing cybersecurity-related news on Twitter, I noticed the hashtag #profilimekimbaktı in the trending topics. I decided to check the accounts sharing this hashtag as it raised suspicion. One of the accounts had written in their message that the Android app Web Postegro & Lili showed who viewed their profile.
Except for LinkedIn, I have always approached social networks like Twitter, Facebook, and Instagram with skepticism because I know that they do not share the information of profile viewers. I downloaded and analyzed this Android application and wrote about it to understand if my suspicions were justified.
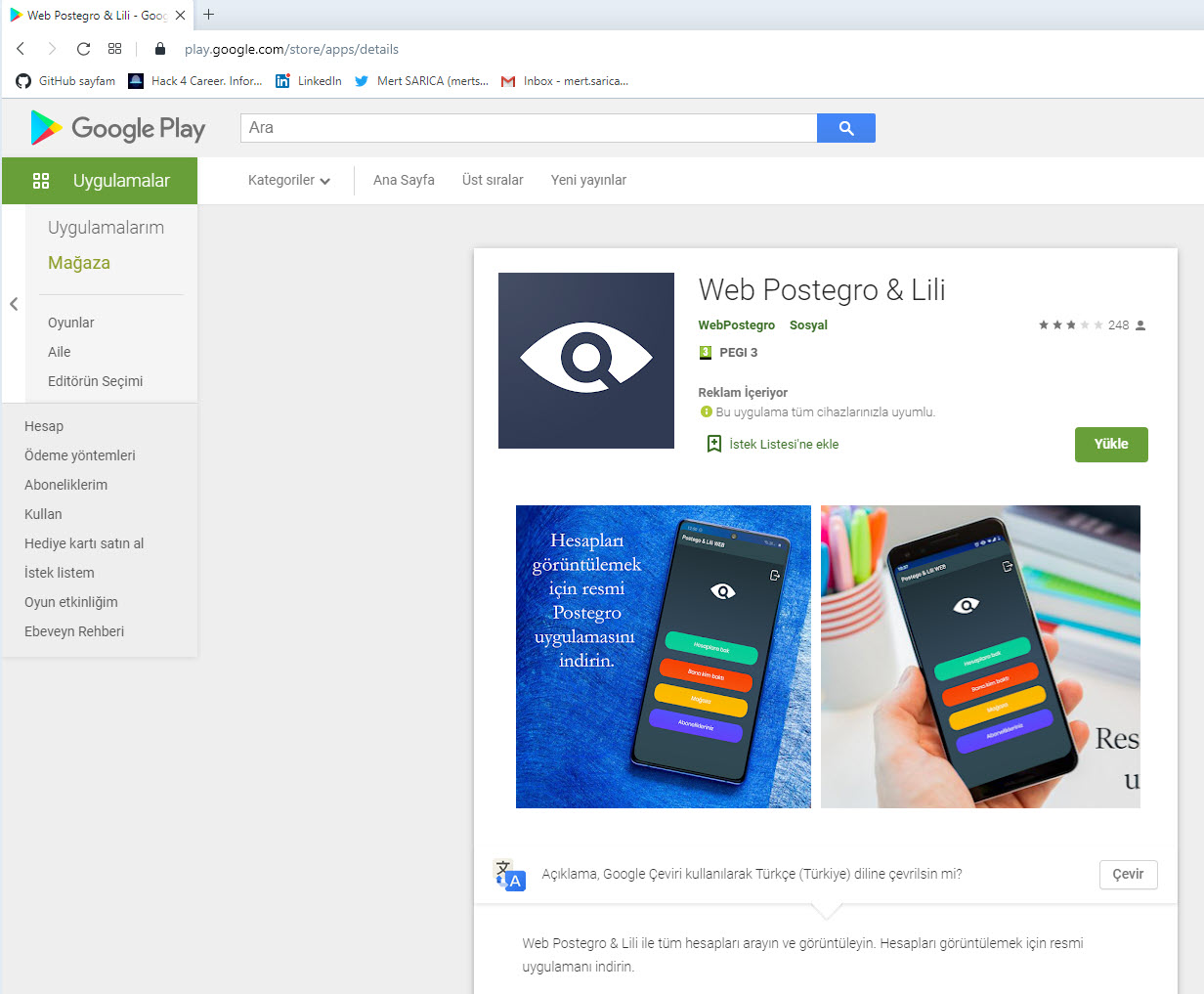
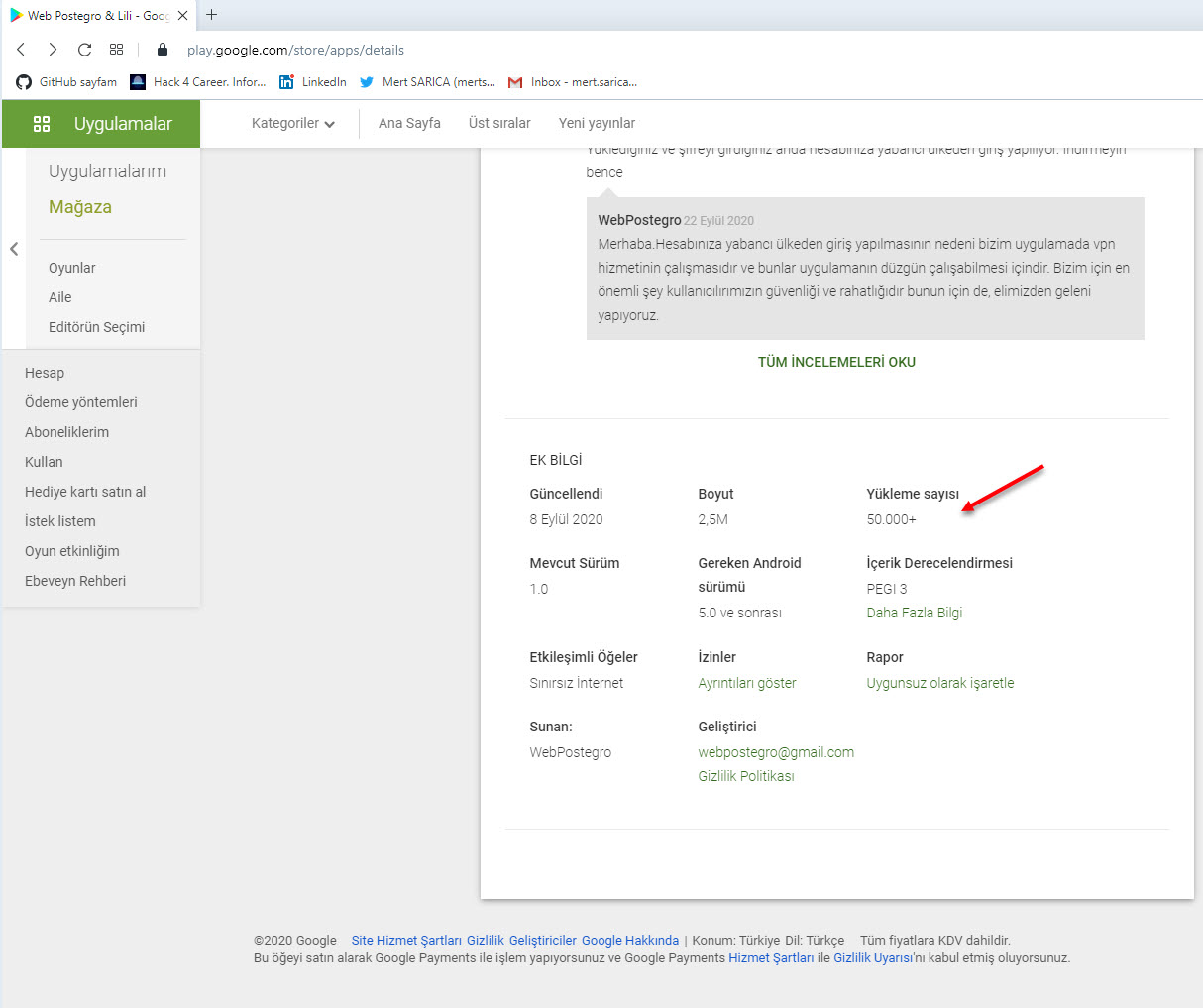
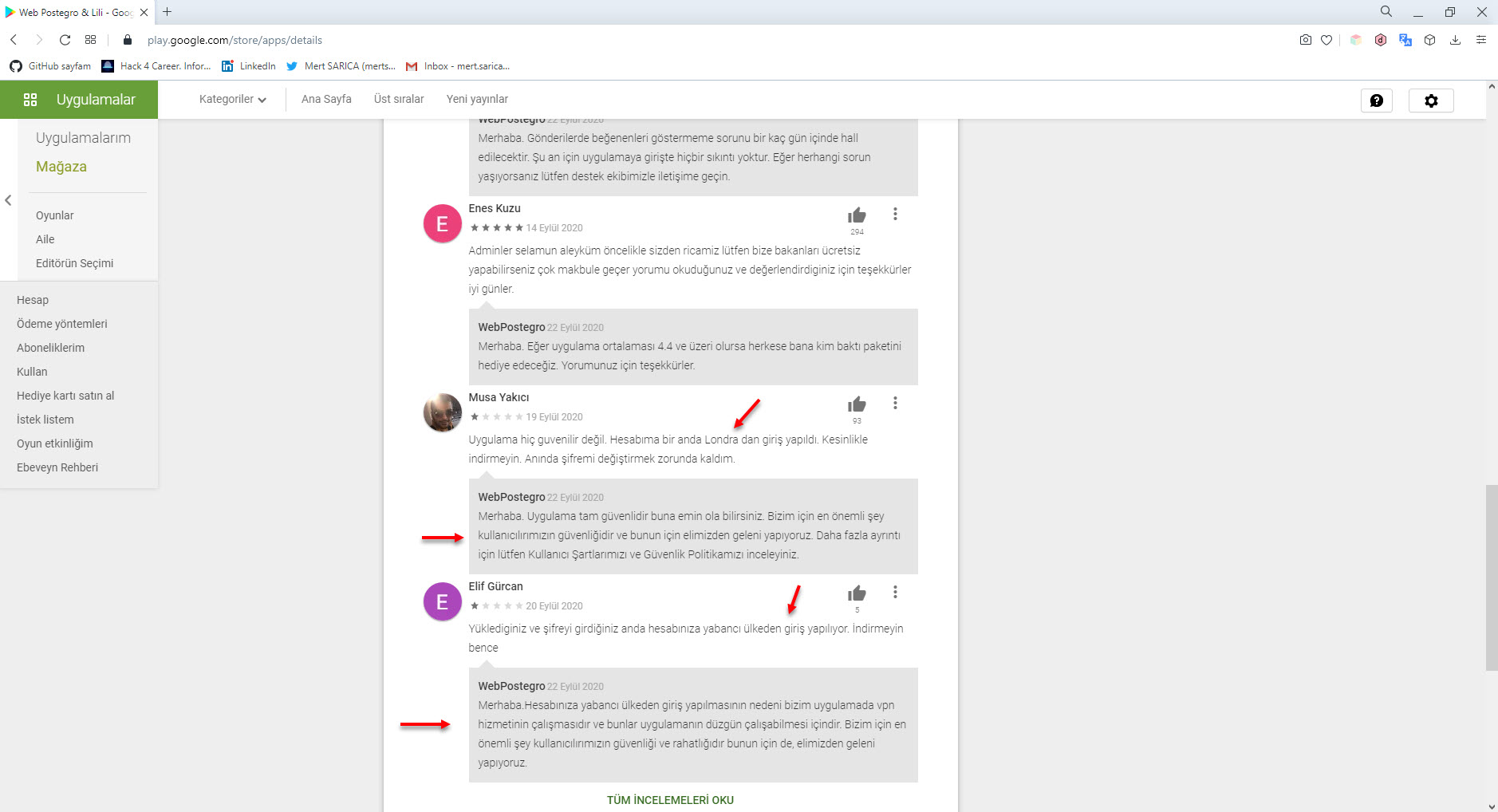
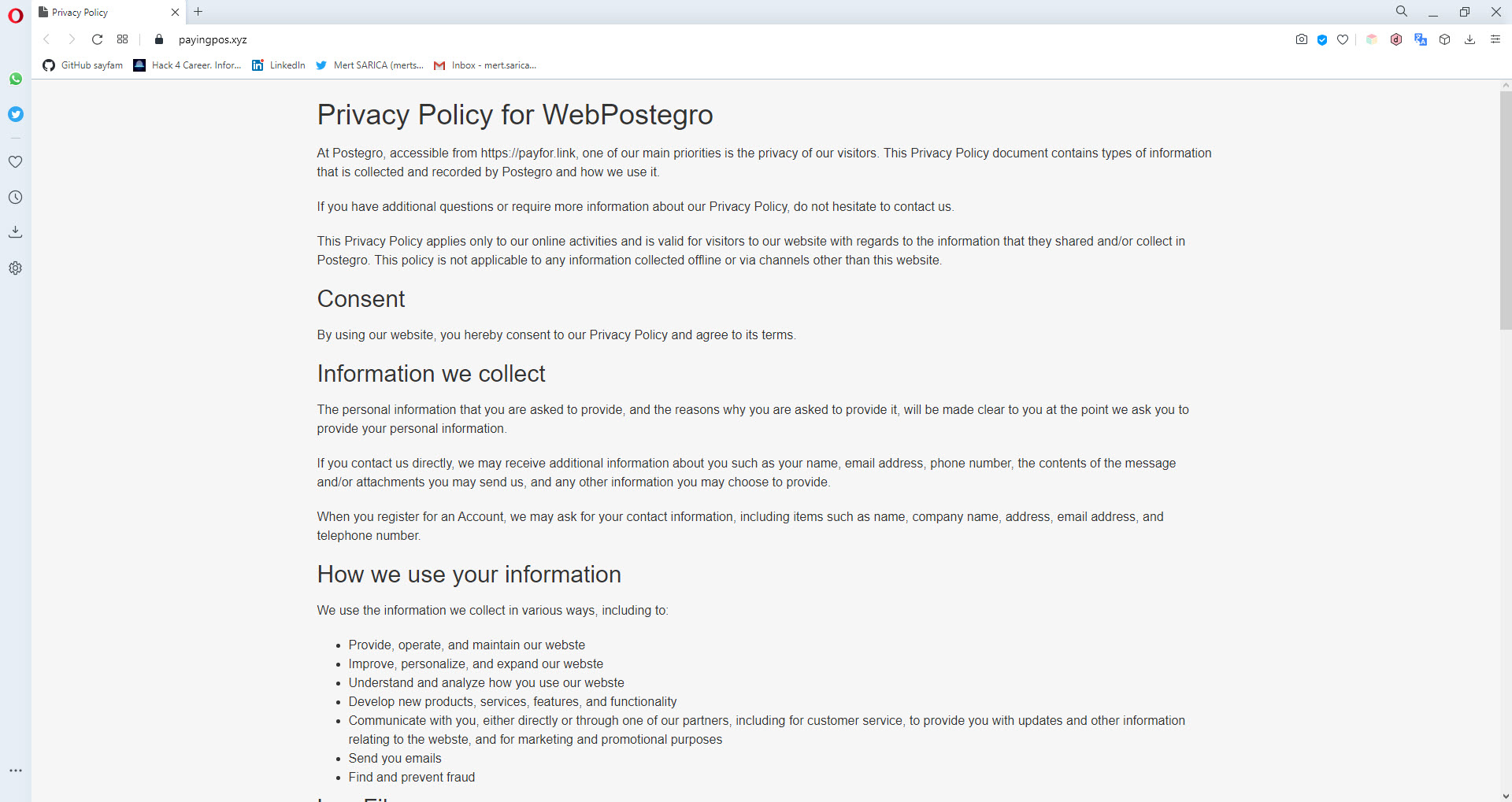
