WordPress Security
For nearly a decade, I have been conducting research on cybersecurity and continue to write and share what I have learned with all of you. When I look at the feedback I receive from you, it makes me very happy to see that many of you benefit from what I write. Sometimes, there are those who perform minor cyber attacks to my blog, such as a small-scale DoS attack, not with malicious intent but simply to send me a message. There are also instances where I encounter attacks that I cannot fully understand the reason or intention behind, including attempts to access the administrator page. Based on this, in this article, I have decided to share how I detect one of these attacks and provide tips on how WordPress CMS users like myself can secure their blogs.
First, if we look at the statistical information related to WordPress, it is the most widely used content management system globally, accounting for about 60% of the CMS market. Approximately 33% of all websites on the internet use WordPress, with over 55,000 plugins available. Over the years, the types of vulnerabilities detected in WordPress have varied, but the most commonly found vulnerability to date is Cross-Site Scripting (XSS). When we examine the WordPress vulnerability database, we can see that more than 15,000 vulnerabilities have been identified in WordPress core code and plugins.
When we consider how WordPress sites are generally hacked, we often find that it is due to insecure hosting services, weak administrator passwords, outdated versions of WordPress, plugins, themes, and the use of pirated themes (Backdoor Hunting) containing backdoors.
Although my wp-admin page, which is used to detect weak administrator passwords, is publicly accessible, I have been using the Duo Two-Factor Authentication plugin for years to implement multi-factor authentication for administrator login. I also utilize the Wordfence Security plugin to automatically block IP addresses involved in brute-force attacks, as well as to detect and report potential security vulnerabilities. Additionally, I prefer to use premium themes to avoid themes containing backdoors. To avoid dealing with insecure hosting services, I have been using a VPS for many years.
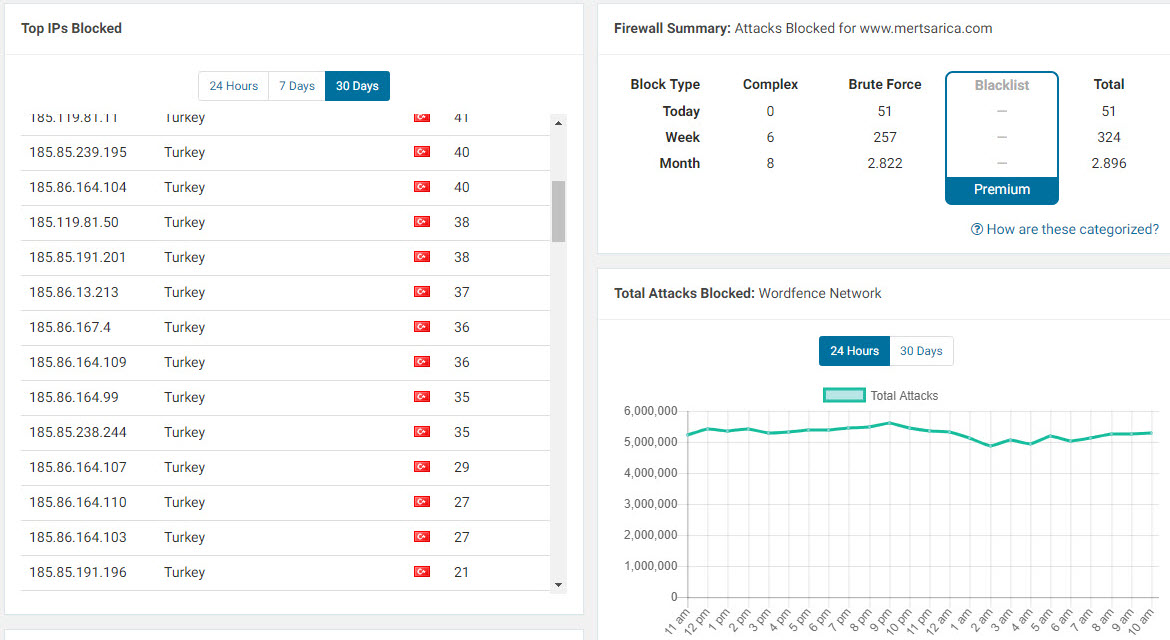
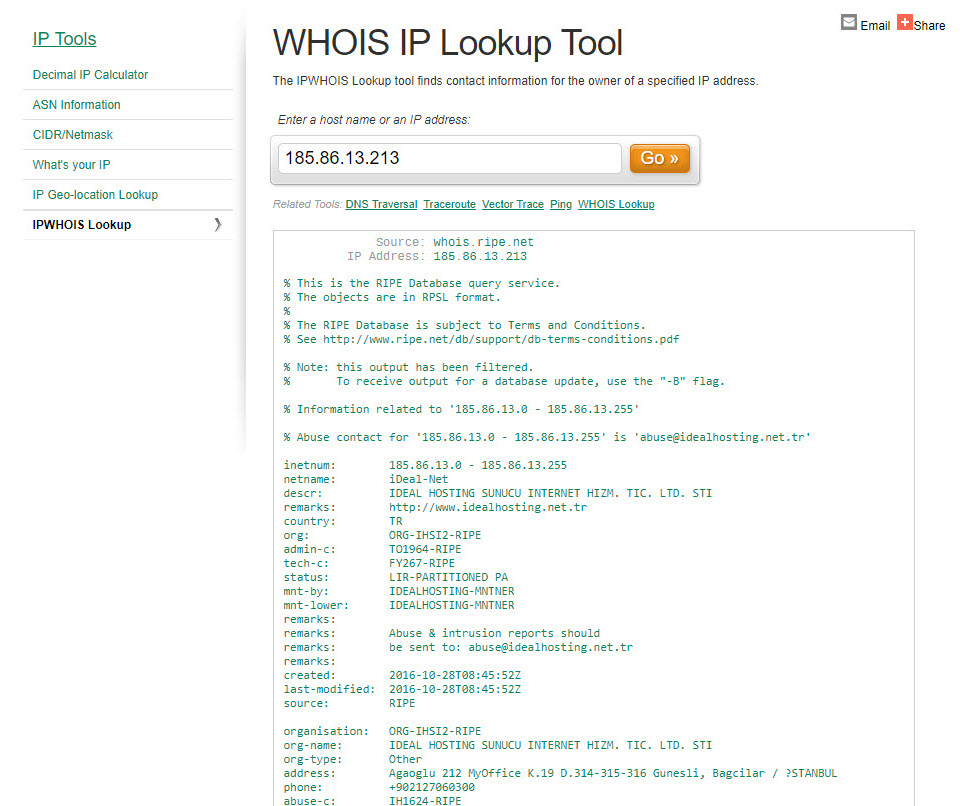
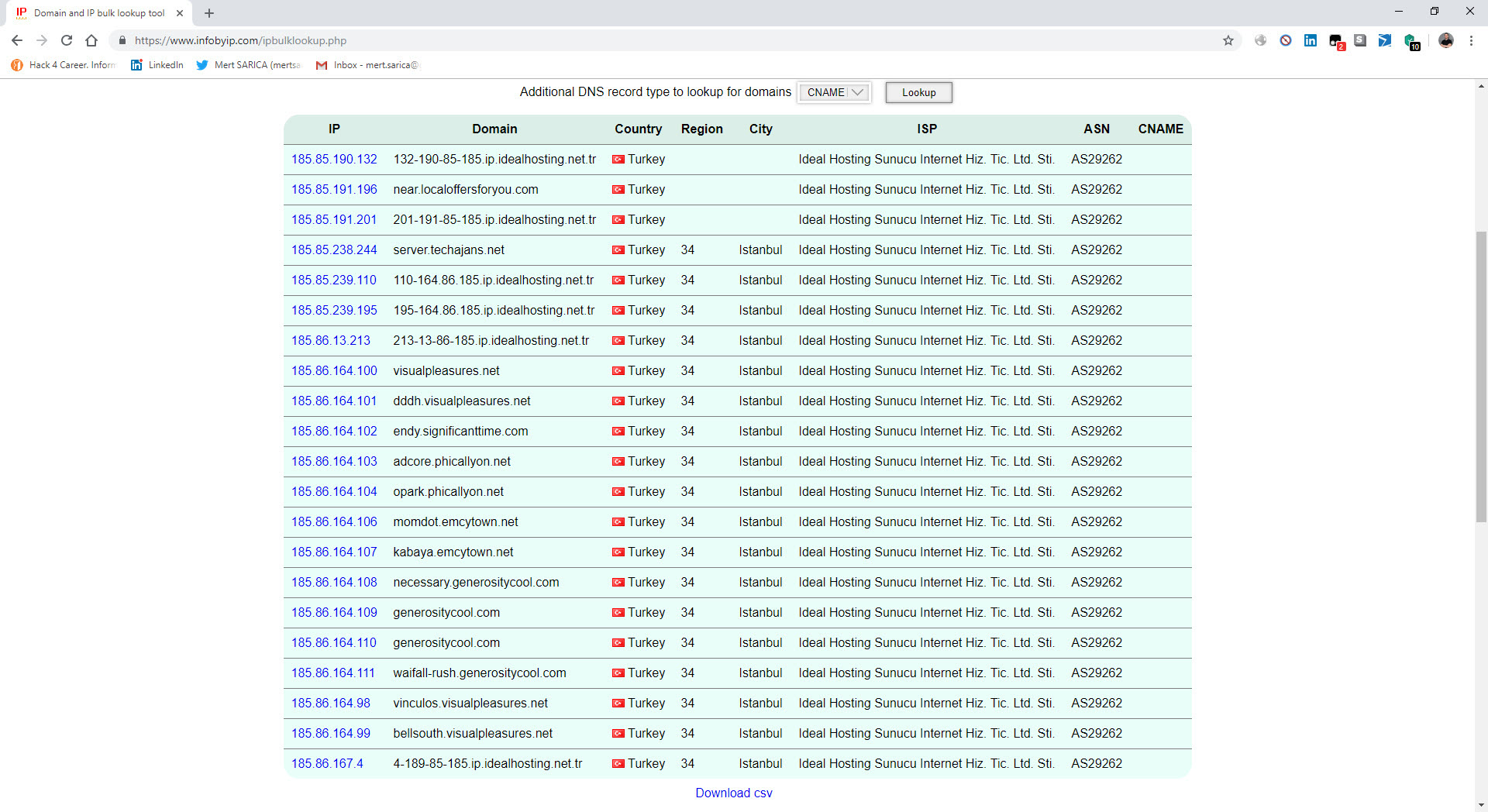
One day in July 2018, while checking the security dashboard of my Wordfence plugin, I noticed that the most blocked IP addresses were from Turkey, indicating attempts of brute-force attacks on my administrator page. When I checked the whois information of these IP addresses, I discovered that the majority of them were associated with a hosting service provider called iDealhosting. Intrigued by this, I decided to closely monitor the attacks originating from these IP addresses on my blog as part of a security investigation.
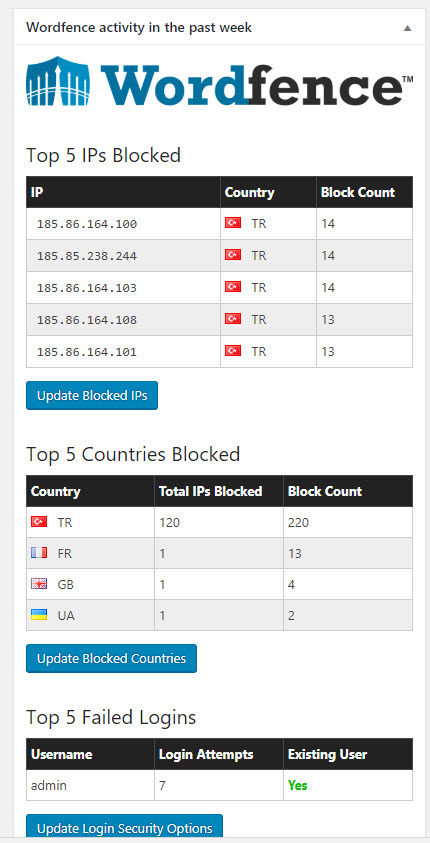
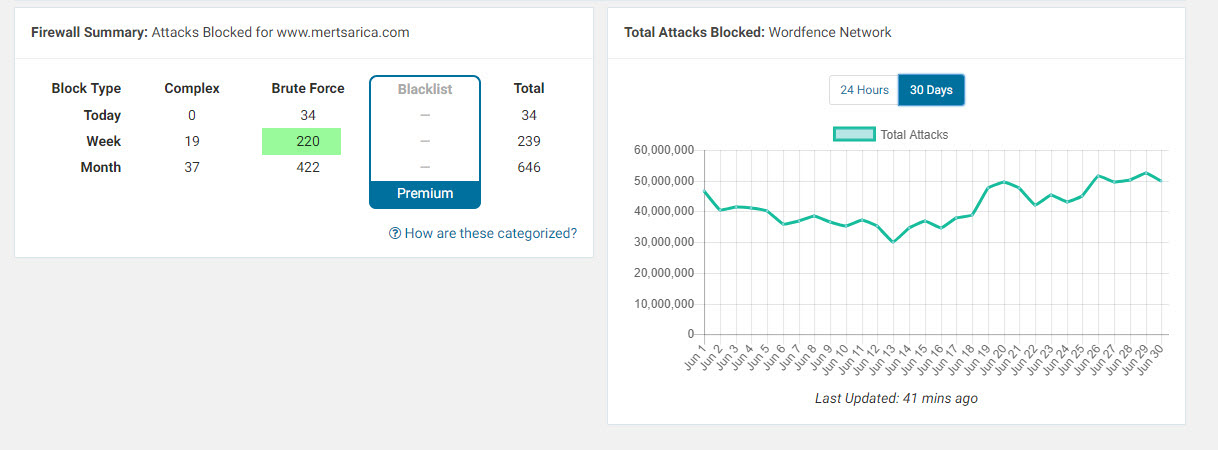
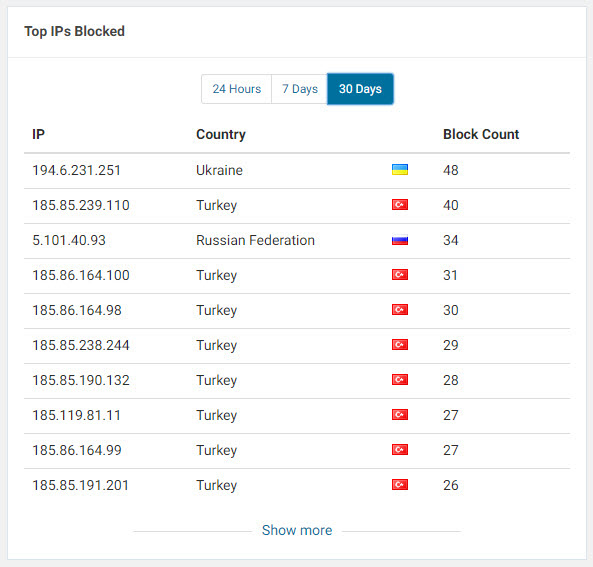
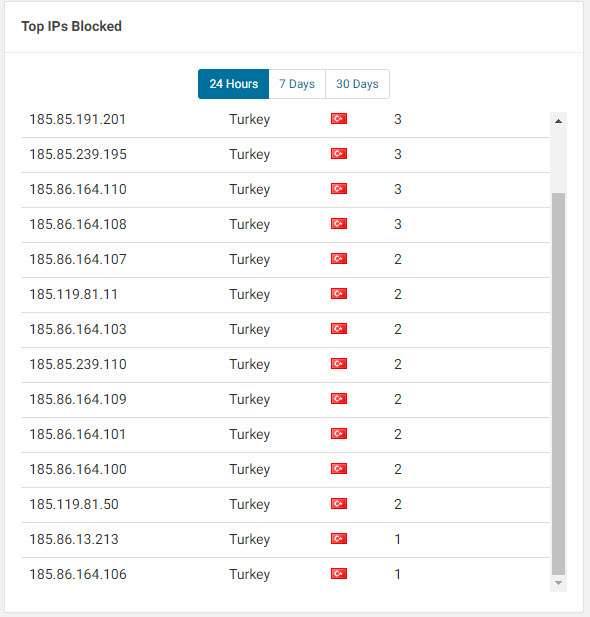
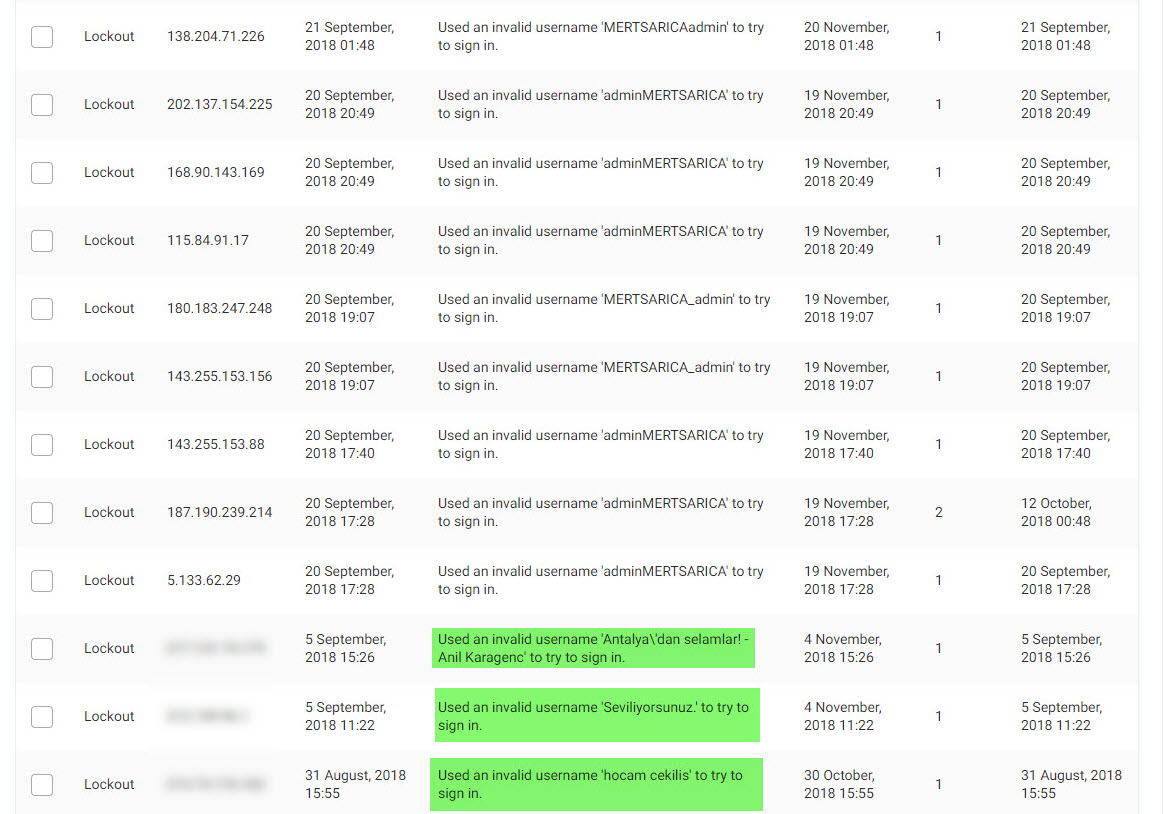
When I checked the security dashboard again in October, I noticed that the brute-force attacks were still ongoing from 22 IP addresses. As a security researcher, one of the first questions that came to mind was whether this was a targeted attack attempt on my