I started by reviewing the page of the Android application Web Postegro & Lili on Google Play. As of September 24, I did not see any permissions that raised any suspicions when I looked at the permissions used by this mobile application, which has been downloaded over 100,000 times. However, when I looked at the comments, I saw some suspicious comments from users claiming that there were unauthenticated logons to their accounts from unknown sources. Although the developer replied to one of the comments stating that it is stated in their security policy that connections may be made from abroad, I could not find such kind of statement in their policy.
After collecting the preliminary information from the Google Play page, I downloaded the Web Postegro & Lili application from the APKPure website to analyze it. When I uploaded the APK file to VirusTotal, I found no evidence that this application was malicious.
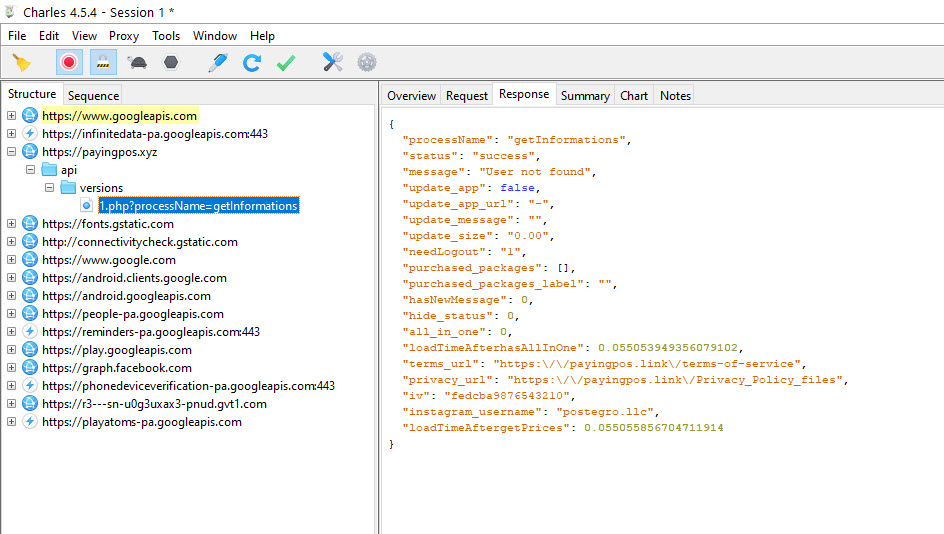
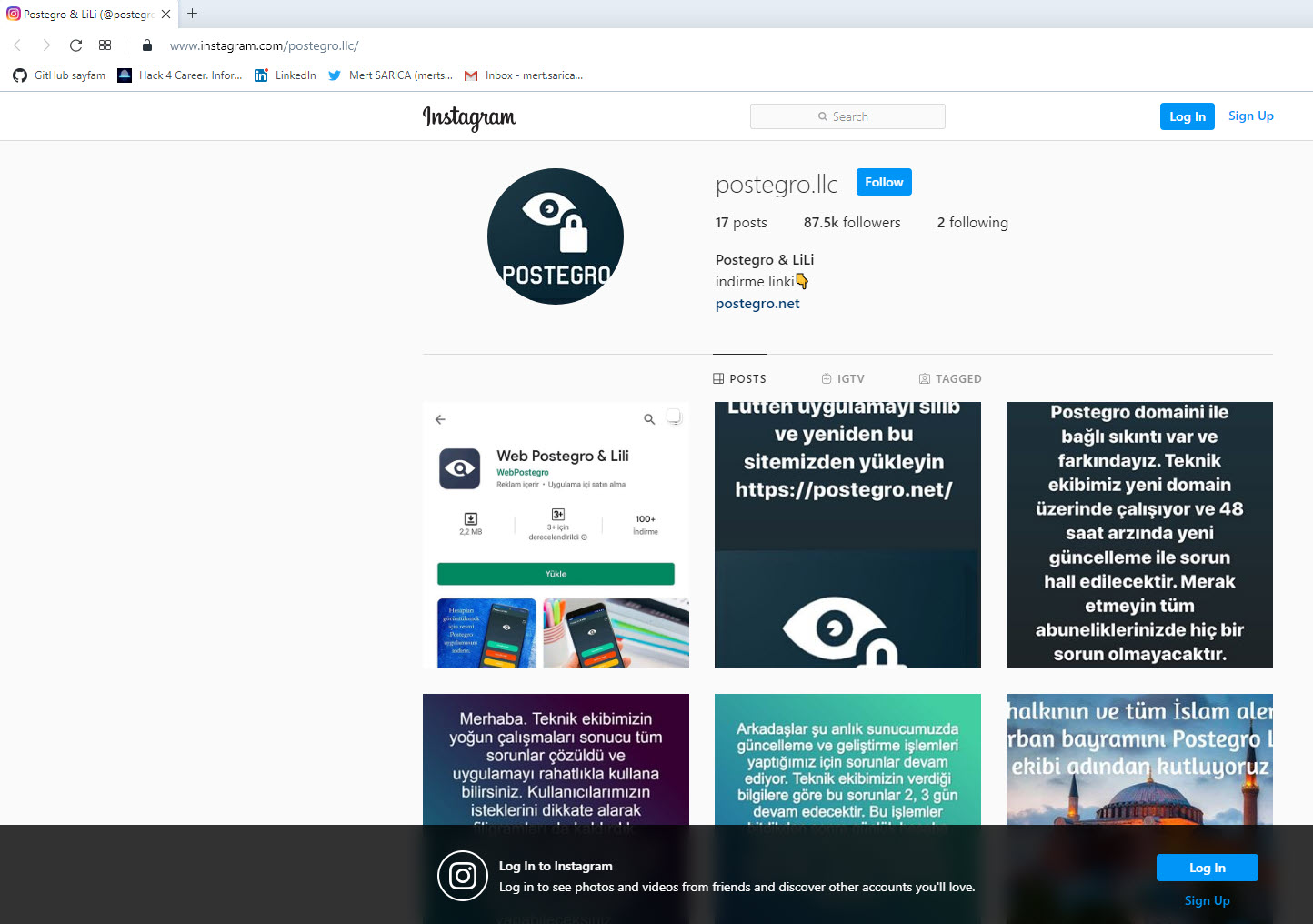
Then, I installed this application on the GenyMotion emulator and began recording the HTTP traffic generated during usage, using Charles Proxy, one of my favorite tools. In the first response from the payingpos[.]xyz web server that the application communicated with, I saw an Instagram account belonging to the application’s developer, postegro.llc. One of the photos shared on the account caught my attention, as it mentioned that the application had been removed from Google Play previously. When I visited the website registered on September 5, which was listed on the Instagram account, I learned that I could directly download the Web Postegro & Lili application (39.apk) from the website.
When I examined the traffic recorded with Charles Proxy, I saw that the Web Postegro Lili (Web Postegro Lili_v1.0_apkpure.com.apk) application communicated with the payingpos[.]xyz, webpostegro[.]net, and postegro[.]net servers during use.
When I uploaded the APK file 39.apk to VirusTotal, I did not receive any warning about it being malicious, similar to previous result. When I used the Web Postegro & Lili (39.apk) application, I saw that it communicated with the postegro202039348[.]com, imagecropper2020[.]com, postegro[.]net, and the inactive postegro[.]com servers. Because the postegro[.]com address was not working, and the general functions of the Web Postegro & Lili (39.apk) application, such as viewing profiles that are hidden and viewing profile viewers were not functioning, so I continued my analysis using the Web Postegro & Lili (Web Postegro Lili_v1.0_apkpure.com.apk) application.
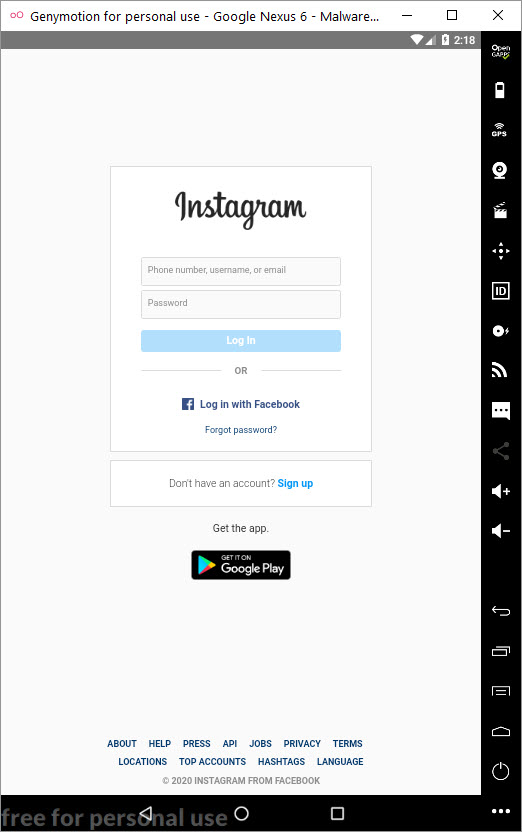