blog. One of the easiest ways to determine this was to learn the passwords used in the brute-force attacks. Therefore, without wasting any time, I got to work on it.
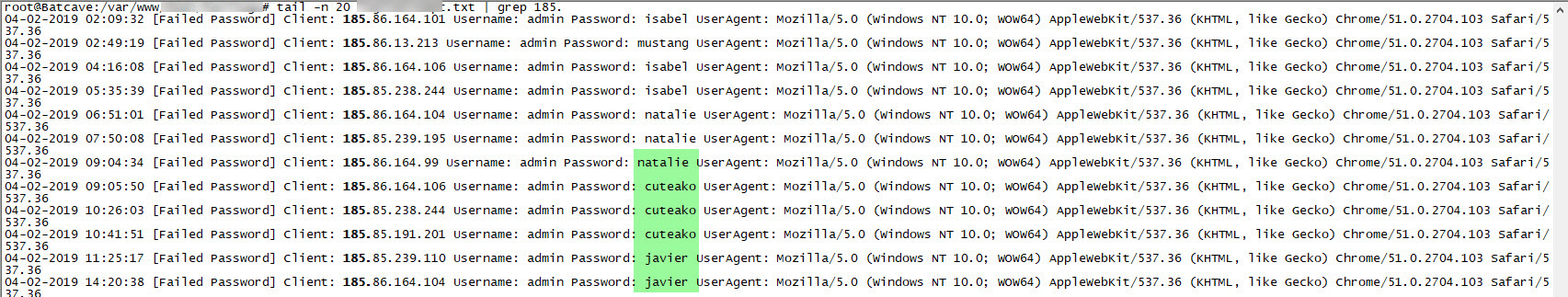
First, I prepared a PHP code that records failed login attempts to the wp-login.php file, along with the passwords, and saves them to disk. Then, to stay informed about any changes in the recorded file in real-time, I made a small definition in OSSEC HIDS.