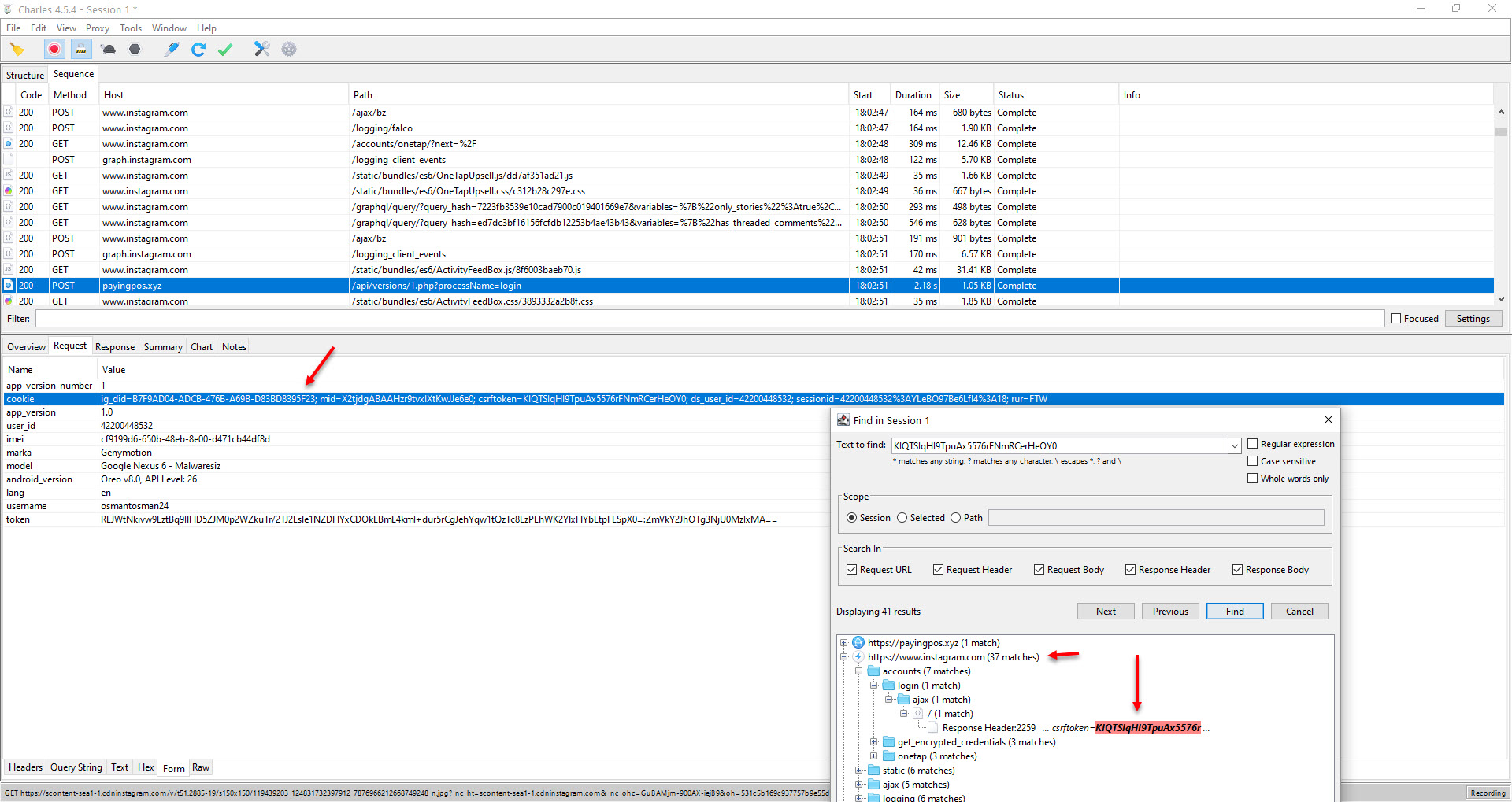
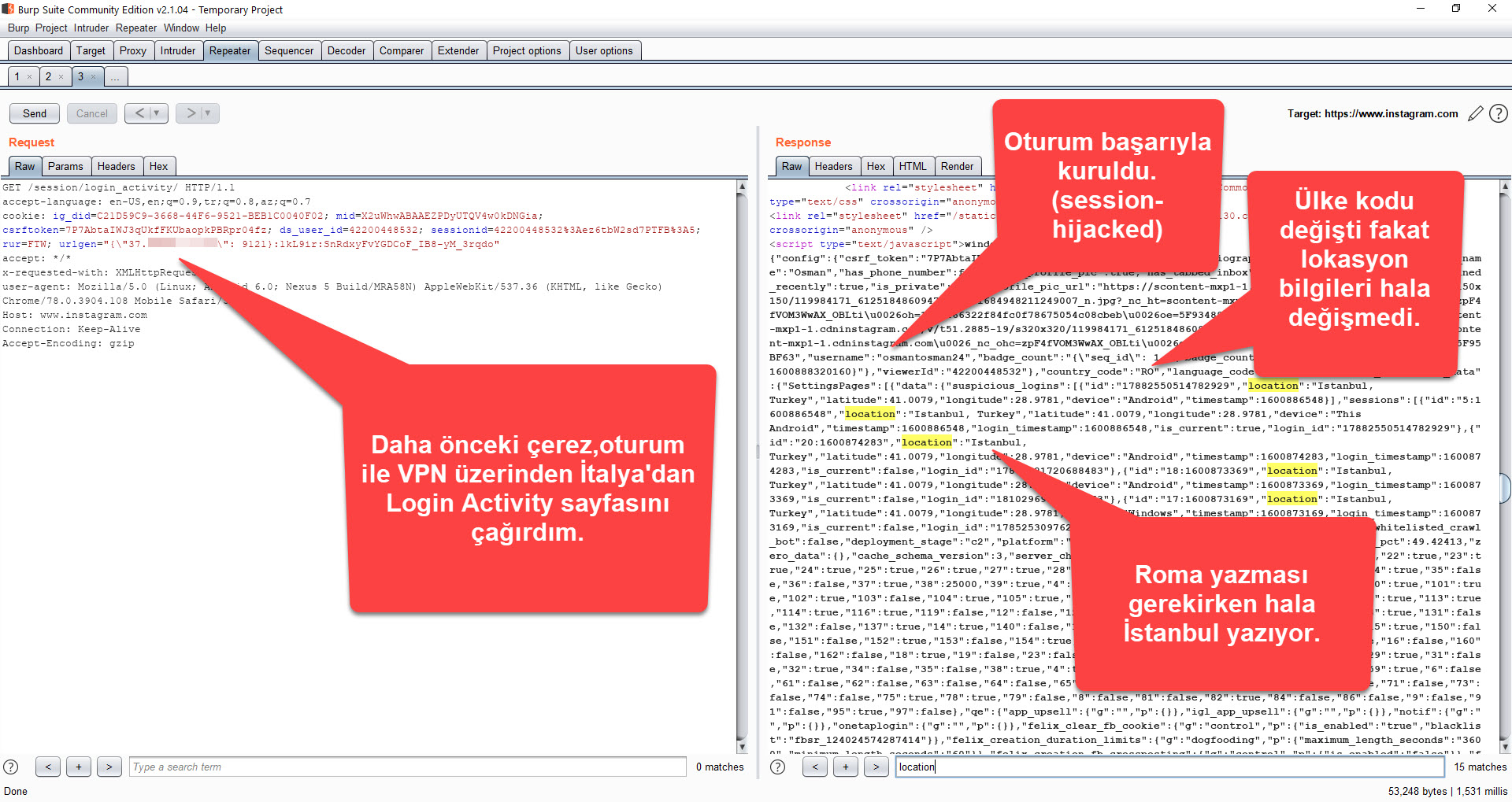
When I ran the Web Postegro & Lili application, I saw menus that allowed me to view profiles set to private (View accounts) and view profile viewers (Who viewed me). When I clicked on the View accounts menu, the application communicated with the instagram.com server through its own interface and brought up the login page where the Instagram username and password were entered. As soon as I logged in with my osmantosman24 Instagram username and password, which I created specifically for this investigation, I noticed that the application sent my session information, which was generated after verification with the instagram.com server, to the payingpos[.]xyz address using the cookie parameter and recorded this and more information in the /data/data/com.web.lilipostego/shared_prefs/com.web.lilipostego_preferences.xml file!
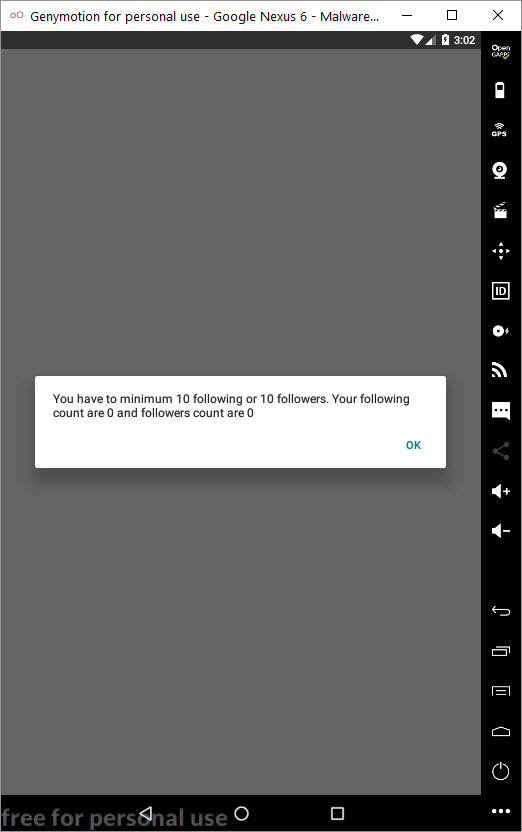
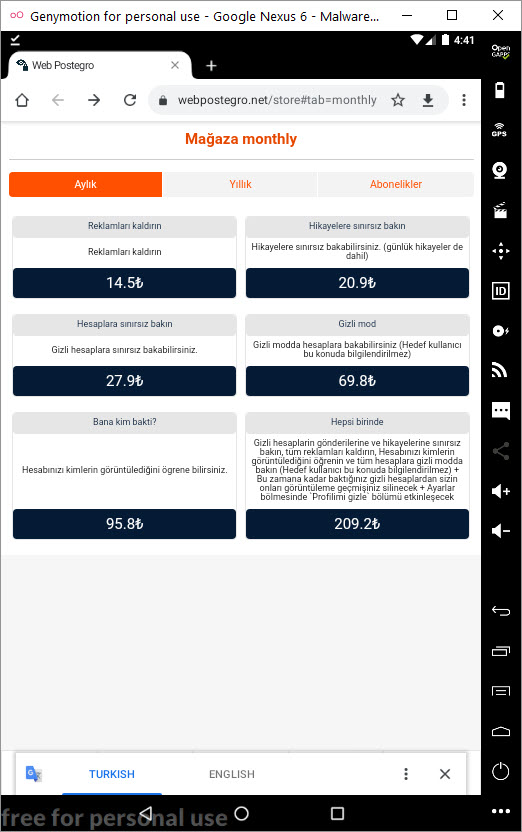
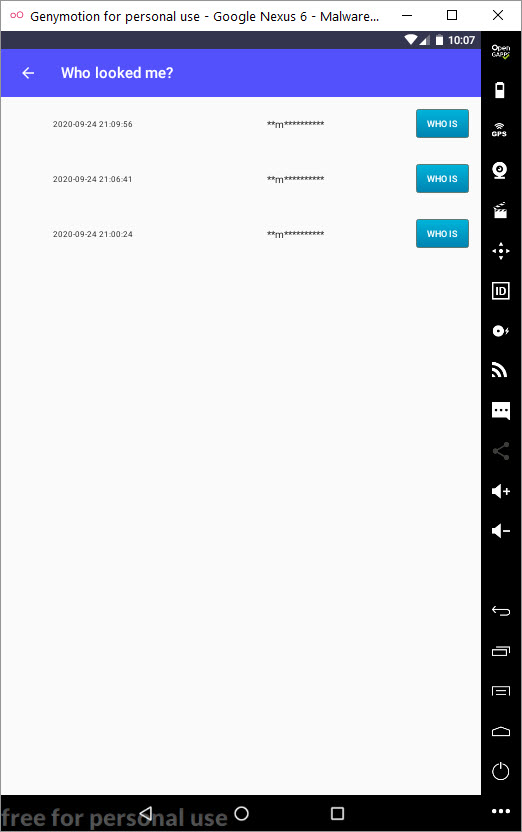
To be able to use the application, I had to follow at least 10 people or have 10 people follow me, so I quickly started following Instagram accounts that followed back and made them follow me as well. After increasing my follower count and stopping following all the accounts I was following, I started exploring the menus of the application and could view the content of profiles that were set to private and hidden. This application generates income by charging a certain fee to remove limits on the application (such as removing ads, unlimited viewing of stories, unlimited viewing of accounts, and the uncensored display of names of profile viewers).
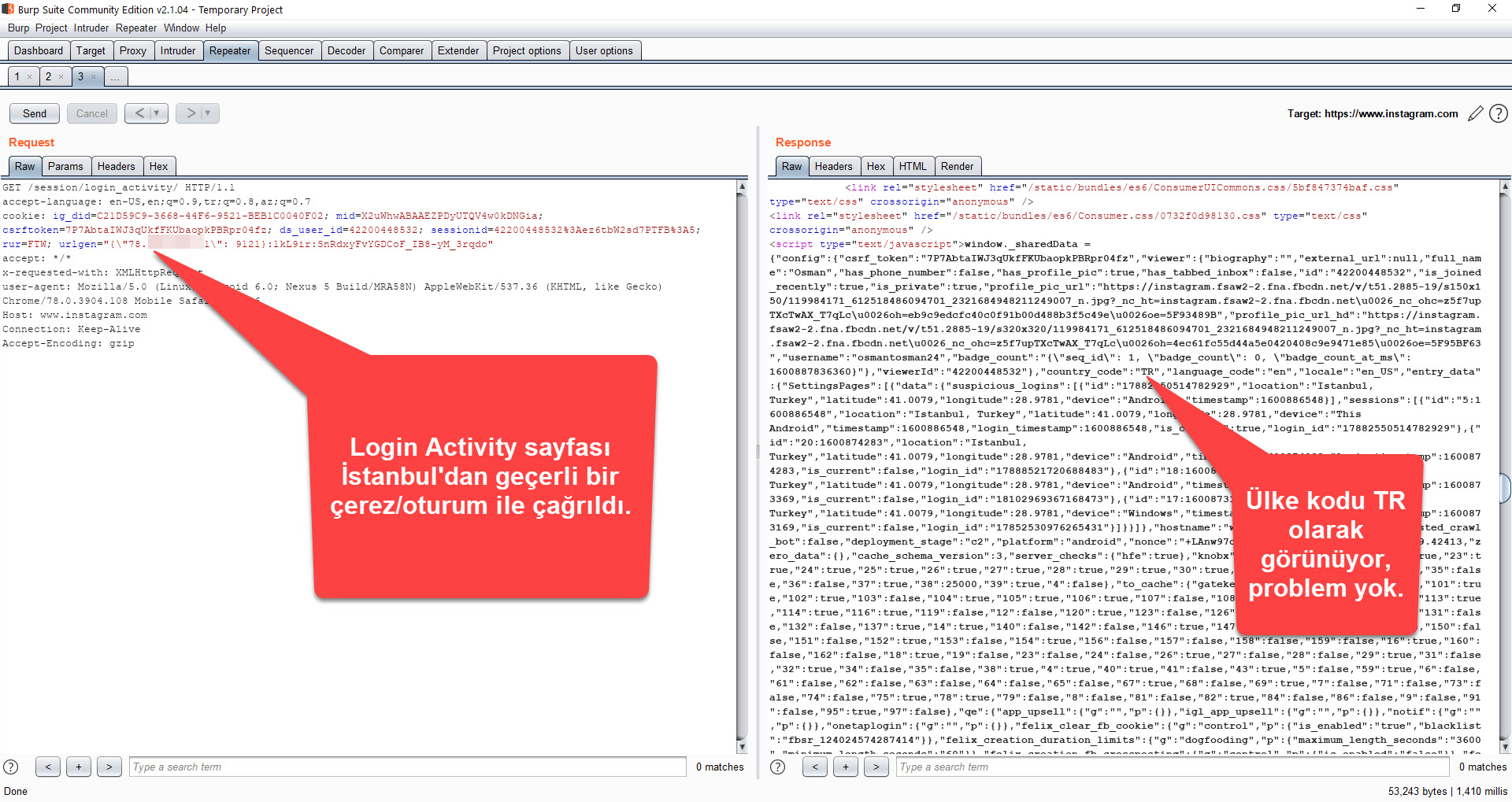
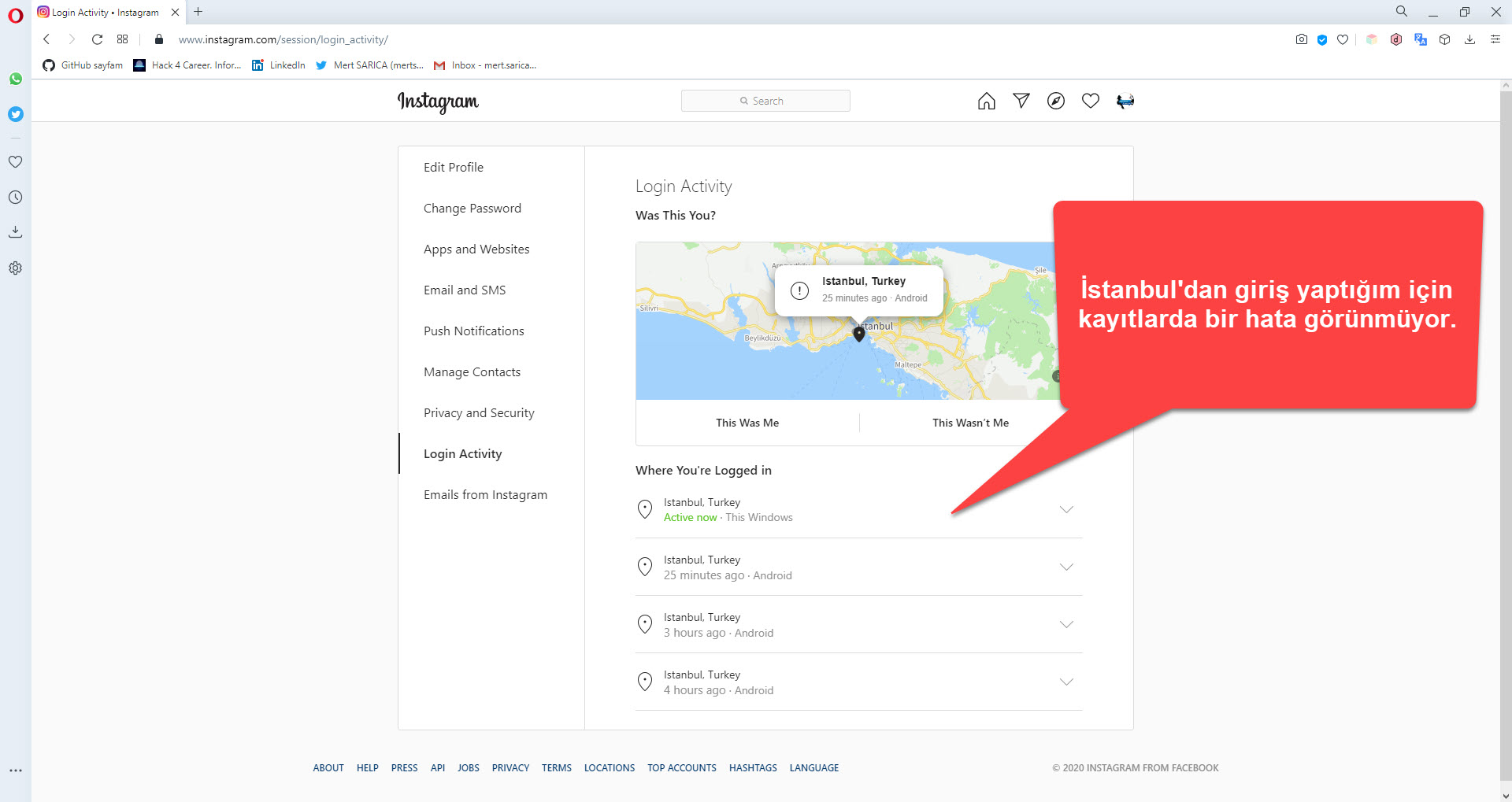
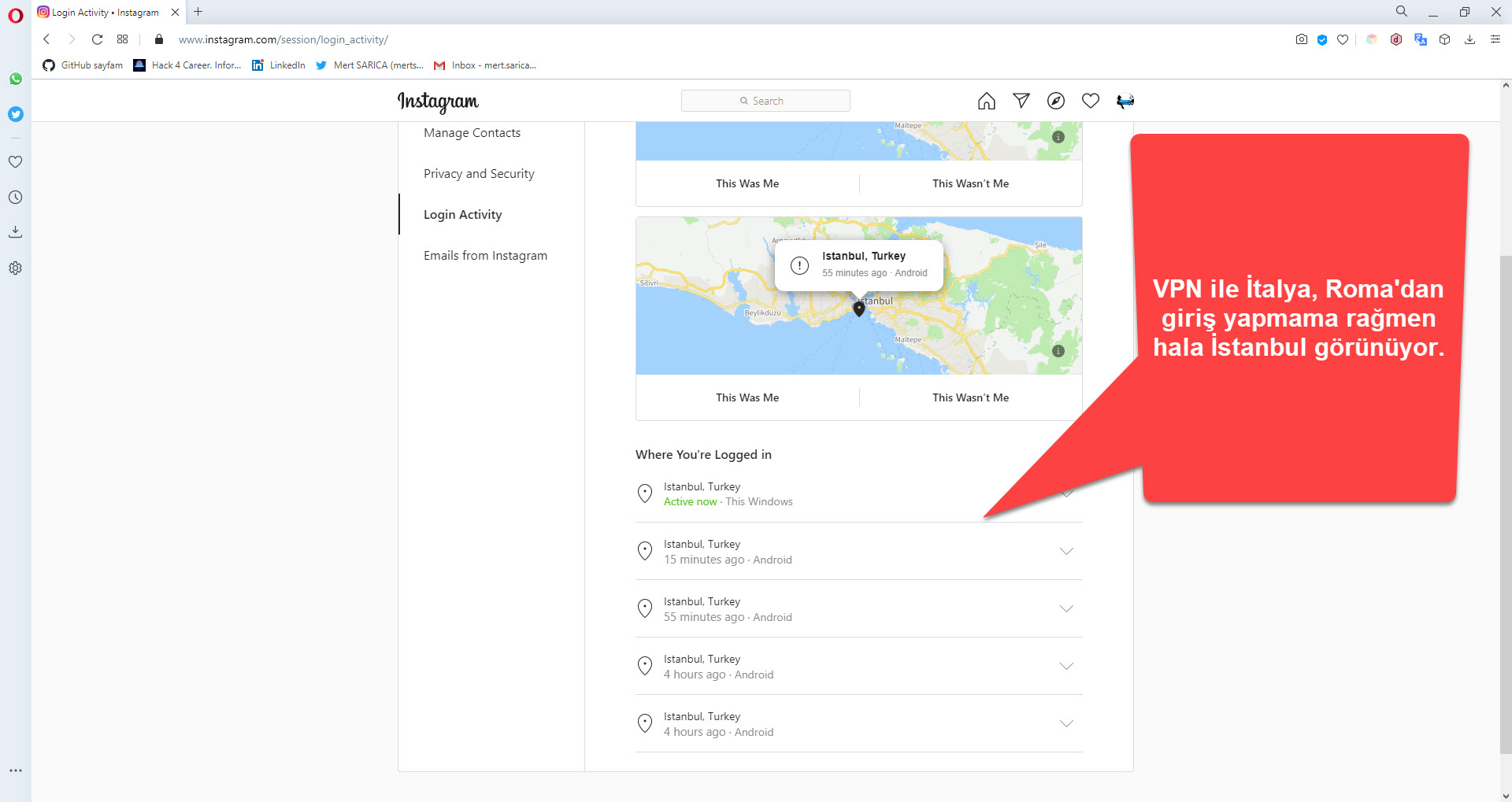
Generally, when an application with a secure architecture wants to access your Instagram information, it uses the Oauth protocol to request authorization from you. However, the Web Postegro & Lili application does not have a section that asks for permission or approval from the user. Therefore, to allow this application to view and list hidden profiles, it must constantly access the information of all accounts belonging to users who log in through the application by connecting to the Instagram servers with session information belonging to those users. (session hijack) To understand that this method is being used, I conducted a test using Burp Suite over VPN to determine if the session information sent by the Web Postegro & Lili application to the payingpos[.]xyz address with the cookie parameter was sufficient to access my Instagram account. When I logged in to Instagram again through the Web Postegro & Lili application and made a request through Burp Suite to my Instagram account’s Login Activity page (https://www.instagram.com/session/login_activity/), I was able to successfully receive a response from the server. When I rechecked the Login Activity page to see if there was a way for Instagram to understand those who accessed the account in this way, unfortunately, my access from abroad using VPN was not shown.