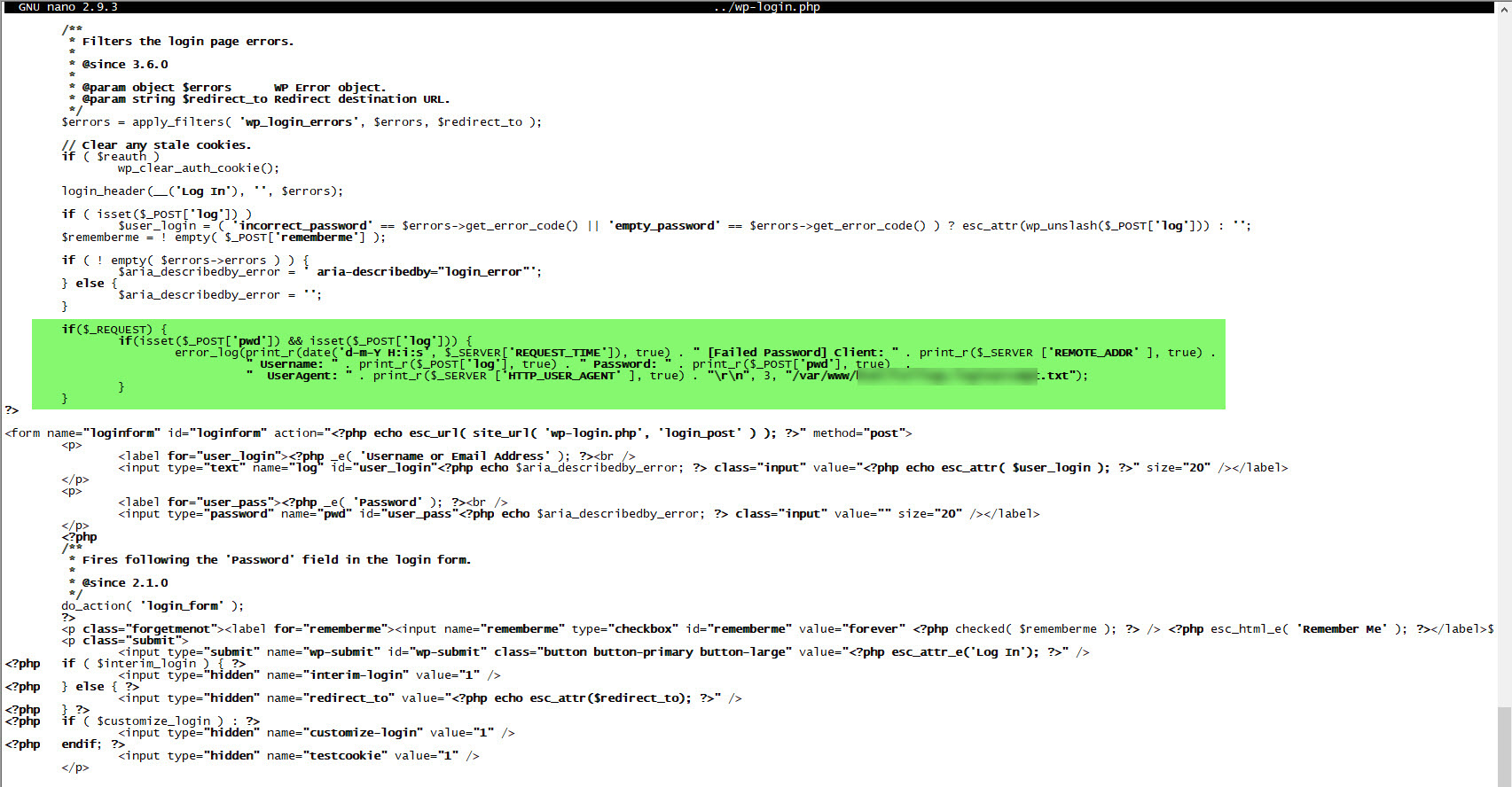
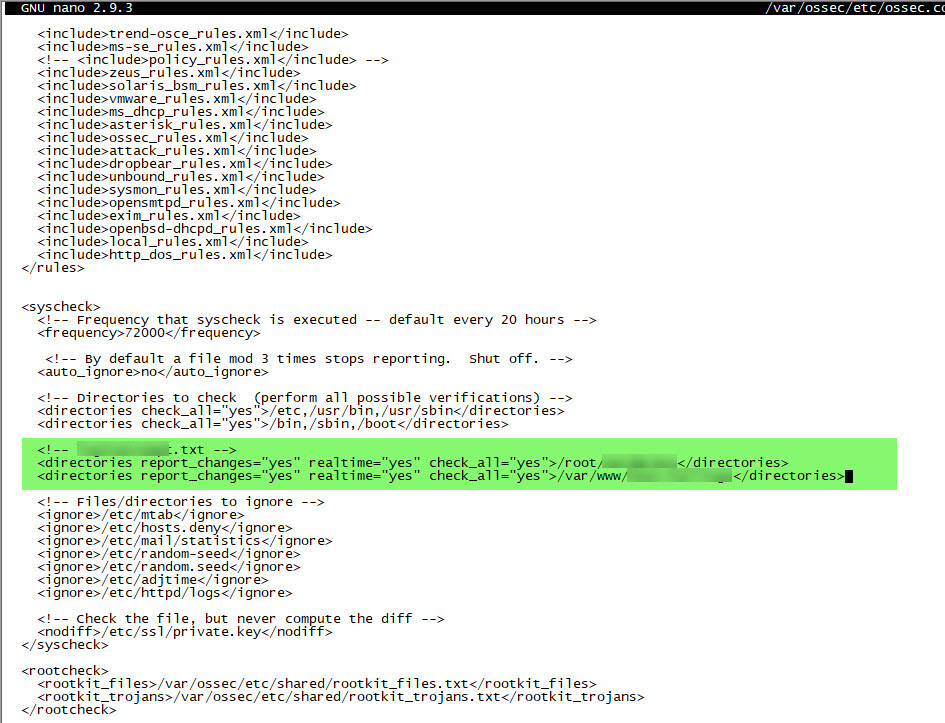
When I examined the recorded failed username and password attempts throughout the end of October and the month of November, I discovered that the attempted usernames and passwords consisted of words found in my blog posts rather than ordinary dictionary words. This information indicated to me that it was indeed a targeted attack attempt.
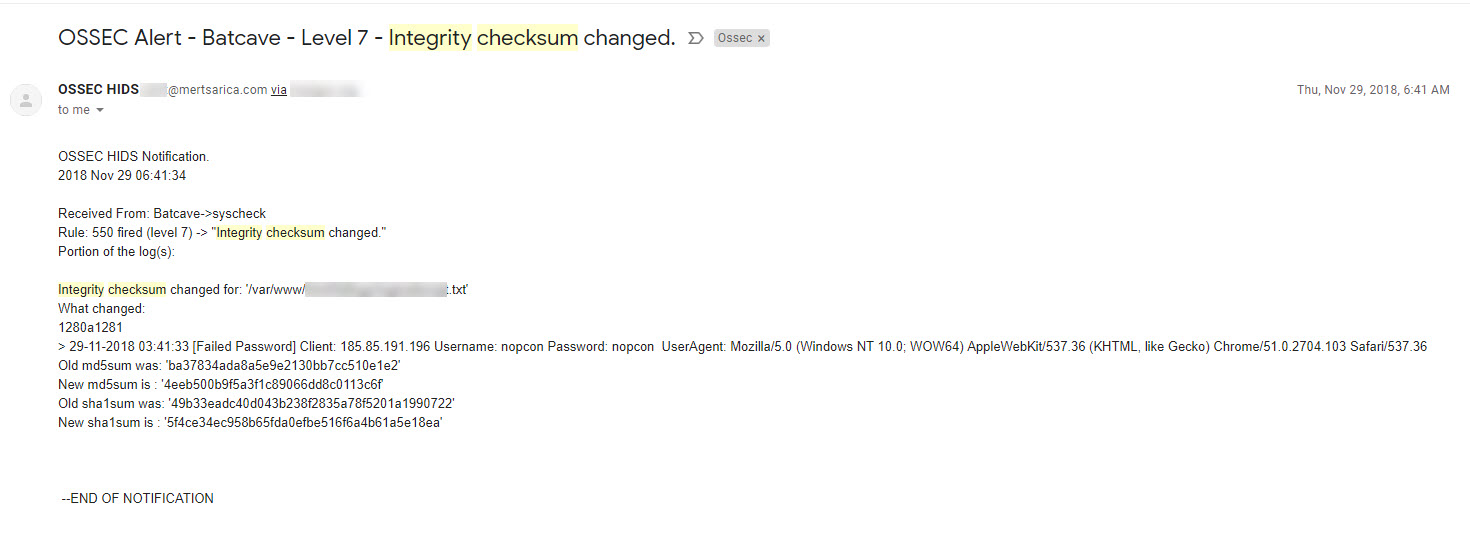
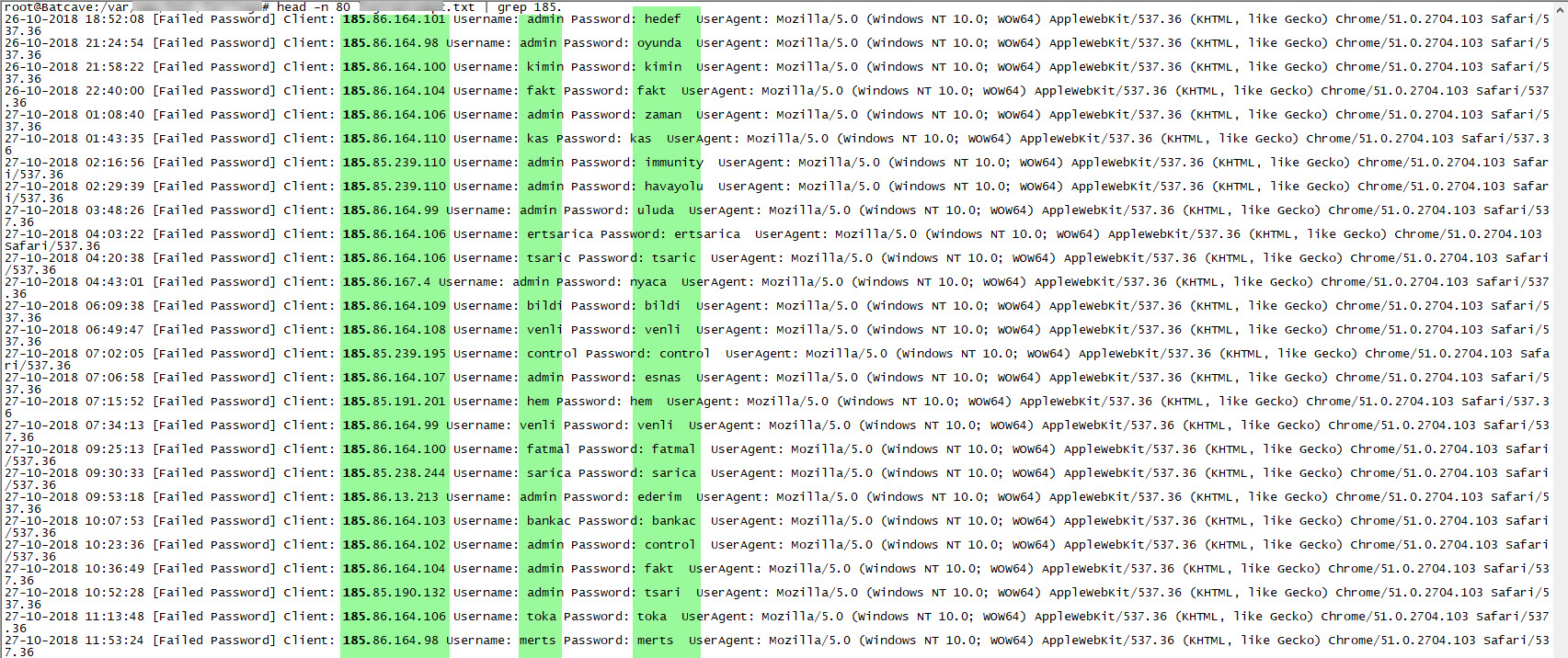
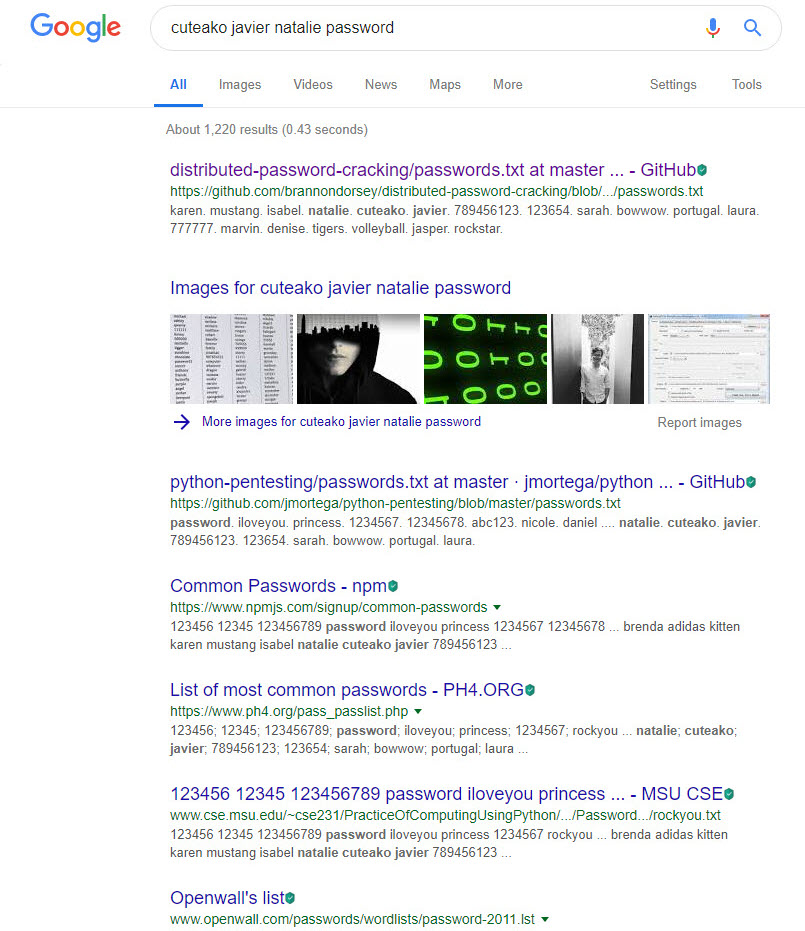
When I revisited the attempted passwords in February 2019, I noticed that this time the passwords being tested were obtained from the database of Rockyou.com, which was hacked in 2009.
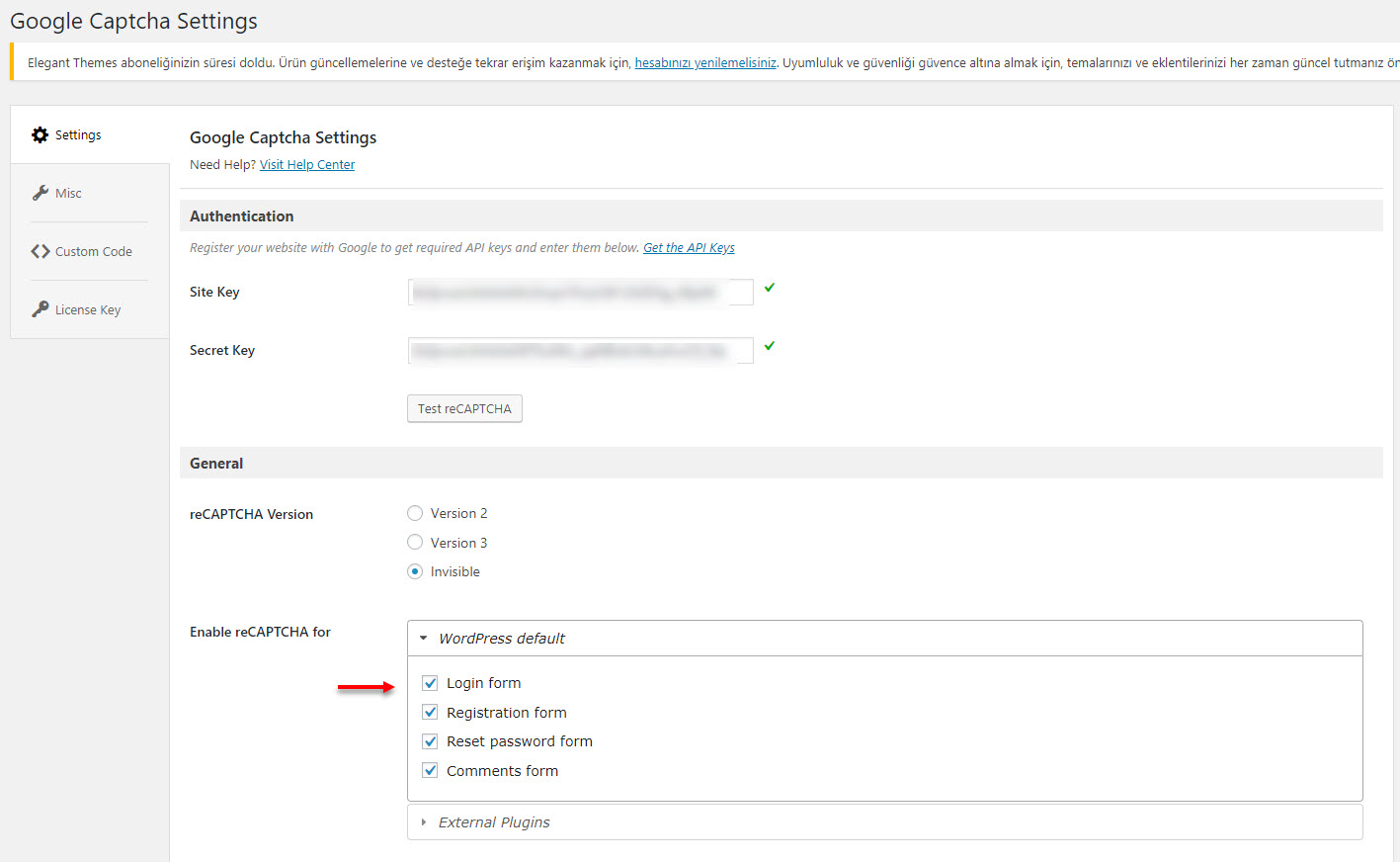
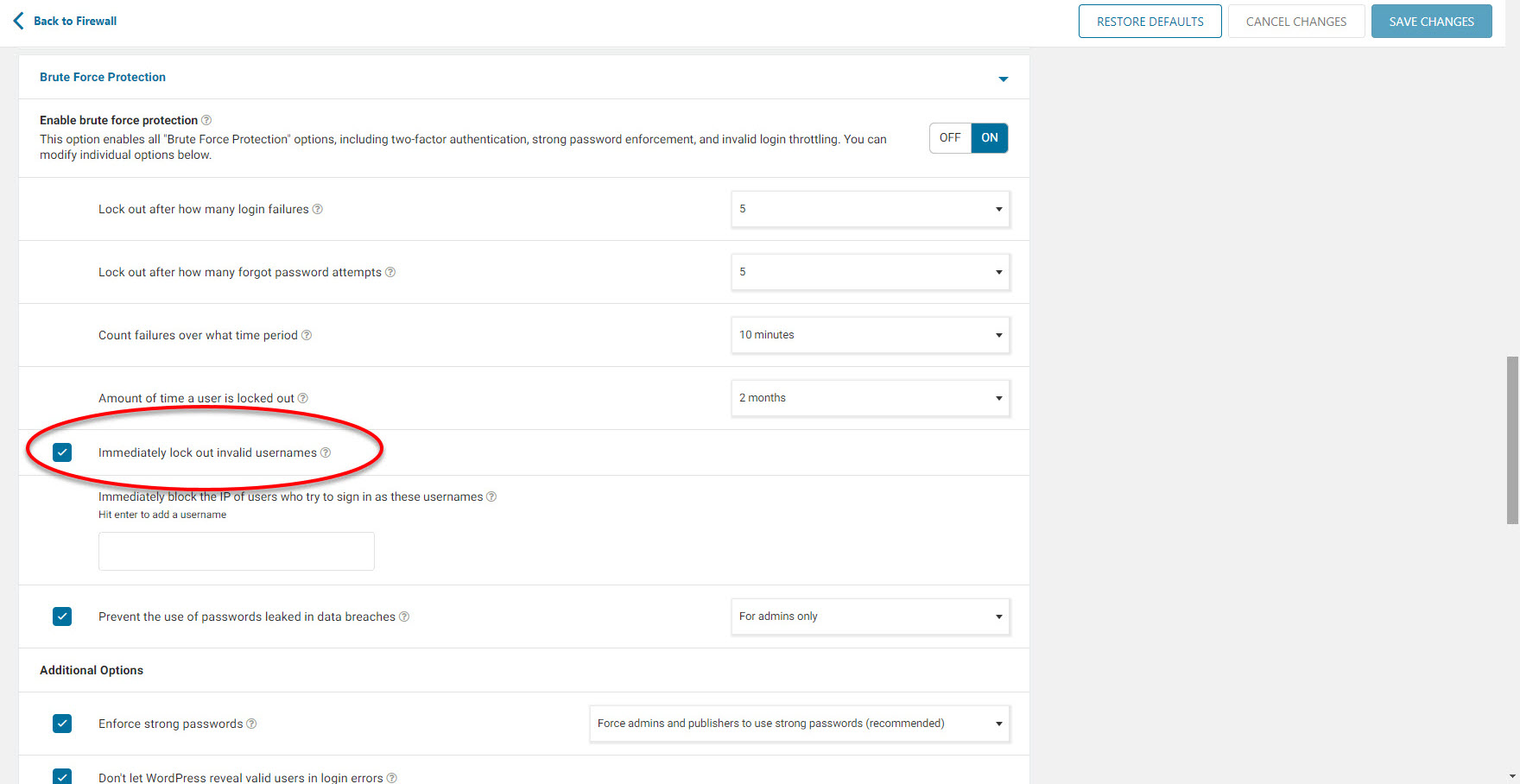
After completing my research, I decided to tighten the security controls that I had previously relaxed. Firstly, I enabled the Google Captcha plugin for the administrator page. This added an additional layer of protection against automated login attempts. Additionally, in the Brute Force Protection section of Wordfence’s Firewall settings, I configured it to automatically block IP addresses that made failed username attempts. These measures helped strengthen the security of my website.
As a result of this research, I sadly learned that someone has been attempting to hack my blog for months. For WordPress CMS users like myself, I strongly recommend installing and properly configuring the Google Captcha, Duo Two-Factor Authentication, and Wordfence Security plugins. Additionally, I highly recommend closely monitoring your systems with OSSEC HIDS to detect any suspicious activities. Taking these precautions is crucial to enhance the security of your WordPress website.
Hope to see you in the following articles.