Despite repeatedly explaining the situation to Facebook’s security team with screenshots, they were unable to understand what they needed to do in the face of even the most basic fraudulent scenario (if an Instagram account is accessed from two different countries within 5 minutes, the user will be warned and the Login Activity page will show which country the connection was made from).
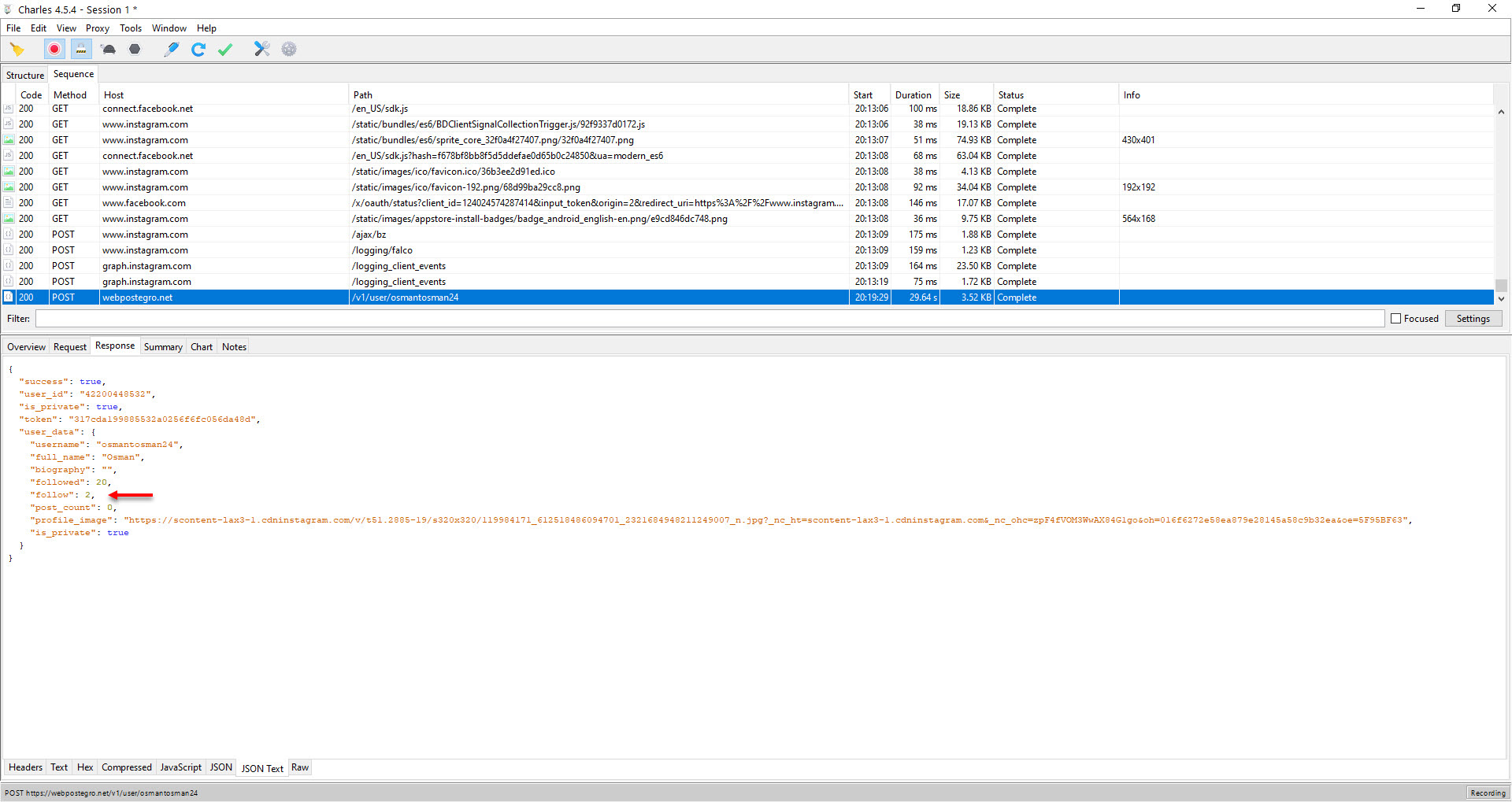
In order to regain control of my account and find out whether the Web Postegro & Lili app developer was still able to access my account after logging out, I accessed my Instagram account from a Windows device and increased the number of people I followed by 1. Then, when I asked the webpostegro[.]net server to bring me the current information belonging to the user, it could also get me the information of the person I had most recently started following, meaning that access was still continuing.
While I was thinking about how to prevent the Web Postegro & Lili application and its developer from accessing my Instagram account and session, I decided to see if changing my Instagram password would work and, whether or not I changed it, I confirmed that they couldn’t access my account through webpostegro[.]net and ended my research here.
Brief summary of my research is:
As a personal recommendation, if you come across a person, application, website, etc., that promises to show you who views your profile, be aware that this feature does not exist among the features of the social media applications.
Hope to see you in the following articles.